Cause#
For keyboard recording, um, it's definitely worth mentioning.
Environment and Preparation#
Environment#
- Kali 2019.1
- Win7 SP1
Source Code Download#
-
Author's GitHub: https://github.com/thelinuxchoice/spykey
-
I copied it over: https://gitee.com/soapffz/spykey
Just one spykey.sh and two ico application icons (for camouflage)
Requires support for mingw-w64:
sudo apt-get install mingw-w64 -y
Usage#
Enter the spykey folder, give spykey.sh executable permissions, and then execute it:
chmod 755 spykey.sh
./spykey.sh
Then there will be several options in sequence:
- Select Port (default is fine)
- Payload name (the name of the generated logger, you can rename it after downloading, just enter anything here)
- Log name (used to see what is being recorded)
- Select Icon (here, only two well-known foreign social software icons,
messengerandwhatsapp, are provided, you can add custom icons)
The author also reminds not to upload to virustotal haha, then the payload will be generated, and it will be downloaded using the author's provided server
You can directly induce the victim to download through this link, or you can download it and do some work before sending it to the other party (for example, bundle it in a normal exe cough cough I didn't say anything)
As you can see, the author's backup download address is down. After generating the payload, Kali starts listening
We send it to Win7 on the same network segment (and NAT network as Kali), and Win7 connects by double-clicking Payload.exe. Let's see the effect by typing some words:
In Kali, enter type log name to view:
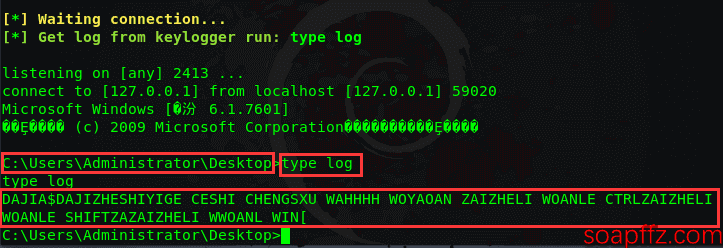
Some minor issues were found, such as not recording shortcuts like ctrl, shift, and win, but it doesn't matter because we know what we want to record
So the virtual machine on the same network segment is fine, let's try other environments
- Roommate's computer + a certain operator's student terminal
The dormitory network is distributed through a certain evil operator's PPP adapter, which is still an intranet in plain terms
The network segment is from 172.31.0.1 to 172.31.xxx (unknown).255, and the roommate's IP at this time is:
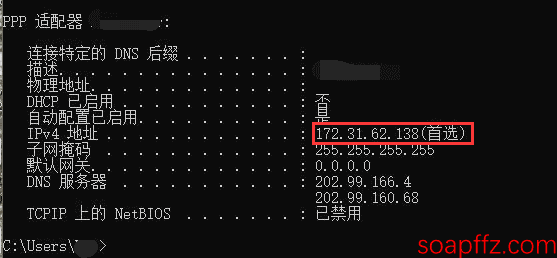
Make a new payload and insert it into the roommate's computer with a USB drive: (seems to be missing a few words?)
Okay, still 127.0.0.1
- Roommate's computer + my hotspot
Use my phone as a hotspot, make a new payload and insert it into the roommate's computer with a USB drive:
Ok, still 127.0.0.1, the experiment ends here
Conclusion: It is not our local connection, but all connections are made on the author's server. Hmm, this is not good, because what we can see, the author can see too
Summary#
| Advantages | Disadvantages |
|---|---|
| Simple, just set the name, download and give it to the other party to use | The server is owned by the author, information can be easily leaked |
| Can be monitored as long as there is internet access | Need to keep listening all the time |
| High evasion, can resist most antivirus software without evasion processing | Functionality needs improvement |
| No need to set up a server yourself | Port change requires re-generation every time |
Ending:
Throughout the process:
Huorong didn't react at all...
Huorong didn't react at all...
Huorong didn't react at all...