起因#
信息收集篇基本讲完了,接下来讲常见漏洞的原理及实现
技术还没有练熟肯定不能直接上公网搞,作为渗透小白的我们肯定要先本地练习
本篇主要介绍基础环境及常见靶场搭建
** 由于我现在写的是自己使用过的靶场,后面我可能会想尝试新的靶场,所以这篇文章设置为长期更新 **
** 有觉得这篇文章没有描述到的靶场并且不是那么难安装的可以在评论区留言探讨! **
基础环境#
既然要搭建渗透环境,那么肯定就要在搞崩环境的时候能快速恢复,虚拟机软件和虚拟机是必备的
我自己习惯使用的搭配是:virtualbox+Win7+Ubuntu Desktop 18 LTS+Kali 2019
其中:
virtualbox:虚拟机软件,提供各种网络环境
Win7:SP1+.NetFramework4.7+微软常用运行库+7-zip,使用NAT或Hostonly能快速切换
Ubuntu:作为常用Linux环境,除了必须在Kali做的都在它完成,使用NAT+Hostonly双网卡
Kali:渗透必备环境,但是由于太耗资源我尽量避免使用,使用NAT+Hostonly双网卡
** 当然,使用双网卡因为我使用的是校园网,不需要认证的网络全部使用桥接即可 **
准备工作#
搭建靶场依赖的环境
** 注意,安装环境的时候一定会遇到 Apache 的 80 端口被系统的 web 广播服务 PID 为 4 的进程占用的情况 **
所以准备阶段先发制人,在管理员cmd执行Sc config http start= disabled重启即可
phpstudy#
phpstudy同时支持Windows和Linux版本
phpstudy 的 Windows 版本#
目前正式版为phpstudy 2018版,在2018-02-11发布,点我下载20180211 正式版
默认安装路径为:C:\phpstudy,一直默认安装如果遇到端口被占用点击重试就好
安装完主界面长这样:
默认主页只有一行Hello World
最新版为 5 月初开始内测的phpstudy V8.0版本,可以到版本更新日志页中去添加内测 qq 群获取新版本体验
默认安装路径为:C:\phpstudy_pro、如果你遇到Apache启动不了的问题,参考最上面准备工作标题下的解决办法
新版本安装完主界面长这样:
默认主页长这样:
估计路径和使用方法和正式版差不多,所以为了方便后面基于phpstudy的环境搭建都是基于phpstudy 2018版的
安装完可以修改下mysql的默认密码为root(默认为空),修改还是挺方便的。
phpstudy 的 Linux 版本#
安装了超久时间都没安装完,总的来说不建议安装。
xampp#
xampp同时支持Windows和Linux版本,版本下载全部托管在sourceforge 上
安装的时候可以默认安装Apache,但是没有Nginx:
所有服务开启后的截图如下:
WampServer#
WAMP 即为 Windows 中 Apache、MySQL 和 PHP 的应用环境
代表为WampServer,官网下载的不是最新版本,到 Sourceforge 下载最新版
安装时没有什么特别的,安装完会问你是否要修改默认查看目录工具和文本编辑工具,均点击否即可
安装完默认是橙色的,单击图标并选择启动所有服务即可:
如果你遇到Apache启动不了的问题,参考最上面准备工作标题下的解决办法,安装完的主页如图所示:
安装完mysql的默认账户为root,密码为空,可以这样修改账户密码:
在WAMP 托盘图标中点击phpmyadmin打开数据库登录界面。
用户名为root,密码不用输,点击执行即可登入数据库;
点击“账户”选项,选中root localhost,点击这一行最右侧的“修改权限”,
选中“修改密码”选项,为root用户设置密码(如果不想将密码加密,不要点击“生成”)
并点击“执行”。提示已修改,说明修改成功。
常见靶场搭建#
常见靶场搭建的都基于phpstudy2018 版和wampserver
常见的靶场有如下:
DVWA#
用 PHP+Mysql 编写的一套用于常规 WEB 漏洞教学和检测的 WEB 脆弱性测试程序。包含了 SQL 注入、XSS、盲注等常见的一些安全漏洞
解压将目录重命名为dvwa,放到phpstudy默认的www目录:
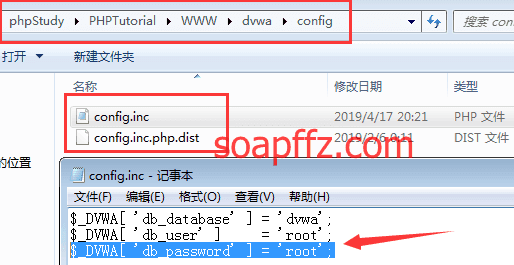
C:\phpStudy\PHPTutorial\WWW\dvwa
下,打开dvwa\config目录,只有一个config.inc.php.dist文件,我们打开复制一份
重命名为config.inc.php
把其中的
$_DVWA[ 'db_password' ]
改为
root(默认为p@ssw0rd)
** 建议将现在修改过的 DVWA 靶机环境打包方便后面存储 **
在地址栏输入ip地址/dvwa即可打开DVWA环境,首次打开是这样的:
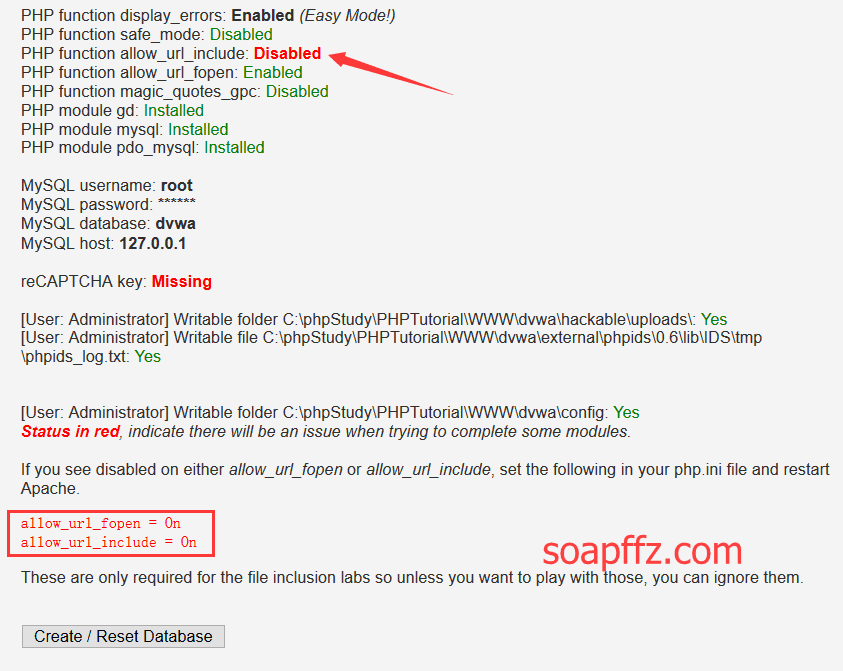
默认phpstudy的allow_url_include参数选项是关闭的,我们手动开启一下 (一般在参数开关最下面一个):
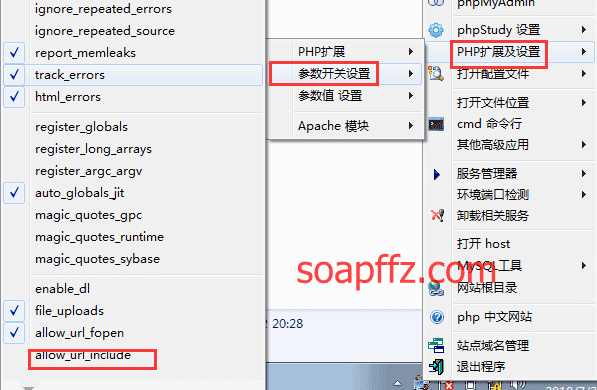
然后直接点击下面Create / Reset Database选项安装完成,等待几秒会自动跳转:

默认用户名为admin,密码为password,就可以进入测试环境了
sqli-labs#
** 注意事项:PHP 版本一定要设置成 7 以下,7 之后的 mysql都改成了 mysql** 了,用 7 以上的都会报错 **
同样放到phpstudy默认的www目录:
C:\phpStudy\PHPTutorial\WWW\dvwa
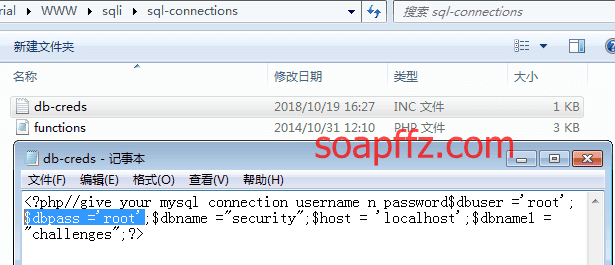
我这里是将目录重命名为了sqli,打开sql-connections/db-creds.inc文件
修改用户和密码,因为 sqli-labs 默认用户名为 root,默认密码为空:
首次使用需要先点击第一个按钮Setup/reset Database for labs安装:
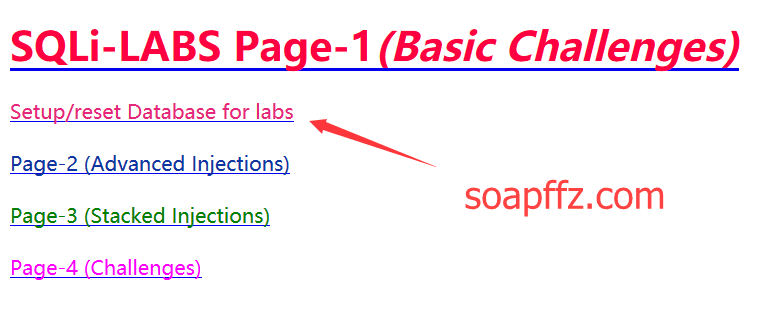
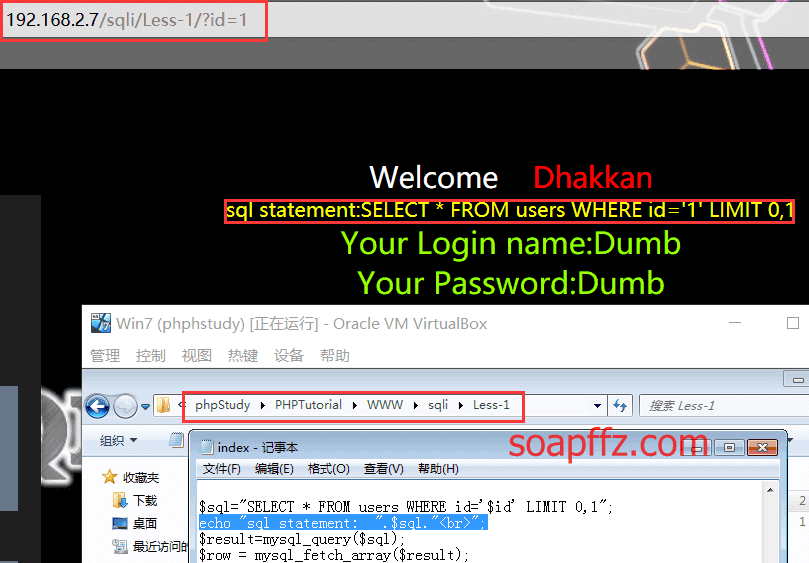
然后就可以使用了,路径为ip/sqli/Less-第几个/
另外为了方便学习查看,可以在源码中的$sql这一行的下一行写入以下 php 语句 (但一般不建议)
就是输出拿到数据库查询的完整语句是怎么样的:
echo "你的 sql 语句是:".$sql."<br>";
permeate#
一个用于渗透透测试演练的 WEB 系统,用于提升寻找网站能力,也可以用于 web 安全教学
中国人开发的,GitHub上介绍两种安装方法:Docker环境和lamp环境
点我下载,我这里就以笔者推荐的wampserver来进行安装
我的安装路径为:E:\wamp64\www\permeate,在httpd.conf最后添加如下代码:
<VirtualHost *:80>
DocumentRoot "E:\wamp64\www\permeate"
ServerName permeate.localhost
<Directory "E:\wamp64\www\permeate">
Options Indexes FollowSymLinks
AllowOverride All
Require all granted
</Directory>
</VirtualHost>
在修改并保存之后,还需要重启 wampserver,让配置文件生效。
新增虚拟主机之后,现在需要修改 hosts 文件,windows 系统 hosts 位置是C:\Windows\System32\drivers\etc\hosts
127.0.0.1 permeate.localhost
首先要确保你的wampserver的mysql的账号密码均为root
如果你默认安装没修改过,参考上面wampserver安装完的密码修改部分
然后打开http://permeate.localhost/install/step1.php
根据引导,数据库账号密码都为root,填写一个管理员账号密码安装即可,然后就可以进入主页了
** 注意,由于自己电脑环境的复杂性,请不要使用 localhost/permeate 这样的路径去安装和访问,很容易出错 **
安装完的主页如图所示:
xss 平台#
经典的 xsser.me#
只要你想搭建xssplatform,这个是肯定逃不掉的,也是最经典的
参考文章:如何搭建自己的 XSS 平台
使用的源码是
wooyun某位大牛利用Bootstrap修改前端代码之后的Xsser.me源代码
界面看起来漂亮多了。并且可以自定义邮件和短信提醒,不用担心不能及时查收食物。
源码下载:链接:http://pan.baidu.com/s/1gfdUYiB 密码:efp1
下载后放在phpstudy的www目录下并重命名为xss
1. 创建数据库
使用phpmyadmin或Navicat for mysql等工具创建一个名为xss的数据库:
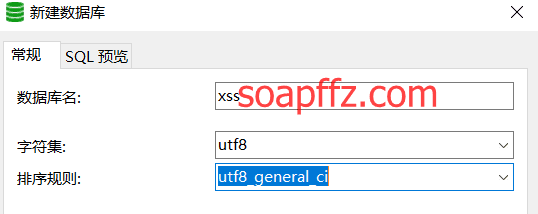
并导入xss目录下的xssplatform.sql
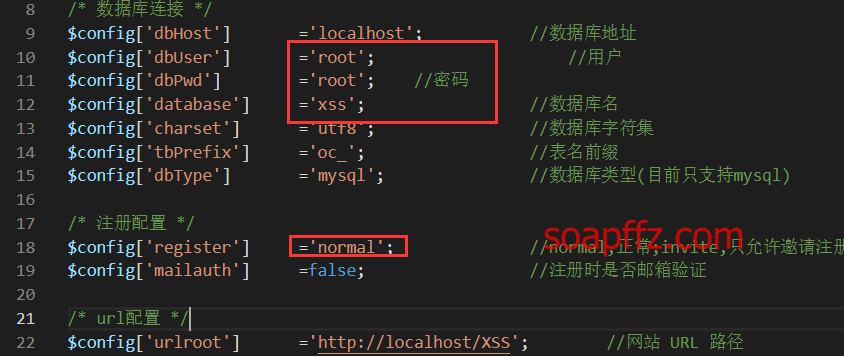
2. 安装前配置
修改config.php中的数据库连接字段,包括用户名、密码和数据库名,访问 xss 平台的 URL 地址,
并先将注册配置设为normal,在自己注册一个之后再改为invite
将authest.php中的网址代码替换为自己的 URL (如果你也是本地使用就不用改):
如果安装在虚拟机,在物理机中使用就改为虚拟机的 ip
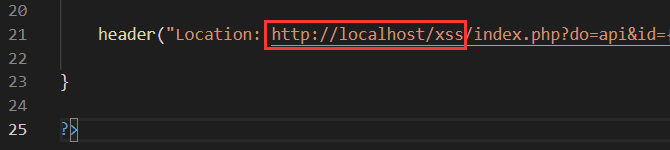
在 phpmyadmin (或者 Navicat) 执行以下 SQL 命令,将数据库中原有的 URL 地址修改为自己使用的 URL:
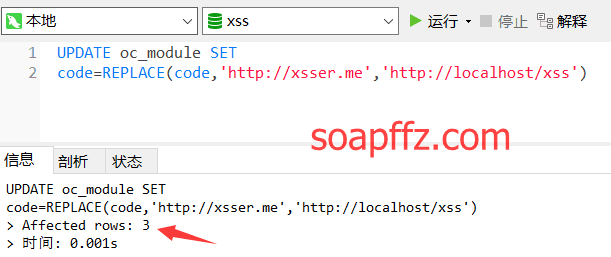
UPDATE oc_module SET
code=REPLACE(code,'http://xsser.me','http://localhost/xss')
3. 注册用户
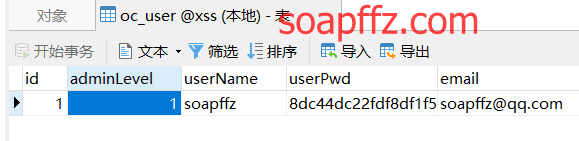
重启下phpstudy,登录http://localhost/xss,注册用户,然后在 phpmyadmin (或 Navicat) 里
选择 oc_user,将注册用户的 adminlevel 改为 1:
重启下mysql即可使用
另外很多文章里面都配置了伪静态,伪静态只是为了防止你放到公网上的时候暴露自己的 IP 地址,
如果你只是自己使用,不分享给别人,那就没必要配置伪静态了
Metasploitable3#
官方 GitHub 地址 (有英文安装文档),使用教程建议参考:
即刻安全的Demon制作的教程:年终福利大放送!!Metasploitable 3 最新实战渗透教程(附 PPT)
Metasploitable 属于一个虚拟靶机系统,里面含有大量未被修复的安全漏洞。安全人员可以利用 Metasploit 对 Metasploitable 进行漏洞挖掘,漏洞演示,网络开发,软件测试,技术工作访谈,销售演示还有 CTF 比赛等。
2016 年 11 月,Rapid 7 社区发布了 Metasploitable 3 虚拟系统,与 Metasploitable 2 相比,这次 Metasploitable 3 的发布隔了数年之久。Metasploitable 3 的发布与以往有些不同,就是 Rapid 7 社区开放了一个全球性 CTF 大赛!!!对,你没听错,Rapid 7 举办了一个全球性的 CTF 大赛来衬托 Metasploitable 3 的发布,任何人都可以参加!在一个月内,谁能从 Metasploitable 3 虚拟系统中拿到的 flag 最多,谁就能获奖。
Metasploitable 3不是像之前的版本那样直接下载虚拟机,而是给了两个安装脚本:
build_win2008.sh、build_win2008.ps1,可以分别在Linux和Windows下面建立的Metasploitable 3镜像。
WeBug#
官网被黑了 @(滑稽),GitHub 地址提供的百度云盘链接也挂了
参考文章: