前言#
资产扫描包括如下内容:扫描子域名和扫描 C 段和旁站
旁站:同服务器不同站点
C 段:同网段不同服务器
扫描子域名#
经典的搜索引擎#
这个我在上一篇文章中已经说过,直接site:xx.com即可:

但是,正如图中所见,比较大的企业的子域名都是成百上千的,用搜索引擎来收集子域名会累死的
此方法仅对小站点有效,故衍生出了子域名查询工具和网站 (但大部分本质都是通过字典去 “碰运气” 的)
域名注册人反查#
一般大企业都是用企业邮箱注册大批量的二级域名,那么我们直接用企业邮箱反查即可
使用站长whois进行查询:http://whois.chinaz.com:
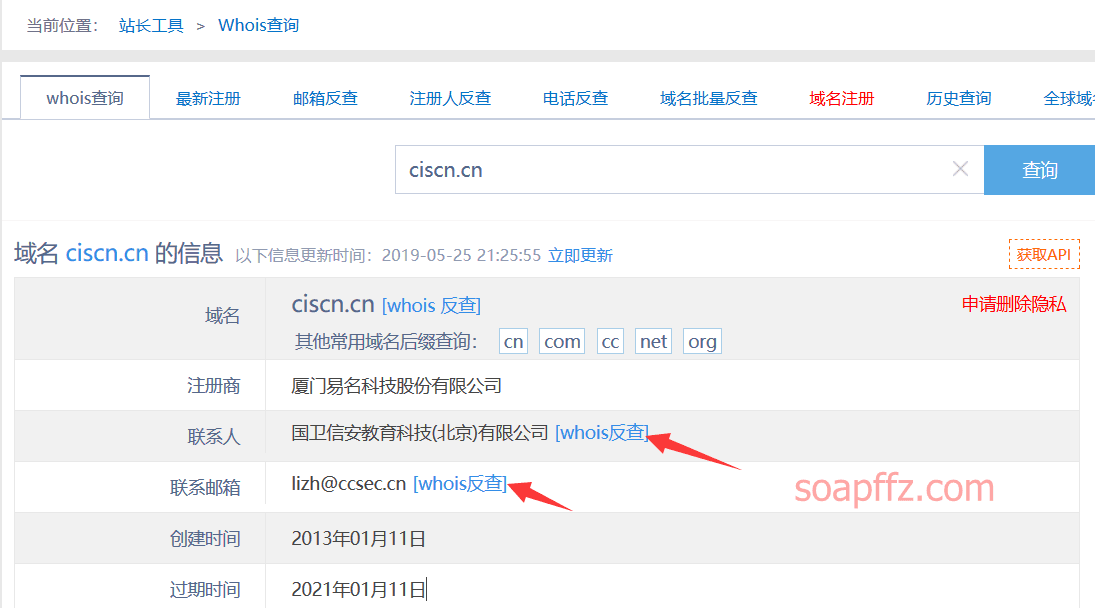
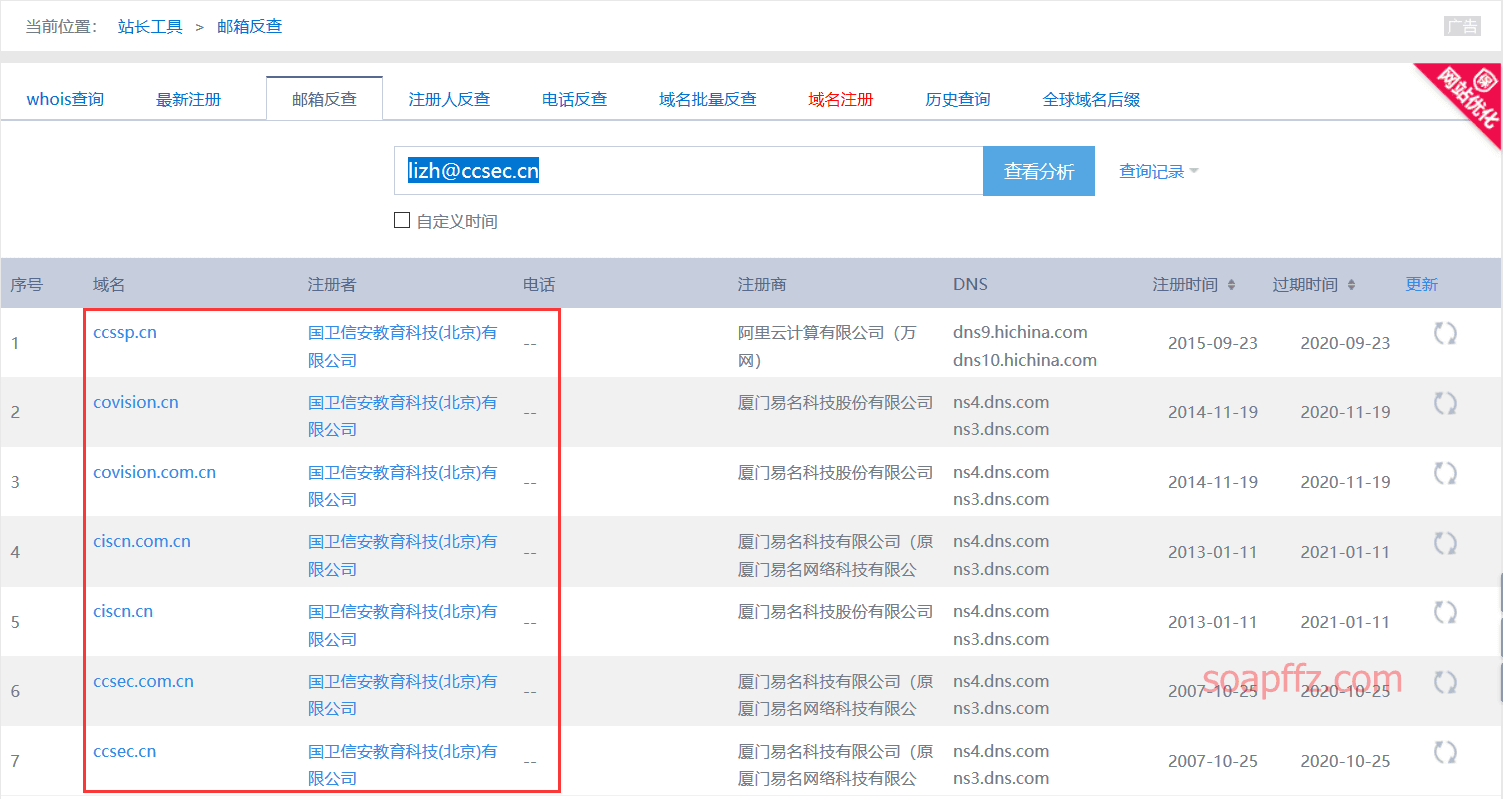
也可以使用云悉资产扫描先扫描一下网站基本信息再去whois反查:


也可以先查询网站的备案信息再去whois反查:
在线查询网站#
phpinfo.me大佬的在线子域名查询:https://phpinfo.me/domain/

子成君大佬的在线子域名查询:http://z.zcjun.com/
另外体验了某 (CYWL.TEAM 后面记得删掉) 团队出的子域名扫描网站
- 注册必须要数字型 QQ 邮箱
- 关注微信公众号获取注册码
- 新账号有 6 分,每个网站扫描消耗一分,用完需用人民币购买,1 块一分
::quyin:heng::
告辞!
几个子域名扫描工具和脚本#
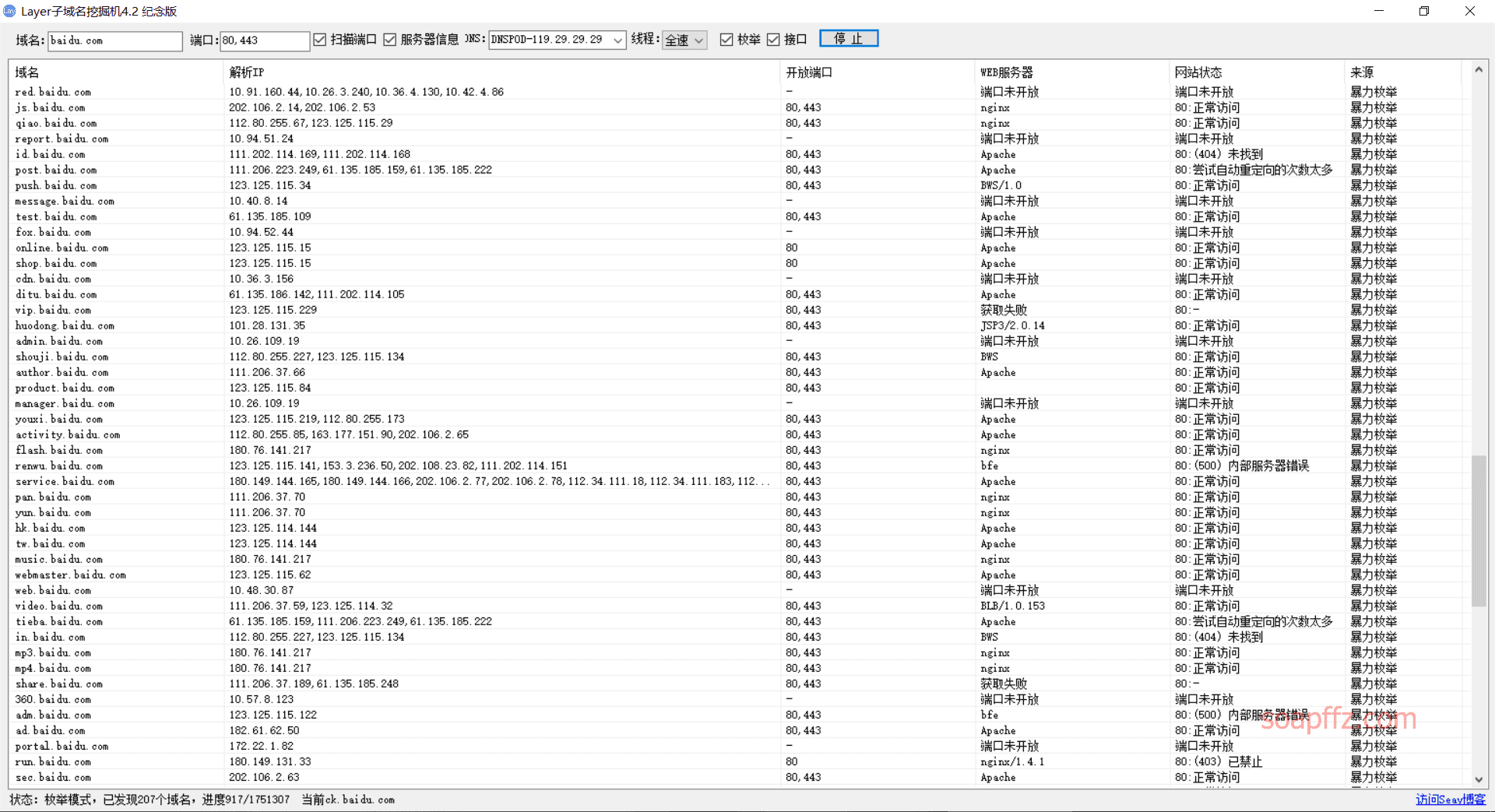
layer 子域名挖掘机#
seay大佬用c#写的子域名挖掘机
seay大佬写的另外一个工具Seay源代码审计系统也很厉害,后面如果讲到代码审计也会提到这个工具,但是这大佬的博客目前打不开了。。
layer 子域名挖掘机在网上只能找到4.2版本的网盘下载地址:https://pan.baidu.com/s/1o8qAKYm
subDomainsBrute#
lijiejie大佬写的子域名收集工具,最近一次更新是在 2019-05-19,GitHub 地址
源码下载下来是python文件,环境为Python2,需要安装一个包:
pip install dnspython gevent
使用教程如下:


相信上面的这些已经够我们使用了,其他还有几个域名扫描工具就不一一测试了:
- 猪猪侠:https://github.com/ring04h/wydomain
- 子域名枚举与地图标记:https://github.com/le4f/dnsmaper
- 高效精准的子域名爆破工具:https://github.com/TheRook/subbrute
扫描 C 段 / 旁站#
在线扫描网站#
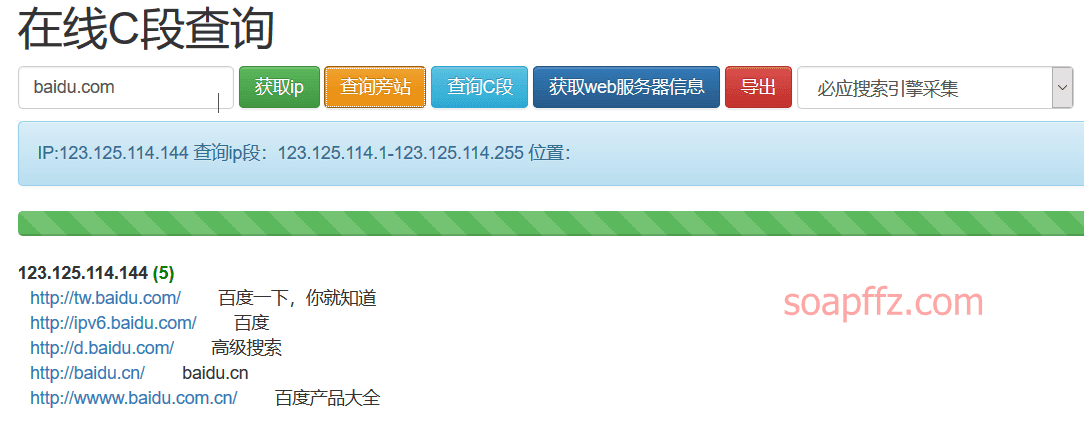
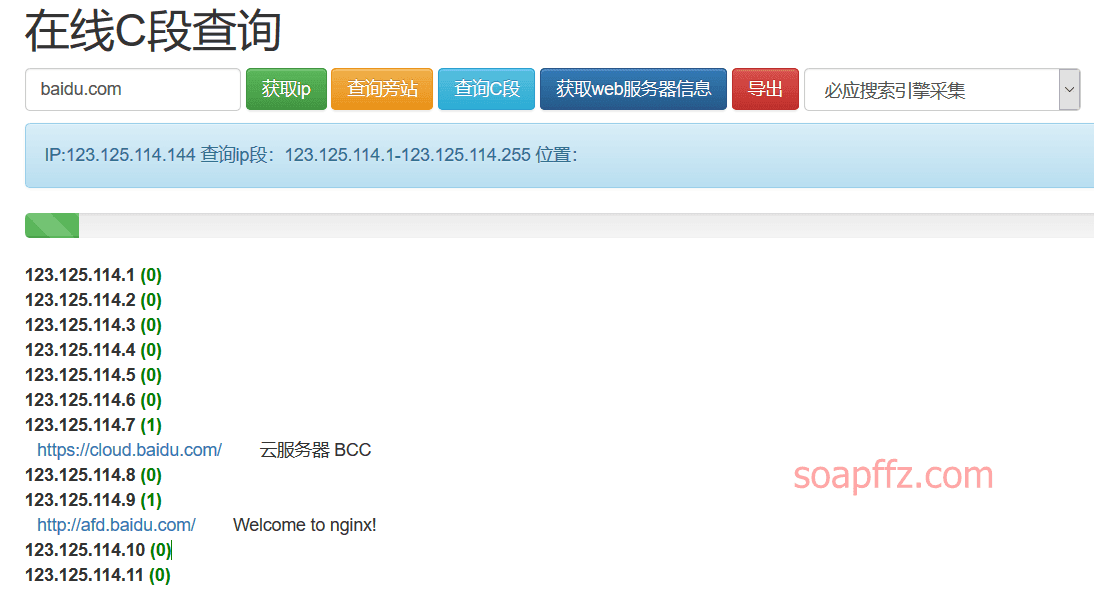
phpinfo.me除了子域名,也搞 C 段 / 旁站:https://phpinfo.me/bing.php
查询旁站:
查询 C 段:
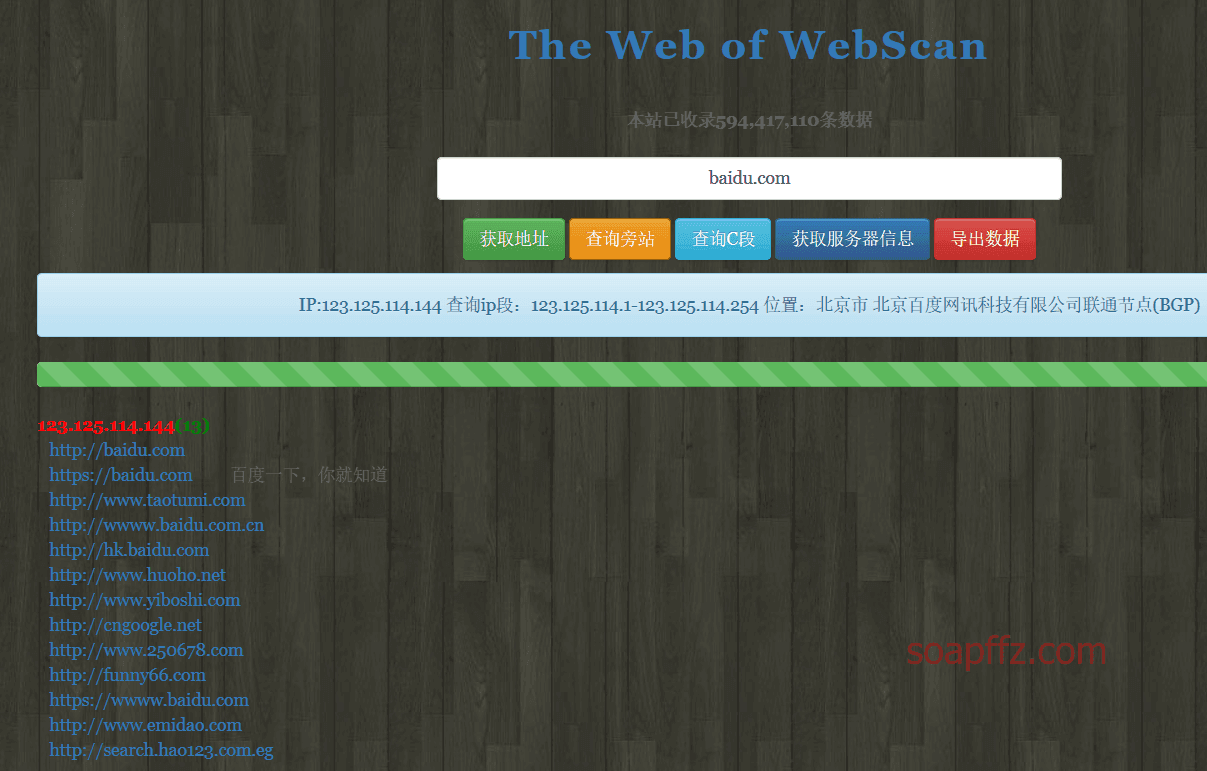
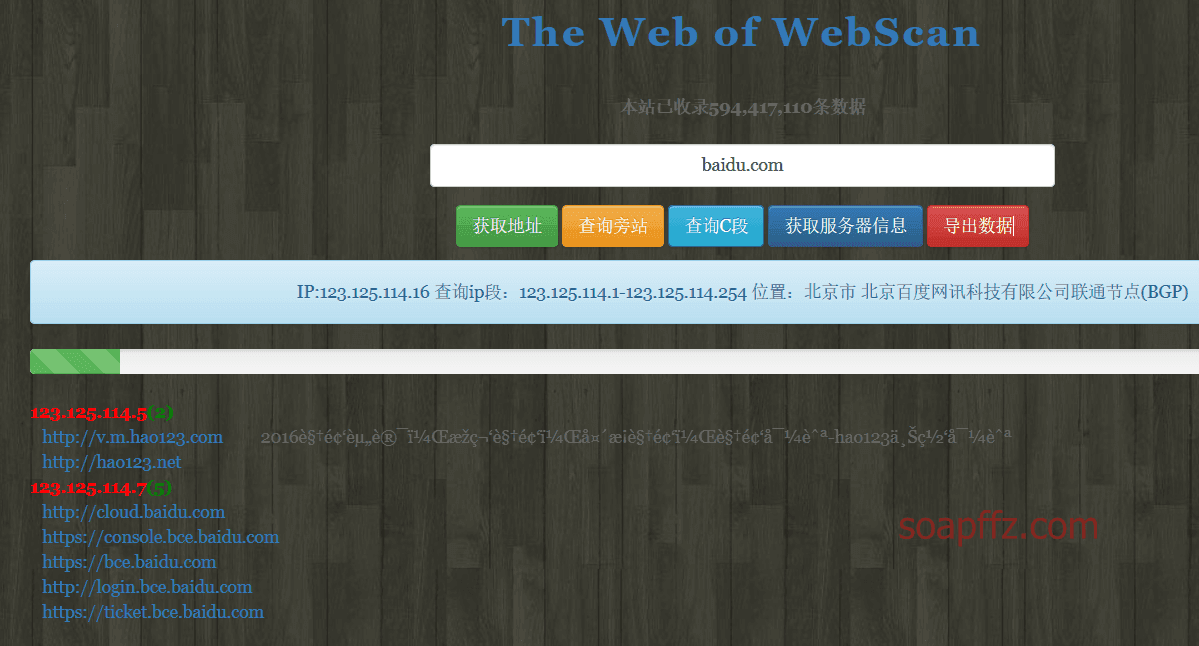
0x4i大佬的网站:http://www.webscan.cc/
查询旁站:
查询 C 段:
扫描工具#
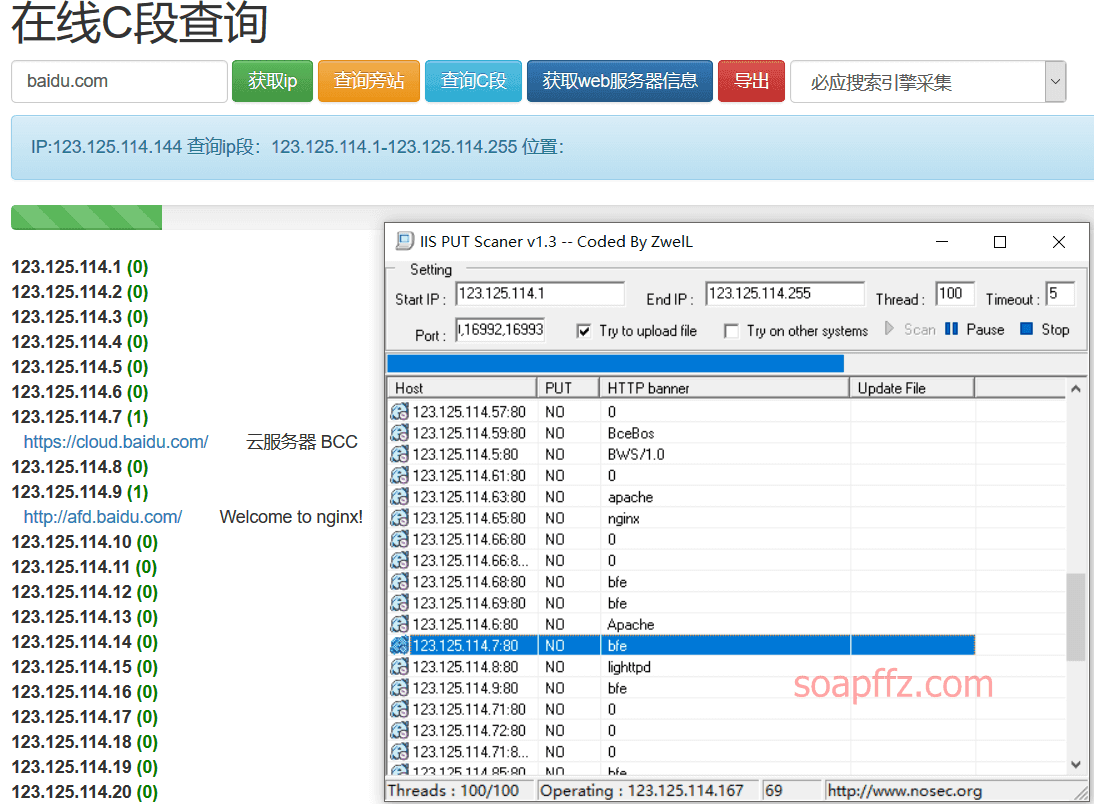
IIS PUT Scaner#
和在线扫描网站一起扫描了一下,效果似乎不是太理想:
K8Cscan#
K8Team 出品,截至写这篇文章时,这个工具最后更新时间为2019-05-06
详细介绍:https://www.cnblogs.com/k8gege/p/10519321.html
这个工具可配合插件使用:
插件教程:
插件9: Weblogic漏洞扫描&GetShell Exploit
https://www.cnblogs.com/k8gege/p/10779728.html
插件8:K8Cscan插件之Cisco思科设备扫描
https://www.cnblogs.com/k8gege/p/10679491.html
插件7: K8Cscan插件之多种方式操作系统版本探测
https://www.cnblogs.com/k8gege/p/10673707.html
插件6: K8Cscan插件之Wmi爆破Windows密码
https://www.cnblogs.com/k8gege/p/10650659.html
插件5: K8Cscan插件之Mysql密码爆破
https://www.cnblogs.com/k8gege/p/10650642.html
插件4: K8Cscan插件之FTP密码爆破
https://www.cnblogs.com/k8gege/p/10650630.html
插件3: K8Cscan新增C段旁站扫描插件\子域名扫描插件
https://www.cnblogs.com/k8gege/p/10626465.html
插件2: 调用c#编写的DLL扫描内网WEB主机Banner以及标题
DLL源码 https://www.cnblogs.com/k8gege/p/10519512.html
已编译:https://www.cnblogs.com/k8gege/p/10650610.html
插件1: 配置Cscan.ini 调用外部程序S扫描器扫描C段主机开放端口
配置Cscan.ini
[Cscan]
exe=s.exe
arg=TCP $ip$ 21,80,3306,3389,1521
命令行下执行cscan
姿势太多,后面用到再现学现卖
K8Cscan 下载地址:
https://github.com/k8gege/K8tools/blob/master/K8Cscan%203.8.rar
解压密码:k8gege
nmap#
此部分只简单介绍nmap的主机解析部分,nmap的详细介绍到端口扫描那篇去看。
nmap 主机发现部分主要有如下参数:
-Pn 将所有指定的主机视为已开启状态,跳过主机发现过程
-PS TCP SYN ping,发送一个设置了SYN标志位的空TCP报文,默认端口为80,也可指定端口
-PA TCP ACK ping,发送一个设置了ACK标志位的空TCP报文,默认端口为80,也可指定端口
-PU UDP ping,发送一个空的UDP报文到指定端口,可穿透只过滤TCP的防火墙
-PR 使用ARP ping
扫描主机用到的-Px和扫描端口用到的-sx基本是一样的功能:
此处我们想要实现以最快速度最全面的扫描指定 C 段内的所有存活主机但是不扫描端口:
nmap -v -sn -Pn -PS -n 47.95.47.1/24


参考文章:
本文完。