Preface#
Asset scanning includes the following contents: scanning subdomains and scanning C segments and adjacent sites.
Adjacent sites: Different sites on the same server.
C segment: Different servers on the same network segment.
Scanning Subdomains#
Classic Search Engines#
As I mentioned in the previous article, you can directly use site:xx.com:
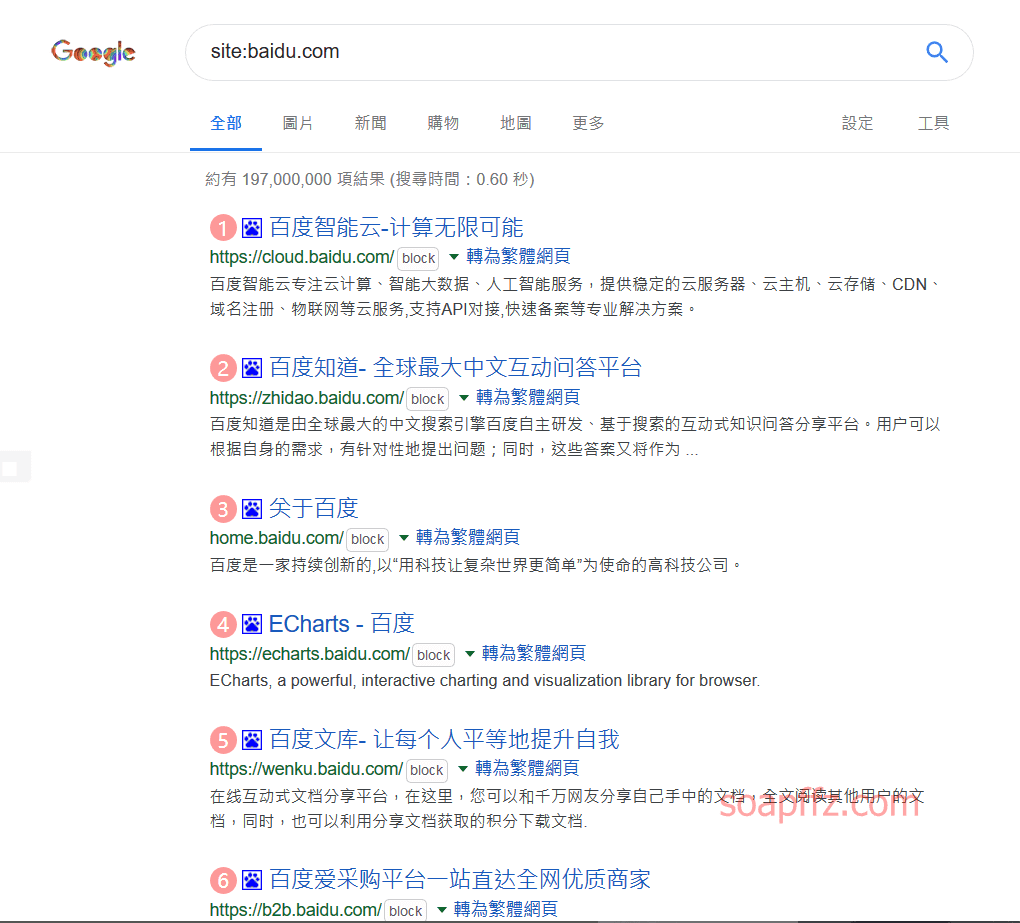
However, as seen in the figure, larger enterprises have hundreds or thousands of subdomains, and it is exhausting to collect subdomains using search engines.
This method is only effective for small websites, so subdomain query tools and websites have been derived (but most of them are essentially "lucky" guesses using dictionaries).
Domain Registrant Reverse Lookup#
Generally, large enterprises use corporate email addresses to register large numbers of second-level domains, so we can directly use corporate email reverse lookup.
Use 站长whois for query: http://whois.chinaz.com:
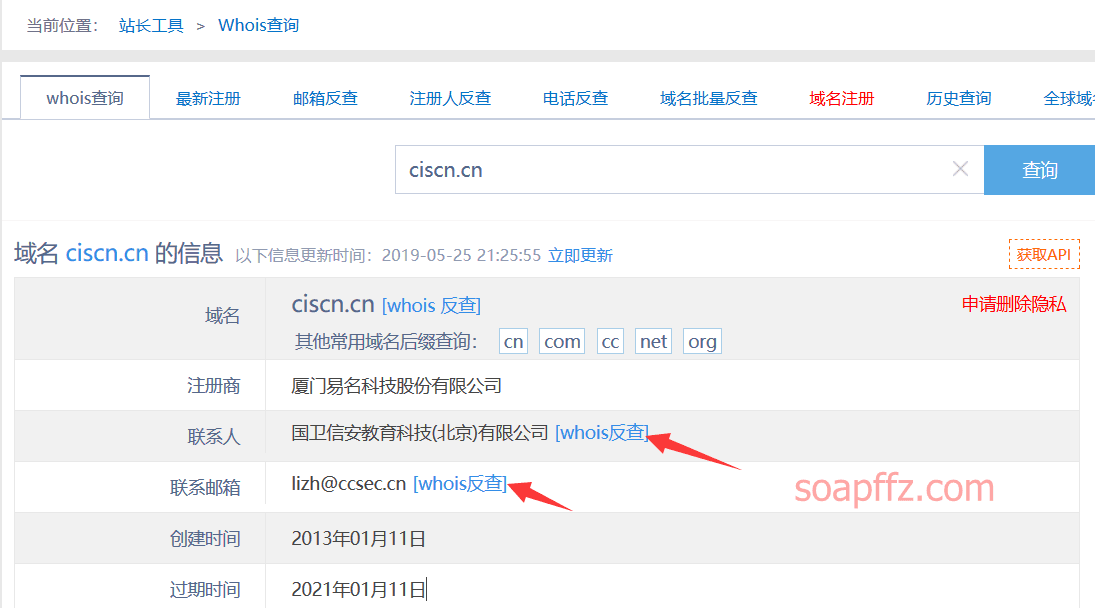
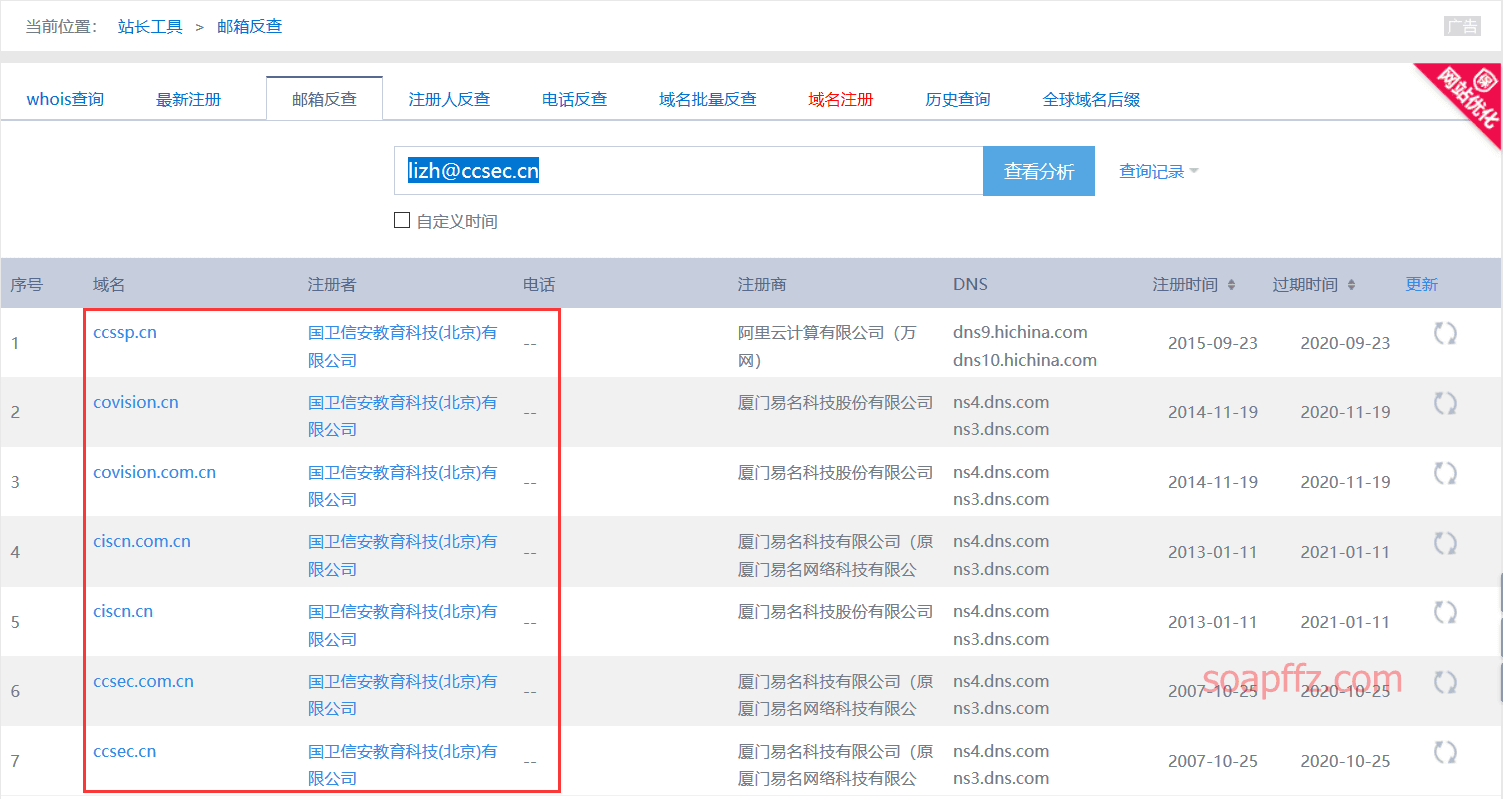
You can also use Yunxi Asset Scanning to scan the basic information of the website before performing a whois reverse lookup:
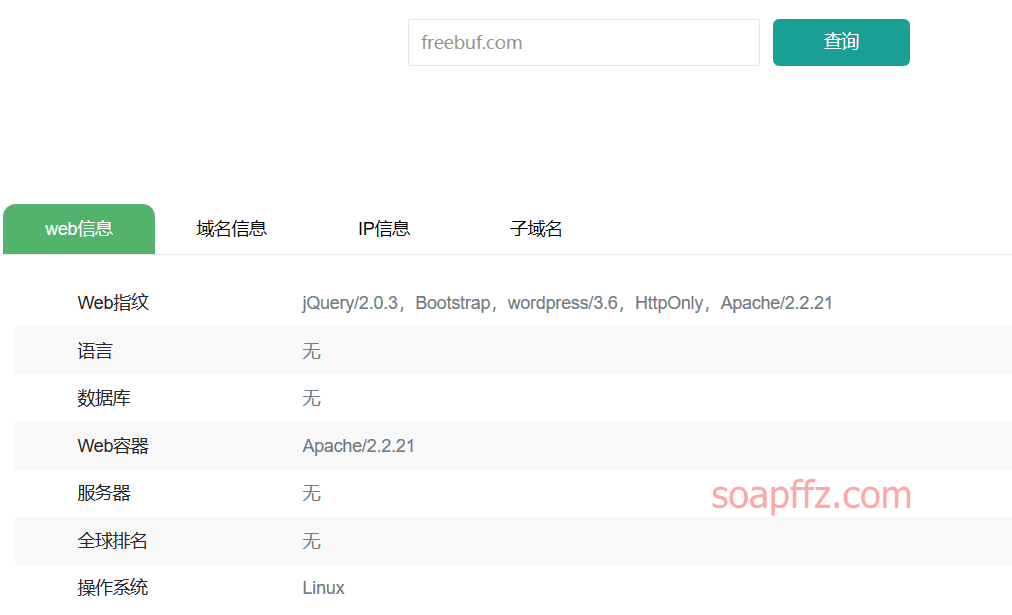
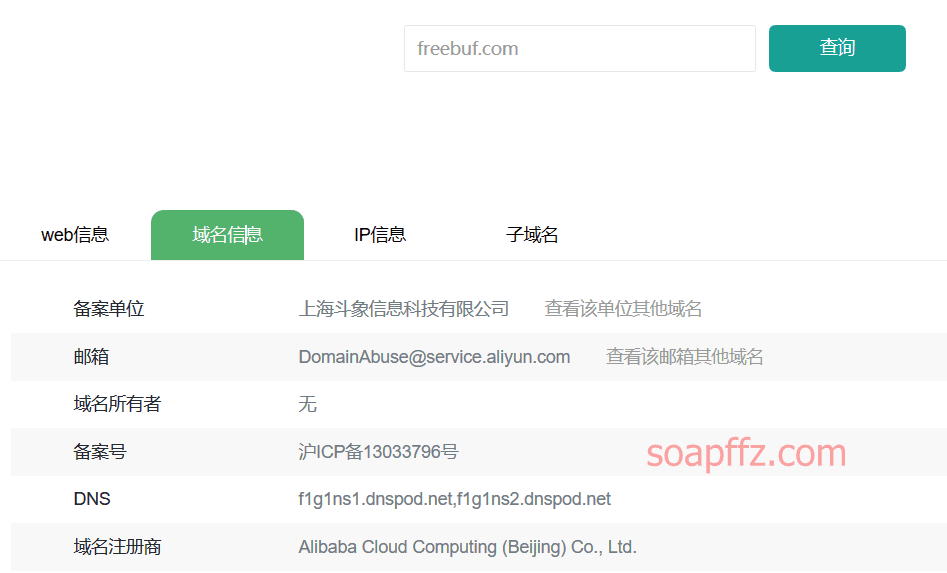
You can also check the filing information of the website before performing a whois reverse lookup:
Public network security information query
Online Query Websites#
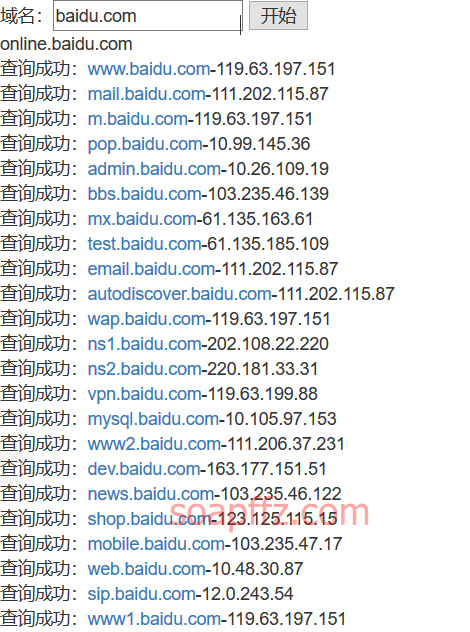
Online subdomain query by phpinfo.me: https://phpinfo.me/domain/
Online subdomain query by zichengjun: http://z.zcjun.com/
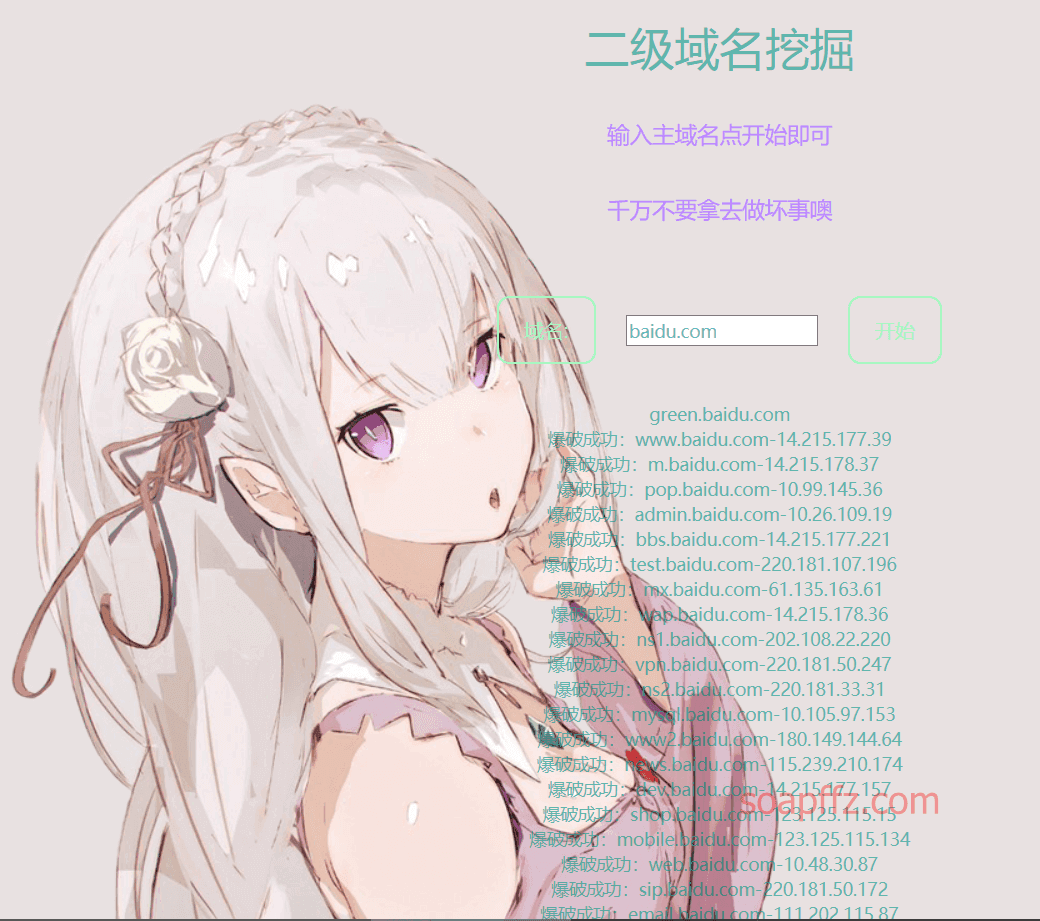
In addition, I experienced a subdomain scanning website developed by a certain (CYWL.TEAM remember to delete later) team.
- Registration requires a numeric QQ email address.
- Follow the WeChat public account to obtain the registration code.
- New accounts have 6 points, and each website scan consumes one point. After using up, you need to purchase with RMB, 1 RMB for one point.
::quyin:heng::
Goodbye!
Several Subdomain Scanning Tools and Scripts#
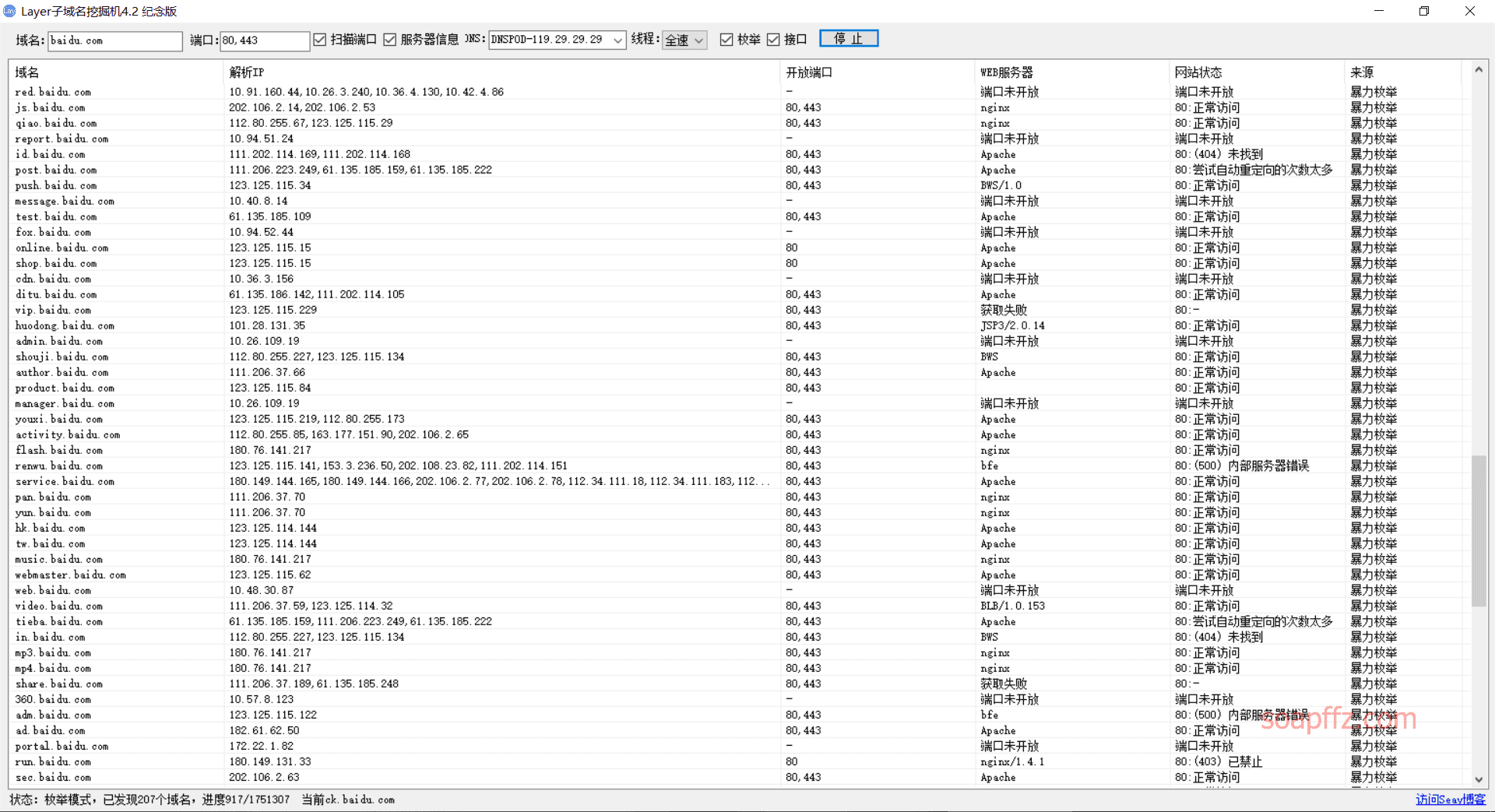
Layer Subdomain Miner#
A subdomain miner written by seay using c#.
Another tool written by seay, Seay Source Code Audit System, is also very powerful. If we talk about code auditing later, we will also mention this tool, but this blogger's blog is currently not accessible...
The Layer Subdomain Miner can only find the download address of version 4.2 on the Internet: https://pan.baidu.com/s/1o8qAKYm
subDomainsBrute#
A subdomain collection tool written by lijiejie. The last update was on 2019-05-19. GitHub address
The downloaded source code is a python file, and the environment is Python2, which requires the installation of a package:
pip install dnspython gevent
The usage tutorial is as follows:
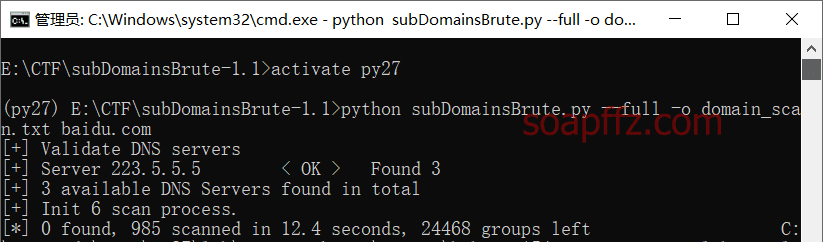
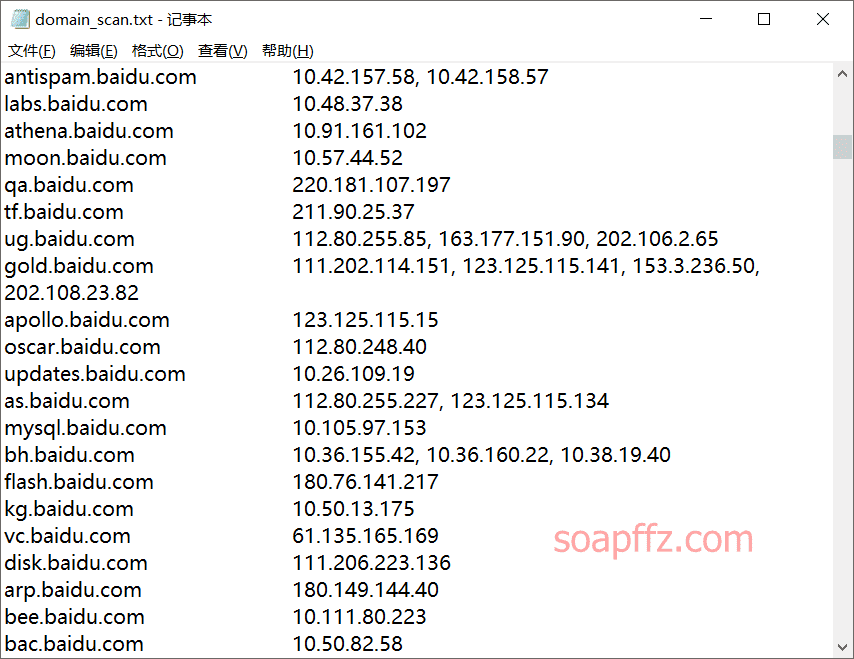
I believe the above tools are enough for our use. There are several other domain scanning tools that will not be tested one by one:
- Piggy: https://github.com/ring04h/wydomain
- Subdomain enumeration and mapping: https://github.com/le4f/dnsmaper
- Efficient and accurate subdomain brute force tool: https://github.com/TheRook/subbrute
Scanning C Segments/Adjacent Sites#
Online Scanning Websites#
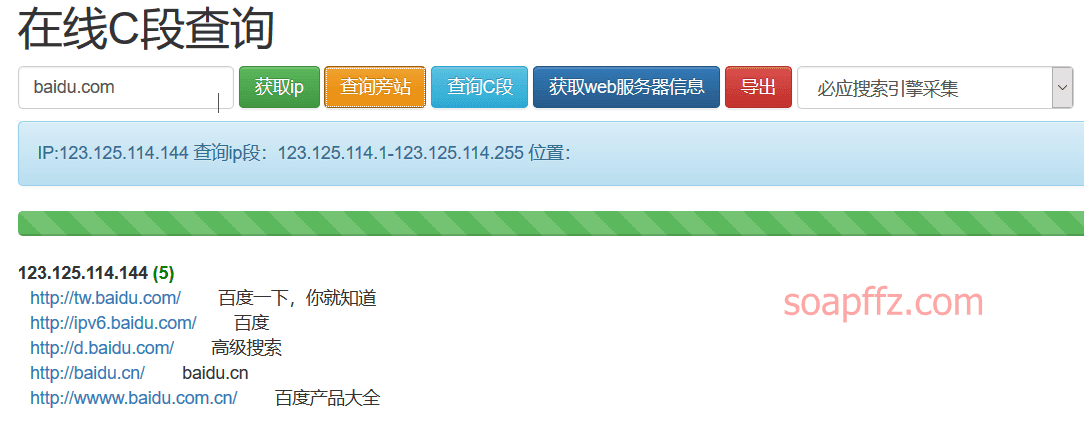
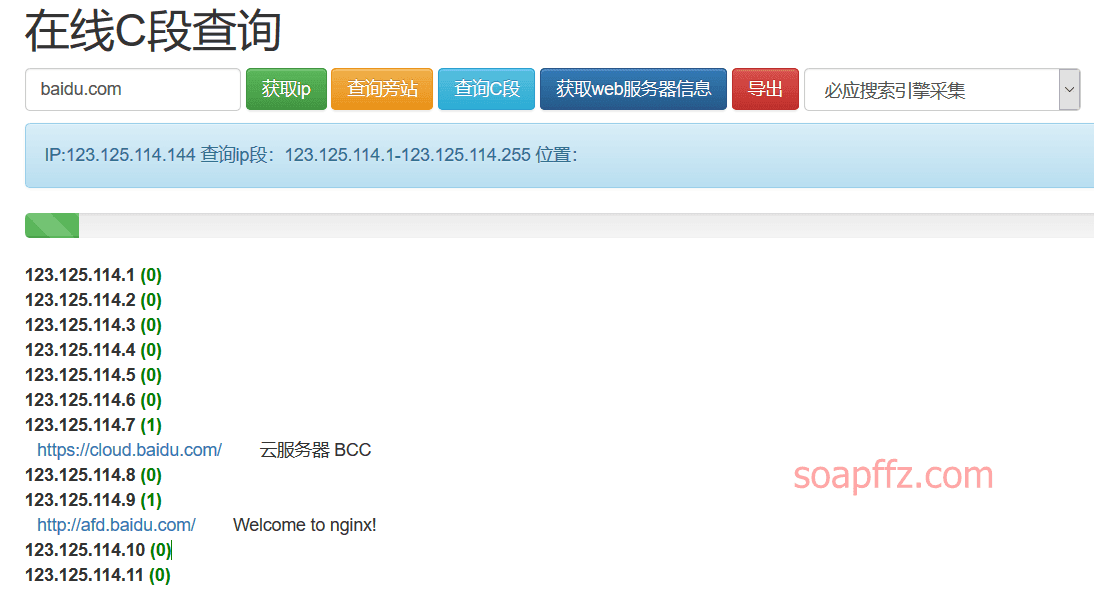
phpinfo.me also scans C segments/adjacent sites in addition to subdomains: https://phpinfo.me/bing.php
Query adjacent sites:
Query C segments:
Website of 0x4i: http://www.webscan.cc/
Query adjacent sites:
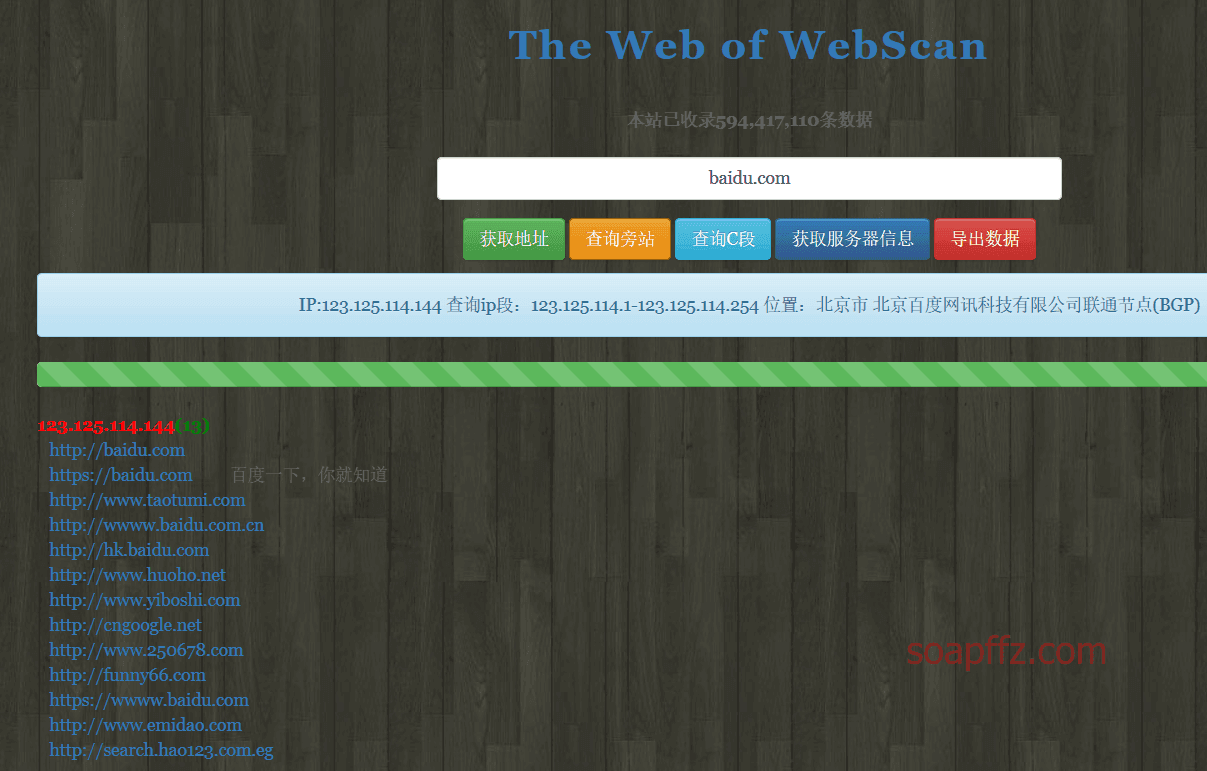
Query C segments:
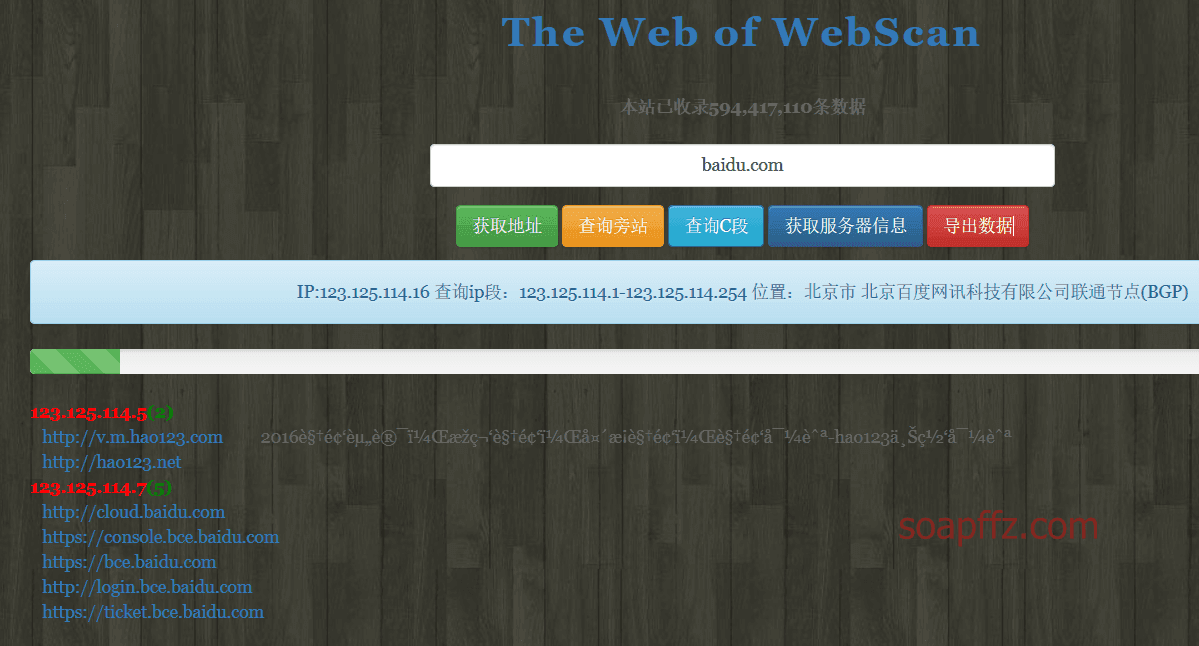
Scanning Tools#
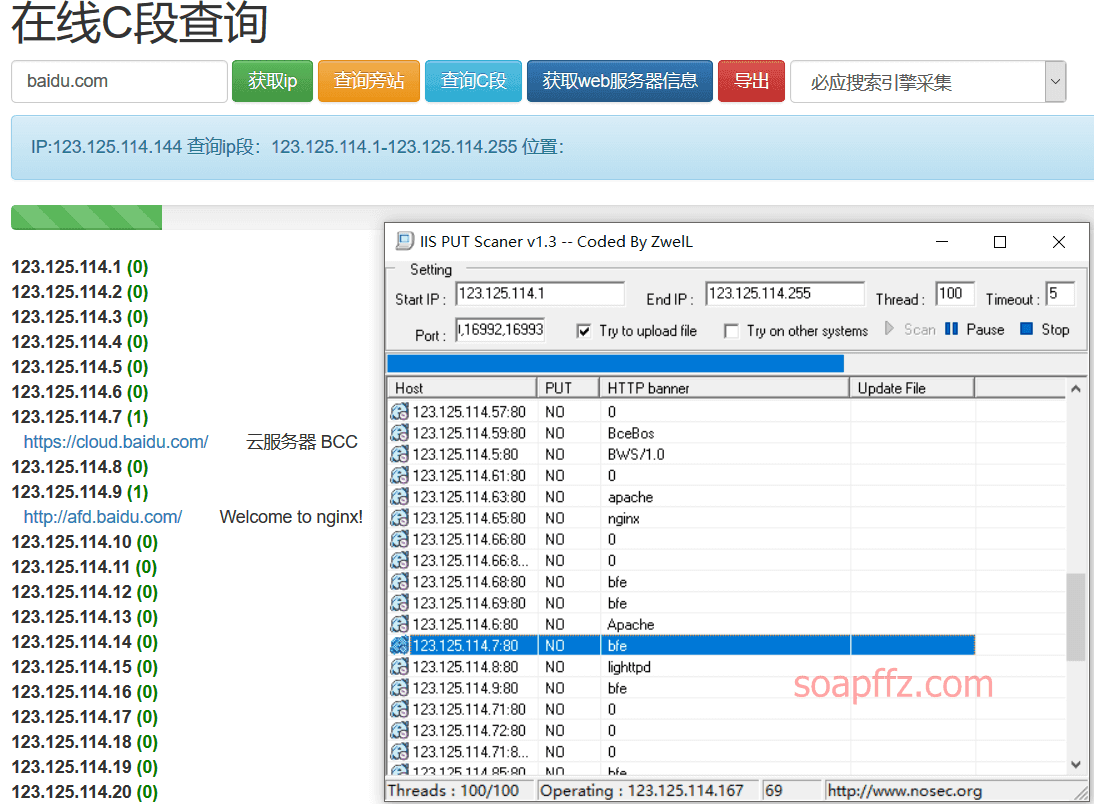
IIS PUT Scanner#
Scanned together with online scanning websites, the effect seems not ideal:
K8Cscan#
Produced by K8Team, as of writing this article, the last update time of this tool is 2019-05-06.
Detailed introduction: https://www.cnblogs.com/k8gege/p/10519321.html
This tool can be used with plugins:
Plugin tutorial:
Plugin 9: Weblogic vulnerability scanning & GetShell Exploit
https://www.cnblogs.com/k8gege/p/10779728.html
Plugin 8: K8Cscan plugin for Cisco devices scanning
https://www.cnblogs.com/k8gege/p/10679491.html
Plugin 7: K8Cscan plugin for detecting various operating system versions using multiple methods
https://www.cnblogs.com/k8gege/p/10673707.html
Plugin 6: K8Cscan plugin for Wmi brute-forcing Windows passwords
https://www.cnblogs.com/k8gege/p/10650659.html
Plugin 5: K8Cscan plugin for Mysql password brute-forcing
https://www.cnblogs.com/k8gege/p/10650642.html
Plugin 4: K8Cscan plugin for FTP password brute-forcing
https://www.cnblogs.com/k8gege/p/10650630.html
Plugin 3: K8Cscan plugin for scanning adjacent sites in C segments and subdomains
https://www.cnblogs.com/k8gege/p/10626465.html
Plugin 2: Call DLL written in c# to scan the banner and title of intranet WEB hosts
DLL source code: https://www.cnblogs.com/k8gege/p/10519512.html
Compiled version: https://www.cnblogs.com/k8gege/p/10650610.html
Plugin 1: Configure Cscan.ini to call an external program S scanner to scan open ports of C segment hosts
Configure Cscan.ini
[Cscan]
exe=s.exe
arg=TCP $ip$ 21,80,3306,3389,1521
Execute cscan on the command line
There are too many methods, I will learn and sell them later when I need them.
K8Cscan download address:
https://github.com/k8gege/K8tools/blob/master/K8Cscan%203.8.rar
Decompression password: k8gege
nmap#
This section only briefly introduces the host resolution part of nmap. For a detailed introduction to nmap, please refer to the article on port scanning.
The main parameters for host discovery in nmap are as follows:
-Pn Treat all specified hosts as online, skip host discovery
-PS TCP SYN ping, sends an empty TCP packet with the SYN flag set, default port is 80, can also specify the port
-PA TCP ACK ping, sends an empty TCP packet with the ACK flag set, default port is 80, can also specify the port
-PU UDP ping, sends an empty UDP packet to the specified port, can penetrate firewalls that only filter TCP
-PR Use ARP ping
The -Px used for scanning hosts and the -sx used for scanning ports are basically the same:
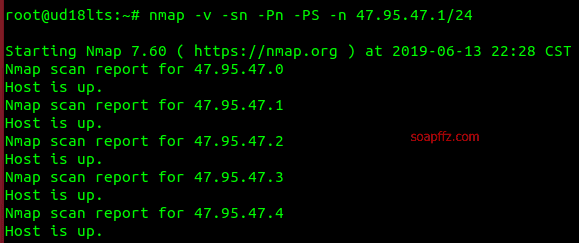
Here we want to achieve the fastest and most comprehensive scanning of all live hosts in the specified C segment without scanning ports:
nmap -v -sn -Pn -PS -n 47.95.47.1/24
Reference articles:
End of this article.