Introduction#
Information gathering is the core of penetration testing, and having comprehensive information about the target is crucial for successful penetration.
Using search engines is the most convenient method for collecting information that we can access in our daily lives.
In addition to the common Google advanced search syntax, this article also introduces network asset scanning engines such as Shodan and ZoomEye.
Google Advanced Search Syntax#
In addition to searching by keywords, the search engines we use in our daily lives also have various "hidden" search syntaxes. Let's briefly introduce them:
| Syntax | Description | Example |
|---|---|---|
| site | Search within a specific website | windows Markdown software site.com |
| inurl | Search for web pages with URLs containing the keyword, such as admin.php, login.php, etc. | Vocational Technical College inurl.php |
| intext | Search for keywords in the body of web pages, such as chess, Macau, etc. | intext New Lisboa |
| intitle | Search for keywords in the titles of web pages, such as management systems, etc. | intitle Management System |
| filetype | Search for files with the specified keyword as the file type, such as php, etc. | Management system usage document filetype |
| link | Search for pages with links containing the keyword | link.com |
Okay, we've finished introducing the basic syntax. Now let's talk about some "combinations":
Name Student ID ID Card Number Contact Number filetype:xlsx inurl:edu.cn
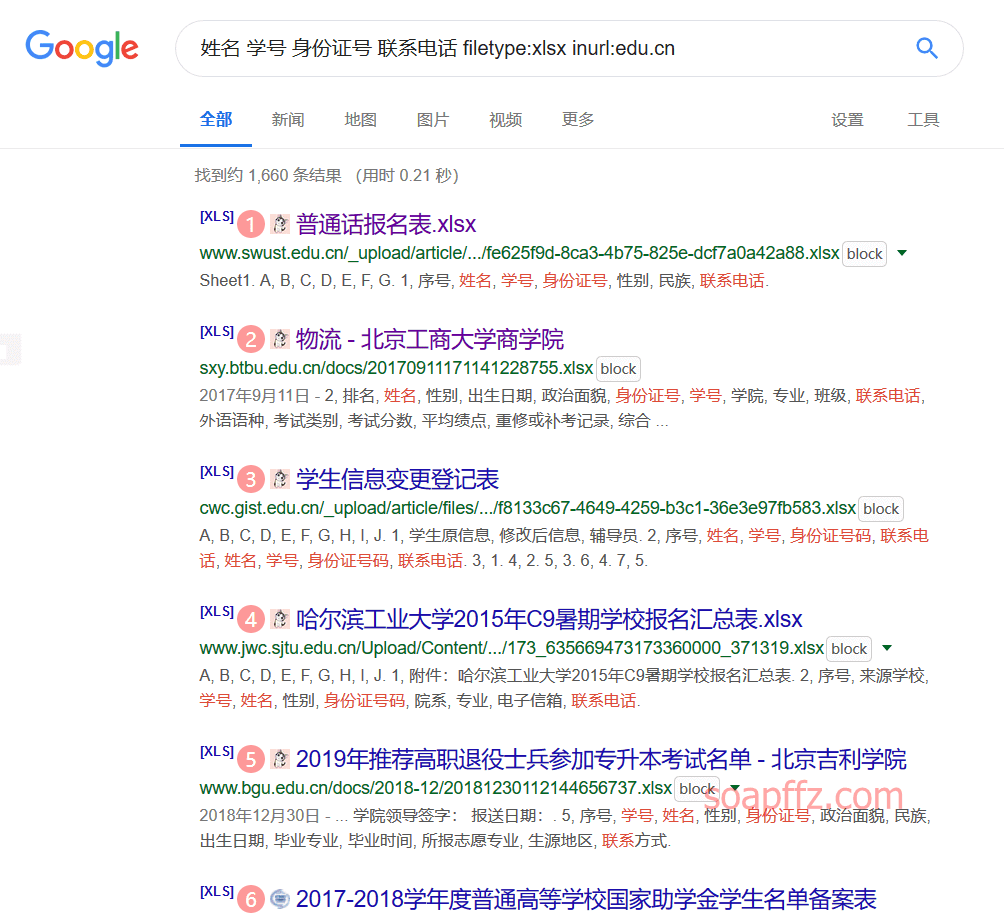
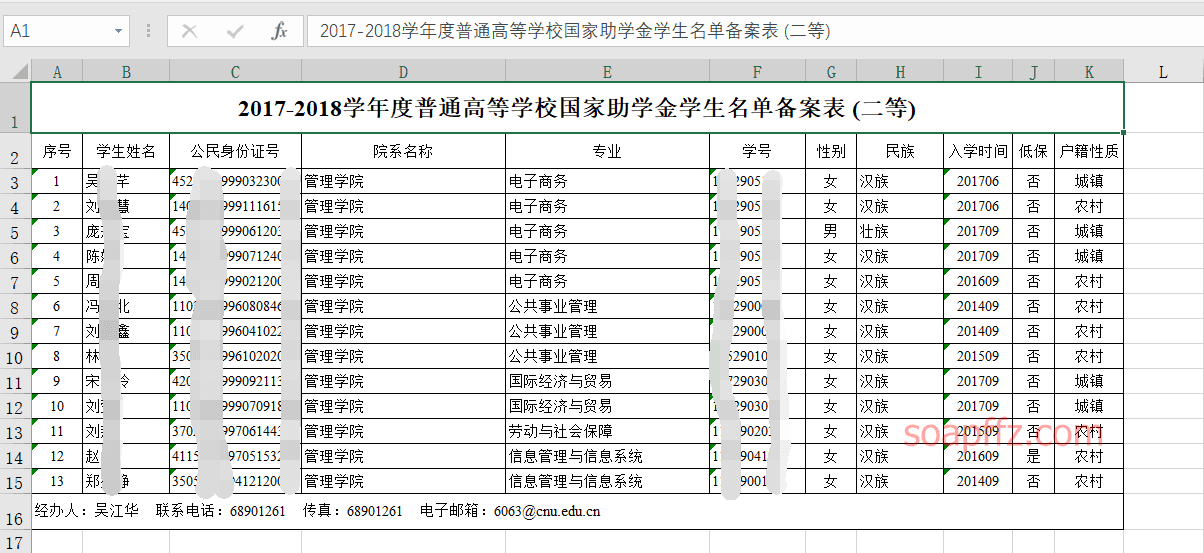
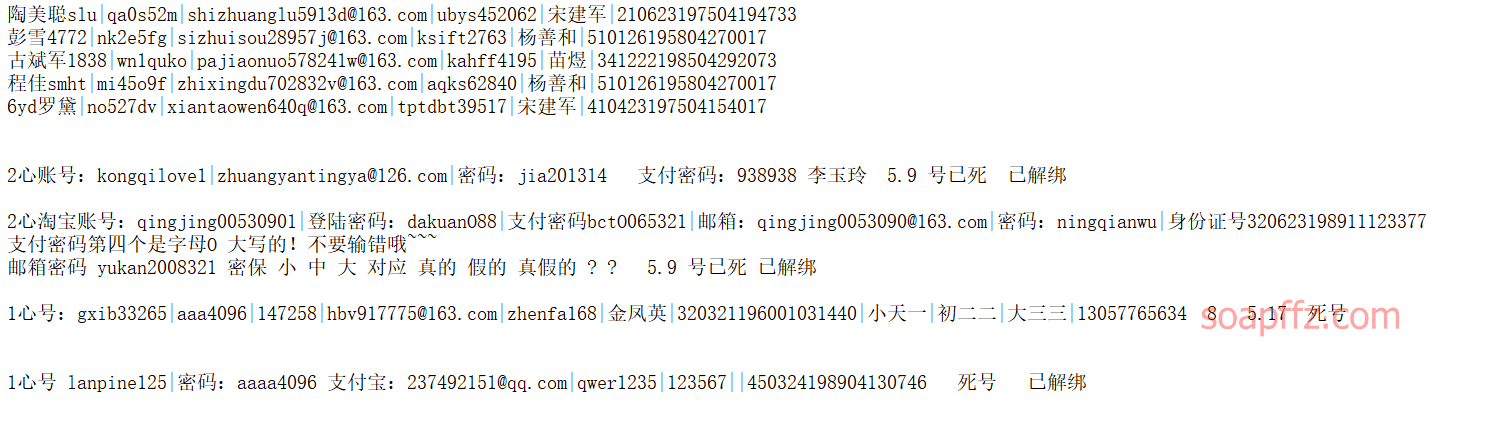
Password filetype:txt inurl:New Text Document
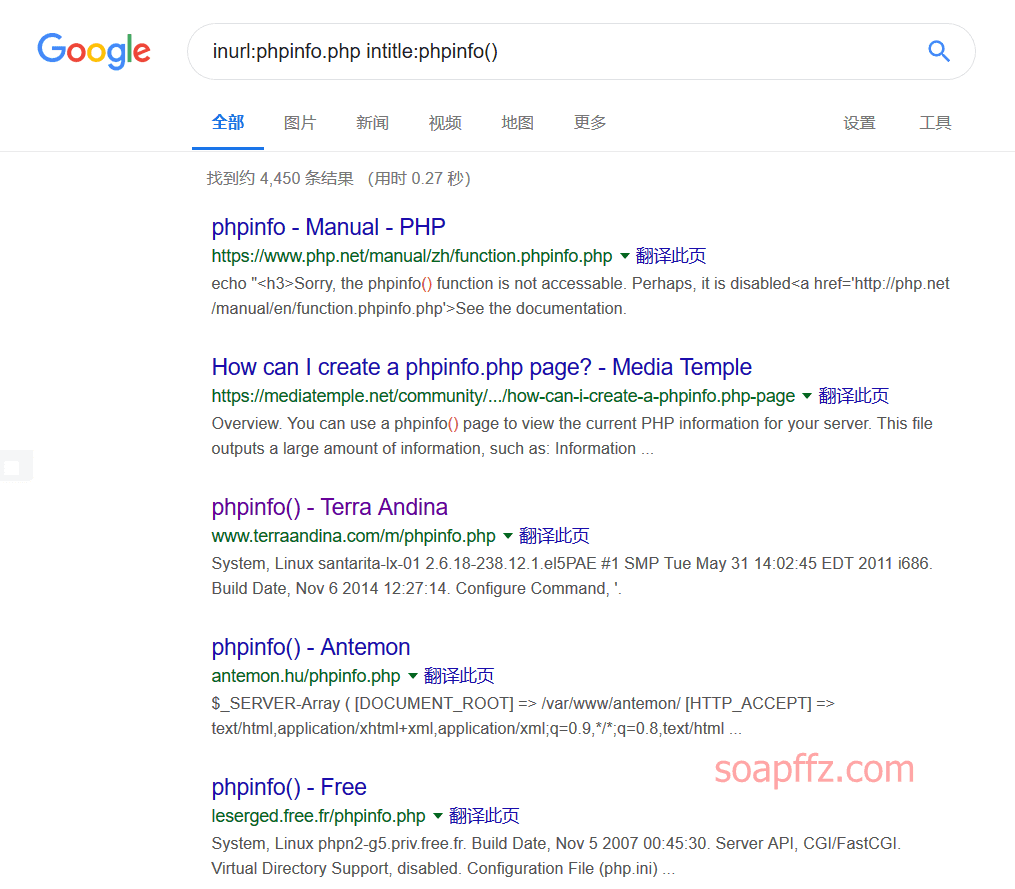
inurl:phpinfo.php intitle:phpinfo()
Network Space Search Engines#
Here are some well-known search engines:
The most famous global asset search engine, but now searching for cameras and IoT devices has become a paid service, with limited search times, and some functions are no longer available. Cherish what you have.

- Censys
In this article, we will only select FOFA, which has Chinese content and basic search tutorials, to learn. The syntax of ZoomEye is similar to FOFA.
FOFA#
FOFA is a network space asset search engine launched by BHH. It can help users quickly match network assets and speed up subsequent work processes. For example, vulnerability impact range analysis, application distribution statistics, application popularity ranking statistics, etc.
The homepage looks like this:
ZoomEye#
ZoomEye is a search engine for network space, which includes information about devices, websites, and the services or components they use in the Internet space.
ZoomEye has two detection engines: Xmap and Wmap, which are designed for devices and websites in the network space. By continuously detecting and identifying for 24 hours, it identifies the services and components used by Internet devices and websites. Researchers can easily understand the popularity of components and the scope of vulnerability hazards through ZoomEye.
Although it is called a "hacker-friendly" search engine, ZoomEye does not actively launch attacks on network devices or websites, and the collected data is only used for security research. ZoomEye is more like a navigation chart of the Internet space.
The homepage looks like this:

Reference articles: