Article Reference: Sh00t: A Penetration Testing Management Tool
Project Address: https://github.com/pavanw3b/sh00t
I synchronized it here: https://gitee.com/soapffz/sh00t
Tool Function#
One-sentence summary: It lists out each task you need to penetrate based on standard penetration testing guidelines, and allows you to check them off when completed, serving as a to-do list.
Translation of the GitHub project homepage:
Security Testing is not as simple as right click > Scan. It's messy, a tough game. What if you had missed to test just that one thing and had to regret later? Sh00t is a highly customizable, intelligent platform that understands the life of bug hunters and emphasizes on manual security testing.
Security testing is not as simple as right click > scan. It's a messy, tough game. What if you missed testing that one thing and had to regret it later? Sh00t is a highly customizable, intelligent platform that understands the life of bug hunters and emphasizes manual security testing.
In other words, the function of this tool is similar to a notebook. It helps you list the items you need for penetration testing and generates reports for you. It is not a "magic tool" for right-clicking and starting penetration.
Tool Installation#
- Installation Environment Requirements
My environment: Win10+Anaconda, for other environments, please refer to GitHub.
*Attachment: Introduction to Python - Environment Configuration - Anaconda and Pycharm and Formatting Tool Black
git clone https://gitee.com/soapffz/sh00t.git
cd sh00t
pip install -r requirements.txt
- Set up the database:
python manage.py migrate
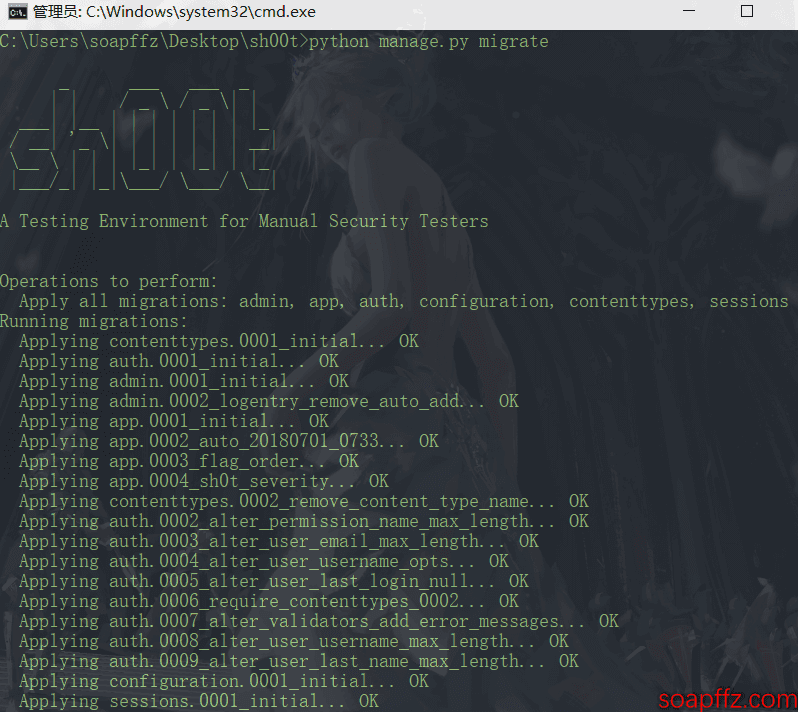
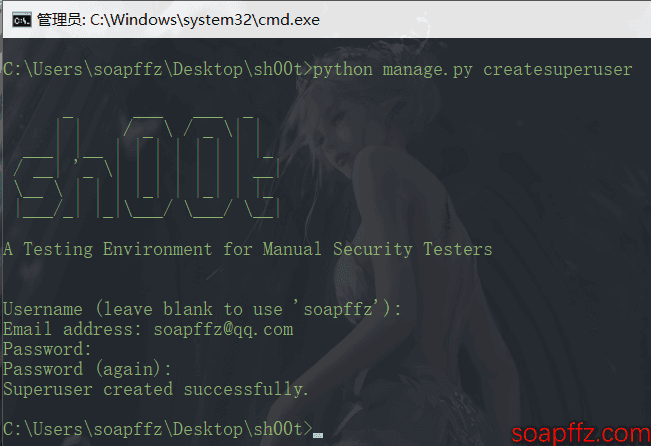
- Create a user account:
python manage.py createsuperuser
And create an account according to the UI.
Tool Usage#
Start:#
python manage.py runserver
Access: http://127.0.0.1:8000/:
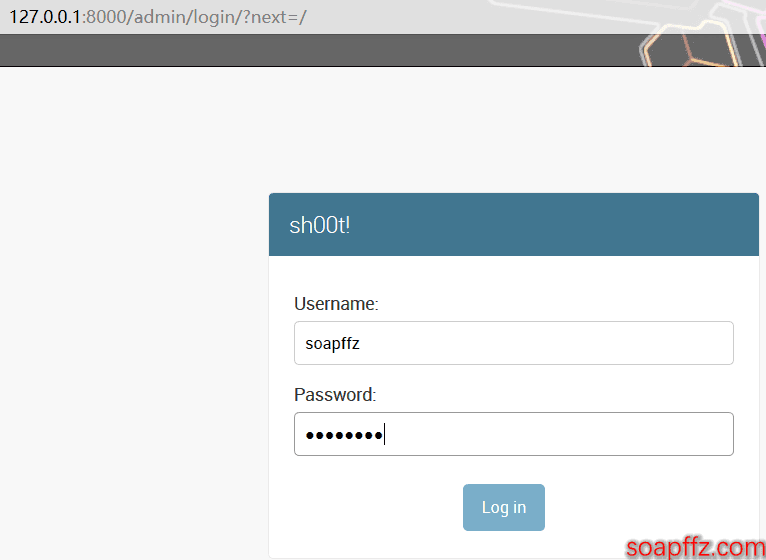
Log in with the user credentials created in the settings before using the tool. The main interface is shown in the figure:
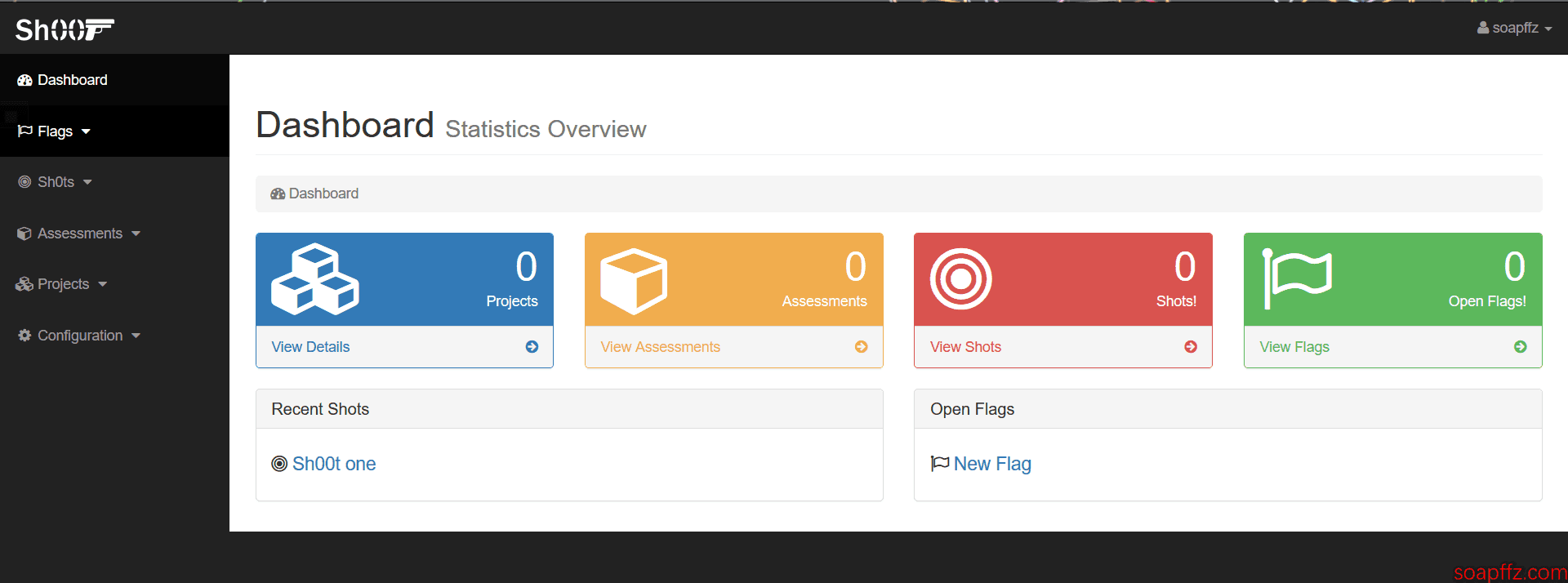
How does it work?#
First, create a new assessment. Choose the method you want to test. There are 330 test cases today, divided into 86 flags, belonging to 13 modules, created according to the testing method of the "Web Application Hacker's Handbook". Modules and flags can be carefully selected and customized. After creating an assessment using flags, testers must manually test them (Sh0t), or semi-automatically test them with the help of scanners and tools, or test them as needed, and mark them as "completed" when finished. When performing an assessment, we often provide custom test cases specific to certain scenarios in the application. New flags can be easily created at any time. Whenever a flag is confirmed to be a valid bug, a Sh0t can be created. The most suitable error template can be selected, and sh00t will automatically populate the error report based on the selected template.
Example Demonstration#
I will use accessing my own site as an example to explain how to use the tool.
Create a project#
Just create a new one in Projects.
Configure assessments#
Then create a new assessment, and the parameter explanations are as follows (please praise me, thank you). The options for WAHH (I don't know what it is either) are as follows:
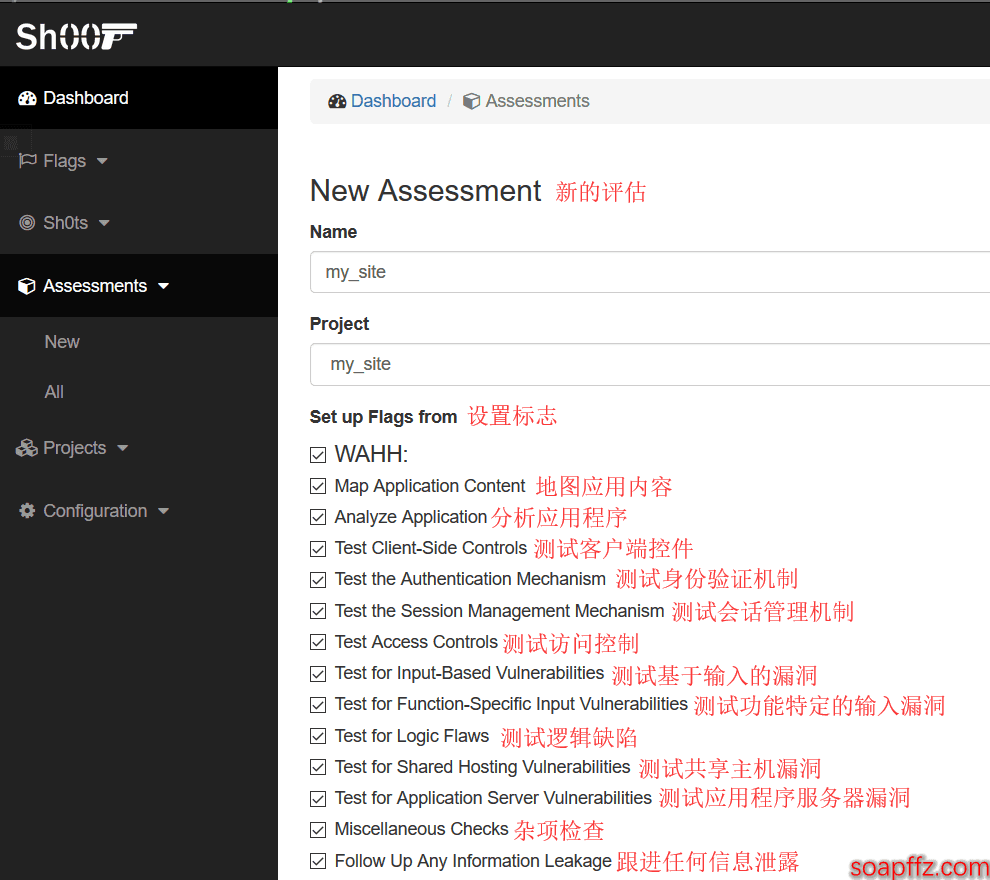
The OWASP configuration is as follows (I believe everyone has heard of this):
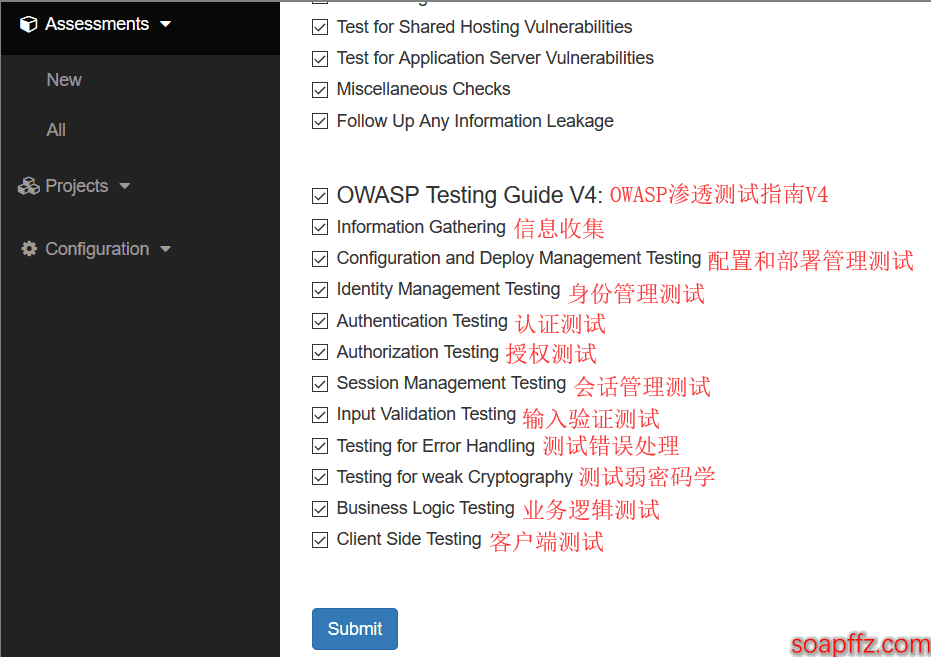
I have selected all options here to see the effect.
Configure Sh0t#
Add the site (or content) you need to penetrate, and then select a security level:
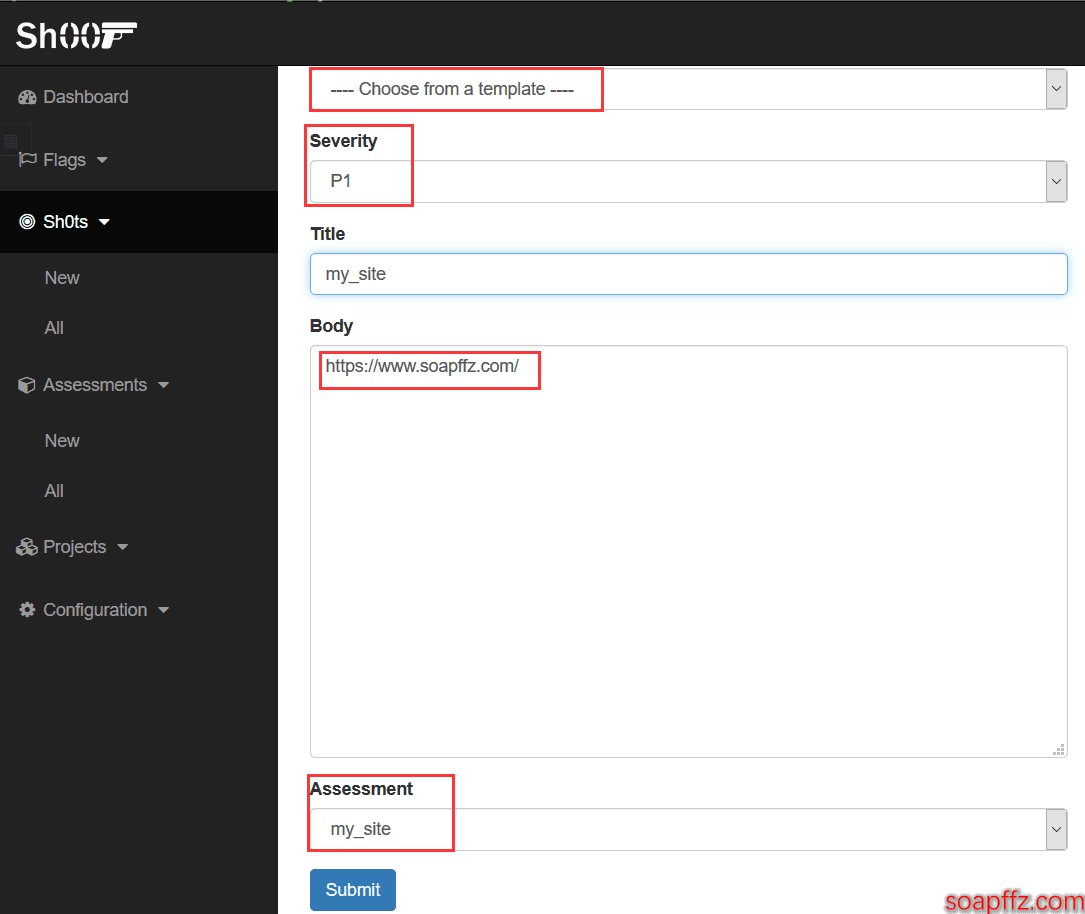
At this point, you have completed all your preparations, and you can view your task list:
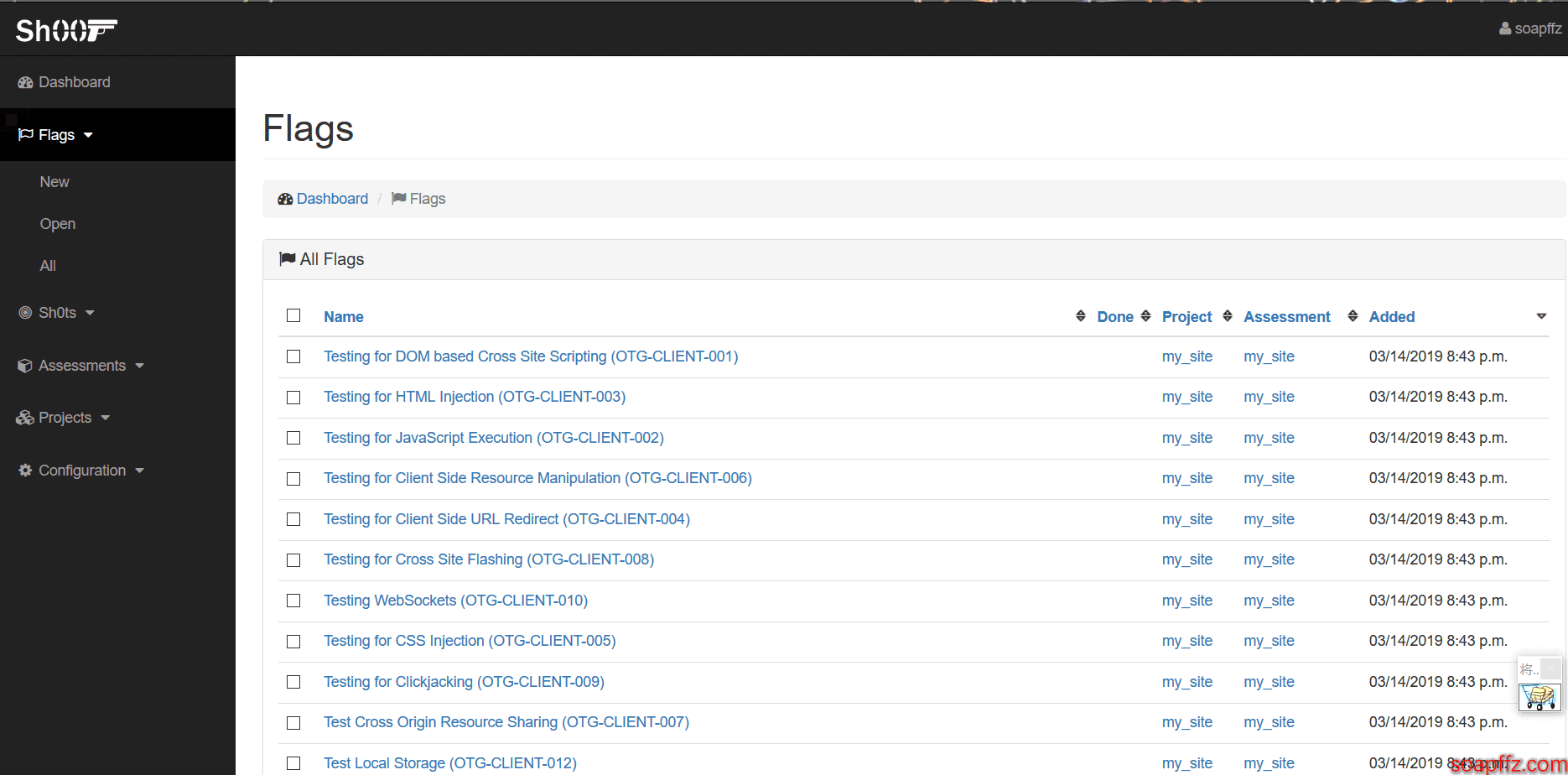
The P1 level only has a little over 174 flags (manual dog head):
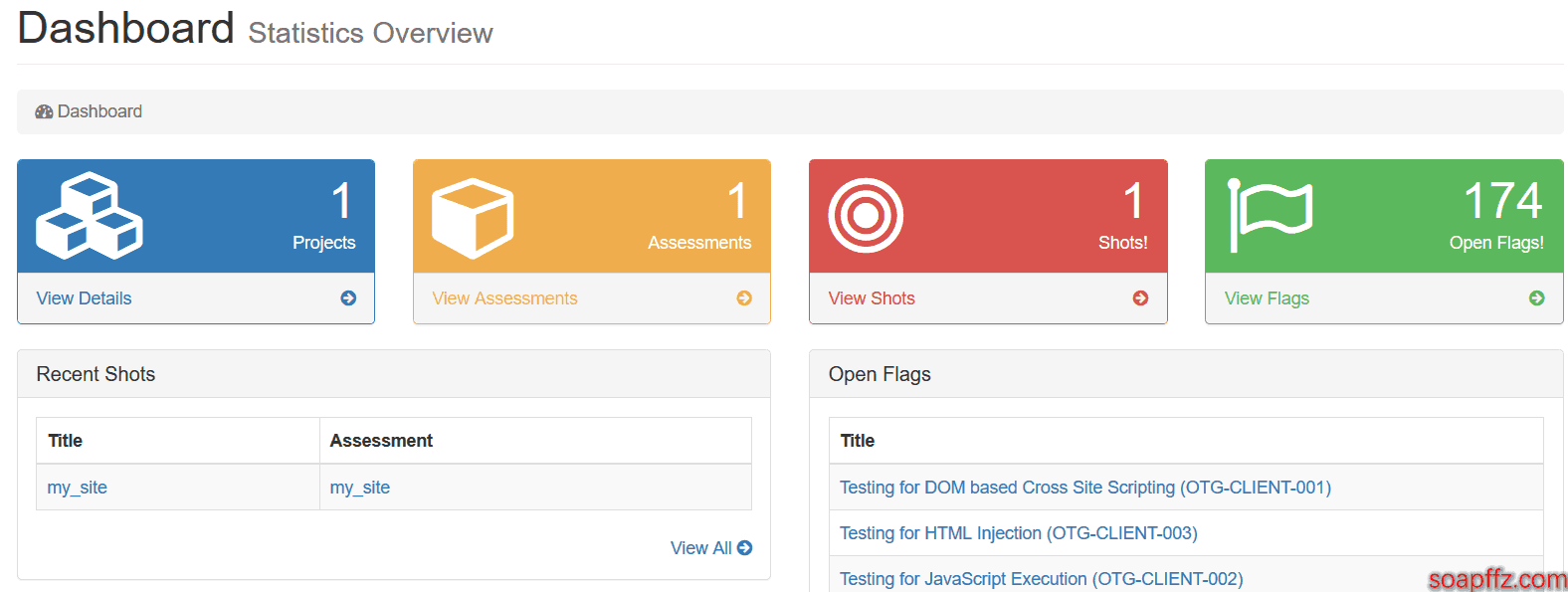
One-sentence summary: This is a task list!