Cause#
(While reviewing for three exams, I'm here again, writing an article and it's not an update to the basic article. Oh~ damn gravity)
When reviewing, it's really easy to slack off with a computer... While slacking off and browsing through the articles I saved as notes
I came across an article on log analysis that I saved a long time ago and it was really well written: Analyzing Server Logs with Shell in Hand
Today, based on this article, I will analyze website access logs and server access logs to see what areas of website security need improvement.
Analysis#
Downloading Logs#
Since I found that I would get disconnected from the shell when using MobaXterm to connect to the server, I decided to download the logs and analyze them using Ubuntu.
By the way, I recommend MobaXterm, the all-in-one terminal tool for Windows. Here's my article on how I got into it: All-in-One Terminal Tool for Windows - MobaXterm
I originally wanted to write an article about this in the tool sharing directory, but I don't have that many services myself. So, just take a look at the article I mentioned above.
Of course, as a newbie like me, I'm using the "Chinese version" of Wu Ai Po Jian (Cracking Paradise). The version I'm currently using is v11.1 Build 3860 translated by the great hx77890.
Click here to download the original post. If you have the ability, it's still better to support the official version. The translated version looks like this:
The website's access logs are usually located in the /www/wwwlogs directory. Open the directory:
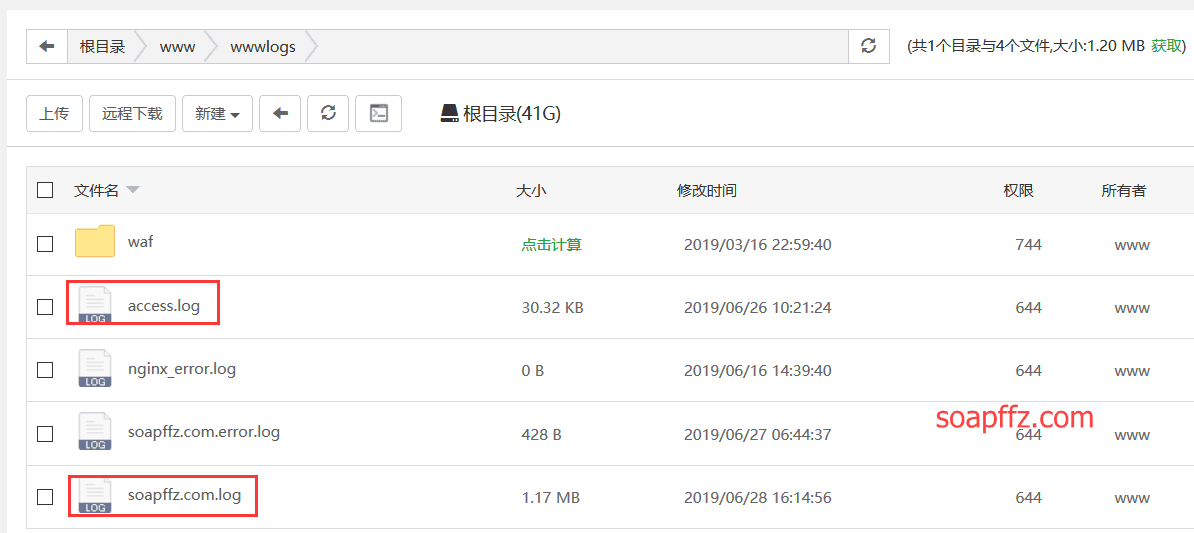
You can see a log named after the website and an access.log, the former being the website's log and the latter being the access log.
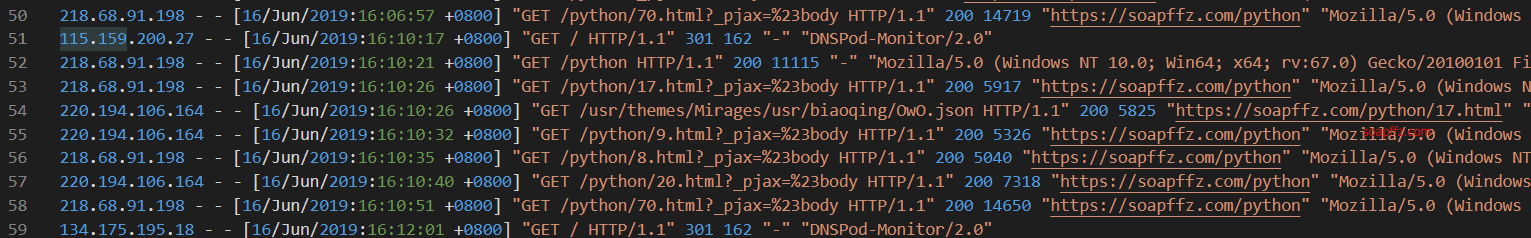
The website log looks something like this:
Analysis#
(The explanation of the command line analysis parameters will be added later)
After downloading the logs, I put them in Ubuntu:
Let's start analyzing the website's logs.
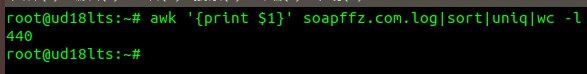
Check how many IP addresses have accessed:
awk '{print $1}' soapffz.com.log|sort|uniq|wc -l
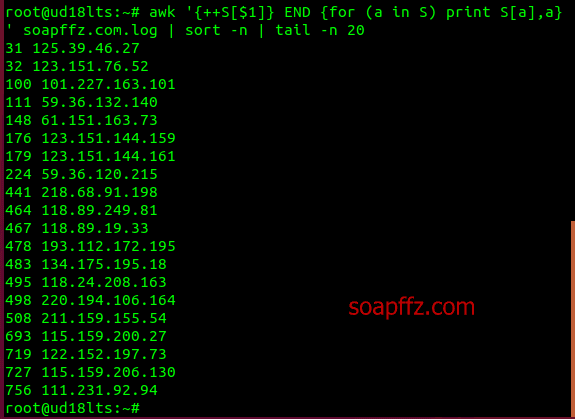
Sort the number of pages accessed by each IP in ascending order and check the top 30 IPs with the most accesses:
awk '{++S[$1]} END {for (a in S) print S[a],a}' soapffz.com.log | sort -n | tail -n 30
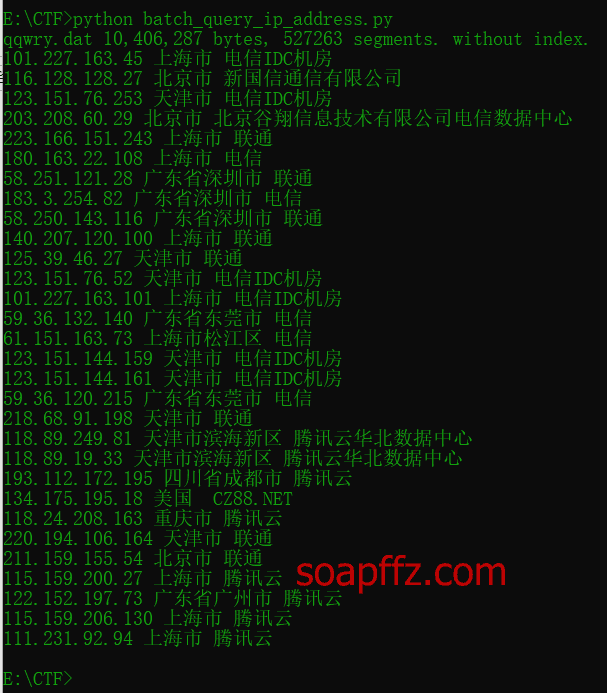
Using the script from my previous article, Python - Batch IP Address Query, the query results are as follows:
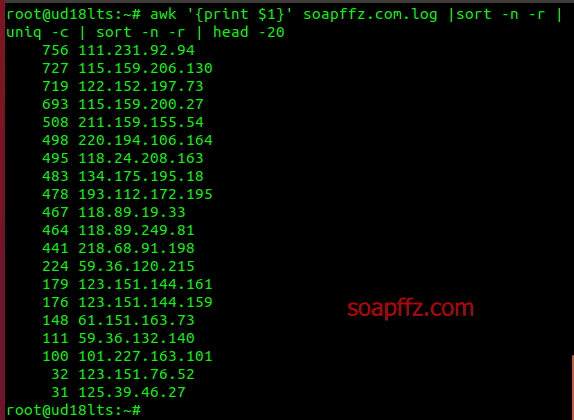
Of course, there is more than one way to see the IP with the highest access:
awk '{print $1}' soapffz.com.log |sort -n -r |uniq -c | sort -n -r | head -20
Check which pages a specific IP has accessed. Here, let's choose the IP with the most accesses, excluding companies like Tencent Cloud:
grep ^140.207.120.100 soapffz.com.log| awk '{print $1,$7}'
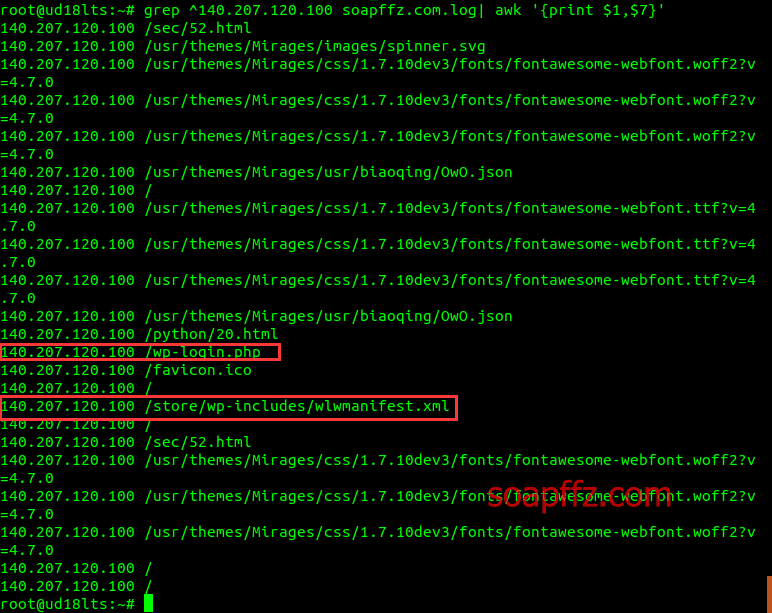
You can see that this person from Shanghai tried to access /wp-login.php and /store/wp-includes/wlwmanifest.xml, which are common sensitive pages for WordPress. Moreover, they only accessed these two pages, so it doesn't look like a scanner scanning.
Check the 20 files or pages with the most accesses:
cat soapffz.com.log|awk '{print $11}'|sort|uniq -c|sort -nr | head -20
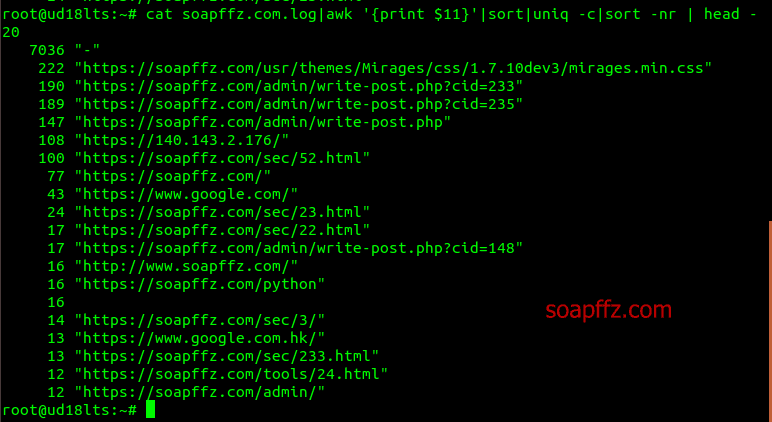
That's about it for soapffz.com.log. Now let's take a look at access.log.
Check the IP with the highest access:
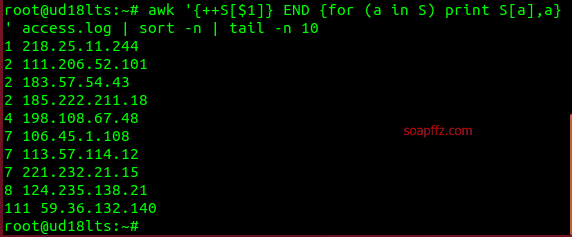
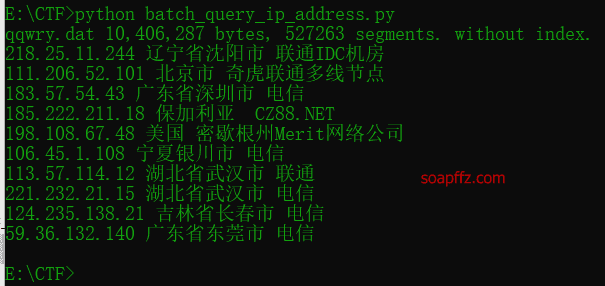
Check the location of the IP:
Check which ports the IP with the highest access has accessed:
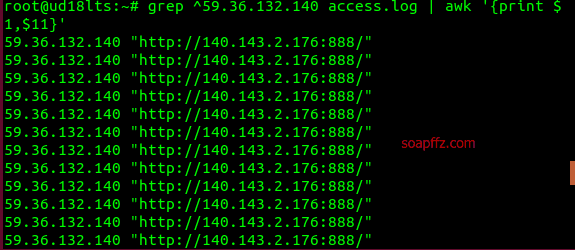
Fortunately, I took a look at the logs and realized that the pages I mentioned earlier only include the content after the "URL: Port". This IP, 59.36.132.140, from Dongguan, Guangdong Province, China, has been brute-forcing my 888 port. I checked soapffz.com.log again and didn't find this issue.
Port 888 is the phpMyAdmin port, and maybe I attracted attention by exposing the port myself.
Since this person likes brute-forcing, then I'll (big GIF warning):
::quyin:1huaji::
Good luck, my friend!
Conclusion#
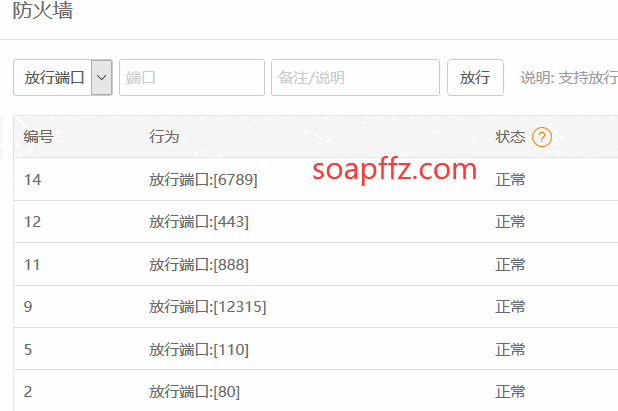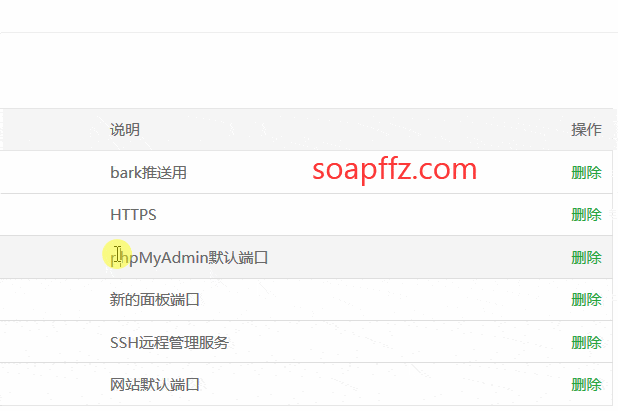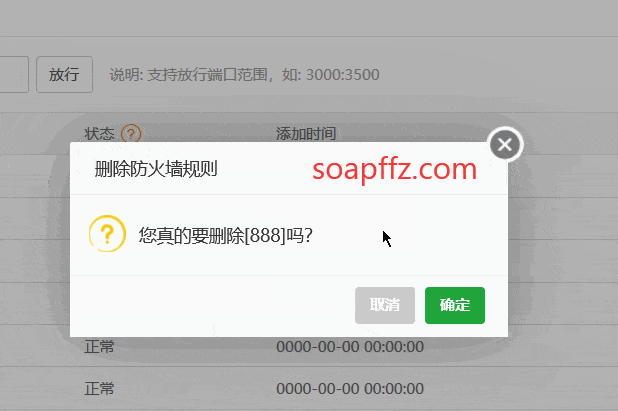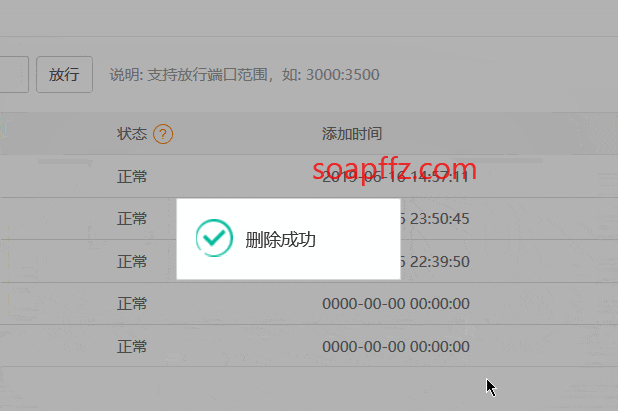
In summary, only open the ports you need.
If it's a common and necessary port, you should also take security measures. Here are the measures I took:
- After installing the blog framework, delete the
installfolder and other configuration files. - Close or delete unnecessary ports.
- Use private key for SSH connection.
- Use secure entry points for panels like Baota and change the login path.
- Use web security protection tools like Tencent Cloud's.
- Detect abnormal website access IPs and automatically block them.
End of article.