前言#
在上一篇文章中,我们已经搞定了子域名,旁站和 C 段
现在基本确定了目标范围,现在我们可以探测以下目标是否有敏感文件泄露以及是否探测目标服务器信息
此部分包括 CMS 类型识别,因为它的本质也是目录扫描
敏感文件泄露扫描#
dirBuster#
GitHub 地址:
Github Repo not found
The embedded github repo could not be found…
经典的扫描工具,java版本,最后一次更新是在2009-03-03,最后一版长这样:

虽然经典,但是太老了,就不介绍了
御剑#
御剑孤独大佬写的工具,网上太多珍藏版御剑和珍藏版字典,御剑珍藏版界面如下:

只支持windows,故也不做介绍
BBScan#
又是lijiejie大佬的作品,对,上篇文章介绍的subDomainsBrute也是他的作品,tql
GitHub 地址:
Github Repo not found
The embedded github repo could not be found…
工具一直保持着更新,使用的是python2,一个很简单小巧的扫描工具,但是好像扫描效果不是那么好:

此处了解下即可。
dirsearch#
GitHub 地址:
Github Repo not found
The embedded github repo could not be found…
参考 居正 大佬的文章:
DF-PUSH (May.17)—— 抛弃过时的御剑:DirSearch 引领 web 路径爆破新时代!
扫一下我的网站
下载 居正 大佬提供的中文目录字典,解压,放到 dirsearch.py 的同目录下:

指定字典,指定站点类型为 php,排除状态码,跟随地址重定向扫描,线程 100,设置随机代理扫描我的网站:
python dirsearch.py -u soapffz.com -w "dics_cn/php.txt" -e php -x 400,403,404,500,503,514,564 -F -t 150 --random-agents
- 注意:字典路径需要用双引号括起来,且路径斜杠需为 / 左斜杠

扫描完后在reports/soapffz.com中就可看到扫描报告:

GitHack#
GitHack 是一个.git 泄露利用脚本,通过泄露的.git 文件夹下的文件,重建还原工程源代码。
渗透测试人员、攻击者,可以进一步审计代码,挖掘:文件上传,SQL 注射等 web 安全漏洞。
它也是由lijiejie大佬写的工具,GitHub 地址:https://github.com/lijiejie/GitHack
不得不说lijiejie大佬 tql!
下面举一个例子,是我在做某 CTF 平台的题遇到的,来自csaw-ctf-2016-quals的mfw一题
先用刚刚介绍过的dirsearch配合自带的字典扫描,结果如下:

发现是 Git 泄露,用GitHack把泄露的文件下载下来 (py2 环境):
python GitHack.py http://url/.git

Dirmap#
H4ckForJob 在2019-04-11在 GitHub 上创建的项目
在 4 月底在 Freebuf 上发文:Dirmap:一款高级 Web 目录文件扫描工具
GitHUb 地址:
Github Repo not found
The embedded github repo could not be found…
An advanced web directory & file scanning tool that will be more powerful than DirBuster, Dirsearch, cansina, and Yu Jian. 一个高级 web 目录、文件扫描工具,功能将会强于 DirBuster、Dirsearch、cansina、御剑。
官方自己说的,真 *
看了下文件目录结构和使用方法,和dirsearch很相似
默认状态下可以扫描网址,网段,自动保存结果到 output 生成一个目标域名.txt
现在是v1.0版本,高级参数不能通过命令行指定,只能配置dirmap.conf文件
默认单URL扫描命令如下:
python3 dirmap.py -i https://target.com -lcf
但是扫描后并没保存结果,看了下使用说明
参数很多,待办事项也很多,emmm,有重复造轮子的嫌疑吗?不知道
就不介绍下去,在此处插个眼,后续发现更新得没那么复杂了,再来写用法
7kbscan-WebPathBrute#
7kbstorm大佬写的工具,发布到GitHub的时间为2019-04-22,截至写文章时最新版本为v1.6
Github 地址:
Github Repo not found
The embedded github repo could not be found…
使用默认的字典,设置 100 线程,字典类型为php和path,扫描如下 (电脑点击看大图):
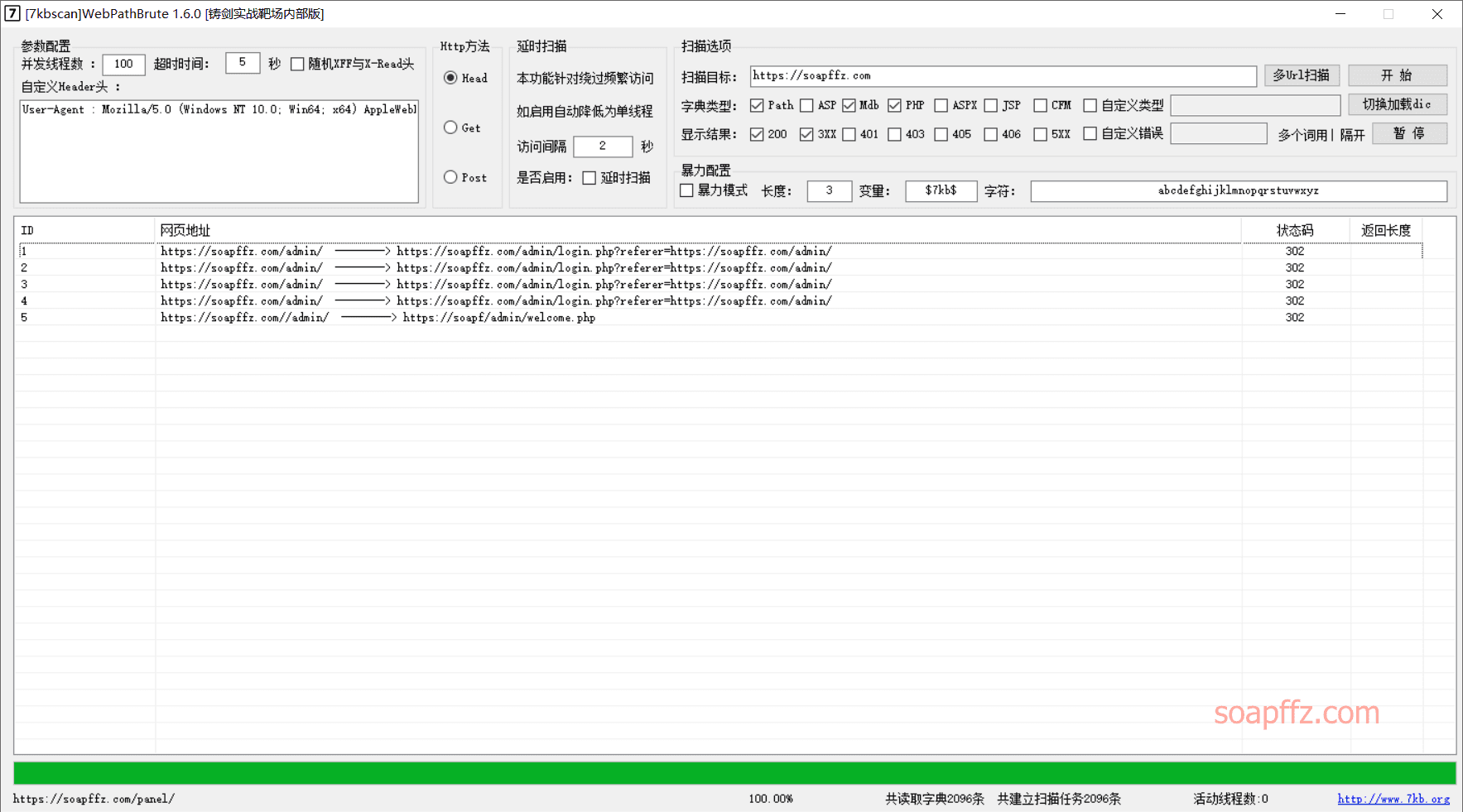
缺点:
Windows平台- 设置超大线程或者加载字典过大,软件就基本卡死了,点击停止会跳为开始,也就是不能停止
优点:
Windows平台替代御剑的最佳选择- 内置了很多很好的字典
综合:很推荐!::quyin:1huaji::
敏感文件泄露扫描总结#
御剑 是不想再用了,7kbstorm团队的WebPathBrute能很好代替它,但是要注意字典和线程不要太大会卡死
命令行版的推荐dirsearch,可配合.git泄露扫描工具GitHack使用,另外dirmap值得关注一下
当然除了这些专职于敏感信息泄露扫描的软件,还有很多漏洞扫描软件也内置目录扫描功能
我会在漏洞扫描软件介绍的文章中提到
CMS 识别#
Test404 轻量 CMS 指纹识别#
原名 Test404 轻量 web 指纹识别,目前的版本是v2.1,2018-10月份的更新
实测几个常见的网站全部请求超时或者识别失败
emmm,但是还是看到有很多人推荐,所以这款软件应该只适用于特征明显的 CMS 系统,暂且留作后备软件使用
Wappalyzer 插件#
它是基于正则表达式来识别 web 应用的,对我的网站识别是这样的:
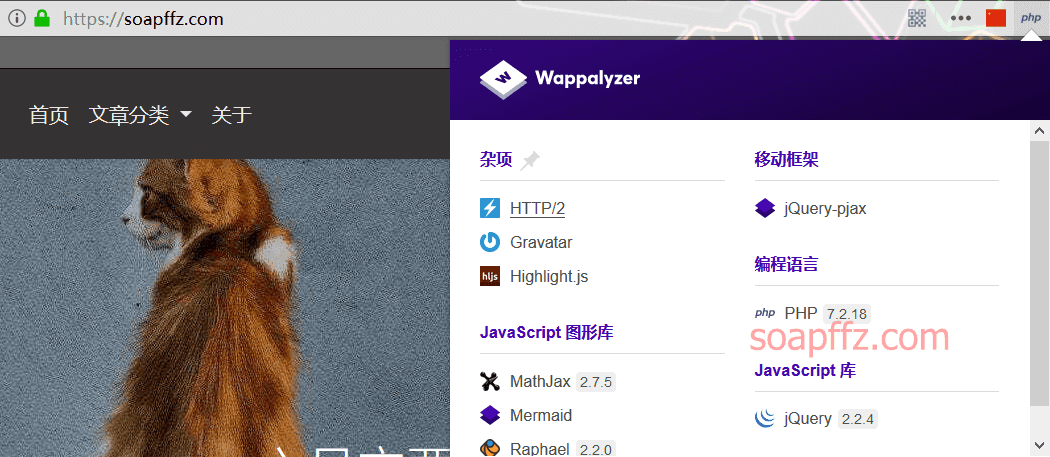
这个小插件安装后会在地址栏的倒数第二个位置,还是很方便的,强烈建议安装!
与Wappalyzer类似的还有一款插件whatruns,直接在你的浏览器中打开它的官网
它会自动识别浏览器并引导你下载安装,效果如下:
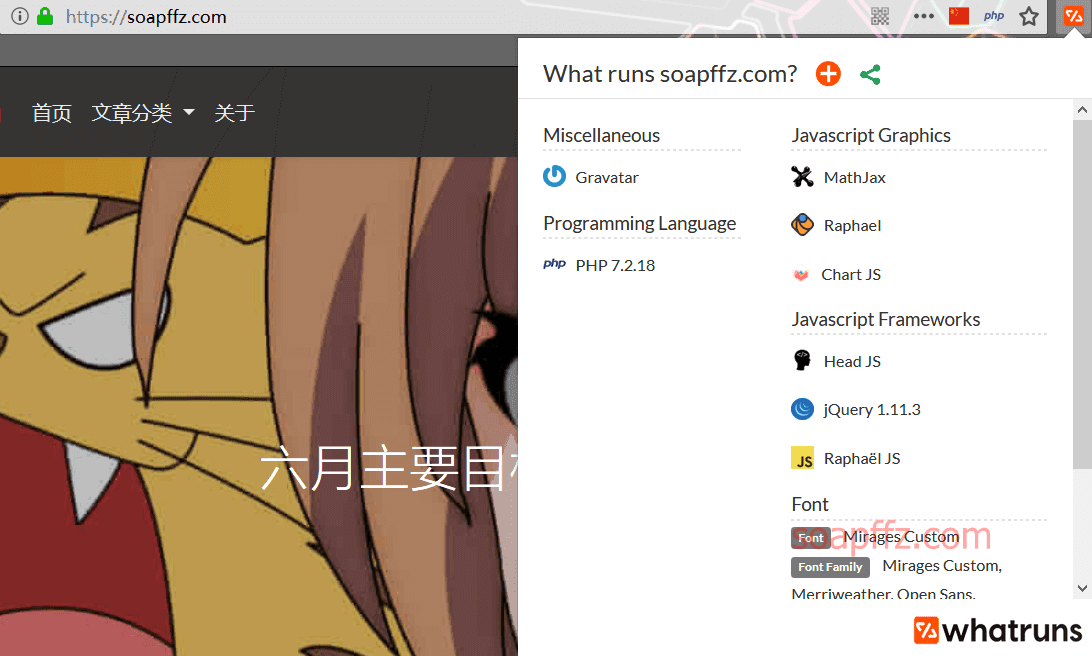
获取的信息和Wappalyzer差不多,两者安装其一即可
云悉在线 WEB 指纹识别#
在上一篇资产扫描中我们介绍的了云悉的资产扫描,它也有 WEB 指纹识别功能
网址:http://www.yunsee.cn/finger.html
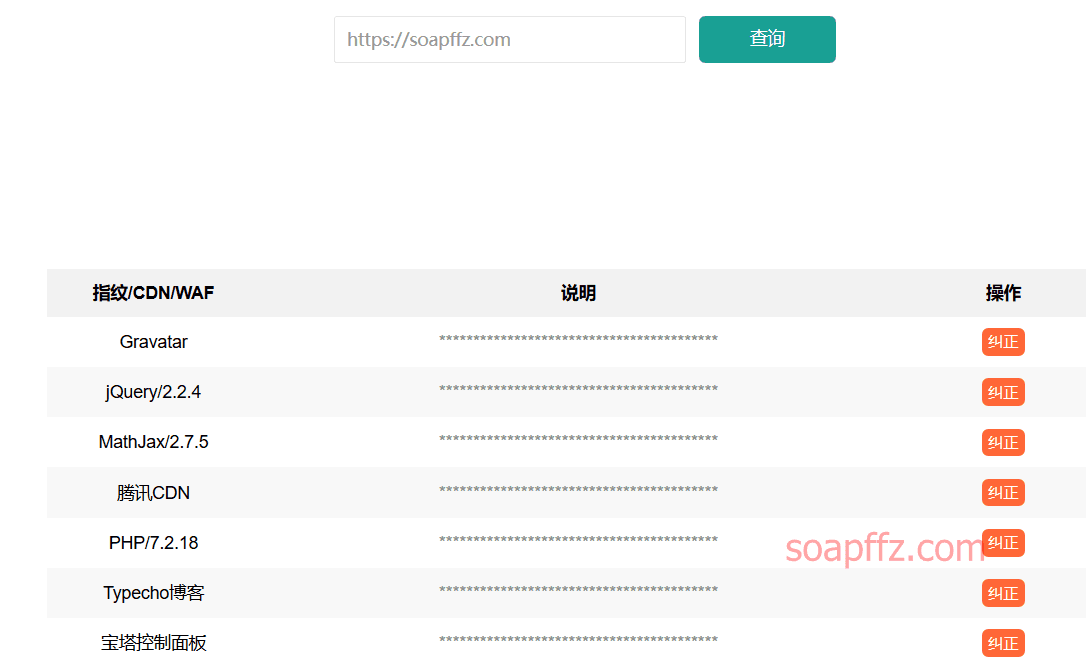
嗯,扫描结果还是很准确的
w11scan#
GitHub 地址:https://github.com/w-digital-scanner/w11scan
作者开发和测试环境都是Ubuntu,看了下安装说明文档太复杂了,放弃了,下一个
Scan-T#
GitHub 地址:
Github Repo not found
The embedded github repo could not be found…
官方简介:
https://nanshihui.github.io/2016/01/21/ToolForSpider%E7%AE%80%E4%BB%8B/
也是Linux环境下安装,这个配置比上一个还要复杂,插个眼
WebEye#
指纹库不是基于 md5 之类的,而是类似于 fofa 通过 http 头信息、关键字等进行快速识别。
GitHub 地址:
Github Repo not found
The embedded github repo could not be found…
依赖python2环境,使用pyhton WebEye.py -u https://soapffz.com命令即可检测:


能检测出 WAF,服务器类型,CMS,脚本语言,方便快捷,可作为小工具备用
whatweb#
截至写文章时,最新版本为2017-11-23发布的0.4.9版本,下载地址
Whatweb基于ruby语言开发,因此需要安装在具备ruby环境的系统中,在Windows下安装需要如下步骤:
Install WhatWeb On Windows 2018
Todo :
* Download Ruby WIth DivKit
* Install Ruby
* Install Git For Windows
* Open CMD Then type :
* git clone https://github.com/urbanadventurer/Wh
* gem install bundler
* bundle install
* bundle update
* gem install bson
* gem install bson_ext
* gem install mongo
* gem install rchardet
whatweb URL_For_Check
参考视频:WhatWeb Web Scanner Installtion On Windows 2018
太复杂了,故不建议在Windows下安装whatweb,Kali已自带,基本使用方法:
whatweb -v 域名 :以详细方式打印出扫描信息:

扫描 1 秒完成,一般只需要读最上面的Summary总结部分即可,下面是对每一部分部件的官方解释,没必要看
还有其他的一些用法:
whatweb -l : 列出所有插件
whatweb --info-plugins='插件名' : 查看插件的具体信息
类似于SQLMAP的level等级,whatweb也有-aggresion(简写为-a)参数,此参数后边可以跟数字1-4分别对应4个不同的等级。
1.Stealthy 每个目标发送一次 http 请求,并且会跟随重定向
2.Unused //不可用。(从2011年开始,此参数就是在开发状态。)
3.Aggressive 每个目标发送少量的 http 请求,这些请求是根据参数为1时结果确定的
4.Heavy 每个目标会发送大量的 http 请求,会去尝试每一个插件
官方也有在线扫描网站,懒得打开 Kali 的同学也可以使用这个,得到的是精简版的结果哦:

CMS 识别总结#
除了上面介绍的这些工具外,信息收集-搜搜引擎这篇文章中介绍的fofa等搜索引擎也是能识别服务框架的
总的来说:
Wappalyzer(或whatruns二选一) 或者云悉在线WEB识别或者whatweb的网页版已经足够满足日常需求
也可以配合WebEye小脚本使用
如果这几个还没有满足你的需求,不妨用 Test404 家的轻量CMS指纹识别碰碰运气
如果需要更强一点的工具,可以使用whatweb -v -a 4 网站命令去搜索
其他一些工具没有介绍的主要原因:
- 御剑 WEB 指纹识别:扫描速度太慢
- Plecost:wordpress 的漏洞指纹识别和漏洞查找器
- BlindElephant:看起来安装很费劲的亚子
参考文章: